This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Rochester"
Duane Peifer (talk | contribs) (→Meeting Dates & Location) |
m (Updated Slack link.) |
||
| (188 intermediate revisions by 8 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | [[File:Rochester_banner.jpg|800px]] | |
== Welcome to the OWASP Rochester Local Chapter == | == Welcome to the OWASP Rochester Local Chapter == | ||
| − | Welcome to the local Rochester chapter homepage. The chapter | + | Welcome to the local Rochester chapter homepage. The chapter leaders are: |
| + | * [mailto:ralph.durkee@owasp.org Ralph Durkee] | ||
| + | * [mailto:[email protected] John King] | ||
| + | * [mailto:[email protected] James Keeler] | ||
| − | + | If you or your organization is interested in sponsoring a meeting or hosting a meeting please contact one of the local officers listed above. | |
| − | |||
| − | + | == Connect With Us == | |
| − | + | {| cellspacing="15" | |
| + | |- | ||
| + | | [[Image:Follow-us-on-twitter.png|175px|link=https://twitter.com/owasprochester]] | ||
| + | | [[Image:meetup-button.png|108px|link=https://www.meetup.com/OWASP-Rochester-Chapter]] | ||
| + | | [[Image:Slack.png|175px|link=https://join.slack.com/t/owasp/shared_invite/enQtNjExMTc3MTg0MzU4LWQ2Nzg3NGJiZGQ2MjRmNzkzN2Q4YzU1MWYyZTdjYjA2ZTA5M2RkNzE2ZjdkNzI5ZThhOWY5MjljYWZmYmY4ZjM]] | ||
| + | |- | ||
| + | | | ||
| + | | | ||
| + | | #chapter-rochester | ||
| + | |} | ||
| − | + | [https://groups.google.com/a/owasp.org/forum/#!forum/rochester-chapter-announce/join Join our announcements mailing list] | |
| − | + | [https://groups.google.com/a/owasp.org/forum/#!forum/rochester-chapter/join Join our discussion mailing list] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == | + | <meetup group="OWASP-Rochester-Chapter" /> |
| + | === Archived events === | ||
| + | [[Rochester_Meeting_Archive|Visit our archive page for all old event details.]] | ||
| − | + | === Last Year's Events === | |
| + | '''OWASP December 19th Meeting''' | ||
| − | < | + | You are invited to join the Rochester OWASP chapter and the ISSA Rochester chapter for our joint December 19<sup>th</sup> Meeting at 6pm. Space is limited, so please RSVP by Dec 12<sup>th</sup> so we can plan accordingly. Dinosaur BBQ will be provided! Come and hear a great presentation, and network with your fellow professionals. |
| − | + | The OWASP chapter is covering its portion of the costs for the event, so if you are a paid OWASP member, Thank you! If not, please consider signing up today. | |
| − | + | Our own illustrious '''Jim Keeler''' will presenting: | |
| − | |||
| − | + | '''Title''': Introduction to Threat Modeling | |
| − | + | '''Abstract''': Every business has something to protect. Has yours modeled all of the ways it could be attacked? How will you defend your assets if attacked? How will you account for changes in the threat landscape? We will explore all of these questions and discuss a repeatable process for reducing risk. | |
| − | + | '''Bio''': Jim is a senior software engineer at Calero Software. He has been designing and building software since 2005 in many different languages and environments. At Calero, Jim volunteers on an internal security team to promote secure development practices, conduct threat modeling, and support security initiatives. He holds a B.S. in Computer Science from SUNY Fredonia and is pursuing a GSSP-.NET certification. | |
| − | + | '''Where''': Nixon Peabody, 1300 Clinton Square, 14th floor [CORRECTED] (free parking underneath the building, bring the ticket to the meeting for validation) | |
| − | + | '''When''': Wednesday, Dec 19th, 6:00 PM | |
| − | |||
| − | |||
| − | |||
| − | < | + | Please RSVP by Dec 12<sup>th</sup> to Ralph Durkee |
| − | + | Thank you, Hope to see you there! | |
| − | |||
| − | |||
| − | |||
| − | + | ;;Rochester Security Summit 2018 | |
| − | + | Date: Oct 9 & 10, 2018 OWASP AppSec Track: | |
| − | + | * What is the Android Colluded Applications Attack and How to Detect It (Igor Khokhlov & Leon Reznik) | |
| − | + | * Pentesting DevOps: Attacking Containers and Container Orchestration (Mark Manning) | |
| − | + | * Rocking The (Vox)Vote (Jason Ross) | |
| − | + | * Your Apps Have Gone Serverless. Has Your Security? (Tal Melamed) | |
| − | + | * Techniques Criminals Use to Break Authentication and How to Defend Against These Attacks (Danny Harris) | |
| − | The | + | * The Industrialization of Red and Blue Teaming (Ashley Zaya) |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ; '''OWASP Juice Shop Workshop''' | |
| + | ; '''July 18th, 2018''' | ||
| + | ; '''5:30 pm - 8:00 pm''' | ||
| + | ; '''44 Celebration Drive, Conference Rooms 2007a and 2007b''' | ||
| − | + | We're looking for chapter members who are familiar with basic application security and the OWASP Top 10 who are interested in learning OWASP Juice Shop. The goal is to help plan and facilitate a larger capture-the-flag event at a future meeting. Please bring a Laptop with a WiFi network connection and a modern web browser. You will be installing OWASP Juice Shop on your laptop. | |
| − | + | ; '''What is OWASP Juice Shop?''' | |
| − | + | OWASP Juice Shop is an intentionally insecure web app for security trainings written entirely in JavaScript which encompasses the entire OWASP Top Ten and other severe security flaws. Juice Shop is written in Node.js, Express and AngularJS. https://www.owasp.org/index.php/OWASP_Juice_Shop_Project | |
| − | + | ; '''What will the workshop cover?''' | |
| − | |||
| + | Jim Keeler will lead the workshop. Attendees will learn about the OWASP Juice Shop project, installation and setup, how to exploit common web application vulnerabilities, jeopardy style capture-the-flag (CTF) events, and CTF scoreboards. At the end of the workshop we will be looking for volunteers to help us host a future CTF event! Pizza will be provided. '''Please RSVP to Ralph Durkee, <[email protected]> so that we may expect you.''' | ||
| − | ; | + | ; '''Directions''' |
| − | : | + | [[File:UofRMC Map.png|thumb]] |
| + | Park anywhere in the green area. You can enter from Elmwood Ave going eastbound only or from Celebration Drive. Parking is free in the labeled surface lot. Enter the building by the arrow. Take the stairs or elevator to the 2nd floor. Take a right off the elevator and you should be able to easily find room 2007. | ||
| − | |||
| − | |||
| − | |||
| − | + | ; '''OWASP Rochester Social Event''' | |
| + | Please join the Rochester OWASP chapter for a social event Wednesday, April 25th at MacGregors' in Henrietta. | ||
| − | + | Appetizers will be provided. | |
| − | + | '''When: Wednesday, April 25 at 5:30pm''' | |
| − | + | '''Where: MacGregors' Grill and Tap Room (300 Jefferson Rd, Rochester, NY)''' | |
| − | + | ; '''OWASP Rochester Social Event''' | |
| + | Please join the Rochester OWASP chapter for a social event Wednesday, December 6th at MacGregors' in Henrietta. | ||
| − | + | Appetizers will be provided. | |
| − | + | When: Wednesday, December 6 at 5:30pm | |
| − | + | Where: MacGregors' Grill and Tap Room (300 Jefferson Rd, Rochester, NY) | |
| − | |||
| − | + | == Participation == | |
| − | + | OWASP chapter meetings are free and open to anyone interested in application security. We encourage members to give presentations on specific topics and to contribute to the local chapter by sharing their knowledge with others. | |
| − | + | '''Mailing Lists:''' | |
| + | * [https://lists.owasp.org/mailman/listinfo/owasp-rochester-announce Announcements] | ||
| + | * [http://lists.owasp.org/pipermail/owasp-rochester-ny Discussion] | ||
| + | Prior to participating with OWASP please review the [[:Category:Chapter Handbook|Chapter Rules]]. | ||
| − | + | == Past Presentations == | |
| + | {| class="wikitable" | ||
| + | !Date | ||
| + | !Title | ||
| + | !Presenter | ||
| + | !Download | ||
| + | |- | ||
| + | |2019, May | ||
| + | |OWASP Amass Project | ||
| + | |Jeff Foley, Anthony Rhodes | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=https://www.owasp.org/images/0/00/OWASP_Amass_Rochester_2019.pdf]] | ||
| + | |- | ||
| + | |2019, April | ||
| + | |Ethical Web Hacking | ||
| + | |Jim Keeler | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=https://docs.google.com/presentation/d/1kGcynzAoTaYajjkaSPo1dRUD1QQ13NuMFTZRDm9QAN0/edit?usp=sharing]] | ||
| + | |- | ||
| + | |2018, December | ||
| + | |Introduction to Threat Modeling | ||
| + | |Jim Keeler | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=https://docs.google.com/presentation/d/1J50yIrf-pHb7pTIjqBzRhLTk3TAPtm_F30J7RnVfOvE/edit?usp=sharing]] | ||
| + | |- | ||
| + | |2012, May | ||
| + | ''Mercury Networks Security Symposium'' | ||
| + | |I'll see your cross site scripting and raise you a Content Security Policy | ||
| + | |Lou Leone | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=https://www.owasp.org/images/9/95/2012_CSP.pptx]] | ||
| + | |- | ||
| + | |2011, January | ||
| + | |State of OWASP and the State of Web Application Security by Ralph Durkee | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Ralph_Durkee_State_of_Web_App_Security_v8.ppt]] [[File:16x16-icon-w-pdf.png|frameless|16x16px|link=Media:Ralph Durkee State of Web App Security v8.pdf]] | ||
| + | |- | ||
| + | |2010, August | ||
| + | |Man in the Middle Attacks: SSL Spoofing | ||
| + | |Duane Peifer | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:SSL_Spoofing.ppt]] [[File:16x16-icon-w-pdf.png|frameless|16x16px|link=Media:SSL Spoofing.pdf]] | ||
| + | |- | ||
| + | |2010, August | ||
| + | |Man in the Middle Attacks: SSL Spoofing | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Ralph_Durkee_SSL_MITM_v1.ppt]] [[File:16x16-icon-w-pdf.png|frameless|16x16px|link=Media:Ralph Durkee SSL MITM v1.pdf]] | ||
| + | |- | ||
| + | |2010, May | ||
| + | |New Techniques in Application Intrusion Detection | ||
| + | |Al Huizenga | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:OWASP may17-10.pptx]] [[File:16x16-icon-w-pdf.png|frameless|16x16px|link=Media:OWASP may17-10.pdf]] | ||
| + | |- | ||
| + | |2010, May | ||
| + | |Identity Federation and Claim-based Security | ||
| + | |Andrea Cogliati | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=Media:SAML and Claims-Based Security.pdf]] | ||
| + | |- | ||
| + | |2010, February | ||
| + | |DC AppSec Conference Recap | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:OWASP Rochester 2010 Feb.ppt]] | ||
| + | |- | ||
| + | |2009, October | ||
| + | ''October Hackerfest'' | ||
| + | |Introduction to OWASP Rochester | ||
| + | |Ralph Durkee, | ||
| + | Lou Leone | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Intro to OWASP Rochester v9.ppt]] | ||
| + | |- | ||
| + | |2009, September | ||
| + | |Securing Apache Web Servers with Mod Security & CIS Benchmark | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Media:Durkee Apache 2009 v7.ppt]], [[Media:Durkee Apache 2009 v7.odp|ODP]] | ||
| + | |- | ||
| + | |2009, May | ||
| + | |Key Management - One Perspective | ||
| + | |Lou Leone | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:N-tierKeyManagementIssues.ppt]] | ||
| + | |- | ||
| + | |2009, May | ||
| + | ''IEEE'' | ||
| + | |Introduction to OWASP | ||
| + | |Ralph Durkee, | ||
| + | Andrea Cogliati | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Intro to OWASP Rochester v5.ppt]] | ||
| + | |- | ||
| + | |2009, January | ||
| + | |Paranoid Programming Practices | ||
| + | |Lou Leone, | ||
| + | Aaron Witt | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:ParanoidProgrammers.ppt]] | ||
| + | |- | ||
| + | |2008, May | ||
| + | |Database Encryption | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:Database_Encryption.ppt]] | ||
| + | |- | ||
| + | |2008, January | ||
| + | |SQL Injection and Dynamic SQL | ||
| + | |Andrea Cogliati | ||
| + | |[[Media:MoreSQL.zip|ZIP]] | ||
| + | |- | ||
| + | |2007, September | ||
| + | |2007 OWASP Top 10 Most Critical Web Application Security Vulnerabilities | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=Media:OWASP Top 10 2007 v6.ppt]] | ||
| + | |- | ||
| + | |2006, October | ||
| + | |The first of the OWASP top ten: unvalidated input | ||
| + | |Steve Buck | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/2006-10-16_owasp-presentation.ppt]] | ||
| + | |- | ||
| + | |2006, April | ||
| + | |PGP: Encryption for e-mail and web applications | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=http://rd1.net/owasp/Apr_OWASP_PGP_Durkee.pdf]] | ||
| + | |- | ||
| + | |2006, February | ||
| + | |Identity Theft, Phishing and Pharming | ||
| + | |Danny Allan | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=http://rd1.net/owasp/AppSec2005DC-Danny_Allan-Identity_Theft_Phishing_and_Pharming.pdf]] | ||
| + | |- | ||
| + | |2006, February | ||
| + | |Secure e-mail | ||
| + | |Thomas Bullinger | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=http://rd1.net/owasp/SecureEmail.pdf]] | ||
| + | |- | ||
| + | |2006, January | ||
| + | |PCI Compliance | ||
| + | |Pat Massey, | ||
| + | Ralph Durkee, | ||
| − | + | Maureen Baran | |
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=http://rd1.net/owasp/Rochester_OWASP_PCI_Compliance.pdf]] | ||
| + | |- | ||
| + | |2005, September | ||
| + | |Two Factor Authentication for Java Applications with Client Certificates | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-pdf.png|frameless|16x16px|link=http://rd1.net/owasp/DCI-Java-SSL-Certs-2005-09-19.pdf]], [http://rd1.net/owasp/DCI-Java-SSL-Certs-2005-09-19.sxi SXI] | ||
| + | |- | ||
| + | |2005, April | ||
| + | |Avoiding Backend Exploitation of Mail Forms | ||
| + | |Max Kessler | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/owasp-mailform-exploitation.ppt]], [http://rd1.net/owasp/owasp-mailform-exploitation.sxi SXI] | ||
| + | |- | ||
| + | |2005, March | ||
| + | |Bringing Two-Factor Authentication to Web Applications | ||
| + | |Michael Starks | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/2005_Mar_OWASP_Two-factor%20Web%20App.ppt]], [http://rd1.net/owasp/2005_Mar_OWASP_Two-factor%20Web%20App.ppt SXI] | ||
| + | |- | ||
| + | |2005, February | ||
| + | |Insecure Storage | ||
| + | |Chris Karr | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/Insecure_Storage.ppt]] | ||
| + | |- | ||
| + | |2005, January | ||
| + | |Access Control and Session Mgmnt | ||
| + | |Steve Buck | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/Jan_OWASP-access-control.ppt]], [http://rd1.net/owasp/Jan_OWASP-access-control.sxi SXI] | ||
| + | |- | ||
| + | |2004, November | ||
| + | |Intro to OWASP | ||
| + | |Ralph Durkee | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/Nov_OWASP_20041103.ppt]] | ||
| + | |- | ||
| + | |2004, November | ||
| + | |Demonstration of SQL Injection attack and prevention | ||
| + | |Paul Cupo | ||
| + | |[[File:16x16-icon-w-ppt.png|frameless|16x16px|link=http://rd1.net/owasp/Nov_OWASP_20041103.ppt]] | ||
| + | |} | ||
| − | + | [[Category:OWASP Chapter]] | |
| − | + | [[Category:United States]] | |
| − | |||
| − | + | __NOTOC__ | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 14:01, 9 October 2019
Welcome to the OWASP Rochester Local Chapter
Welcome to the local Rochester chapter homepage. The chapter leaders are:
If you or your organization is interested in sponsoring a meeting or hosting a meeting please contact one of the local officers listed above.
Connect With Us

|

|

|
| #chapter-rochester |
Join our announcements mailing list
Join our discussion mailing list
Chapter Meetings
Visit our group on meetup.comArchived events
Visit our archive page for all old event details.
Last Year's Events
OWASP December 19th Meeting
You are invited to join the Rochester OWASP chapter and the ISSA Rochester chapter for our joint December 19th Meeting at 6pm. Space is limited, so please RSVP by Dec 12th so we can plan accordingly. Dinosaur BBQ will be provided! Come and hear a great presentation, and network with your fellow professionals.
The OWASP chapter is covering its portion of the costs for the event, so if you are a paid OWASP member, Thank you! If not, please consider signing up today.
Our own illustrious Jim Keeler will presenting:
Title: Introduction to Threat Modeling
Abstract: Every business has something to protect. Has yours modeled all of the ways it could be attacked? How will you defend your assets if attacked? How will you account for changes in the threat landscape? We will explore all of these questions and discuss a repeatable process for reducing risk.
Bio: Jim is a senior software engineer at Calero Software. He has been designing and building software since 2005 in many different languages and environments. At Calero, Jim volunteers on an internal security team to promote secure development practices, conduct threat modeling, and support security initiatives. He holds a B.S. in Computer Science from SUNY Fredonia and is pursuing a GSSP-.NET certification.
Where: Nixon Peabody, 1300 Clinton Square, 14th floor [CORRECTED] (free parking underneath the building, bring the ticket to the meeting for validation)
When: Wednesday, Dec 19th, 6:00 PM
Please RSVP by Dec 12th to Ralph Durkee
Thank you, Hope to see you there!
- Rochester Security Summit 2018
Date: Oct 9 & 10, 2018 OWASP AppSec Track:
- What is the Android Colluded Applications Attack and How to Detect It (Igor Khokhlov & Leon Reznik)
- Pentesting DevOps: Attacking Containers and Container Orchestration (Mark Manning)
- Rocking The (Vox)Vote (Jason Ross)
- Your Apps Have Gone Serverless. Has Your Security? (Tal Melamed)
- Techniques Criminals Use to Break Authentication and How to Defend Against These Attacks (Danny Harris)
- The Industrialization of Red and Blue Teaming (Ashley Zaya)
- OWASP Juice Shop Workshop
- July 18th, 2018
- 5:30 pm - 8:00 pm
- 44 Celebration Drive, Conference Rooms 2007a and 2007b
We're looking for chapter members who are familiar with basic application security and the OWASP Top 10 who are interested in learning OWASP Juice Shop. The goal is to help plan and facilitate a larger capture-the-flag event at a future meeting. Please bring a Laptop with a WiFi network connection and a modern web browser. You will be installing OWASP Juice Shop on your laptop.
- What is OWASP Juice Shop?
OWASP Juice Shop is an intentionally insecure web app for security trainings written entirely in JavaScript which encompasses the entire OWASP Top Ten and other severe security flaws. Juice Shop is written in Node.js, Express and AngularJS. https://www.owasp.org/index.php/OWASP_Juice_Shop_Project
- What will the workshop cover?
Jim Keeler will lead the workshop. Attendees will learn about the OWASP Juice Shop project, installation and setup, how to exploit common web application vulnerabilities, jeopardy style capture-the-flag (CTF) events, and CTF scoreboards. At the end of the workshop we will be looking for volunteers to help us host a future CTF event! Pizza will be provided. Please RSVP to Ralph Durkee, <[email protected]> so that we may expect you.
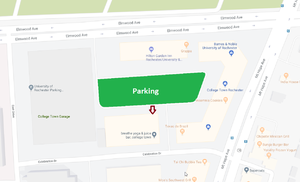
- Directions
Park anywhere in the green area. You can enter from Elmwood Ave going eastbound only or from Celebration Drive. Parking is free in the labeled surface lot. Enter the building by the arrow. Take the stairs or elevator to the 2nd floor. Take a right off the elevator and you should be able to easily find room 2007.
- OWASP Rochester Social Event
Please join the Rochester OWASP chapter for a social event Wednesday, April 25th at MacGregors' in Henrietta.
Appetizers will be provided.
When: Wednesday, April 25 at 5:30pm
Where: MacGregors' Grill and Tap Room (300 Jefferson Rd, Rochester, NY)
- OWASP Rochester Social Event
Please join the Rochester OWASP chapter for a social event Wednesday, December 6th at MacGregors' in Henrietta.
Appetizers will be provided.
When: Wednesday, December 6 at 5:30pm
Where: MacGregors' Grill and Tap Room (300 Jefferson Rd, Rochester, NY)
Participation
OWASP chapter meetings are free and open to anyone interested in application security. We encourage members to give presentations on specific topics and to contribute to the local chapter by sharing their knowledge with others.
Mailing Lists:
Prior to participating with OWASP please review the Chapter Rules.
Past Presentations
| Date | Title | Presenter | Download |
|---|---|---|---|
| 2019, May | OWASP Amass Project | Jeff Foley, Anthony Rhodes | |
| 2019, April | Ethical Web Hacking | Jim Keeler | |
| 2018, December | Introduction to Threat Modeling | Jim Keeler | |
| 2012, May
Mercury Networks Security Symposium |
I'll see your cross site scripting and raise you a Content Security Policy | Lou Leone | |
| 2011, January | State of OWASP and the State of Web Application Security by Ralph Durkee | Ralph Durkee | |
| 2010, August | Man in the Middle Attacks: SSL Spoofing | Duane Peifer | |
| 2010, August | Man in the Middle Attacks: SSL Spoofing | Ralph Durkee | |
| 2010, May | New Techniques in Application Intrusion Detection | Al Huizenga | |
| 2010, May | Identity Federation and Claim-based Security | Andrea Cogliati | |
| 2010, February | DC AppSec Conference Recap | Ralph Durkee | |
| 2009, October
October Hackerfest |
Introduction to OWASP Rochester | Ralph Durkee,
Lou Leone |
|
| 2009, September | Securing Apache Web Servers with Mod Security & CIS Benchmark | Ralph Durkee | |
| 2009, May | Key Management - One Perspective | Lou Leone | |
| 2009, May
IEEE |
Introduction to OWASP | Ralph Durkee,
Andrea Cogliati |
|
| 2009, January | Paranoid Programming Practices | Lou Leone,
Aaron Witt |
|
| 2008, May | Database Encryption | Ralph Durkee | |
| 2008, January | SQL Injection and Dynamic SQL | Andrea Cogliati | ZIP |
| 2007, September | 2007 OWASP Top 10 Most Critical Web Application Security Vulnerabilities | Ralph Durkee | |
| 2006, October | The first of the OWASP top ten: unvalidated input | Steve Buck | |
| 2006, April | PGP: Encryption for e-mail and web applications | Ralph Durkee | |
| 2006, February | Identity Theft, Phishing and Pharming | Danny Allan | |
| 2006, February | Secure e-mail | Thomas Bullinger | |
| 2006, January | PCI Compliance | Pat Massey,
Ralph Durkee, Maureen Baran |
|
| 2005, September | Two Factor Authentication for Java Applications with Client Certificates | Ralph Durkee | |
| 2005, April | Avoiding Backend Exploitation of Mail Forms | Max Kessler | |
| 2005, March | Bringing Two-Factor Authentication to Web Applications | Michael Starks | |
| 2005, February | Insecure Storage | Chris Karr | |
| 2005, January | Access Control and Session Mgmnt | Steve Buck | |
| 2004, November | Intro to OWASP | Ralph Durkee | |
| 2004, November | Demonstration of SQL Injection attack and prevention | Paul Cupo |