This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Security Integration System"
MB netblue4 (talk | contribs) (→What does SCAT do) |
MB netblue4 (talk | contribs) (→Process integrity tool vs point in time security verification tool) |
||
| Line 25: | Line 25: | ||
<li>Both types of tools are important and some applications have functionality that crosses the line</li> | <li>Both types of tools are important and some applications have functionality that crosses the line</li> | ||
</ul> | </ul> | ||
| + | |||
| + | |||
| + | <h1>Tools and SDLC</h1> | ||
| + | |||
| + | |||
| + | |||
| + | <table border="1px"> | ||
| + | <tr> | ||
| + | <td>SDLC phase</td> | ||
| + | <td>SCAT Process integrity tool</td> | ||
| + | <td>Point in time security verification tool</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Sprint planning</td> | ||
| + | <td><strong>Ensures security requirements are understood </strong> | ||
| + | <ul> | ||
| + | <li>Security requirements are enriched with environment specific contextual information and guidance <span style="text-decoration:underline;">before development begins</span> </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | <td><strong>Relevant security requirements </strong> | ||
| + | <ul> | ||
| + | |||
| + | <li>Automatic scans generate security requirements to fix existing vulnerabilities | ||
| + | </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Develop | ||
| + | </td> | ||
| + | <td><strong>Ensures correct implementation of security requirements</strong> | ||
| + | <ul> | ||
| + | |||
| + | <li>Code level guidance and automatic DAST tool scans to verify correct implementation | ||
| + | </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | <td> | ||
| + | </td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Secure code review | ||
| + | </td> | ||
| + | <td><strong>Ensures correct implementation of security requirements</strong> | ||
| + | <ul> | ||
| + | |||
| + | <li>Manually review guidance and automatic SAST tool scans to verify manual review | ||
| + | </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | <td> | ||
| + | </td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Testing | ||
| + | </td> | ||
| + | <td><strong>Ensures valid security testing</strong> | ||
| + | <ul> | ||
| + | |||
| + | <li>Secure test plans to guide correct implementation of security requirements | ||
| + | </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | <td> | ||
| + | </td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Approval | ||
| + | </td> | ||
| + | <td><strong>Streamline audit/approval process </strong> | ||
| + | <ul> | ||
| + | <li>Providing one click traceability through requirements as evidence of secure development and testing | ||
| + | </li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | <td> | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | <ul> | ||
| + | <li>Using only point in time vulnerability detection tools will teach developers to fix vulnerabilities through trial and error. But when experienced developers leave the team, new developers have to learn by making the same costly mistakes again</li> | ||
| + | <li>Process integrity tools fix this problem by guiding and verifying correct implementation at each stage of the SDLC. Making security part of the process of building software and reducing the reliance on individuals</li> | ||
| + | |||
| + | |||
<h1><b>Description</b></h1> | <h1><b>Description</b></h1> | ||
| + | |||
==Build, Verify Assure== | ==Build, Verify Assure== | ||
<ul> | <ul> | ||
Revision as of 11:37, 30 September 2019
What is the Secure code assurance tool (SCAT)
What SCAT does not do
What SCAT does do
Process integrity tool vs point in time security verification tool
Build, Verify Assure
Low levels of compliance
Compliance and assurance seen as blockers
Duplication of effort and inconsistent implementation
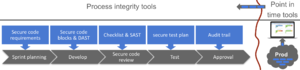
See below how the Secure code assurance tool integrates security into software development phases Sprint planning phaseObjective: Ensures security requirements are understood
Development phaseObjective: Ensure correct implementation of security requirements
Secure code review phaseObjective: Ensure correct implementation of security requirements
Testing phaseObjective: Ensure valid security testing
Approval phaseObjective: Streamline the approval and audit process
Risk managementObjective: Enable risk managers to prioritise, plan and monitor mitigation efforts
When developing secure software we need to consider both standard secure code and client specific architectural requirements Standard secure code requirements
Client specific architectural requirements
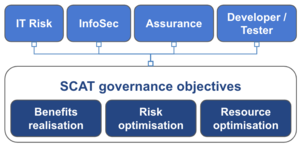
SCAT has the following governance objectives implemented by the following “first line of defense” functions Benefits realisation: Enabling development teams to deliver at speedRisk optimisation: Minimise the negative and maximise the positive consequencesResource optimisation: Predictable, repeatable and consistent level of security across all teams
Promoting compliance to security requirements
Minimising the impact of audit and assurance
Informing risk based decision making
Integrating security into the software development process
LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the link GNU Affero General Public License 3.0 as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. Project Resources[Installation Package] [Source Code] Project LeaderClassifications
| ||||||||||||||||||||||||