This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP China Summit 2010"
Weilin Zhong (talk | contribs) (→Conference Committee: Added Eric) |
(→OWASP China Summit 2010 - Beijing China) |
||
| (86 intermediate revisions by 4 users not shown) | |||
| Line 9: | Line 9: | ||
'''Press Release: [http://www.owasp.org/images/d/d8/OWASP_China_Summit_2010_Announcement.pdf OWASP China Summit 2010 Announcement]''' | '''Press Release: [http://www.owasp.org/images/d/d8/OWASP_China_Summit_2010_Announcement.pdf OWASP China Summit 2010 Announcement]''' | ||
| + | |||
| + | [[File:OWASP_CHINA_01.jpg]] | ||
| + | [[File:OWASP_CHINA_02.jpg]] | ||
| + | [[File:OWASP_CHINA_03.jpg]] | ||
| + | [[File:OWASP_CHINA_04.jpg]] | ||
| + | |||
====中文(Chinese)==== | ====中文(Chinese)==== | ||
| Line 32: | Line 38: | ||
For student discount, attendees must present proof of enrollment when picking up your badge. | For student discount, attendees must present proof of enrollment when picking up your badge. | ||
| − | Questions, please contact: [mailto: | + | Questions, please contact: [mailto:weilin.zhong@owasp.org OWASP China Summit 2010 Organization Team] |
| + | |||
| + | ==== Training: Oct 20 - 21 ==== | ||
| + | ---- | ||
| + | ===== Training Agenda ===== | ||
| + | {| border="0" align="center" style="width: 80%;" | ||
| + | |- | ||
| + | | align="center" colspan="6" style="background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | '''Training Oct 20 - Oct 21''' | ||
| + | |||
| + | |- | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | Time | ||
| + | | style="width: 20%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Trainer | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Topic | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Language | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | Price (Before Oct.10) | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | Price (After Oct.10) | ||
| + | |- | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | AM Oct 20 | ||
| + | | style="width: 20%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Yuezhong Bao, Microsoft | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Secure Development Lifecycle | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1000 ($150) | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1500 ($230) | ||
| + | |- | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | PM Oct 20 | ||
| + | | style="width: 20%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Benson Wu, Armorize | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Security Code Review | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1000 ($150) | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1500 ($230) | ||
| + | |- | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | AM Oct 21 | ||
| + | | style="width: 20%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Xin Fang, VulnHunt | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Security Testing | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1000 ($150) | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1500 ($230) | ||
| + | |- | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | PM Oct 21 | ||
| + | | style="width: 20%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Aaron, DBAppSecurity | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Security Testing | ||
| + | | style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1000 ($150) | ||
| + | | style="width: 15%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | RMB 1500 ($230) | ||
| + | |} | ||
| + | |||
| + | ---- | ||
| − | ==== | + | ===== Enrollment & Questions: ===== |
| + | * Ivy: 13510601178, [email protected] | ||
| + | * Rip: 13699898080, [email protected] | ||
| − | === | + | ---- |
| + | ===== Trainer Bios & Course Abstracts ===== | ||
| + | * More details, please see the [http://www.owasp.org.cn/index.php?option=com_content&view=article&id=57&Itemid=83 summit Chinese website (详情请见峰会中文网站)]. | ||
| − | + | ---- | |
| − | |||
| − | ==== | + | ==== Agenda: Oct 22 ==== |
| + | [http://www.owasp.org.cn/index.php?option=com_content&view=article&id=56&Itemid=82 '''Detailed Agenda in Chinese (详细会议日程)''']. | ||
| − | === | + | {| border="0" align="center" style="width: 80%;" |
| + | |- | ||
| + | | align="center" colspan="4" style="background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | '''Conference Day 1 - Oct 22, 2010 Tentative''' | ||
| − | + | |- | |
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | Time | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Speaker | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Presentation | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Language | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 08:30-09:00 | ||
| + | | align="center" colspan="3" style="width: 90%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Registration and Networking | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 09:00-09:10 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/index.php/China-Mainland Rip Torn], OWASP China Chapter and [http://www.owasp.org/index.php/User:Brennan Tom Brennan] OWASP Board | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Opening Statement: [http://www.owasp.org/images/9/97/Brennan-Keynote.pdf Welcome to OWASP China Summit 2010] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese/English | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 09:10-10:00 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Keynote: [http://www.owasp.org/index.php/Chenxi_Wang,_Ph.D._(Forrester_Research) Chenxi Wang], PhD, Forrester Research | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | [[#Application Security Market Trend 应用安全市场动态]] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 10:10-10:40 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/index.php/User:Weilin_Zhong Weilin Zhong], OWASP | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | [http://www.owasp.org/index.php/OWASPTop10-2010-PressRelease OWASP TOP 10] | ||
| + | [http://www.owasp.org/images/a/a7/OWASP_Top_10_PR_Chinese.pdf OWASP十大风险] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 10:50-11:20 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/index.php/Frank_Yuan_Fan,_OWASP_China_Chapter Frank Fan], DBAppSecurity | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Web Attack and Defense Trends | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 11:30-12:00 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/images/e/e4/WongOnnChee_Biodata.pdf Wong Onn Chee], [http://www.owasp.org/index.php/Singapore OWASP Singapore Chapter] | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | [[#Outbound Monitoring of Web Servers: a Forgotten Child in Information Security?]] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese/English | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 12:00-13:30 | ||
| + | | align="center" colspan="3" style="width: 90%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Lunch Break | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 13:30-14:10 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/images/5/58/Bio_-_Kenny_Lee_2010.pdf Kenny Lee], Verizon Business | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | [[#2010 Data Breach Investigation Report]] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | English with real-time Chinese translation | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 14:20-15:00 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/index.php/User:Pravir_Chandra Pravir Chandra], OWASP | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | [[#Building an effective SSA program in measurable iterations]] | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | English with real-time Chinese translation | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 15:10-15:40 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | [http://www.owasp.org/images/8/81/BioGaoWenInfoSec.pdf Helen Gao], [http://www.owasp.org/index.php/Long_Island OWASP Long Island Chapter] | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | OWASP and OWASP Projects | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(123, 138, 189);" | 16:00-17:00 | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(188, 133, 122);" | Panel | ||
| + | | align="center" style="width: 40%; background: none repeat scroll 0% 0% rgb(153, 255, 153);" | Round Table: Web App Security - State of Art | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(92, 121, 187);" | Chinese | ||
| + | |} | ||
| − | + | == Application Security Market Trend 应用安全市场动态 == | |
| + | =====Chenxi Wang, PhD===== | ||
| + | 应用安全是很多企业安全部门的重要运行目标。在这个报告中我们将分析全球应用安全市场动态,并看一下世界的一些领先机构是怎样在内部推广和运行应用安全产品。我们将分析一些金融界和保险行业的成功案例 ,看一下这些公司是怎样把应用安全产品分门别类融进他们的日常运行程序,并怎样克服运行中遇到的困难。最后我们还将讨论应用安全产品的发展和研究趋势。 | ||
| + | == Outbound Monitoring of Web Servers: a Forgotten Child in Information Security? == | ||
| + | ===== Wong Onn Chee ===== | ||
| + | Outbound monitoring of enterprise web servers is an oft-neglected aspect in the overall security of an enterprise web infrastructure.When outbound monitoring is missing, risks from information leakage and transmission of malware are ever present. Onn Chee will walk through the most common causes of information leakage and malware transmission from web servers. Anonymised case studies of major US and Chinese organisations will be presented for the audience to have a better understanding. | ||
| + | == 2010 Data Breach Investigation Report == | ||
| + | ===== Kenny Lee ===== | ||
| + | *[http://www.owasp.org/images/c/c1/201008_DBIR_Executive_Summary_CHT_Final.pdf Executive Summary in Chinese (中文摘要)] | ||
| + | This presentation is based on the Verizon Business Data Breach Investigations Report1 (DBIR) and will be delivered by Kenny Lee, one of the contributors of the report. The DBIR is a collaborative effort between the United States Secret Service Cyber Intelligence Section and Verizon Business to collect and analyse what we believe to be the world’s largest study of data breaches consisting of over 900 cases and 900 million compromised records across six years of first hand forensic investigations. | ||
| + | We have learned a great deal from this journey and we’re glad to have the opportunity to share these findings with you. As always, our goal is that the data and analysis presented in this report prove helpful to the planning and security efforts of the audience. Many of the lessons learnt from this study strongly indicated the need for improvements in web application security. Data breaches are often a series of simple oversights that culminate in a significant event where huge amounts of data are stolen. We will discuss the most common issues through the use of statistics, war stories and case studies. Key recommendations will be discussed that we believe will help your organisation not be the next victim of a data breach. | ||
| + | More information can be found at [http://www.verizonbusiness.com/databreach/ Verizon Business website]. | ||
| − | + | == Building an effective SSA program in measurable iterations == | |
| − | + | ===== Pravir Chandra ===== | |
| − | + | Integrating security activities into the software development process remains a challenge for most organizations despite the existence of several secure SDLC models. We've learned from experience that the hard questions of "what", "when", and "how much" require answers customized to each organization and there are no simple, one-size-fits-all answers. | |
| − | + | To help organizations find their own answers, this session will introduce the Open Software Assurance Maturity Model (OpenSAMM), a flexible framework for building a balanced software security assurance (SSA) program. Using the framework, attendees will learn how to self-assess their security activities and use roadmap templates to improve in small and measurable iterations. We'll also talk about several real-world case studies that demonstrate the framework in action. Time allowing, additional case studies will also be discussed. OpenSAMM is an open a free project and has recently been donated to the Open Web Application Security Project (OWASP) Foundation. For more information on OpenSAMM, visit http://www.opensamm.org/. | |
| − | + | ==== Sponsors ==== | |
| − | + | ---- | |
| − | + | === Diamond Sponsors: === | |
| − | + | [http://www.dbappsecurity.com.cn/ http://www.owasp.org/images/2/27/Dbappsecurity_logo.gif] 安恒信息 [http://www.armorize.com https://www.owasp.org/images/9/98/Armorize.png] | |
| − | + | ---- | |
| − | |||
| − | |||
| − | + | === Platinum Sponsors: === | |
| − | + | ---- | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | === Gold Sponsors: === | |
| + | [http://www.barracudanetworks.com/ http://www.owasp.org.cn/images/stories/logo.png] | ||
| + | [http://www.venustech.com.cn/ http://www.owasp.org/images/4/4d/VenusTech_logo.gif] | ||
| + | [http://www.ankki.com/ http://www.owasp.org.cn/images/stories/ankkilog.png]深圳昂楷科技有限公司 | ||
| + | [http://www.honkwin.com/ http://www.honkwin.com/images/demo_03.gif]红科网安(北京)科技有限公司 | ||
| + | ---- | ||
| − | === | + | === Supporting Sponsors: === |
| + | [http://www.huawei.com/ http://www.owasp.org/images/f/ff/Huawei_Logo.gif] 华为 | ||
| − | == | + | |
| + | {{MemberLinks|link=http://www.microsoft.com|logo=Logo_microsoft.jpg}}微软中国 | ||
| − | + | ||
| + | [http://www.vulnhunt.com/ '''南京翰海源'''] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ---- | |
| − | |||
| − | |||
| − | + | === Educational Sponsors: === | |
| − | + | [http://www.is.cas.cn/ http://www.owasp.org/images/1/15/ISCAS_logo.gif]中国科学院软件研究所 [http://www.infosec.pku.edu.cn/ http://www.owasp.org/images/2/21/InfoSec_Lab_PKU_logo.gif] | |
| − | + | ---- | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | === Organizing Partners: === | |
| + | [http://www.idcquan.com/ http://www.idcquan.com/images/logo2009.gif] | ||
| + | [http://www.seczone.org http://www.seczone.org/templates/jsn_epic_pro/images/logo.png] | ||
| + | [http://www.nsace.org.cn http://www.nsace.org.cn/templets/images/toplogo.gif] | ||
| − | + | ---- | |
| − | + | === Media Partners: === | |
| + | OWASP media resources and China mainstream IT Medias publicize this web application security summit in every rolling stage. Participated Medias include: | ||
| + | * Print Media:CIW, CNW, 365master, TTM, CCW, CISMAG, CBINEWS, etc | ||
| + | * Network Media: | ||
| + | [http://www.chinabyte.com/ http://image.chinabyte.com/w/pic/logo.gif] | ||
| + | [http://www.it168.com/ http://www.it168.com/himages/logo.gif] | ||
| + | [http://www.51cto.com http://images.51cto.com/images/index/Images/Logo.gif] | ||
| + | [http://www.cww.net.cn/ http://www.cww.net.cn/images/top_logo.jpg] | ||
| + | [http://www.ccidnet.com/, http://image.ccidnet.com/www/logo.jpg], CTOCIO, etc. | ||
| + | ---- | ||
| − | Slots are going fast so contact [mailto: | + | === Sponsor US! === |
| + | We are still soliciting sponsors for the OWASP China Summit. An exhibit hall will be held for vendor booths and presentations. For more details, please see the OWASP China Summit 2010 Investment Guide [[http://www.owasp.org/images/1/17/OWASP_China_Summit_2010_Investment_Guide.pdf English]][[http://www.owasp.org/images/6/66/OWASP_China_Summit_2010_Investment_Guide_Chinese.pdf Chinese]]. Slots are going fast so contact [mailto:weilin.zhong@owasp.org OWASP China Summit 2010 Organization Team] to sponsor today! | ||
| + | ---- | ||
==== Conference Committee ==== | ==== Conference Committee ==== | ||
===Contact=== | ===Contact=== | ||
| − | * [mailto: | + | * [mailto:weilin.zhong@owasp.org OWASP China Summit 2010 Organization Team] |
===Organizers=== | ===Organizers=== | ||
* Local host: | * Local host: | ||
| − | **[mailto:[email protected] Rip Torn] [http://www.owasp.org/index.php/China-Mainland OWASP China-Mainland Chapter] | + | **[mailto:[email protected] Rip Torn] [http://www.owasp.org/index.php/China-Mainland OWASP China-Mainland Chapter Chair] |
| + | **[mailto:[email protected] Ivy Zhang] [http://www.owasp.org/index.php/China-Mainland OWASP China-Mainland Chapter Summit Secretary] | ||
* Overseas: | * Overseas: | ||
** [mailto:[email protected] Weilin Zhong] | ** [mailto:[email protected] Weilin Zhong] | ||
** [mailto:[email protected] Helen Gao] | ** [mailto:[email protected] Helen Gao] | ||
| + | ** [mailto:[email protected] Zhendong Yu] | ||
===Conference Committee=== | ===Conference Committee=== | ||
| − | * [mailto:[email protected] Rip Torn] | + | * [mailto:[email protected] Rip Torn] 万振华,Chair of OWASP China Mainland chapter |
| − | * [mailto:[email protected] Frank Fan] | + | * [mailto:[email protected] Frank Fan] 范渊,Vice President of OWASP China Mainland chapter, President of DBAPPSecurity Ltd. |
* [mailto:[email protected] Weilin Zhong] 钟卫林,Lead of OWASP Chinese Project and Honeycomb Project, Senior Info Sec Eng at Wells Fargo, CISSP | * [mailto:[email protected] Weilin Zhong] 钟卫林,Lead of OWASP Chinese Project and Honeycomb Project, Senior Info Sec Eng at Wells Fargo, CISSP | ||
* [mailto:[email protected] Helen Gao] 高雯,Lead of OWASP Long Island Chapter and OWASP Chinese Project, CISSP | * [mailto:[email protected] Helen Gao] 高雯,Lead of OWASP Long Island Chapter and OWASP Chinese Project, CISSP | ||
| − | * [mailto: | + | * [mailto:ggf.ish@gmail.com Zhendong Yu] 于振东, OWASP Chinese Project, Co-Founder, VP Engineering, Innovative Query Inc, CISSP |
* [mailto:[email protected] Eric Chio] 趙嘉言, Lead of OWASP Shanghai Chapter, Microsoft. | * [mailto:[email protected] Eric Chio] 趙嘉言, Lead of OWASP Shanghai Chapter, Microsoft. | ||
* [mailto:[email protected] Jianchun Jiang] 蒋建春 - Lead of OWASP Beijing Chapter, Associate Professor, The Software Institute, Chinese Academy of Sciences, 中科院软件所副研究员. NSACE 负责人 | * [mailto:[email protected] Jianchun Jiang] 蒋建春 - Lead of OWASP Beijing Chapter, Associate Professor, The Software Institute, Chinese Academy of Sciences, 中科院软件所副研究员. NSACE 负责人 | ||
* [mailto:[email protected] Jie Wang] 王颉 - High Speed Network Group, Dept of Electronic and Electrical Engineering, Loughborough Univ.,UK. | * [mailto:[email protected] Jie Wang] 王颉 - High Speed Network Group, Dept of Electronic and Electrical Engineering, Loughborough Univ.,UK. | ||
* [mailto:[email protected] Wayne Huang] 黃耀文 - OWASP conference committee, OWASP Taiwan Chapter Chair, Founder and CEO of Armorize Technology. | * [mailto:[email protected] Wayne Huang] 黃耀文 - OWASP conference committee, OWASP Taiwan Chapter Chair, Founder and CEO of Armorize Technology. | ||
| + | * [mailto:[email protected], Ivy Zhang] 张小姐 - OWASP China Summit Secretary, OWASP China-Mainland Chapter, 会务秘书 | ||
| + | |||
| + | ==== Expense ==== | ||
| − | === | + | === OWASP China Summit Expense === |
| − | + | [[File:OWASP_China_Summit_Cost.png]] | |
| − | + | ==== Logistics==== | |
| − | + | === Venue === | |
| − | + | Hotel Nikko New Century Beijing Conference Center | |
| − | + | === Hotel === | |
| − | + | Hotel Nikko New Century Beijing | |
| − | + | 北京新世纪日航酒店 北京市海淀区首体南路6号 | |
| − | + | * Add: No.6 Southern Road, Capital Gym, Haidian District, Beijing 100044 | |
| + | * Tel: 86-10-6849 2001 | ||
| + | * Fax: 86-10-6849 1103 | ||
| + | * http://www.newcenturyhotel.com.cn | ||
| − | + | [http://www.newcenturyhotel.com.cn http://www.owasp.org.cn/images/stories/hotel.jpg] | |
| − | Hotel | + | === Hotel Booking === |
| + | * Mention attending the "OWASP China Summit", you can get the discount prices. | ||
| + | * The summit local team is happy to book the hotel for you, please contact: | ||
| + | ** Peter Zhang | ||
| + | ** Email: [email protected] | ||
| + | ** Tel: 010-85655622 | ||
| + | ** Fax: +86-10-85653108 | ||
| + | * For more detail information, please see the [http://www.owasp.org.cn/index.php?option=com_content&view=article&id=58&Itemid=85 summit Chinese website (详情请见峰会中文网站)]. | ||
=== Travel === | === Travel === | ||
| Line 165: | Line 298: | ||
* For detailed information on obtaining a business visa for this event, please refer to [http://www.china-embassy.org/eng/hzqz/zgqz/t84247.htm Chinese embassy] | * For detailed information on obtaining a business visa for this event, please refer to [http://www.china-embassy.org/eng/hzqz/zgqz/t84247.htm Chinese embassy] | ||
* More questions, please contact [mailto:[email protected] Helen Gao] | * More questions, please contact [mailto:[email protected] Helen Gao] | ||
| − | |||
| − | |||
| − | |||
| − | |||
<headertabs /> | <headertabs /> | ||
[[Category:OWASP AppSec Conference]][[Category:OWASP_China_Summit_2010]][[Category:China]] | [[Category:OWASP AppSec Conference]][[Category:OWASP_China_Summit_2010]][[Category:China]] | ||
Latest revision as of 05:03, 30 October 2010
Welcome
OWASP China Summit 2010 - Beijing China
OWASP China-Mainland Chapterwill host OWASP China Summit 2010 in Beijing China on Oct 20-23, 2010, with two days of training followed by two days of conference. The summit will gather OWASP leaders, security experts, executives, technical thought leaders, developers, scientists and researchers from China and around the world for in-depth discussions of cutting-edge application security issues. The summit will draw participation from major Chinese and global organizations across various verticals including government, information technology, services and consulting, telecommunications, finance, e-commerce, Internet, universities and research institutes. About 800 people are expected to attend the summit, which will be covered by major news media. Panel discussions, vendor exhibit, and dinners will be held at the summit, providing sufficient networking opportunities.
Press Release: OWASP China Summit 2010 Announcement
中文(Chinese)
中文网站
本次会议设有专门的中文网站: OWASP 2010 中国峰会中文网站。
Registration
Please register yourself to attend the OWASP China Summit. General admission is FREE.
Who Should Attend OWASP China Summit 2010:
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interesting in Improving IT Security
For student discount, attendees must present proof of enrollment when picking up your badge.
Questions, please contact: OWASP China Summit 2010 Organization Team
Training: Oct 20 - 21
Training Agenda
| Training Oct 20 - Oct 21 | |||||
| Time | Trainer | Topic | Language | Price (Before Oct.10) | Price (After Oct.10) |
| AM Oct 20 | Yuezhong Bao, Microsoft | Secure Development Lifecycle | Chinese | RMB 1000 ($150) | RMB 1500 ($230) |
| PM Oct 20 | Benson Wu, Armorize | Security Code Review | Chinese | RMB 1000 ($150) | RMB 1500 ($230) |
| AM Oct 21 | Xin Fang, VulnHunt | Security Testing | Chinese | RMB 1000 ($150) | RMB 1500 ($230) |
| PM Oct 21 | Aaron, DBAppSecurity | Security Testing | Chinese | RMB 1000 ($150) | RMB 1500 ($230) |
Enrollment & Questions:
- Ivy: 13510601178, [email protected]
- Rip: 13699898080, [email protected]
Trainer Bios & Course Abstracts
- More details, please see the summit Chinese website (详情请见峰会中文网站).
Agenda: Oct 22
Detailed Agenda in Chinese (详细会议日程).
| Conference Day 1 - Oct 22, 2010 Tentative | |||
| Time | Speaker | Presentation | Language |
| 08:30-09:00 | Registration and Networking | ||
| 09:00-09:10 | Rip Torn, OWASP China Chapter and Tom Brennan OWASP Board | Opening Statement: Welcome to OWASP China Summit 2010 | Chinese/English |
| 09:10-10:00 | Keynote: Chenxi Wang, PhD, Forrester Research | #Application Security Market Trend 应用安全市场动态 | Chinese |
| 10:10-10:40 | Weilin Zhong, OWASP | OWASP TOP 10 | Chinese |
| 10:50-11:20 | Frank Fan, DBAppSecurity | Web Attack and Defense Trends | Chinese |
| 11:30-12:00 | Wong Onn Chee, OWASP Singapore Chapter | #Outbound Monitoring of Web Servers: a Forgotten Child in Information Security? | Chinese/English |
| 12:00-13:30 | Lunch Break | ||
| 13:30-14:10 | Kenny Lee, Verizon Business | #2010 Data Breach Investigation Report | English with real-time Chinese translation |
| 14:20-15:00 | Pravir Chandra, OWASP | #Building an effective SSA program in measurable iterations | English with real-time Chinese translation |
| 15:10-15:40 | Helen Gao, OWASP Long Island Chapter | OWASP and OWASP Projects | Chinese |
| 16:00-17:00 | Panel | Round Table: Web App Security - State of Art | Chinese |
Application Security Market Trend 应用安全市场动态
Chenxi Wang, PhD
应用安全是很多企业安全部门的重要运行目标。在这个报告中我们将分析全球应用安全市场动态,并看一下世界的一些领先机构是怎样在内部推广和运行应用安全产品。我们将分析一些金融界和保险行业的成功案例 ,看一下这些公司是怎样把应用安全产品分门别类融进他们的日常运行程序,并怎样克服运行中遇到的困难。最后我们还将讨论应用安全产品的发展和研究趋势。
Outbound Monitoring of Web Servers: a Forgotten Child in Information Security?
Wong Onn Chee
Outbound monitoring of enterprise web servers is an oft-neglected aspect in the overall security of an enterprise web infrastructure.When outbound monitoring is missing, risks from information leakage and transmission of malware are ever present. Onn Chee will walk through the most common causes of information leakage and malware transmission from web servers. Anonymised case studies of major US and Chinese organisations will be presented for the audience to have a better understanding.
2010 Data Breach Investigation Report
Kenny Lee
This presentation is based on the Verizon Business Data Breach Investigations Report1 (DBIR) and will be delivered by Kenny Lee, one of the contributors of the report. The DBIR is a collaborative effort between the United States Secret Service Cyber Intelligence Section and Verizon Business to collect and analyse what we believe to be the world’s largest study of data breaches consisting of over 900 cases and 900 million compromised records across six years of first hand forensic investigations. We have learned a great deal from this journey and we’re glad to have the opportunity to share these findings with you. As always, our goal is that the data and analysis presented in this report prove helpful to the planning and security efforts of the audience. Many of the lessons learnt from this study strongly indicated the need for improvements in web application security. Data breaches are often a series of simple oversights that culminate in a significant event where huge amounts of data are stolen. We will discuss the most common issues through the use of statistics, war stories and case studies. Key recommendations will be discussed that we believe will help your organisation not be the next victim of a data breach. More information can be found at Verizon Business website.
Building an effective SSA program in measurable iterations
Pravir Chandra
Integrating security activities into the software development process remains a challenge for most organizations despite the existence of several secure SDLC models. We've learned from experience that the hard questions of "what", "when", and "how much" require answers customized to each organization and there are no simple, one-size-fits-all answers. To help organizations find their own answers, this session will introduce the Open Software Assurance Maturity Model (OpenSAMM), a flexible framework for building a balanced software security assurance (SSA) program. Using the framework, attendees will learn how to self-assess their security activities and use roadmap templates to improve in small and measurable iterations. We'll also talk about several real-world case studies that demonstrate the framework in action. Time allowing, additional case studies will also be discussed. OpenSAMM is an open a free project and has recently been donated to the Open Web Application Security Project (OWASP) Foundation. For more information on OpenSAMM, visit http://www.opensamm.org/.
Sponsors
Diamond Sponsors:
Platinum Sponsors:
Gold Sponsors:
Supporting Sponsors:
Educational Sponsors:
Organizing Partners:
Media Partners:
OWASP media resources and China mainstream IT Medias publicize this web application security summit in every rolling stage. Participated Medias include:
- Print Media:CIW, CNW, 365master, TTM, CCW, CISMAG, CBINEWS, etc
- Network Media:
Sponsor US!
We are still soliciting sponsors for the OWASP China Summit. An exhibit hall will be held for vendor booths and presentations. For more details, please see the OWASP China Summit 2010 Investment Guide [English][Chinese]. Slots are going fast so contact OWASP China Summit 2010 Organization Team to sponsor today!
Conference Committee
Contact
Organizers
- Local host:
- Overseas:
Conference Committee
- Rip Torn 万振华,Chair of OWASP China Mainland chapter
- Frank Fan 范渊,Vice President of OWASP China Mainland chapter, President of DBAPPSecurity Ltd.
- Weilin Zhong 钟卫林,Lead of OWASP Chinese Project and Honeycomb Project, Senior Info Sec Eng at Wells Fargo, CISSP
- Helen Gao 高雯,Lead of OWASP Long Island Chapter and OWASP Chinese Project, CISSP
- Zhendong Yu 于振东, OWASP Chinese Project, Co-Founder, VP Engineering, Innovative Query Inc, CISSP
- Eric Chio 趙嘉言, Lead of OWASP Shanghai Chapter, Microsoft.
- Jianchun Jiang 蒋建春 - Lead of OWASP Beijing Chapter, Associate Professor, The Software Institute, Chinese Academy of Sciences, 中科院软件所副研究员. NSACE 负责人
- Jie Wang 王颉 - High Speed Network Group, Dept of Electronic and Electrical Engineering, Loughborough Univ.,UK.
- Wayne Huang 黃耀文 - OWASP conference committee, OWASP Taiwan Chapter Chair, Founder and CEO of Armorize Technology.
- Ivy Zhang 张小姐 - OWASP China Summit Secretary, OWASP China-Mainland Chapter, 会务秘书
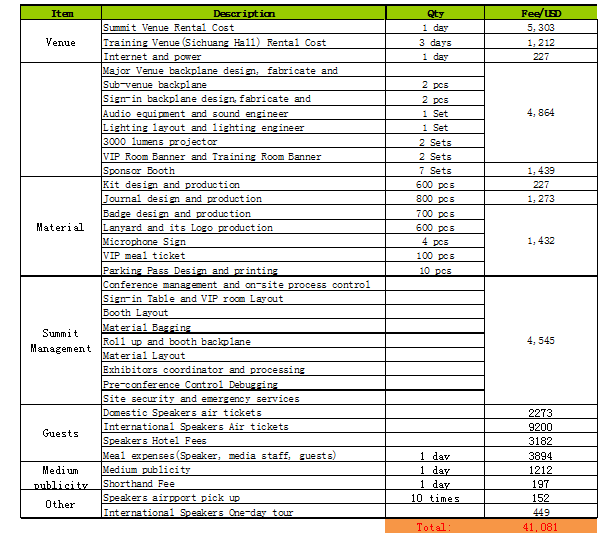
Expense
OWASP China Summit Expense
Logistics
Venue
Hotel Nikko New Century Beijing Conference Center
Hotel
Hotel Nikko New Century Beijing 北京新世纪日航酒店 北京市海淀区首体南路6号
- Add: No.6 Southern Road, Capital Gym, Haidian District, Beijing 100044
- Tel: 86-10-6849 2001
- Fax: 86-10-6849 1103
- http://www.newcenturyhotel.com.cn
Hotel Booking
- Mention attending the "OWASP China Summit", you can get the discount prices.
- The summit local team is happy to book the hotel for you, please contact:
- Peter Zhang
- Email: [email protected]
- Tel: 010-85655622
- Fax: +86-10-85653108
- For more detail information, please see the summit Chinese website (详情请见峰会中文网站).
Travel
How to obtain a visa for the event
- Invitation letter will be sent out for overseas attendees after registration.
- For detailed information on obtaining a business visa for this event, please refer to Chinese embassy
- More questions, please contact Helen Gao