This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Projects/OWASP Mobile Security Project -2015 Scratchpad"
Andipannell (talk | contribs) (→Audience-Specific Guidance) |
Razorpointer (talk | contribs) (→Overview Text) |
||
| Line 144: | Line 144: | ||
| − | Owner(s): Milan Singh Thakur | + | Owner(s): Milan Singh Thakur, Amin Lalji |
===Prominent Characteristics=== | ===Prominent Characteristics=== | ||
Revision as of 14:15, 7 April 2015
This is just a place to gather some ideas for the 2015 reworking of the Mobile Top Ten. It's totally unofficial open musings about truth, beauty, and justice.
- 1 What is It?
- 2 Who is it For?
- 3 Comments on Submitted Data
- 4 Other Questions
- 5 Conclusions Drawn From Data
- 6 OWASP Category Elements
- 7 "Test Drive" Category Element
- 8 Top Ten Scratchpad
- 8.1 M1: Weak Server Side Controls
- 8.2 M2: Insecure Data Storage
- 8.3 M3: Insufficient Transport Layer Protection
- 8.4 M4: Unintended Data Leakage
- 8.5 M5: Poor Authorization and Authentication
- 8.6 M6: Broken Cryptography
- 8.7 M7: Client Side Injection
- 8.8 M8: Security Decisions Via Untrusted Inputs
- 8.9 M9: Improper Session Handling
- 8.10 M10: Lack of Binary Protections
What is It?
This is the "Mobile Top Ten" what? It's the top 10 "stuff people tend to screw up", but here are some important questions.
- Business risk or technical risk? The business risk would be something like "intellectual property unprotected" or "customer data exposed." A technical risk would be something like "data stored in plain text files."
- Root cause, or final impact? Often root causes are things like not encrypting when we should. Final impact is stuff like unintended data leaks. The problem is that some of these things are overlapping. Not every lack of crypto is a data leak, but many are.
- What threats are in scope? There are apps that simply do not care about protecting from malware, jailbreaking, etc. Think Yelp: it's just restaurant reviews. No financial impact, no reason to care about many client-side attacks. Plenty of apps do care about client-side attacks. E.g., banking, communications, health data. Many items hinge on whether or not you care about client side attacks. How do we capture this?
- If you care about client-side attacks, then failing to encrypt stuff is basically a data leakage.
- If you don't care about client-side attacks, then failing to encrypt stuff is kinda "gee you should do that".
- If you care about client-side attacks, there are probably some platform features that are not sufficient as-is: the app sandbox, etc. You probably want to be putting your own additional layer of encryptiong / protection, etc.
- If you don't care about client-side attacks, then you simply need to be using the standard APIs (keychain, app data storage, etc.) in the standard supported ways.
Who is it For?
Do we intend this to be a tool that infosec / appsec people use? Do we intend lay people to make use of it? (e.g., developers and non-mobile IT security people) What does the target audience need to get from it?
(Paco's opinion) We need to have a narrative: If you found functionality that does X, it is probably in bucket A, unless it is also doing (or not doing) Y, in which case that's bucket B.
Comments on Submitted Data
General
(Jason) By looking at some data sets it becomes clear there is a doctrine that some consultancies use to do mobile testing. Some did not contribute m1 data, because they consider mobile security client-only. The same applied to m10. In addition, a couple of datasets used CWE IDs. These were harder to parse because generic CWE's do not specify if the vuln is client or server (and in a lot of these cases the vuln could be either). As Paco stated, code quality, source level findings are hard to categorize as well.
BugCrowd
I see “storing passwords in the clear” as a very common finding among their data. It gets classifed as M5 poor authentication, M2 insecure data storage, M4 data leakage, and sometimes M6 (broken crypto).
I see “storing session tokens insecurely” as a common finding. It is getting classified as M9 (session handling) and M2 (insecure data storage). I wonder openly whether passwords and session tokens are really that different.
We see a lot of caching of non-password, non-session data. Some of it is done explicitly by the app, some of it is done by the mobile OS through snapshotting, backups, etc. Sometimes it is classified as “data leakage” (M4) and sometimes as insecure storage (M2). And what is interesting is that some of it is the result of the OS and some is the result of the app. Do we want to make that distinction in the T10?
MetaIntelli
They only have 18 distinct things they report on, though they have 111,000 data points. Two of the 18 things are double-counted. They appear to be categorised in both M3 and another one.
Other Questions
Communications issues are a problem a lot. But TLS and crypto are tightly coupled. “Communications issues" includes certificate pinning, weak TLS ciphers, improper cert validation, HTTP and plaintext protocols, and more. There’s a lot of overlap with “broken crypto” like using Base64 instead of encryption, hard coded keys/passwords, weak hash algorithms, and so on. How do we tease out “crypto” issues from “communications” issues from “insecure storage” issues?
I can imagine a heuristic like this:
- did you use crypto where you were supposed to, but the crypto primitive you chose wasn’t appropriate for the task? That’s broken crypto.
- Did you omit crypto entirely when you should have used it? That’s insecure comms or insecure storage.
Some findings are deeply mobile (e.g., intent hijacking, keychain issues, jailbreak/root detection, etc.). They’re really tied to their respective platforms. Is that a problem for us? Does it matter?
Conclusions Drawn From Data
These are conclusions proposed from the 2014 data.
At Least One New Category Is Needed
((Paco)) The "Other" category is not the least popular category. It's more popular, by an order of magnitude, than several others. This tells me that if we had a better category that captured "other" findings, it would be a benefit to the users of the top 10.
The Bottom 5 Categories account for 25% Or Less
The least popular 5 items are (where "1" is the least popular and "5" is 5th least popular or 6th most popular):
- M8: Security Decisions Via Untrusted Inputs
- M7: Client Side Injection
- M9: Improper Session Handling
- M6: Broken Cryptography
- M1: Weak Server Side Controls
Combined with the fact that the 3rd or 4th most popular category is "Other", this suggests that 2 or 3 of these are, in fact, not in the "top ten". They may be, for example, 11 and 12 or even higher.
The Existing Buckets are Hard To Use
A few contributors tried to categorise their findings into the existing MT10. When they did, they showed symptoms of difficulty. Some examples in the table below show how MetaIntelli flagged findings in two different categories, and BugCrowd flagged the same kind of finding in 3 different categories. This suggests that the existing MT10 is not clear enough about where these issues belong.
| Description | Contributor | Categories |
|---|---|---|
| The app is not verifying hostname, certificate matching and validity when doing SSL secure connections. | MetaIntelli | M3 and M9 |
| Contains URLs with not valid SSL certificates and/or chain of trust | MetaIntelli | M3 and M5 |
| Authentication cookies stored in cleartext in sqlite database | BugCrowd | M9 - Improper Session Handling |
| Blackberry app stores credentials in plaintext | BugCrowd | M2 - Insecure Data Storage |
| Credentials and sensitive information not secured on Windows Phone app | BugCrowd | M5 - Poor Authorization and Authentication |
Some Topics that Show Up But Are Hard To Place
There are a few things that show up in the contributed data that do not have a good category to go into.
Code Level Findings
If someone is doing bad C coding (e.g., strcpy() and similar), there is no good bucket for that. Likewise, misusing the platform APIs (e.g., Android, iOS, etc.) is not well covered. It's hard to place violations of platform best practices (e.g., with intents and broadcasts and so on).
Most of the Android developers use "printStackTrace" in their code, which is a bad practice. Even the Android APK is released in DEBUG mode.
OWASP Category Elements
This section explores the critical elements that must be included within all OWASP Mobile Top Ten 2015 categories. Each element is listed below along with a brief description of the appropriate content. The goal is to "test drive" this list of required elements with a sample, non-commital category to verify that the elements adequately cover what is needed within each of the OWASP Mobile Top Ten 2015 categories. Each of these elements has been initially based off the Google Hangout meeting held on April 1 2015.
Label (generic and audience-specific labels)
This element is a unique identifier for the bucket of issues that belong together. In the OWASP Mobile Top Ten 2015 Survey, we found that there were many different audiences that may use the OWASP Mobile Top Ten 2015 for different purposes. As always, there needs to be a generic label that uniquely identifies each bucket of issues. However, there should also be additional labels for the same category that are audience-specific to make it easier for different audiences to identify the category they are looking for. These additional labels will help clarify and differentiate the categories.
Overview Text
This element is a generic education piece (100-200 words) around the nature of the category. It should describe the nature of the category as it relates to the different audiences (e.g., penetration testers; software engineers). It should include external references and educational links to other sources around the nature of the problem.
Prominent Characteristics
This element eliminates any uncertainty or ambiguity that may result from vagueness / broadness in the category labels. It should include "headline vulnerabilities" that made it into the media and help each audience get a "gut feel" for what belongs to this category. In the 2014 list, we found that there were many instances where the same vulnerabilities were spread across many different categories. Hence, the need for this additional element along with a strive towards better categorisation.
Risk
This element helps clarify how critical the category of issues is from both a business and technical perspective. During the meeting of April 1 2015, it was proposed that the CVSS classification scheme may be used here as a way of helping guide the audiences in prioritisation of the fixing of the issues.
Examples
This element gives coding-specific examples, CVE vulnerabilities and newsworthy events that fall into this category. This element will help clarify to the difference audiences what fits into this category.
Audience Specific Guidance
This element gives practical advice and guidance for category remediation that is relevant to each audience (100-200 words). Each audience may approach the issue of remediation from very different perspectives. For example, an auditor may simply want to know more about whether or not remediation is appropriate. Meanwhile, a software engineer may want to have coding-specific advice. Each audience's concerns must be addressed in this element.
"Test Drive" Category Element
Here, we are testing a particular category to see whether or not the proposed elements for each category are adequate to address each audience's needs. It is important to note that this is a sample category and is not a formal commitment to any final category in the OWASP Mobile Top Ten 2015. It is strictly meant for testing purposes. Members who would like to 'own' particular elements in the category below should 'sign up' and add content where appropriate.
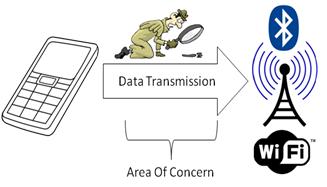
Insecure Data Transmission
Generic Label
Owner(s): Jonathan Carter
Audience-Specific Labels
Owner(s): Jonathan Carter
Overview Text
This category focuses on the many available communication channels in the mobile environment and the secure transmission of data through them. If your application is using Wi-Fi, WiFi-direct, Bluetooth, Infra-red, RFIDs, POS devices (with NFC Tags); then this category provides guidance in securing data while in transit. Included but not limited to are plaintext transmission of sensitive data, insufficient authentication of encrypted channel endpoints, insufficient regard to failures in building a properly encrypted channel, poor choice of security mechanisms over distinct networks, etc.
Additionaly, this category applies in the same way to secure data transmission in the Internet Of Things (IoT).
Owner(s): Milan Singh Thakur, Amin Lalji
Prominent Characteristics
Owner(s): David Fern
The key differentiator of this vulnerability is that it is concerned about unencrypted or improperly encrypted data being stolen during transmission, not on the device but through the airwaves.
Insecure Data Transmission should not be confused with others in the top 10 such as:
M3: Insufficient Transport Layer Protection – I DO NOT SEE ANT DIFFERENCE
M4: Unintended Data Leakage – Unintended data leakage is a result of insecure data transmission. Once data has been stolen and interpreted it may contain information that is valuable to attackers (leaked).
M6: Broken Cryptography – While broken cryptography does relate to data that has been improperly encrypted, and it may be an input or causes of insecure data transmission, it focuses on the encryption process/technique itself on the device transmitting the data.
Risk
Confidential and sensitive data residing on the mobile devices if not fully SSL encrypted during transmission is highly susceptible to eavesdropping. As majority of wireless, mobile devices have capability to use and switch to various home Wifi and public unsecured Wifi. This could be disastrous while giving attackers a glimpse of your personal, non-shareable information which can lead to identity theft and social engineering attacks. Similarly, it applies to those mobile apps also where data transmission is not fully SSL encrypted and failed to perform a Valid SSL Certificate check. Additionally, this might lead further to man-in-the-middle attacks.
Even if the application uses encryption and the device is connected to a public WiFi, an attacker can easily capture all Wireless traffic (as in War-driving). Then attacker can perform offline decryption and possibly have all your sensitive data. Consider the situation where your application server uses TLS1.0/SSLv3. You think it is secure? Nope, it is highly vulnerable to attacks like CRIME, POODLE and Handshake Re-negotiation.
Owner(s): Rajvinder Singh, Milan Singh Thakur
Examples
Owner(s): Adam Kliarsky
Audience-Specific Guidance
Owner(s): Andi Pannell
From both a development and auditing stance, the easiest way to test this is to insert a proxy (such as burp) between the device running the mobile app and the wifi connection. Looking for data being transferred over plain text, as well as identifying weak procotols (SSLv2, SSLv3) and ciphers (RC4, MD5) being used to transmit data.
Top Ten Scratchpad
Here's some top-ten possible categories. This is a wiki. Edit them. Change them. Leave comments. Mark it up.
M1: Weak Server Side Controls
Stuff
M2: Insecure Data Storage
(Jason) As i look through the data I think more and more about how m2 and m4 might be combined.
M3: Insufficient Transport Layer Protection
Stuff
M4: Unintended Data Leakage
Stuff
M5: Poor Authorization and Authentication
Stuff
M6: Broken Cryptography
Stuff
M7: Client Side Injection
Stuff
M8: Security Decisions Via Untrusted Inputs
Stuff
M9: Improper Session Handling
Stuff
M10: Lack of Binary Protections
(Jason) Regarding m10 - Several submissions reported m10 vulns. Unfortunately some were types of services such as binary reputation scanners, that do not have the ability to check for dynamic or code level findings. In order to fix this i recommend a name change or re-working of this category. I want to separate out the delineation of Anti-exploit vs Code Obfuscation/Anti-reversing. Must talk to group about this.