This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Top 10 Card Game"
(Edits) |
(Edits) |
||
| Line 29: | Line 29: | ||
A primary requirement for the game is that it be designed around the standard set of playing cards so that the general public is familiar with the medium facilitating internationalization. The standard two player configuration includes one TA deck and one DC deck for each gamer. The Threat Agent (TA) deck includes two Joker cards that are used to represent a Phishing attack. This brings the TA’s deck to a total of 54. The Defense Control (DC) deck also includes two joker cards that are used to represent White Hat defensive controls. This also brings the DC deck to a total of 54. | A primary requirement for the game is that it be designed around the standard set of playing cards so that the general public is familiar with the medium facilitating internationalization. The standard two player configuration includes one TA deck and one DC deck for each gamer. The Threat Agent (TA) deck includes two Joker cards that are used to represent a Phishing attack. This brings the TA’s deck to a total of 54. The Defense Control (DC) deck also includes two joker cards that are used to represent White Hat defensive controls. This also brings the DC deck to a total of 54. | ||
| − | During game design, | + | During game design, a blue color deck was used to represent the DC team and a red color deck (of the same manufacture) was used to represent the malicious TA team. Cybersecurity activities and training are frequently designed around the concept of red (attacking) and blue (defending) teams. |
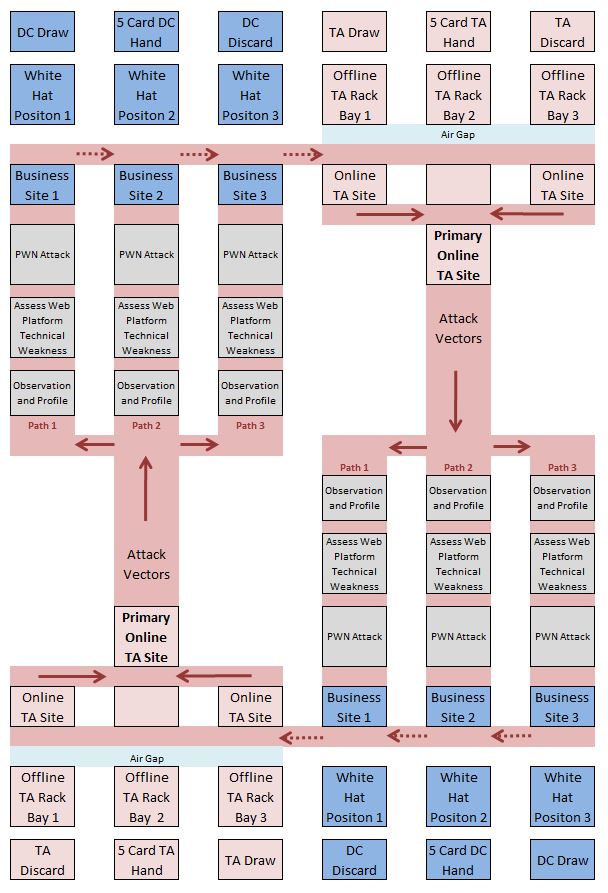
The game’s detailed play grid (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) is based in part on the attack path flow diagram provided with OWASP’s Top 10 publication. The play grid is designed to help students visualize how threat agents can potentially use many different paths through your application to do harm to your business or organization. The standard two player (four deck) version of the play grid can be summarized as follows: | The game’s detailed play grid (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) is based in part on the attack path flow diagram provided with OWASP’s Top 10 publication. The play grid is designed to help students visualize how threat agents can potentially use many different paths through your application to do harm to your business or organization. The standard two player (four deck) version of the play grid can be summarized as follows: | ||
| Line 36: | Line 36: | ||
</gallery> | </gallery> | ||
| − | The detailed version of the play grid contains instructional content and provides visual continuity for players | + | The detailed version of the play grid contains instructional content and provides visual continuity for players: |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | [[File:Play Grid Detailed.jpg|OWASP Card Game Grid]] | ||
| + | </gallery> | ||
The objective of the game is to take control of (PWN) your opponent’s three business websites while protecting your business websites. It is possible to knockout all three of your opponents TA attack websites. | The objective of the game is to take control of (PWN) your opponent’s three business websites while protecting your business websites. It is possible to knockout all three of your opponents TA attack websites. | ||
| Line 126: | Line 123: | ||
|- | |- | ||
| 8 || Game Grid || The initial prototype was designed with a more simple grid; however, this proved to be a bit boring for the gamer. The current game grid design reflects design aspects taken from the OWASP Top 10 publication and a layered attack vector that is segmented into five defense-in-depth activities that are summarized with the mnemonic OWASP || Consider ways to modify the game grid to enhance the learning experience || Dennis Johnson | | 8 || Game Grid || The initial prototype was designed with a more simple grid; however, this proved to be a bit boring for the gamer. The current game grid design reflects design aspects taken from the OWASP Top 10 publication and a layered attack vector that is segmented into five defense-in-depth activities that are summarized with the mnemonic OWASP || Consider ways to modify the game grid to enhance the learning experience || Dennis Johnson | ||
| + | |- | ||
| + | | 9 || Card Back Designs || At a minimum, the TA deck should be a color different than the DC deck. A red TA deck and a Blue DC deck seem to augment a more realistic learning experience. Using cards with the same design pattern, made it easy to mix up the player cards || Consider ways to help the players not mix up their playing cards, such as different card back patterns or maybe card jackets.|| Dennis Johnson | ||
|} | |} | ||
[[Category:OWASP Project]] [[Category:OWASP_Document]] | [[Category:OWASP Project]] [[Category:OWASP_Document]] | ||
Revision as of 01:08, 13 April 2019
OWASP Top 10 Card Game - Game DescriptionThe OWASP Top Ten card game is a fun to play poker deck card game that pits the black hats against the white hats to see who can be the first to hack their opponent’s website. OWASP Top 10 Card Game - Mission StatementUsing a standard poker card deck, design a card game that combines the concepts of the OWASP Top 10 and the OWASP Top 10 Proactive Controls, for novice level learners, that can be easily converted for use with customized OWASP branded playing cards. OWASP Top 10 Card Game - Game OverviewThe game is designed to be an easy to learn introduction to the risk concepts of the OWASP Top Ten and the best practices control concepts of the OWASP Top Ten Proactive Controls at a novice level in an environment that reflects a sense realism and excitement.
The four main components of the game (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) include:
A primary requirement for the game is that it be designed around the standard set of playing cards so that the general public is familiar with the medium facilitating internationalization. The standard two player configuration includes one TA deck and one DC deck for each gamer. The Threat Agent (TA) deck includes two Joker cards that are used to represent a Phishing attack. This brings the TA’s deck to a total of 54. The Defense Control (DC) deck also includes two joker cards that are used to represent White Hat defensive controls. This also brings the DC deck to a total of 54. During game design, a blue color deck was used to represent the DC team and a red color deck (of the same manufacture) was used to represent the malicious TA team. Cybersecurity activities and training are frequently designed around the concept of red (attacking) and blue (defending) teams. The game’s detailed play grid (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) is based in part on the attack path flow diagram provided with OWASP’s Top 10 publication. The play grid is designed to help students visualize how threat agents can potentially use many different paths through your application to do harm to your business or organization. The standard two player (four deck) version of the play grid can be summarized as follows: The detailed version of the play grid contains instructional content and provides visual continuity for players: The objective of the game is to take control of (PWN) your opponent’s three business websites while protecting your business websites. It is possible to knockout all three of your opponents TA attack websites. OWASP Top 10 Card Game - LicensingThis card game is free to use. It is licensed under the Creative Commons Attribution ShareAlike 3.0 license, so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. Special customized card decks are available through OWASP. These are standard poker decks that have been modified to enhance the game’s learning experience. These decks and the related play grid contain OWASP copyrighted images and related descriptions and all rights are reserved. Generally, these decks (and play grid) are updated as the new versions of the OWASP Top 10 are released. All profit derived from the sale of the customized decks (and other related items) are used to further OWASP global efforts. See [add reference / link here] for additional information and examples. OWASP Top 10 Card Game - RoadmapPhase 1 of the project is complete and it resulted in the completion of the proof of concept, mission statement, short team goals, long team goals and a basic game prototype. Phase 2 of the project includes assistance from the OWASP foundation, setting up a project Wiki page, setting up a GitHub page, and adding the project to the OWASP project inventory (Incubator Status). Phase 3 of the project includes looking for other people to help lead and contribute to the project. Areas of need and the corresponding volunteer are listed in the “Getting Involved” section of this Wiki. Phase 4 will move the project to the Labs phase. Phase 5 will move the project to the Flagship phase. Phase 6 addresses the project’s long team goals. It will incorporate the basic OWASP Top 10 Card Game as presented in the Flagship phase along with special customized card decks that will be available through OWASP. These are standard poker decks that have been modified to enhance the game’s learning experience. These decks and the related play grid contain OWASP copyrighted images and related descriptions and all rights are reserved by OWASP. OWASP Top 10 Card Game - Getting Involved
OWASP Top 10 Card Game - Project ResourcesGitHub - https://github.com/OWASP/Top-10-Card-Game/ OWASP Top 10 Card Game - Project LeaderOWASP Top 10 Card Game - Related ProjectsNone OWASP Top 10 Card Game - Lessons Learned
|