This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Mobile Top 10 2012-M2"
Jason Haddix (talk | contribs) (Created page with "{{Top_10_2010:SummaryTableHeaderBeginTemplate}} {{Top_10_2010:SummaryTableValue-1-Template|Exploitability|EASY}} {{Top_10_2010:SummaryTableValue-2-Template|Prevalence|COMMON}}...") |
Jason Haddix (talk | contribs) |
||
| Line 13: | Line 13: | ||
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=1|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=1|risk=2}} | ||
| − | + | The M2 category is one that is always in heavy debate. It encompasses almost everything that a mobile application can do badly that does not take place on the phone. Which is exactly the argument… should it be listed at all? Don’t we have Top Ten lists for Web Applications? Don’t we have one for cloud too? | |
| + | |||
| + | In fact, we do. If we could be altogether sure that everyone who wanted information on mobile security also stopped by those projects… it would be a perfect world. Unfortunately, after two rounds of data collection from some of the world’s top assessment teams, we find that server side issues are so prevalent in mobile applications that we cannot ignore them in the Risk listing. M2 is only .52% lower in prevalence than M1 (Insecure Data Storage) and almost always trumps M1 findings in terms of overall risk. While not statistically validated we feel that several factors lead to bad mobile application server code (and on a larger scale mobile insecurity in general): | ||
| + | |||
| + | * Rush to market | ||
| + | * Lack of security knowledge because of the new-ness of the languages | ||
| + | * Easy access to frameworks that don’t prioritize security | ||
| + | * Higher than average outsourced development | ||
| + | * Lower security budgets for mobile applications | ||
| + | * Assumption that the mobile OS takes full responsibility for security | ||
| + | * Weakness due to cross-platform development and compilation | ||
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=2|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=2|risk=2}} | ||
| − | + | Secure coding and configuration practices must be used on server-side of the mobile application. For specific vulnerability information refer to the OWASP Web Top Ten or Cloud top Ten sections. We will try and link all things referenced here to those projects and possibly the OWASP Testing guide. | |
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=3|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=3|risk=2}} | ||
| − | + | ||
| + | === The Worst Offenders === | ||
| + | |||
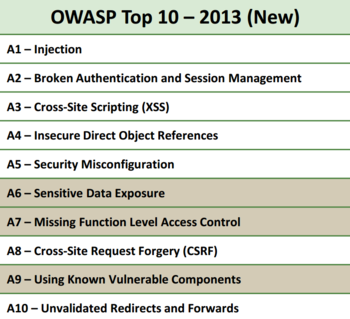
| + | If you look below, you can see that there is a ton of surface area to cover when thinking about M2: | ||
| + | |||
| + | |||
| + | [[File:CloudTT_thum.png|border|350px]][[File:WebTT_thumb.png|border|350px]] | ||
| + | |||
| + | |||
| + | While we cannot go over all of these, what we can do is list vulnerability types that we see most often within M2: | ||
| + | |||
| + | |||
| + | ;Poor web services hardening | ||
| + | : Logic flaws | ||
| + | : Weak Authentication | ||
| + | : Weak or no session management | ||
| + | : Session fixation | ||
| + | : Sensitive data transmitted using GET method | ||
| + | |||
| + | |||
| + | ; Insecure web server configurations | ||
| + | : Default content | ||
| + | : Administrative interfaces | ||
| + | |||
| + | |||
| + | ; Injection (SQL, XSS, Command) on both web services and mobile-enabled websites | ||
| + | |||
| + | ; Authentication flaws | ||
| + | |||
| + | ; Session Management flaws | ||
| + | |||
| + | ; Access control vulnerabilities | ||
| + | |||
| + | ; Local and Remote File Includes | ||
| + | |||
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=4|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=4|risk=2}} | ||
References | References | ||
Revision as of 19:52, 22 January 2014
| Threat Agents | Attack Vectors | Security Weakness | Technical Impacts | Business Impacts | |
|---|---|---|---|---|---|
| Application Specific | Exploitability EASY |
Prevalence COMMON |
Detectability EASY |
Impact SEVERE |
Application / Business Specific |
| Threat Description | Attack Vector Description | Security Weakness Description | Technical Impacts | Business Impacts | |
The M2 category is one that is always in heavy debate. It encompasses almost everything that a mobile application can do badly that does not take place on the phone. Which is exactly the argument… should it be listed at all? Don’t we have Top Ten lists for Web Applications? Don’t we have one for cloud too?
In fact, we do. If we could be altogether sure that everyone who wanted information on mobile security also stopped by those projects… it would be a perfect world. Unfortunately, after two rounds of data collection from some of the world’s top assessment teams, we find that server side issues are so prevalent in mobile applications that we cannot ignore them in the Risk listing. M2 is only .52% lower in prevalence than M1 (Insecure Data Storage) and almost always trumps M1 findings in terms of overall risk. While not statistically validated we feel that several factors lead to bad mobile application server code (and on a larger scale mobile insecurity in general):
- Rush to market
- Lack of security knowledge because of the new-ness of the languages
- Easy access to frameworks that don’t prioritize security
- Higher than average outsourced development
- Lower security budgets for mobile applications
- Assumption that the mobile OS takes full responsibility for security
- Weakness due to cross-platform development and compilation
Secure coding and configuration practices must be used on server-side of the mobile application. For specific vulnerability information refer to the OWASP Web Top Ten or Cloud top Ten sections. We will try and link all things referenced here to those projects and possibly the OWASP Testing guide.
The Worst Offenders
If you look below, you can see that there is a ton of surface area to cover when thinking about M2:
While we cannot go over all of these, what we can do is list vulnerability types that we see most often within M2:
- Poor web services hardening
- Logic flaws
- Weak Authentication
- Weak or no session management
- Session fixation
- Sensitive data transmitted using GET method
- Insecure web server configurations
- Default content
- Administrative interfaces
- Injection (SQL, XSS, Command) on both web services and mobile-enabled websites
- Authentication flaws
- Session Management flaws
- Access control vulnerabilities
- Local and Remote File Includes
References