This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Droid10 Project"
(→OWASP Droid 10) |
(→OWASP Droid 10) |
||
| (20 intermediate revisions by 2 users not shown) | |||
| Line 9: | Line 9: | ||
==OWASP Droid 10== | ==OWASP Droid 10== | ||
| − | Droid10 is a handheld system based (android) web pen testing tool. It can scan for web application bugs from any android device. The world is moving towards handheld systems . There isn't any mobile based tool from owasp to do web app pen testing from handheld systems . This app is going to be OWASP first ever mobile app to test web app security. Apart from this this tool will be developed in such a way that it can be customized in an easy way .User supplied vectors can be added easily . It will have encoders,decoders and they can be integrated with different modules easily example (Url encoding with XSS Module). In short this | + | # OWASP Droid10 |
| − | [[File: | + | |
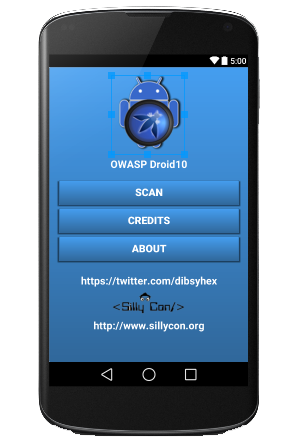
| + | OWASP Droid10 is an opensource handheld based (android) web pen testing tool. It can scan for web application vulnerability from any android device.Some features can be customized according to testers need. Droid10 is a handheld system based (android) web pen testing tool. It can scan for web application bugs from any android device. The world is moving towards handheld systems . There isn't any mobile based tool from owasp to do web app pen testing from handheld systems . This app is going to be OWASP first ever mobile app to test web app security. Apart from this this tool will be developed in such a way that it can be customized in an easy way .User supplied vectors can be added easily . It will have encoders,decoders and they can be integrated with different modules easily example (Url encoding with XSS Module). In short this project will have the combined features of modern day scanners as an a mobile app . | ||
| + | |||
| + | Some cool features list: | ||
| + | |||
| + | * Automated Scan - Automated Scan to find vulnearabilities | ||
| + | * Live Scan - Live View of results against attack vectors | ||
| + | * Repeater - Request / Response Tester | ||
| + | |||
| + | |||
| + | |||
| + | You too can extend the project | ||
| + | |||
| + | * Easy to add new modules | ||
| + | * Easy to add new vectors | ||
| + | * Easy to maintain | ||
| + | |||
| + | And this is still in development phase! | ||
| + | |||
| + | |||
| + | |||
| + | This is on [OWASP](https://www.owasp.org/index.php/OWASP_Droid10_Project) website. This project will soon be available in Google's Play Store. | ||
| + | |||
| + | |||
| + | If you would like to be a contributor to this project please [contact me](http://dibsy.github.io/). | ||
| + | |||
| + | Download and import this project in Android Studio to test all its features | ||
| + | |||
| + | [[File:Newdroid10.PNG]][[File:droid103.png]] | ||
==Description== | ==Description== | ||
| Line 24: | Line 52: | ||
== Project Resources == | == Project Resources == | ||
| − | + | Github[https://github.com/dibsy/OWASP_Droid10] | |
| − | |||
== Project Leader == | == Project Leader == | ||
| Line 33: | Line 60: | ||
== Related Projects == | == Related Projects == | ||
| − | + | [[OWASP_JSEC_CVE_Details]] | |
| − | |||
==Classifications== | ==Classifications== | ||
| Line 48: | Line 74: | ||
|- | |- | ||
| colspan="2" align="center" | [[File:Agplv3-155x51.png|link=http://www.gnu.org/licenses/agpl-3.0.html|Affero General Public License 3.0]] | | colspan="2" align="center" | [[File:Agplv3-155x51.png|link=http://www.gnu.org/licenses/agpl-3.0.html|Affero General Public License 3.0]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:sillycon.png|link=http://www.sillycon.org]] | ||
|} | |} | ||
| − | | valign="top" style="padding-left:25px;width:200px;" | | + | | valign="top" style="padding-left:25px;width:200px;" | |
| − | |||
== News == | == News == | ||
| Line 89: | Line 116: | ||
==Getting Involved== | ==Getting Involved== | ||
| − | + | ||
| − | |||
Some of the ways you can help are as follows: | Some of the ways you can help are as follows: | ||
| Line 101: | Line 127: | ||
=Minimum Viable Product= | =Minimum Viable Product= | ||
<!-- Instructions are in RED and should be removed from your document by deleting the text with the span tags.--> | <!-- Instructions are in RED and should be removed from your document by deleting the text with the span tags.--> | ||
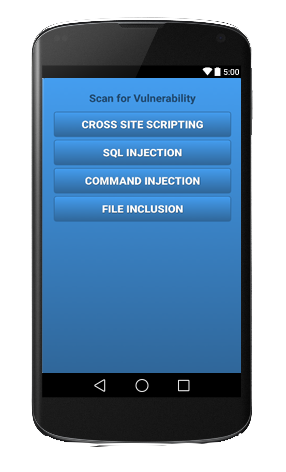
| − | + | The scanner has various module . Each module is independent of other . The project will be extended by adding more modules to it. | |
| − | |||
| − | |||
| − | |||
Latest revision as of 22:25, 8 March 2015
|
OWASP Droid 10
OWASP Droid10 is an opensource handheld based (android) web pen testing tool. It can scan for web application vulnerability from any android device.Some features can be customized according to testers need. Droid10 is a handheld system based (android) web pen testing tool. It can scan for web application bugs from any android device. The world is moving towards handheld systems . There isn't any mobile based tool from owasp to do web app pen testing from handheld systems . This app is going to be OWASP first ever mobile app to test web app security. Apart from this this tool will be developed in such a way that it can be customized in an easy way .User supplied vectors can be added easily . It will have encoders,decoders and they can be integrated with different modules easily example (Url encoding with XSS Module). In short this project will have the combined features of modern day scanners as an a mobile app . Some cool features list: * Automated Scan - Automated Scan to find vulnearabilities * Live Scan - Live View of results against attack vectors * Repeater - Request / Response Tester
* Easy to add new modules * Easy to add new vectors * Easy to maintain And this is still in development phase!
This is on [OWASP](https://www.owasp.org/index.php/OWASP_Droid10_Project) website. This project will soon be available in Google's Play Store.
Download and import this project in Android Studio to test all its features DescriptionThe file will be available in form of apk file which runs on android device . This file can be downloaded from the github / owasp site / Google's app store . LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the link GNU Affero General Public License 3.0 as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. |
Project ResourcesGithub[1] Project LeaderRelated ProjectsClassifications
|
News | |||||||||
How can I participate in your project?
All you have to do is make the Project Leader's aware of your available time to contribute to the project. It is also important to let the Leader's know how you would like to contribute and pitch in to help the project meet it's goals and milestones. There are many different ways you can contribute to an OWASP Project, but communication with the leads is key.
If I am not a programmer can I participate in your project?
Yes, you can certainly participate in the project if you are not a programmer or technical. The project needs different skills and expertise and different times during its development. Currently, we are looking for researchers, writers, graphic designers, and a project administrator. See the Road Map and Getting Involved tab for more details.
Roadmap
Currently all owasp tools are running on pc . The world is moving towards handheld systems . There isn't any mobile based tool from owasp to do web app pen testing from handheld systems . This app is going to be OWASP first ever mobile app to test web app security. Apart from this this tool will be developed in such a way that it can be customized in an easy way .User supplied vectors can be added easily . It will have encoders,decoders and they can be integrated with different modules easily example (Url encoding with XSS Module). In short this app will have the combined features of modern day scanners with an added mobility & easy customization feature . The application will be opensource . So others can fork and extend and contribute easily .
Getting Involved
Some of the ways you can help are as follows:
Coding
Localization
Testing
Feedback
The scanner has various module . Each module is independent of other . The project will be extended by adding more modules to it.