This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Mobile Security Testing Guide"
m (Fix link) |
|||
| Line 124: | Line 124: | ||
Work will be split between working groups based on mobile OS and topic. On top of completing the content, we want to apply a basic level of proof-reading, review and editing to get the guide beta-ready. | Work will be split between working groups based on mobile OS and topic. On top of completing the content, we want to apply a basic level of proof-reading, review and editing to get the guide beta-ready. | ||
| − | In order to be able to schedule work during the summit and create work groups we need to know who will be attending the OWASP Summit and how much time you can/will spend for the mobile workshop. Please [ | + | In order to be able to schedule work during the summit and create work groups we need to know who will be attending the OWASP Summit and how much time you can/will spend for the mobile workshop. Please [https://github.com/OWASP/owasp-summit-2017/blob/master/Working-Sessions/Mobile-Security/MSTG.md add yourself to the list of participants] and reach out directly to Sven via Slack. |
If you do not have time during the summit but are interested to help, you can start immediately by assigning issues to yourself and creating pull requests. We can also loop you in remotely during the submit. | If you do not have time during the summit but are interested to help, you can start immediately by assigning issues to yourself and creating pull requests. We can also loop you in remotely during the submit. | ||
Revision as of 05:58, 14 May 2017
Our Vision"Define the industry standard for mobile application security."We are writing a security standard for mobile apps and a comprehensive testing guide that covers the processes, techniques, and tools used during a mobile app security test, as well as an exhaustive set of test cases that enables testers to deliver consistent and complete results. Main Deliverables
|
Classifications
Project Leaders
Road Map
Parent ProjectLicensingThe guide is licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. | |||||||||||||
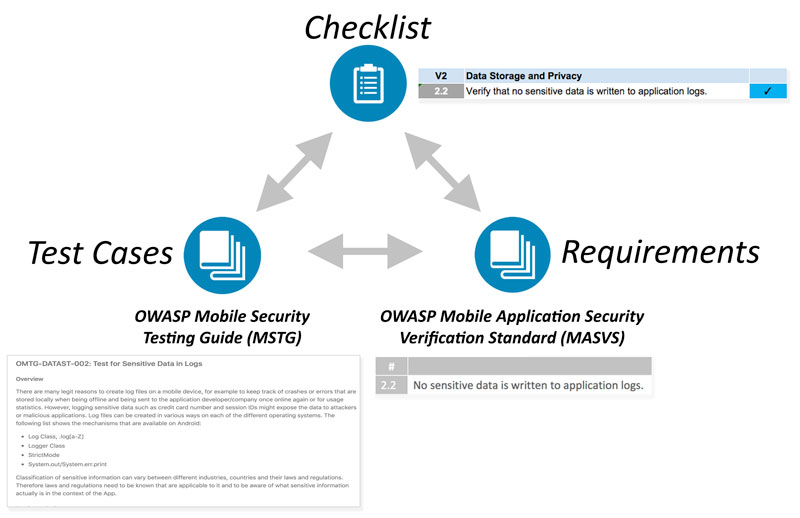
Using the OWASP Mobile App Security Verification Standard, Testing Guide and Checklist
The documents produced in this project cover many aspects of mobile application security, from the high-level requirements to the nitty-gritty implementation details and test cases. They can be used to plan and verify security controls during any phase of mobile app development, as well as during pre-release code review and penetration testing.
- The Mobile Application Security Verification Standard (MASVS) contains generic security requirements along with mappings to verification levels that can be chosen depending on the overall need for security.
- The Mobile Security Testing Guide (MSTG) provides verification instructions for each requirement in the MASVS, as well as security best practices for apps on each supported mobile operating system (currently Android and iOS). It is also useful as a standalone learning resource and reference guide for mobile application security testers.
- The Mobile App Security Checklist can be used to apply the MASVS requirements during practical assessments. It also conveniently links to the MSTG test case for each requirement, making mobile penetration testing a breeze.
It is important to note that the security standard, testing guide and checklists are closely related: They all map to the same basic set of requirements. Depending on the context, the documents can be used stand-alone or in combination to achieve different objectives.
For example, the MASVS requirements may be used in the planning and architecture design stages, while the checklist and testing guide may serve as a baseline for manual security testing or as a template for automated security tests.
Mobile App Security Testing
The checklist works great as a reference during mobile app security assessments. You can walk through the requirements one-by-one - for more information on each requirement, simply click on the link in the "Testing procedures" column. Or, fill out the checklist at the end of an assessment to ensure completeness.
Security Engineering in the SDLC
Properly defined security requirements are an important part of the Secure SDLC. The MASVS levels can be used along with threat modeling to determine the appropriate set of security controls for a particular mobile app. MASVS V1 also lists requirements pertaining to the architecture and design of the mobile apps, as well as general processes and activities that should be part of the development process.
Mobile App Security Education
The Mobile Security Testing Guide can be used as a standalone learning resource. Its main chapters contain general how-tos and tutorials that cover a variety of topics from mobile OS internals to advanced reverse engineering techniques.
Mobile Security Testing Workshop on the OWASP Summit 2017
During the last few months the Mobile Security Testing Guide has made a lot of progress. As we want to push things forward in order to have a first draft of the guide) at the end of Q2, we will be holding a five days working session during the OWASP Summit 2017 in London. Our ambitious goal is to complete the mobile security testing guide. To achieve this, we’ll need to at least close the 126 “missing content” tickets listed on the project dashboard and produce an estimated 200 book-sized pages of content. This sounds like a lot - however, if we can gather 10 people for this working session, this amounts to 4 pages of content per person/day which is achievable.
The main tasks of the five days workshop are:
- Write original content, such as describing testing processes and writing test cases. - Proofreading and technical editing to improve the overall quality of the MSTG.
Work will be split between working groups based on mobile OS and topic. On top of completing the content, we want to apply a basic level of proof-reading, review and editing to get the guide beta-ready.
In order to be able to schedule work during the summit and create work groups we need to know who will be attending the OWASP Summit and how much time you can/will spend for the mobile workshop. Please add yourself to the list of participants and reach out directly to Sven via Slack.
If you do not have time during the summit but are interested to help, you can start immediately by assigning issues to yourself and creating pull requests. We can also loop you in remotely during the submit.
Let’s work on the testing guide and fix mobile application security!
April 5th, 2017: Mobile App Security Verification Standard Update
Version 0.9.3 of the MASVS is now available for download . This release contains several bug fixes and modifications to security requirements:
* Merged requirements 7.8 and 7.9 into for simplification * Removed Anti-RE controls 8.1 and 8.2 * Updated MSTG links to current master * Section "Environmental Interaction" renamed to "Platform Interaction" * Removed To-dos * Fixed some wording & spelling issues
January 31st, 2017: Mobile App Security Verification Standard v0.9.2 Available For Download
The Mobile App Security Verification Standard (MASVS) has undergone a major revision, including a re-design of the security model and verification levels. We also revised many security requirements to address the multitude of issues raised on GitHub. The result is MASVS v0.9.2, which is now available for download in PDF format.
As the MASVS is nearing maturity, we have decided to freeze the requirements until the Mobile Testing Guide and checklists "catch up" (due to the one-to-one mapping between requirements in the MASVS and MSTG, changes to the requirements make it necessary to update the other documents as well, causing repeated effort). Unless major issues pop up, the current list will therefore remain in place until MASVS/MSTG v1.0, and further changes will be reserved for v1.1 or later releases.
The MASVS is a community effort to establish security requirements for designing, developing and testing secure mobile apps on iOS and Android. Join the OWASP Mobile Security Project Slack Channel to meet the project members! You can sign up for an account here.
January 28th, 2017: Mobile Crackmes and Reversing Tutorials

|
A key goal of the OWASP Mobile Testing Project is to build the ultimate learning resource and reference guide for mobile app reversers. As hands-on hacking is by far the best way to learn, we'd like to link most of the content to practical examples. Starting now, we'll be adding crackmes for Android and iOS to the GitHub repo that will then be used as examples throughout the guide. The goal is to collect enough resources for demonstrating the most important tools and techniques in our guide, plus additional crackmes for practicing. For starters there are three challenges: |
One of these three already has a documented solution in the guide. Tutorials for solving the other two still need to be added.
We Need More Authors and Contributors!
Maybe you have noticed that the reverse engineering sections in the Mobile Testing Guide are incomplete. The reason: We're still in the starting stages and don't have a lot of authors and contributors (in fact, 99% of the reversing content was produced by one guy). We'd love to welcome *you* as a contributor of crackmes, tutorials, writeups, or simply new ideas for this project.
What You Can Do
The OWASP MSTG is an open project and there's a lot of flexibility - it mostly depends on your skill set and willingness to commit your time. That said, the some areas that need help are:
- Solving crackmes and contributing a tutorial to the guide (preferable a technique that's not already documented. Check the TOC first).
- Writing and adding new crackmes along with solutions (should also describe something not already in the guide. Cracking white-boxes, dynamic analysis using an emulator / introspection, etc. etc.).
- General reversing write-ups to describe specific processes and techniques
- Help us figure out resiliency testing processes and obfuscation metrics
The reversing part of the guide consists of the following chapters:
- Tampering and Reverse Engineering - General Overview
- Tampering and Reverse Engineering on Android
- Tampering and Reverse Engineering on iOS
How To Join
Read the author's guide first, and join the OWASP Mobile Security Project Slack Channel, where you'll find all the other project members. You can sign up for an account here.
January 22nd, 2017: Mobile Testing Guide TOC Available
As of now, we'll be auto-generating a table of contents out of the current MSTG master branch. This reflects the current state of the guide, and should make it easier to coordinate work between authors. A short-term goal is to finalize the structure of the guide so we get a clearer picture of what will be included in the final document. Lead authors are encouraged to complete the outline of their respective chapters.
On another note, we still need additional authors to help with all sections of the guide, including mobile operating system overviews, testing processes and techniques, and reverse engineering. Especially iOS authors are in short supply! As usual, ping us on the Slack Channel if you want to contribute.
December 4th, 2016: Call For Authors: The Ultimate Open-Source Mobile App Reverse Engineering Guide
Reverse engineering is an art, and describing every available facet of it would fill a whole library. The sheer range techniques and possible specializations is mind-blowing: One can spend years working on a very specific, isolated sub-problem, such as automating malware analysis or developing novel de-obfuscation methods. For mobile app security testers, it can be challenging to filter through the vast amount of information and build a working methodology. Things become even more problematic when one is tasked to assess apps that are heavily obfuscated and have anti-tampering measures built in.
One of the main goals in the MSTG is to build the ultimate resource for mobile reverse engineers. This includes not only basic static and dynamic analysis, but also advanced de-obfuscation, scripting and automation. Obviously, writing all this content is a lot of work, both in terms of general content and OS-specific how-tos. We're therefore looking for talented authors that want to join the project early on. Topics include the following:
- Basic Hybrid Static/Dynamic Analysis
- Code Injection and Dynamic Instrumentation (Substrate, FRIDA)
- Dynamic Binary Instrumentation (Valgrind, PIE)
- Analysis Frameworks (Metasm / Miasm)
- Symbolic Execution
- DCA and DPA attacks on white-box crypto
- Dynamic analysis frameworks (PANDA / DroidScope,...)
- Anything else we might have missed
What is in for me?
All of this is unpaid, volunteer work. However, depending on your contribution, you will be named in the "lead authors" or "contributors" list, and you'll be able to point to the fact that you co-authored the guide. You'll also be contributing to the field, helping others who are just starting out, and in turn becoming a happier person yourself (reaping the full benefits of your altruism).
Where do I sign up?
First of all, have a look at the existing RE chapters outline:
You'll probably immediately have ideas on how you can contribute. If that's the case, read the author's guide first.
Then contact Bernhard Mueller - ideally directly on the OWASP Mobile Security Project Slack Channel, where you'll find all the other project members. You can sign up for an account here.
How can I participate in your project?
We are searching for additional authors, reviewers and editors. The best way to get started is to browse the existing content. Also, check the project dashboard for a list of open tasks.
Drop a us line on the Slack channel before you start working on a topic. This helps us to keep track of what everyone is doing and prevent conflicts. You can create a Slack account here:
Before you start contributing, please read our brief style guide which contains a few basic writing rules.
If there's something you really want to see in the guide, or you want to suggest an improvement, create an issue issue or ping us on Slack.
Where do you guys need help the most?
There's a lot of areas where you can help out:
- Writing original content, such as describing testing processes and writing test cases. We're all doing this in our spare time, which unfortunately means that things sometimes slow down to a crawl. If you're knowledgeable in some area and have time available, we'd be incredibly thankful to anyone who contributes, even if it's only one or two test cases.
- Reviewing content and giving feedback. The proper channel for questions and feedback is the GitHub issues system of the respective repo, contacting us on OWASP Mobile Security Project Slack Channel is another possibility.
- Developing tools. For example, we still don't have an automated way of generating checklists out of the GitHub repo.
- Contributing to auxiliary projects: The obfuscation metrics project is an auxiliary project that deals with specific forms of control flow and data obfuscation. This project needs experts in advanced obfuscation / de-obfuscation. Please contact us if you have experience in this area.
If I am not a programmer can I participate in your project?
Yes, you can certainly participate in the project if you are not a programmer or technical. The project needs different skills and expertise and different times during its development. Currently, we are looking for researchers, writers, graphic designers, and a project administrator.
I contributed to the original Google Doc, but I'm not credited in the new version of the MSTG?
As we migrated some of the existing content, we did our best to backtrack the original authors and credit them appropriately. We also added a revision history that lists all the authors from old Google Docs. If you are not on that list but feel you should be, please contact Bernhard or Sven and they'll fix it. Or better yet, re-join the author's team and start contributing to the new guide.
Contributors
The Mobile Security Testing Guide was initiated by Milan Singh Thakur in 2015. The original document was hosted on Google Drive. Guide development was moved to GitHub in October 2016. Below is the full list of contributors for each revision.
MSTG in its current form
Authors:
- Bernhard Mueller
- Sven Schleier
Contributors:
- Abdessamad Temmar
- Francesco Stillavato
- Pawel Rzepa
- Gerhard Wagner
- Daniel Ramirez Martin
- Jin Kung Ong
- Alexander Antukh
- Claudia André
- Ryan Teoh
- Prathan Phongthiproek
- Jeroen Willemsen
- Romuald Szkudlarek
- Luander Ribeiro
- Pishu Mahtani
- Sebastian Banescu
- Prabhant Singh
- Stephen Corbiaux
- Ali Yazdani
Reviewers:
MSTG "Beta 2" on Google Drive
Authors:
- Mirza Ali
- Stephen Corbiaux
- Ryan Dewhurst
- Mohammad Hamed Dadpour
- David Fern
- Ali Yazdani
- Bao Lee
- Anto Joseph
- Nutan Kumar Panda
- Rahil Parikh
- Julian Schütte
- Abhinav Sejpal
- Anant Shrivastava
- Pragati Singh
- Milan Singh Thakur
- Stephanie Vanroelen
- Gerhard Wagner
Reviewers:
- Andrew Muller
- Jonathan Carter
- Stephanie Vanroelen
- Milan Singh Thakur
MSTG "Beta 1" on Google Drive
Authors:
- Mirza Ali
- Mohammad Hamed Dadpour
- David Fern
- Rahil Parikh
- Abhinav Sejpal
- Pragati Singh
- Milan Singh Thakur
Reviewers:
- Andrew Muller
- Jonathan Carter
Top Contributors:
- Jim Manico
- Yair Amit
- Amin Lalji
- OWASP Mobile Team