This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP AW00T"
Nitin arya (talk | contribs) |
Nitin arya (talk | contribs) |
||
| Line 105: | Line 105: | ||
</table> | </table> | ||
| + | <table border="0" cellspacing="0" cellpadding="0" bgcolor="#EBFFE9"> | ||
| + | <tr> | ||
| + | <td width="624" valign="top"><p>004018E4 > \B8 25304000 MOV EAX,Trojan2.00403025<br /> | ||
| + | 004018E9 . 8030 0F XOR BYTE PTR DS:[EAX],0F<br /> | ||
| + | 004018EC . B8 00000000 MOV EAX,0<br /> | ||
| + | 004018F1 . 55 PUSH EBP<br /> | ||
| + | 004018F2 . 8BEC MOV EBP,ESP<br /> | ||
| + | 004018F4 . 83EC 08 SUB ESP,8<br /> | ||
| + | 004018F7 . C70424 01000000 MOV DWORD PTR SS:[ESP],1<br /> | ||
| + | 004018FE .^ E9 2AF9FFFF JMP Trojan2.0040122D</p></td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | |||
| + | And made the olly to copy the changes to an executable and then save the file. The final result was as shown . | ||
| + | |||
| + | [[File:stub4.png]] | ||
| + | [[File:stub5.png]] | ||
=Project About= | =Project About= | ||
Revision as of 13:36, 20 December 2012
Media:Bypassingantivirus.docx=Main= The Project is under development .

Initially the project was focused in displaying raw code and methodologies used in bypassing AV but the project is now going up a new level.
I have decided to develop a functional program that will bypass antivirus on the go with advanced polymorphic and Human like intelligence techniques.
Just for starters Demonstration. This is something that i did in 2008 so you can have a look how it starts!
1. Bypassing Antivirus a. Objective
The objective of this exercise was to make the trojan.exe undetectable from the AVG antivirus and we were free to use any stub and the original functionality of the file must be regained.
b. Case one implementation --------> (Failure)
Case one (Failure)
Result Failure AVG detected both file
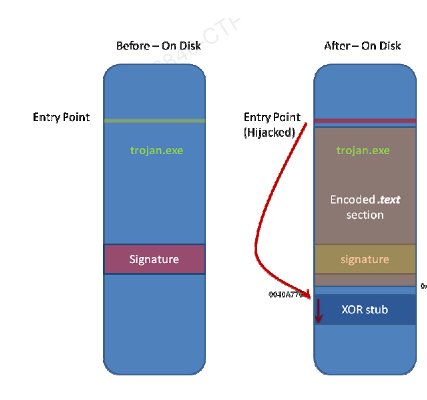
Case one was based on the assumption that the signature is available on the .text section of our file but as soon i implemented it the AVG detected the file provided with the XOR stub as well.
The .text section of the program was encoded. We used Lord PE to make the text section writable.
Encode from here to here 00401225 90 NOP
To 004018DF. Initial instructions were:-
00401220 T> $ 55 PUSH EBP |
I used a XOR stub looks like this:-
004018D8 > \B8 25124000 MOV EAX,Trojanch.00401225 004018DD > 8030 0F XOR BYTE PTR DS:[EAX],0F004018F3 00 DB 00 |
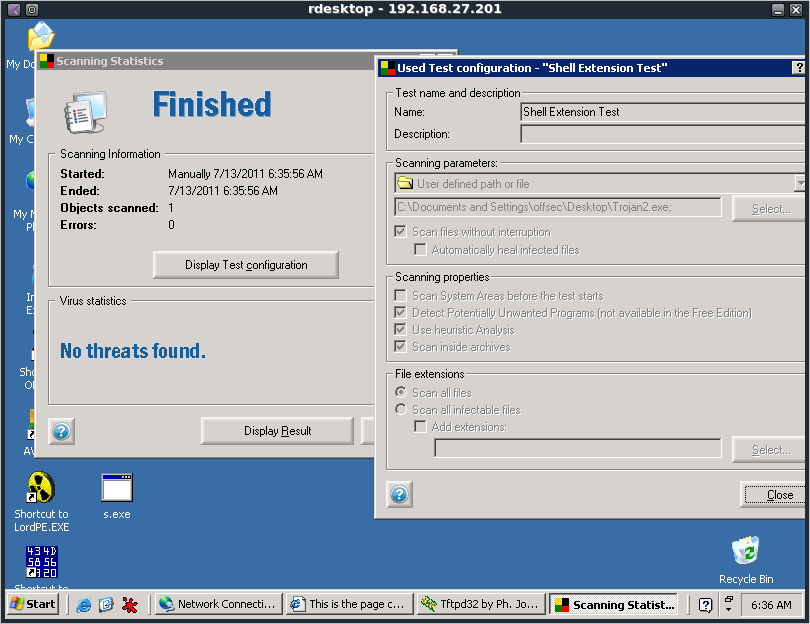
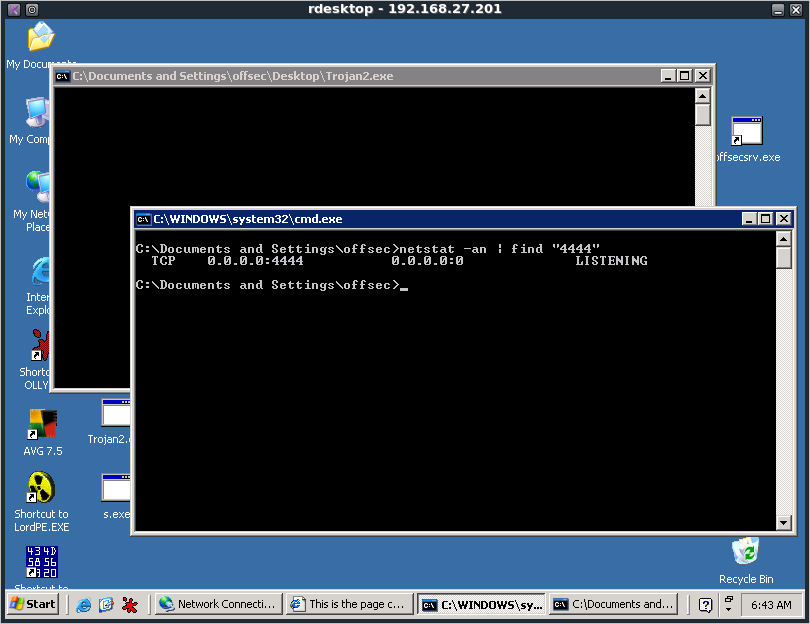
The original functionality was regained but AVG was still detecting the malicious file. So a secondary approach was required as shown in case two.
d. Hunting Antivirus Signature c. Case Two (Success)
Since the case one was based on our assumption that the Antivirus signature is based in the .text section of our file and thus we failed.
So our second approach was to dig out the signature or use the stub on all other sections as well but the latter idea does not sound so good as we have to deal with a lot of cases and program details in that case so we will be now hunting for the signature that the poor AVG antivirus is using.
Our approach will be as follows:-
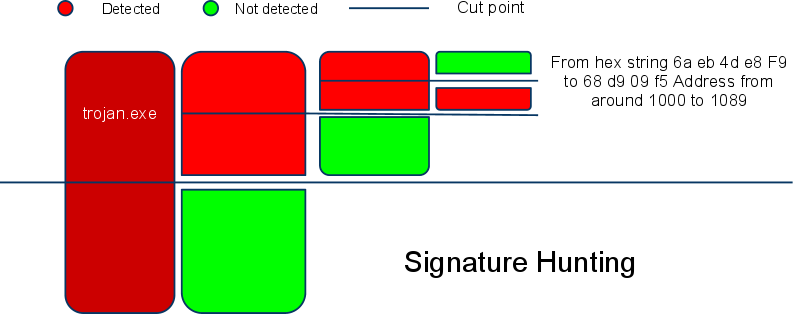
We however are not concerned with the complete signature or the length and address it is associated with what we need is a single byte change in the signature of the file and making it undetectable from the antivirus. We used the hexedit to cut the file and then scanning it with the AVG Antivirus to check the respective files and check up to the minimal point up to which it detects and thus we can easily extract the signature from it. The signature was present in the .rdata section of the file. In hexedit if you see it starts from 1000 address or search it From hex string
This is the signature that the AVG is detecting in the program. What we noticed is an instruction xor eax,eax which can easily be replaced with the mov eax,0 and on its implementation the bytes around the signature will be changed and the file will be undetectable from the AVG but the problem with this solution is that we have to add some extra bytes because of the different instruction size of these instructions the latter being larger Rather than using the above approach i used a simple method as mentioned in case one the XOR stub and used it on the address of the 31 05 (xor eax,eax) .We could have used any simple stub like just add a byte to it or subtract from it but we have to again save the file by editing and adding the opposite instruction like if we use add than after changed instruction change it to subtraction and vice versa to obtain the original file in run time. So we are using a XOR stub on the 31 05(xor eax,eax) instruction .
Implementation stub
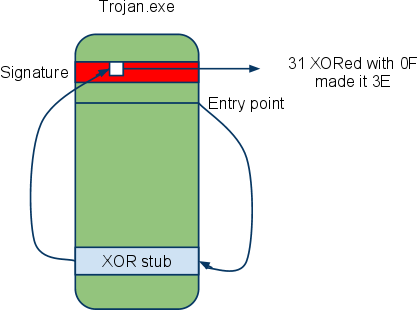
As clearly shown in diagram above the XORed byte 3E was regained when the program is run as XORing it again makes it 31 again and the original instruction 31 C0 is regained. We need to make the .rdata section writable with LORD PE first but for safety sake i made all the first four sections writable.
Firstly the initial instructions were copied and a jump to 004018e4 is done.
00401220 T> $ 55 PUSH EBP 00401221 . 89E5 MOV EBP,ESP00401233 . E8 C8FEFFFF CALL Trojan.00401100 |
004018E4 > \B8 25304000 MOV EAX,Trojan2.00403025 004018E9 . 8030 0F XOR BYTE PTR DS:[EAX],0F004018FE .^ E9 2AF9FFFF JMP Trojan2.0040122D |
And made the olly to copy the changes to an executable and then save the file. The final result was as shown .
Project About
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||