This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OAT-001 Carding"
m (→Description) |
(Fixed a minor type) (Tag: Visual edit) |
||
| (7 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
__NOTOC__ | __NOTOC__ | ||
| − | This is an automated threat. To view all automated threats, please see the [[:Category:Automated Threat|Automated Threat Category]] page | + | This is an automated threat. To view all automated threats, please see the [[:Category:Automated Threat|Automated Threat Category]] page. The OWASP Automated Threat Handbook - Web Applications ([https://www.owasp.org/index.php/File:Automated-threat-handbook.pdf pdf], print), an output of the [[OWASP Automated Threats to Web Applications|OWASP Automated Threats to Web Applications Project]], provides a fuller guide to each threat, detection methods and countermeasures. The [https://www.owasp.org/index.php/File:Oat-ontology-decision-chart.pdf threat identification chart] helps to correctly identify the automated threat. |
== Definition == | == Definition == | ||
| − | + | ===OWASP Automated Threat (OAT) Identity Number === | |
| + | OAT-001 | ||
| + | |||
| + | ===Threat Event Name=== | ||
| + | |||
| + | Carding | ||
| + | |||
| + | === Summary Defining Characteristics=== | ||
| + | |||
| + | Multiple payment authorisation attempts used to verify the validity of bulk stolen payment card data. | ||
| + | |||
| + | ===Indicative Diagram=== | ||
| + | |||
| + | [[File:OAT-001_Carding.png|500px|link=]] | ||
=== Description === | === Description === | ||
| Line 12: | Line 25: | ||
Lists of full credit and/or debit card data are tested against a merchant’s payment processes to identify valid card details. The quality of stolen data is often unknown, and Carding is used to identify good data of higher value. Payment cardholder data may have been stolen from another application, stolen from a different payment channel, or acquired from a criminal marketplace. | Lists of full credit and/or debit card data are tested against a merchant’s payment processes to identify valid card details. The quality of stolen data is often unknown, and Carding is used to identify good data of higher value. Payment cardholder data may have been stolen from another application, stolen from a different payment channel, or acquired from a criminal marketplace. | ||
| − | When partial cardholder data is available, and the expiry date and/or security code are not known, the process is instead known as [[ | + | When partial cardholder data is available, and the expiry date and/or security code are not known, the process is instead known as [[OAT-010 Card Cracking]]. The use of stolen cards to obtain cash or goods is [[OAT-012 Cashing Out]]. |
=== Other Names and Examples === | === Other Names and Examples === | ||
| Line 20: | Line 33: | ||
=== See Also === | === See Also === | ||
| − | * [[ | + | * [[OAT-010 Card Cracking]] |
| − | * [[ | + | * [[OAT-012 Cashing Out]] |
== Cross-References == | == Cross-References == | ||
| Line 29: | Line 42: | ||
* 210 Abuse of Functionality | * 210 Abuse of Functionality | ||
| − | === CWE Base / Class / Variant | + | === CWE Base / Class / Variant IDs === |
* 799 Improper Control of Interaction Frequency | * 799 Improper Control of Interaction Frequency | ||
* 837 Improper Enforcement of a Single, Unique Action | * 837 Improper Enforcement of a Single, Unique Action | ||
| − | === WASC Threat | + | === WASC Threat IDs === |
* 21 Insufficient Anti-Automation | * 21 Insufficient Anti-Automation | ||
| Line 42: | Line 55: | ||
* [[:Category:Abuse of Functionality|Abuse of Functionality]] | * [[:Category:Abuse of Functionality|Abuse of Functionality]] | ||
| − | |||
| − | |||
[[Category: Automated Threat]] | [[Category: Automated Threat]] | ||
Latest revision as of 15:52, 21 August 2018
This is an automated threat. To view all automated threats, please see the Automated Threat Category page. The OWASP Automated Threat Handbook - Web Applications (pdf, print), an output of the OWASP Automated Threats to Web Applications Project, provides a fuller guide to each threat, detection methods and countermeasures. The threat identification chart helps to correctly identify the automated threat.
Definition
OWASP Automated Threat (OAT) Identity Number
OAT-001
Threat Event Name
Carding
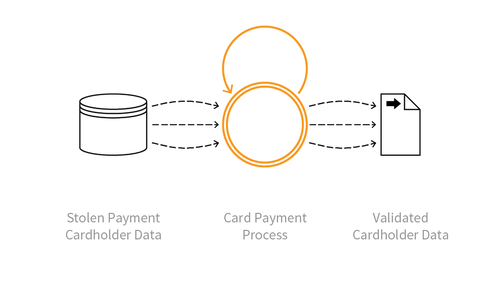
Summary Defining Characteristics
Multiple payment authorisation attempts used to verify the validity of bulk stolen payment card data.
Indicative Diagram
Description
Lists of full credit and/or debit card data are tested against a merchant’s payment processes to identify valid card details. The quality of stolen data is often unknown, and Carding is used to identify good data of higher value. Payment cardholder data may have been stolen from another application, stolen from a different payment channel, or acquired from a criminal marketplace.
When partial cardholder data is available, and the expiry date and/or security code are not known, the process is instead known as OAT-010 Card Cracking. The use of stolen cards to obtain cash or goods is OAT-012 Cashing Out.
Other Names and Examples
Card stuffing; Credit card stuffing; Card verification
See Also
Cross-References
CAPEC Category / Attack Pattern IDs
- 210 Abuse of Functionality
CWE Base / Class / Variant IDs
- 799 Improper Control of Interaction Frequency
- 837 Improper Enforcement of a Single, Unique Action
WASC Threat IDs
- 21 Insufficient Anti-Automation
- 42 Abuse of Functionality