This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Bucharest AppSec Conference 2017"
Oana Cornea (talk | contribs) (edit6) |
Oana Cornea (talk | contribs) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 49: | Line 49: | ||
| valign="middle" bgcolor="#EEEEEE" align="left" | '''Venue Location:''' [http://www.carohotel.ro/contact Hotel Caro] '''Workshops''': [http://www.carohotel.ro/contact Hotel Caro]<br> | | valign="middle" bgcolor="#EEEEEE" align="left" | '''Venue Location:''' [http://www.carohotel.ro/contact Hotel Caro] '''Workshops''': [http://www.carohotel.ro/contact Hotel Caro]<br> | ||
'''Venue Address''': 164A Barbu Vacarescu Blvd. 2nd District, 020285 Bucharest, Romania <br> | '''Venue Address''': 164A Barbu Vacarescu Blvd. 2nd District, 020285 Bucharest, Romania <br> | ||
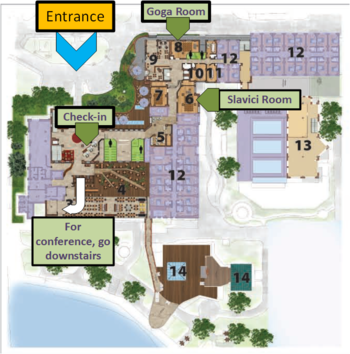
| − | Venue Map: --> | + | Venue Map: -->[[Image:FloorPlan.png|350px]] |
|- | |- | ||
| align="center" style="background:#CCCCEE;" colspan="2" | '''Price and registration''' | | align="center" style="background:#CCCCEE;" colspan="2" | '''Price and registration''' | ||
| Line 89: | Line 89: | ||
=CTF= | =CTF= | ||
{{:OWASP_Bucharest_AppSec_Conference_2017_CTF}} | {{:OWASP_Bucharest_AppSec_Conference_2017_CTF}} | ||
| + | |||
| + | =Sponsor CTF= | ||
| + | {{:OWASP_Bucharest_AppSec_Conference_2017_CTFS}} | ||
=Team= | =Team= | ||
Latest revision as of 15:43, 5 October 2017
- Welcome
- Become a sponsor
- Conference 0101 talks
- Conference 1010 talks
- WiA
- Free workshops
- 2 days training
- 1 day training
- CTF
- Sponsor CTF
- Team
|
|
CONFERENCE (Friday 13th of October) | ||
| Date | Location | |
| Friday 13th of October, 8.00 AM |
Venue Location: Hotel Caro Workshops: Hotel Caro Venue Address: 164A Barbu Vacarescu Blvd. 2nd District, 020285 Bucharest, Romania | |
| Price and registration | ||
| The conference entrance is FREE, you need to register on the link provided below, print your ticket and present it at the entrance. The training sessions will be paid. The workshops and CTF attendance is free of charge Registration |
||
Sponshorship opportunities
Why sponsor?
- Join 300+ leaders, security consultants, security architects and developers gathered to share cutting-edge ideas, initiatives and trends in technology.
- OWASP events attract an audience interested in "What's next?" - As a sponsor, you will be promoted as an answer to this question.
- Increase awareness and recognition in Romanian Security IT environment.
- Support and involvement in the world of information security enthusiasts.
Conference agenda, 13th of October | |||||
| Time | Title | Speaker | Description | ||
| 9:00 - 9:30 (30 mins) |
Registration and coffee break | ||||
| 9:30 - 9:45 (15 mins) |
Introduction | Oana Cornea | Introduction to the OWASP Bucharest Event, Schedule for the Day | ||
| 9:45 - 10:30 (45 mins) |
OWASP Juice Shop: The most trustworthy online shop out there | Bjoern Kimminich | OWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and other severe security flaws. In this talk you will learn all about the project and its capabilities. You will...
| ||
| 10:45 - 11:30 (45 mins) |
Application Security Lifecycle | Adrian Locusteanu | A complete perspective on application security assumes addressing the whole application lifecycle: from secure design and (static or dynamic) testing to changes and continuous operational protection through adaptive managed application security services. A standardized end2end frame to provide secure enablement for both application developers and online presences will be presented from Telekom's experience. | ||
| 11:45 - 12:30 (45 mins) |
N different strategies to automate OWASP ZAP | Marudhamaran Gunasekaran (Maran) | In this talk we will explore the many different ways of automating security testing with the OWASP Zed Attack Proxy and how it ties to an overall Software Security Initiative. Over the years, ZAP has made many advancements to its powerful APIs and introduced scripts to make security automation consumable for mortals. This talk is structured to demonstrate how ZAP's API, and scripts could be integrated with Automated Testing frameworks beyond selenium, Continuous Integration and Continuous Delivery Pipelines beyond Jenkins, scanning authenticated parts of the application, options to manage the discovered vulnerabilities and so on with real world case studies and implementation challenges.
This is a demonstration oriented talk that explains OWASP ZAP automation strategies for Security Testing by example. | ||
| 12:30 - 13:30 (60 mins) |
Lunch/Coffee Break | ||||
| 13:30 - 14:15 (40 mins) |
Women in AppSec Panel
| ||||
| 14:20 - 15:05 (45 mins) |
Security champions 2.0 | Alexander Antukh | Security champions is an interesting concept of scaling security in multi-team companies. During this presentation I'll share experience of building a team of champions, challenges we had to overcome, and metrics to evaluate the efficiency of the model. As a bonus, security champion playbook will be introduced to the audience. | ||
| 15:05 - 15:20 (15 mins) |
Coffee break | ||||
| 15:20 - 16:05 (45 mins) |
Man-in-the-browser attacks | Daniel Tomescu | Most of today's efforts towards securing web applications rely on securing the web server and providing users with web pages which are protected against common weaknesses over a secure channel. However, we often forget that web applications are client-server applications where the client is the web browser. Therefore, accessing a website is not safe as long as the web browser cannot be trusted.
How many web browsers do we use in a week or a month? Are those web browsers exposed to attacks? Do we trust our favourite web browsers? We will discover multiple attack scenarios and attack vectors which can endanger our browsing experience. Be warned, your relationship with your favourite web browser might suffer and trust issues might arise. | ||
| 16:05 - 16:50 (45 mins) |
How my SVM nailed your Malware | Nikhil.P.K | As we know the Android Application Industry from a security perspective, it is also quite well known that the Android platform is succeptible to malicious applications. And with the recent trend where all the vendors and customers going completely mobile, android has now become an attack surface for most of the malicious attacks. Moreover, the mechanisms used for android malware detection comprise of several known methods, and we also know that most of these mechanisms are permission based or based on API usage. This Project implementation is based on well known machine learning algorithm which is Support Vector Machines for solving the problem of android malware analysis. This method involves the mechanism of detection of android malware by effeciently embedding the functional call graphs along the feature map. The gamechanger in this concept would be the optimal utilization of the SVM Algorithm(Support Vector Machine) that proves to be better than other approaches with a minimalistic amount of false positives found and a higher detection rate. | ||
| 16:50 - 17:00 (15 mins) |
Closing ceremony | OWASP Bucharest team | CTF Prizes | ||
Conference agenda, 13th of October | |||||
| Time | Title | Speaker | Description | ||
| 9:00 - 9:30 (30 mins) |
Registration and coffee break | ||||
| 9:30 - 9:45 (15 mins) |
Introduction | Oana Cornea | Introduction to the OWASP Bucharest Event, Schedule for the Day | ||
| 9:45 - 10.30 (45 mins) |
Threat modelling – How we deconstruct systems and the threats they are at risk from | Mustafa Kasmani | The presentation focuses on plenty of great case studies in threat modelling – how we deconstruct systems and the threats they are at risk from. There will be implicit training in the form of practical exercises in how you calculate risk and accountability. Threat modelling also involves different disciplines in design, development and security so we expect the audience to join the conversation. | ||
| 10:45 - 11.30 (45 mins) |
Testing for cyber resilience: tools & techniques for adversary attack/defense simulation | Teodor Cimpoesu and Adrian Ifrim | We know that testing selected points around large infrastructures, combined with testing a subset of the enterprise applications (the critical ones) is no longer enough to match what is going on in the wild in terms of cyber risk.
Nowadays real attacks often go undetected for months, use modern tools & techniques, and the responders many times get overwhelmed by the complexity of analysis, time pressure, and the need to understand adversary tactics. | ||
| 11:45 - 12.30 (45 mins) |
Less Known Web Application Vulnerabilities | Ionut Popescu | Many application programs (including their testing strategies) rely on rather simple standards, sometimes even as simple as OWASP Top Ten. This often leads to a false sense of security – developers tend to believe that if they have worked their way through ready-made checklists and took proper care of the well-known topics like authentication, authorization or using parameterized queries, there should be no big surprises ahead. Nevertheless, the real world of application security is way more complicated than this. New attack vectors are being found on a regular basis and security standards and vulnerability libraries tend to get obsolete pretty fast. It’s nearly impossible to keep on track regarding all vulnerabilities which an application can be vulnerable to. | ||
| 12:30 - 13:30 (60 mins) |
Lunch/Coffee Break | ||||
| 13:30 - 14:15 (45 mins) |
Overview of TLS v1.3 | Andy Brodie | Transport Layer Secure (TLS), a.k.a. Secure Sockets Layer (SSL), is probably the most important security protocol used on the Internet today. It provides privacy, integrity and authentication for any two parties who want to have a secure conversation across the public Internet. Most popular websites and web services, and all online banking and payment services use TLS today, and the uptake is increasing as consumers demand more protection against both hackers and state agencies trying to monitor or interfere with communications. The TLS v1.3 specification, managed by the Internet Engineering Task Force (IETF), is currently on its 21st draft and is aiming to be ratified later this year. It marks the biggest change in the protocol since 1996 when SSL v3.0 was published. Rather than incremental additions and deprecations, features such as RSA key exchange, 3DES and session renegotiation have been removed completely and big efficiency gains can now be made from one-round-trip and even zero-round-trip handshakes. This talk will explain to the audience thee basics of TLS 1.3: the goals of the protocol and how it achieves them; what features have been added, removed and changed The talk is technical, but does not require knowledge or experience of cryptography or mathematics. | ||
| 14:20 - 15:05 (45 mins) |
Protecting against credential stuffing attacks | Cristian Opincaru, Catalin Manole, Razvan Matei |
Attackers have easy access to vast amounts of credentials from known breaches of major websites (ex. Yahoo: 1.5 billion credentials). Furthermore, automation tools specially crafted for ease of use, are readily available: Sentry.MBA (brute-forcer), ProxyScraper (scraper for open proxies), D3V Spider (credential scraper for Paste Bin). What’s more, tutorials are available on YouTube. This presentation will go through reactive and proactive measures that authentication systems can take to protect their users against credential stuffing. | ||
| 15:05 - 15:20 (15 mins) |
Coffee break | ||||
| 15:20 - 16:05 (45 mins) |
BDD Mobile security testing with OWASP MASVS, OWASP MSTG and Calabash | Davide Cioccia | Big companies only use mobile BDD tests to check that all the functionalities work. BDD security testing is becoming more and more important in the business panorama, where complex applications need to be tested continuously because part of continuous delivery (CD) and continuous integration (CD). Agile way of working requires more flexibility also in the security testing,so this means that a complete pentest at the end of the development is not enough anymore. OWASP MASVS and MSTG (Mobile Security Testing Guide), gives developers and security professionals hints on what to test and how. What if we can automate this tests directly in the development pipeline before building the application? Integrating together Cucumber, Calabash and Ruby is possible to create simple, medium and advanced security tests, automating the UI, accessing the Filesystem, Keychain, Databases, Logs in the background and check the memory on the fly. | ||
| 16:05 - 16:50 (45 mins) |
Securing the code and waiting for skilled hackers | Sergiu Zaharia | When code is analyzed and secured early in the development phase, the developers are really curious about the remaining channels that can be exploited by hackers.
Via this presentation we try to provide hints on the following topics:
| ||
| 16:50 - 17:00 (15 mins) |
Closing ceremony | OWASP Bucharest team | CTF Prizes | ||
 Panel discussion
Panel discussion
Presented by Iulia Ivanov
For 11 years Iulia Ivanov lives a transformational professional journey in the human resources field, accessing diverse organisation cultures like Heineken, Oracle, Samsung. Passionate about planning and career management counseling, focused on the young generation, Iulia follows a vocational calling in this area thru an all-inclusive practical approach:
- Studies a dedicated master program at the University of Psychology & Educational Sciences
- Collaborates closely with Fundatia Calea Victoriei whereas a public speaking lector she delivers the tailored workshop for the adolescents
Kicked-off a new partnership with the Aspire for Teachers academy in the role of Community Engagement Leader.
| Panelist | Bio | Photo |
|---|---|---|
| Giorgiana Vlăsceanu | Giorgiana Vlăsceanu has more than 8 years of experience in organizing events, she pursued the Bachelor degree at the Faculty of Automatic Control and Computers, UPB, where she is currently a Master student, studying Advanced Computer Architectures.. She is passionate about technology and teaching and she's a co-founder at Codette, the community for all Romanian women technologists, regardless of age, level of experience, or tech branch. Codette aims to develop events based on education, inclusion and personal development. Among the Codetteevents the ones which stand out the most are IoT4Girls, Codette Stories, Codette Travel Grant. | |
| Alexandra Anghel | Alexandra Anghel is the Co-founder & CTO at Appticles.com, a multi-channel mobile publishing platform, and Co-founder at Codette. She has a technical background, mostly in backend programming, and she has previously owned an outsourcing company. She's passionate about startups & entrepreneurship and likes to get involved in various activities to help women get into programming/coding. In 2012, she won the runner up award at Girls in Tech, Paris. In 2016, she graduated from the Prosper Women Entrepreneurs accelerator in the US. | |
| Daniela Ene | Daniela is a passionate software developer with a bachelor degree at the Faculty of Automatic Control and Computer Science, UPB. She has over 5 years of experience in developing java solutions for virtual machine management, investment banking and digital publishing. She is a curious person continuously looking to learn new technologies that can help at delivering a better user experience. In her spare time, she enjoys traveling, snowboarding, photography or reading random things about machine learning. | |
| Daniel Barbu | Daniel BARBU is a Ph.D candidate in the field of Information Security who brings passion into his daily tasks. He enjoyed learning and growing while working at Electronic Arts, Dell Secureworks and now Adobe. As a member of OWASP Bucharest Chapter and RAISA (Romanian Association for Information Security Assurance) , Daniel is constantly seeking opportunities to popularize information security. Daniel is currently managing a multi - role & diverse security team within TechOps Romania at Adobe where he focuses on the growth of the team members’ skill set. |
Workshop | |||||
| Time | Title | Trainers | Description | ||
| Workshop 13th of October 2 hours: begins at 10:30 Goga Room |
Threat Modelling a fictitious payment web application |
Mustafa Kasmani | Description: Following on from the Threat Modelling presentation by the same author, this workshop will aim to put the theory covered by that presentation into practice. The objective of doing so is to introduce the audience to the benefits of performing Threat Modelling on a system during the early stages of design / development. This ensures that key security threats are known and understood early on allowing remediation to be done in a more cost effective and pragmatic way than had they been found much later on during testing or when in production. A fictitious payment web application will be examined in this session – defining its business functionality, actors, assets and technology stack. Data flowing between the components will then be drawn out in the form of data-flow diagrams (DFD’s). Thereafter the attack-surface will be mapped out using the STRIDE methodology identifying threats pertaining to Spoofing, Tampering, Repudiation, Information disclosure, Denial of service and the Elevation of privilege. Finally, these will documented in a form allowing categorisation of risk together with identified security controls that should be tested. | ||
| Workshop 13th of October 3 hours: begins at 13:30 Goga Room |
AppSec Bucharest vs. OWASP Juice Shop |
Björn Kimminich | Description: In this *free* workshop you can test your skills in hacking modern web applications against the OWASP Juice Shop! There are 43+ challenge that are waiting to be solved, ranging from simple functional problems and the usual XSS/SQLi issues over severe authentication flaws to multi-step & multi-path attacks against the discount coupons issued by the application! How many challenges can you beat? During the workshop you can get some first-hand hints in case you fell stuck. At the end of the workshop there will be a demo of some of the more mindboggling challenges - but only for those, who don't want to solve them on their own later! You will have an idea how good you and your tools are with
| ||
| Workshop 13th of October 3 hours: begins at 9:30 Slavici Room |
Free Diving into Android Security |
Nikhil P Kulkarni and Ravi Kumar Kovela | Description: The agenda of this free workshop is to get the taste of working on Android Security. The workshop would involve the attendees to install and learn the tools used for android pentesting. The following would be the topics that would be covered during the 3 hour session:
Though not in-depth but this workshop would definitely give a great push to start into the Mobile Security Scene. At the end of the workshop, the attendees would be given few challenges to be solved, giving them an understanding and idea on how to find some of the very well-known Android Security Issues. Intended Audience: Application Developers, Penetration Testers who plan to get into the field of Mobile Pentesting with basic knowledge and understanding of the Android Operating System. Prerequisites:
Software Requirements:
Seats available: 20 (first-come, first served) | ||
Training | |||||
| Time | Title | Trainers | Description | ||
| 2 days training 11th and 12th of October daily: 9:00 - 17:00 |
Assessing and securing applications using the OWASP ASVS (Application Security Verification Standard) |
Oana Cornea | Description: The focus of this training will be on how to build secure applications and how to evaluate them using real world scenarios. The attendees will learn the concepts solving exercises and using various OWASP resources like the OWASP ASVS (Application Security Verification Standard) and the OWASP Testing Guide.
Topics covered:
Day 2:
| ||
Training | |||||
| Time | Title | Trainers | Description | ||
| 1 day training 11th of October daily: 9:00 - 17:00 |
OWASP Top 10 vulnerabilities – discover, exploit, remediate |
Adrian Furtună – Founder & Ethical Hacker – VirtualStorm Security and Ionuţ Ambrosie – Security Consultant – KPMG Belgium |
Description: The overall objective of this workshop is to increase the participants’ awareness on the most common web application vulnerabilities and their associated risks. We will discuss each type of vulnerability described in the OWASP Top 10 project and will teach participants manual discovery and exploitation techniques. Furthermore, a set of useful security testing tools will be introduced during the workshop. This is a hands-on workshop where participants will learn how to:
Moreover, we will discuss ways in which security can be better integrated into the software development lifecycle and how the OWASP Top 10 vulnerabilities can be avoided, identified early on or mitigated before they reach production environments.
Seats available: 20 (first-come, first served) | ||
CTF (Capture The Flag) contests are popular ways to hone your practical security skills by solving challenges on topics such as web, crypto, reverse, exploiting.
We invite everyone passionate about practical security at the OWASP AppSec 2017 CTF, where you and your team will solve challenges on web, reverse and exploiting. Challenges will be Linux-centric and web.
Please note that this is a competition designed for beginners, students and security enthusiasts.
Here are the important dates:
- The qualifiers are online on 9th of September, between 10:00 and 22:00 (Bucharest time, UTC+2). In order to participate please REGISTER HERE!
- The first 10 teams will be invited to the final.
- The final will be on 12th of October. The qualified teams that want to compete for the prizes must be on site, in the competition room.
The CTF webpage is here: https://owasp-ctf.security.cs.pub.ro/home .
The CTF final will take place during the OWASP Bucharest AppSec 2017 conference, on site, for 8 hours, from 9am to 5pm. Teams will consist of at most 5 players; everyone has to be on site at the conference.
The teams qualified for the final are:
| knights who say ni | 775 |
| penthackon | 350 |
| UPTimSec | 275 |
| StackOrSlack | 275 |
| Fuszuly | 225 |
| Shellphish | 225 |
| tum_cyber | 225 |
| ynot ro | 150 |
| Just a Hack | 75 |
| TimeXlord | 75 |
| Xor_the_World | 75 |
We would not cover any transport or accommodation costs for the final competitors, in order to attend the event on 12th of October.
Hope you can make it! You’ll have tons of fun!
If you’re new to CTFs or you want to know more please check these links:
- picoCTF (https://picoctf.com/): A good place for beginners to go through CTF tasks
- Computer and Network Security (http://ocw.cs.pub.ro/courses/cns): A masters class featuring concepts and tools on practical security
- Hack Night (https://github.com/isislab/Hack-Night): Training session run by the NYU Poly ISIS lab
- CTF Write-ups (https://github.com/ctfs/): Write-ups (solutions) for CTF contests arount the globe
- Online Wargames Bundle (http://security.cs.pub.ro/hexcellents/wiki/kb/practice-and-learning): A list of wargame sites you can use for honing your skills
Prizes:
- 1st place: 1024 euros
- 2nd place: 512 euros
- 3rd place: 256 euros
Capture the Flag (CTF) is a special kind of information security competition that touches on many aspects of information security.
If you are interested in practicing your skills, you are invited to participate in the SecureWorks CTF challenge. This competition is mainly addressed to beginners who are passionate about practical security.
This CTF encourages you to exploit web application vulnerabilities in order to gain access to the server.
In order to begin the registration process please follow the instructions found on this website: http://35.196.148.115/.
You are welcome to participate as an individual or as a team of 2. The maximum number of participants will be 14. Everyone will need to be on site and with a working laptop in order to participate. The prize for this challenge will be an iPad 2.
The competition will take place on October 13th. It will start at 13.30 PM and end at 16.30 PM, so you’ll have 3 hours to solve the challenges.
We’re looking forward to seeing you at the event!
Sponsors
Platinum+ Sponsor |
||||||

|
||||||
Platinum Sponsors |
||||||

|

|
|||||
Gold Sponsors |
||||||

|

|

|
||||
|   | ||||||
Event Supporters |
||||||

|

|

|
||||

|

|

|
||||
| |

|
|
||||

|

|
|
||||

|

|