This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "AppSecAsiaPac2014"
(Updated sponsorship documents.) |
|||
| (66 intermediate revisions by 5 users not shown) | |||
| Line 5: | Line 5: | ||
! width="500" align="center" | <br> | ! width="500" align="center" | <br> | ||
|- | |- | ||
| − | | align="center" | [[Image:AppSecAPAC_2014.JPG| | + | | align="center" | [[Image:AppSecAPAC_2014.JPG|1150px| link=]] |
| align="center" | | | align="center" | | ||
|} | |} | ||
| − | + | {{Social Media Links}} | |
=WELCOME= | =WELCOME= | ||
| − | + | <br> | |
| − | |||
| − | |||
| − | |||
| + | '''日本語サイト Appsec APAC 2014 Japanese site''': '''[https://appsecapac.org/2014/ https://appsecapac.org/2014/]''' | ||
| + | <br> | ||
| + | <br> | ||
| + | '''We are pleased to announce that the OWASP Japan chapter will host the OWASP AppSec APAC 2014 conference in Tokyo, Japan at the Sola City Conference Center.''' | ||
| + | <br> | ||
| + | <br> | ||
'''The event will be composed of 2 days of training (March 17-18), followed by 2 days of conference talks (March 19-20).''' | '''The event will be composed of 2 days of training (March 17-18), followed by 2 days of conference talks (March 19-20).''' | ||
| − | |||
| − | |||
The Global AppSec APAC 2014 Conference will be a reunion of Information Security Asia-Pacific leaders, and will present cutting-edge ideas. | The Global AppSec APAC 2014 Conference will be a reunion of Information Security Asia-Pacific leaders, and will present cutting-edge ideas. | ||
OWASP events attract a worldwide audience interested in “what’s next”. The conference is expected to draw 250-300 technologists from Government, Financial Services, Media, Pharmaceuticals, Healthcare, Technology, and many other verticals. | OWASP events attract a worldwide audience interested in “what’s next”. The conference is expected to draw 250-300 technologists from Government, Financial Services, Media, Pharmaceuticals, Healthcare, Technology, and many other verticals. | ||
<br> | <br> | ||
<br> | <br> | ||
| − | + | '''Should you want to REGISTRE FOR A TRAINING SESSION please send an e-mail to [mailto:[email protected] [email protected]]''' | |
| − | '''Conference Registration is | + | <br> |
| + | <br> | ||
| + | '''Conference Registration is CLOSED''' | ||
<br> | <br> | ||
<br> | <br> | ||
| − | + | '''Who Should Attend Global AppSec APAC 2014:''' | |
| − | Who Should Attend Global AppSec APAC 2014: | ||
*Application Developers | *Application Developers | ||
*Application Testers and Quality Assurance | *Application Testers and Quality Assurance | ||
| Line 41: | Line 43: | ||
If you have any questions, please email the conference committee: '''[mailto:[email protected] [email protected]]''' | If you have any questions, please email the conference committee: '''[mailto:[email protected] [email protected]]''' | ||
| − | <br> | + | <br><br> |
| − | + | '''OWASP PodCast 24/7''' | |
| − | + | * '''[https://soundcloud.com/owasp-podcast/2014-appsec-apac-history-and Riotaro Okada and Robert Dracea talking about the upcoming 2014 AppSec APAC Conference in Tokyo]''' | |
| + | * '''[http://trustedsoftwarealliance.com/2014/01/14/appsec-apac-2014-with-tobias-gondrom-what-to-expect/ AppSec APAC 2014 with Tobias Gondrom – What To Expect]''' | ||
| + | =TEAM= | ||
| + | ==Global AppSec APAC 2014 Executive Committee== | ||
'''Riotaro Okada''' | '''Riotaro Okada''' | ||
| − | Researcher. Born in Kobe, Hyogo Prefecture, Japan, Mr. Okada has over 20 years of experience in software development and network construction. He has been involved in network construction, software development and the implementation of information security measures at independent software development companies, the R&D divisions of manufacturing companies as well as consulting firms. Mr. Okada has also facilitated various technology-related communities such as for Linux and PHP. In 2004, he founded the Web Application Security Forum and as a member of the board became involved in the diffusion of security-related information. Moreover, he | + | Researcher. Born in Kobe, Hyogo Prefecture, Japan, Mr. Okada has over 20 years of experience in software development and network construction. He has been involved in network construction, software development and the implementation of information security measures at independent software development companies, the R&D divisions of manufacturing companies as well as consulting firms. Mr. Okada has also facilitated various technology-related communities such as for Linux and PHP. In 2004, he founded the Web Application Security Forum and as a member of the board became involved in the diffusion of security-related information. Moreover, he was also a researcher at the Information-technology Promotion Agency, Japan (IPA) for 8 years, and responsible for the IT strategy as well as disaster response projects at various government organizations. Mr. Okada is the co-leader of OWASP Japan since its founding, is CISA certified and holds an MBA from BBT (2009). |
<br> | <br> | ||
| Line 64: | Line 69: | ||
'''Robert Dracea''' Mr. Dracea is responsible for the global strategy of a Japanese internet service company. With the mission of better sharing Japan’s advanced technological power with the world, from a business perspective, he has successfully architected numerous alliances and tie-ups both domestically in Japan as well as overseas. Additionally, he has also, on a volunteer-basis, conducted the translation and interpretation at multilingual OWASP Meetings. Mr. Dracea has been since its founding a member of the OWASP Japan Advisory Board. | '''Robert Dracea''' Mr. Dracea is responsible for the global strategy of a Japanese internet service company. With the mission of better sharing Japan’s advanced technological power with the world, from a business perspective, he has successfully architected numerous alliances and tie-ups both domestically in Japan as well as overseas. Additionally, he has also, on a volunteer-basis, conducted the translation and interpretation at multilingual OWASP Meetings. Mr. Dracea has been since its founding a member of the OWASP Japan Advisory Board. | ||
| + | <br> | ||
| + | <br> | ||
| + | |||
| + | ==Program Selection Committee== | ||
| + | |||
| + | '''Youki Kadobayashi, Ph.D.''' | ||
| + | Associate professor at Nara Institute of Science and Technology (NAIST). After being employed at Osaka University’s Cybermedia Center, Dr. Kadobayashi joined his current position in 2000. Since 2008 he has been involved in cyber security standardization at the International Telecommunications Union Telecommunications Standardization Sector. Dr. Kadobayashi is also actively involved in cyber security education and training programs. Additionally, he is a board member of the industry-academic-government collaborative research consortium WIDE Project and since 2013 the Japanese representative of the American-Japanese international joint research project FP7 NECOMA Project. Dr. Kadobayashi is also a member of the executive committee for the WASForum Hardening Project. | ||
| + | <br> | ||
| + | |||
| + | '''Masakazu Takahashi''' | ||
| + | Chief Security Advisor, Microsoft Japan. | ||
| + | After being involved in standard library, OS development and other basic development, Mr. Takahashi became involved in the security business after engaging in vulnerability assessment and intrusion detection at a security company. | ||
| + | At a time when penetration testing was a common practice in vulnerability assessment, Mr. Takahashi became a proponent of white box testing as a logical and repeatable inspection method. In terms of intrusion detection, he oversaw the systemization of surveillance and operations technologies and was in charge of starting numerous SOC businesses. | ||
| + | In November of 2006, Mr. Takahashi joined Microsoft Japan. As the chief security advisor, he is involved in attaining the secure computing that Microsoft aims for while at the same time publishing papers and conducting various lectures. | ||
| + | Additionally, Mr. Takahashi is actively involved in associations within the industry and is the head of a community involved in the promotion of information security measures as well as the vice president of the Japan Network Security Association (JNSA). | ||
| + | <br> | ||
| + | |||
| + | '''Keiji Takeda, Ph.D.''' | ||
| + | Lecturer at Keio University, Faculty of Environment and Information Studies. | ||
| + | Ph.D. from Keio University Graduate School of Media and Governance. After being employed at the Ministry of Defense, the Japan Air Self-Defense Force and Accenture, Dr. Takeda became a lecturer at Carnegie Mellon University’s school in Japan before moving on to his current position. Dr. Takeda is also a member of various information security-related committees including participating as an advisor for the Hyogo Prefectural government. In addition, he is actively involved in the information security industry through a broad array research & development, operations, personnel training and consulting activities including development assessment of intrusion detection systems, participation at various security events and the planning of organizations for the distribution of information related to security vulnerabilities. | ||
| + | <br> | ||
| + | |||
| + | '''Masafumi Negishi''' | ||
| + | Senior Engineer, Office of Emergency Response and Clearinghouse for Security Information, Internet Initiative Japan Inc. | ||
| + | Mr. Negishi has been involved in network construction, security inspection and security consulting, etc. at a major electronics manufacturer, a security company and foreign-affiliated computer vendor. In 2003 he became employed at IIJ Technology and placed in charge of security services, overseeing numerous security inspections. Currently he is part of the security incident support team and is primarily responsible for the collection and analysis of security information as well as taking appropriate action when security issues are discovered. Since 2007 he has been an instructor at the SANS Institute and since 2012 he has also been a member of the Advisory Board for OWASP Japan. | ||
| + | <br> | ||
| + | '''Yoshinari Fukumoto''' | ||
| + | System Security Office Manager, Rakuten Inc. | ||
| + | After being involved in research and development of security products at a security-related company, in 2002 Mr. Fukumoto joined Rakuten and became responsible for the internet service security for Rakuten Group. He is primarily involved in the promotion and development of secure software as well as the support of security-related operations. Mr. Fukumoto is also a Rakuten-CERT Representative. He has been a member of the OWASP Japan Advisory Board since the chapter began its activities. | ||
| Line 70: | Line 104: | ||
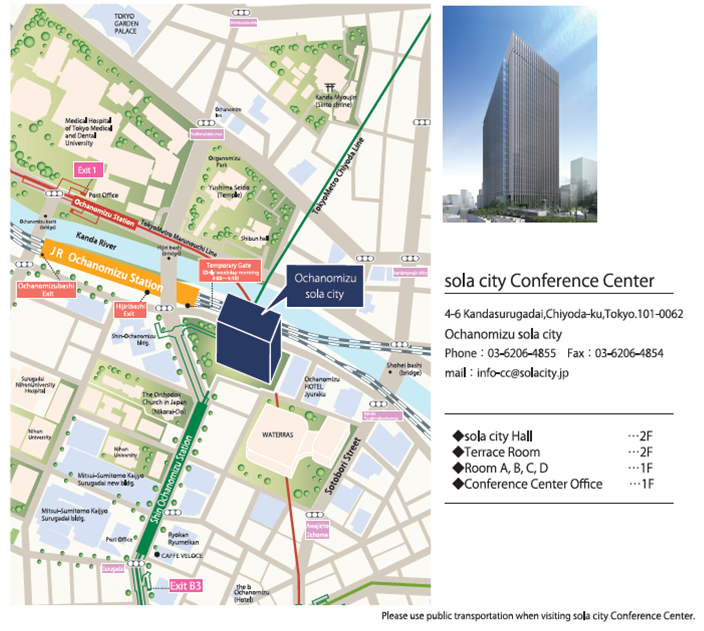
'''AppSec APAC 2014 will be held at the SOLA CITY CONFERENCE CENTER in Tokyo, Japan'''.<br> | '''AppSec APAC 2014 will be held at the SOLA CITY CONFERENCE CENTER in Tokyo, Japan'''.<br> | ||
| + | |||
| + | [https://plus.google.com/110347373259238043803/about?hl=en Google Map of SCCC] | ||
| Line 76: | Line 112: | ||
| − | = | + | =HOW TO GET THERE= |
| + | '''TOKYO''' has two international airports, Tokyo International Airport (Haneda: HND) and Narita International Airport (NRT).<br> | ||
| + | Both airports are located away from the city center but Haneda is the closer of the two.<br><br> | ||
| − | + | We advise against taking a taxi from the airport since it is farther and more expensive than you might expect. To avoid high costs take the train or bus to the nearest station to your hotel or destination and then take a taxi if needed.<br>'''Please find out what the best way to reach your destination is before arriving.''' | |
| + | <br> | ||
| + | <br> | ||
| + | [[Image:Train.png |left|150px|caption]] '''From Tokyo International Airport to Tokyo Station (HND: Haneda)''' | ||
| + | * Train http://www.haneda-airport.jp/inter/en/access/train.html | ||
| + | * Take either the Tokyo Monorail to Hamamatsucho Station (JPY 470, 23 min) or the Airport Limited Express to Keikyu Shinagawa Station (JPY 400, 22 min) <br> | ||
| + | '''From Narita International Airport to Tokyo Station (NRT: Narita)''' | ||
| + | * Train http://www.narita-airport.jp/en/access/train/index.html | ||
| + | * Take the Narita Express to Tokyo Station [approx. JPY 3,000 or JPY 4,500 for Green Car (first class), approx. 1 hour] | ||
| + | <br> | ||
| + | <br> | ||
| + | [[Image:Bus.png |left|150px|caption]] '''Taking the bus to Tokyo Station''' | ||
| + | * From Haneda http://www.haneda-airport.jp/inter/en/access/bus.html | ||
| + | * From Narita http://www.narita-airport.jp/en/access/bus/index.html | ||
| + | <br> | ||
| + | There are numerous buses going to Tokyo Station and various locations and some may take you very close to your hotel or other destination. Some buses go directly to major hotels. | ||
| + | Please find out what your nearest station is and chose the appropriate bus from the list at the URL found above.<br> | ||
| + | <br> | ||
| + | Depending on where your hotel is, you may choose to continue on by train or take a taxi.<br><br> | ||
| + | [[Image:Taxi.png |left|150px|caption]] '''Taxis in Tokyo:''' | ||
| + | Taxis in Japan are extremely reliable and you generally do not have any problems.<br> | ||
| + | To avoid language issues, have the name and address of your hotel, or Sola City Conference Center and other destinations written (with a map if possible) and keep it handy at all times to show it to the driver. | ||
| + | [[Image:Taxi_availabe.png |right|100px|caption]]* Taxis can be found at taxi waiting areas or you can hail an empty cab (indicated by the red “空車” light in the front window).<br><br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
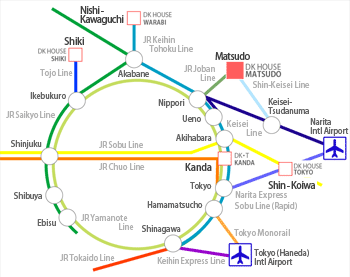
| + | The JR Yamanote Line or any stations within the Yamanote Line circle are considered '''downtown Tokyo'''.<br> | ||
| + | The venue, '''Sola City Center''', is close to Ochanomizu-Station on the JR Chuo-Line. | ||
| + | [[Image:Metro_map_Tokyo.png|center|800px|caption]] | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | <br> | ||
| + | = HOTEL RESERVATIONS= | ||
| + | <br> | ||
| + | Tokyo boasts a variety of accommodations from Ryoakans to full-service hotels and luxury inns. '''Rooms may go fast on the conference days, so book early for best availability!''' | ||
| + | <br><br> | ||
| + | The conference venue, [http://solacity.jp/cc/access/index.html Sola City Conference Center], is located in Tokyo Central Region, Kanda/Akihabara/Ochanomizu area. The closest train station is Ochanomizu Station. | ||
| − | + | As the conference venue is not a hotel, you must reserve your accommodation. The venue is really close to JR Ochanomizu Station, and Tokyo Metro Shin-Ochanomizu station which is at the heart of downtown Tokyo. | |
| + | Because of the central location, you can reach the venue relatively easily from any area in downtown Tokyo like Akihabara, Kanda and Nihonbashi, so feel free to book your hotel using any web site you like. | ||
| + | <br><br> | ||
| + | For your help: | ||
| + | * Hotel Reservation in Tokyo: [http://japanican.com/en/hotel/list/A27/?AFF=GMTCD Japanican Site] | ||
| + | * Hotel reservation near the Conference Venue (Ochanomizu area): [http://japanican.com/en/hotel/list/A27/130103/?navcheckin=&navcheckout=&sn=1&rn=1&apn=2&hcpn=0&cbn=0?AFF=GMTCD Japanican Site for Ochanomizu Area] | ||
| − | + | Alternatively, if you would like to book your accommodation by contacting JTB Global Marketing and Travel they will be happy to help you with your hotel booking and provide assistance organizing your time in Tokyo. | |
| − | ---- | + | * E-mail: [email protected] |
| + | * Phone: +81-3-5796-5445 | ||
| + | * FAX:+81-3-5495-0685 | ||
| − | + | =REGISTRATION= | |
| − | + | <br> | |
| − | + | '''OWASP AppSec APAC features two days of training March 17-18, and two days of talks, March 19-20, 2014.'''<br> | |
| − | + | <br> | |
| − | + | == '''Training Sessions Registration''' == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | '''Should you want to register for a Training Session please send an e-mail to [mailto:laura.[email protected] [email protected]]'''<br> | |
| − | '' | ||
<br> | <br> | ||
| − | + | '''Training Sessions Registration Fees''' ''(Please note that conference Registration is separate.)'' | |
| − | |||
| − | |||
| − | '''Training Fees''' ''(Please note that conference Registration is separate.)'' | ||
---- | ---- | ||
{| class="wikitable" | {| class="wikitable" | ||
| Line 137: | Line 199: | ||
| $800 USD <span style="color:blue"> (80,000 Yen)</span> | | $800 USD <span style="color:blue"> (80,000 Yen)</span> | ||
|} | |} | ||
| − | '' | + | ''Payment will be processed in Japanese Yen but we can process invoice in USD or other currencies.''<br> |
| + | <br> | ||
<br> | <br> | ||
| + | =='''Conference Registration ''' == | ||
| + | |||
| + | Conference on-line registration is '''CLOSED'''<br> | ||
| + | <br> | ||
| + | '''Conference Registration Fees''' ''(not including training)'' | ||
| + | ---- | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! scope="col"| Ticket price | ||
| + | ! scope="col"| On-site Fee | ||
| + | |- | ||
| + | ! scope="row"| Active OWASP member | ||
| + | | $400 USD <span style="color:blue"> (40,000 Yen)</span> | ||
| + | |- | ||
| + | ! scope="row"| Non-Member | ||
| + | | $450 USD <span style="color:blue"> (45,000 Yen)</span> | ||
| + | |- | ||
| + | ! scope="row"|Student | ||
| + | | $120 USD <span style="color:blue"> (12,000 Yen)</span> | ||
| + | |} | ||
| + | ''Payment will be processed in Japanese Yen but we can process invoice in USD or other currencies.''<br> | ||
| + | <br> | ||
'''Cancellations, Refunds, and Substitutions''' | '''Cancellations, Refunds, and Substitutions''' | ||
| Line 155: | Line 241: | ||
| − | = | + | = TRAINING SESSIONS= |
| − | |||
| − | == | + | == Monday and Tuesday, March 17th - 18th == |
| − | + | *'''''Mobile Security: Securing Mobile Devices & Applications''''' _ ENGLISH <br> | |
| + | '''Dave Wichers'''<br> | ||
| + | ROOM A 10am-5pm<br><br> | ||
| + | ''Mobile applications enable new threats and attacks which introduce significant risks to the enterprise, and many custom applications contain significant vulnerabilities that are unknown to the team that developed them.'' | ||
| + | ''Considering the number of mobile applications available in the Google Play and Apple AppStore is nearing 1.5 million and vulnerabilities are skyrocketing it is imperative to perform typical application security practices. But, how is mobile different?''<br> | ||
| + | ''This two-day, hands-on course enables students to understand how easily mobile devices and applications can be successfully attacked. They will learn how to identify, avoid and remediate common vulnerabilities by walking through a threat analysis and learning critical security areas such as those identified in the OWASP Top Ten Mobile Risks and Controls. Using state-of-the-art testing tools, students will learn how to secure mobile devices across the enterprise. Students will be able to choose from iOS or Android hands-on labs throughout the course, while they learn how easily the bad guy can compromise applications and the data they contain.''<br> | ||
| − | |||
| − | |||
| − | ''' | + | == Monday, March 17th== |
| + | * '''''Secure Web Development''''' _ ENGLISH<br> | ||
| + | '''Jerry Hoff'''<br> | ||
| + | ROOM B 10am-6pm<br><br> | ||
| + | ''Web application security is the #1 security issue for most enterprises today. This class goes through fundamental security principles for Java and .NET web developers, focusing on secure development practices.''<br> | ||
| + | ''This highly interactive, intensive 2-day class provides essential Java application security training for developers, architects and software testers. The class is a combination of lecture, hands-on development and code review. Instructor bring years of hands-on security experience, and provide invaluable insight from numerous security assessments.'' | ||
| + | ''Participants will not only learn the most common threats against web applications, but more importantly they will learn how to also fix the problems via control based code samples and review. Each student will have their own web application they will secure and test. This class is suitable for web application software engineers, web quality assurance engineers, and web architects''. | ||
| + | ''Focus will be put on covering not only the OWASP Top 10, but other common web vulnerabilities that plague modern web applications. Participants will gain a strong knowledge of web vulnerabilities, how vulnerabilities are exploited, and what security controls need to be in place to write defensible applications. Emphasis will also be placed on how these secure coding techniques relate to mobile, secure API development, and how security can be introduced throughout the SDLC.''<br> | ||
| − | |||
| − | |||
| − | |||
| − | ''' | + | * '''''Hands on Simple method of the penetration testing using OWASP ZAP''''' _ JAPANESE<br> |
| − | + | '''Minoru Sakai''' and '''Yuho Kameda'''<br> | |
| − | + | ROOM C 10am - 6pm <br><br> | |
| − | + | ''This course goes through automated security testing from OWASP tools.''<br> | |
| − | + | ''Tools:''<br> | |
| − | + | ''OWASP Zed Attack Proxy''<br> | |
| − | + | ''OWASP Broken Web Applications''<br><br><br> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == | + | == Tuesday, March 18th == |
| − | |||
| − | : | + | * '''''CISO training: Managing Web & Application Security – OWASP for senior managers''''' _ ENGLISH<br> |
| − | + | '''Tobias Gondrom'''<br> | |
| − | + | ROOM C 10am - 6pm <br> <br> | |
| − | + | ''Managing and improving your global information security organization, Leverage OWASP and common best practices to improve your security programs and organization. Achieving cost-effective application security, bringing it all together on the management level.'' | |
| − | + | ''Considering the number of mobile applications available in the Google Play and Apple AppStore is nearing 1.5 million and vulnerabilities are skyrocketing it is imperative to perform typical application security practices. But, how is mobile different?''<br> | |
| − | + | ''This two-day, hands-on course enables students to understand how easily mobile devices and applications can be successfully attacked. They will learn how to identify, avoid and remediate common vulnerabilities by walking through a threat analysis and learning critical security areas such as those identified in the OWASP Top Ten Mobile Risks and Controls. Using state-of-the-art testing tools, students will learn how to secure mobile devices across the enterprise. Students will be able to choose from iOS or Android hands-on labs throughout the course, while they learn how easily the bad guy can compromise applications and the data they contain''.<br> | |
| − | |||
| − | |||
| − | |||
| − | '' | + | * '''''Developer Security Training''''' _ FREE TRAINING _ ENGLISH<br> |
| + | '''Jim Manico'''<br> | ||
| + | ROOM B 1pm - 6pm <br><br> | ||
| + | ''This free training session will teach a developer about the fundamentals of secure software development practices. The session is a fast-paced combination of lecture, security testing and code review. This class will also highlight production quality API's from various languages, frameworks, and 3rd party libraries that provide production quality and scalable security controls''. <br> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | = CONFERENCE SESSIONS= | |
| − | |||
| − | |||
| − | + | All conference session will be translated into English - Japanese. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ''' | + | [http://owaspappsecapac2014.sched.org/?iframe=no '''Conference Schedule'''] |
| − | |||
| − | |||
| − | |||
| − | + | == Wednesday, March 19th == | |
| − | |||
| − | |||
| − | |||
| − | + | PLENARY SESSIONS: | |
| − | + | * 10.00am-10.30am Welcome Address and Openening Remarks (Riotaro Okada & Tobais Gondrom) | |
| − | + | * 10.30am-11.20am KEYNOTE (Suguru Yamaguchi) | |
| + | * 11.30am-12.20pm OWASP Top 10 - 2013. KEYNOTE ([[User:Wichers|Dave Wichers]])<br><br> | ||
| + | TRACK A: | ||
| + | * 1.30pm-2.20pm The OWASP Proactive Controls. (Jim Manico) | ||
| + | * 2.30pm-3.20pm OWASP documents for every people.(Chia-Lung Albert Hsieh) | ||
| + | * 4.00pm-4.50pm 12 Case Studies for the Access Controls of Web Application. (Takashi Honda) | ||
| + | * 5.00pm-5.50pm Get Ready for the Next Big Wave of Attacks: Hacking of Leading CMS Systems. (Helen Bravo, Sanjay Agnani)<br><br> | ||
| + | TRACK B: | ||
| + | * 1.30pm-2.20pm Why OWASP AppSensor is the future of Application Security, and why you should be using it. (Dennis Groves) | ||
| + | * 2.30pm-3.20pm Inside Story of the first SaaS type WAF Service. (Kana Toko) | ||
| + | * 4.00pm-4.50pm The Art and Science of Configuring SSL. (Nick Galbreath) | ||
| + | * 5.00pm-5.50pm Bad Web Apps are Good – The Broken Web Application Project. (Mordecai Kraushar)<br><br> | ||
| + | TERRACE ROOM | ||
| + | * 1.30am-2.20pm Women in AppSec | ||
| + | * 2.30pm-3.20pm OWASP Japan | ||
| + | * 4.00pm-4.50pm The fact report of attack traffic on the Internet. (Makoto Niimura) | ||
| + | * 5.00pm-5.50pm The investigation of Web Application Vulnerabilities in Japan. (Koki Takahashi) | ||
| + | == Thursday, March 20th == | ||
| + | TRACK A: | ||
| + | * 9.30am-10.20am eXtend Security on Xcode. (Tokuji Akamine, Raymund Pedraita) | ||
| + | * 10.30am-11.20am Getting a handle on mobile security. (Jerry Hoff) | ||
| + | * 11.50am-12.40pm Preinstalled Android application poisoning. (Yoshitaka Kato)<br><br> | ||
| + | TRACK B: | ||
| + | * 9.30am-10.20am HTML 5 Security for Web Application Development. (Yoshinori Matsumoto) | ||
| + | * 10.30am-11.20am XSS Allstars from Japan. (Yosuke Hasegawa, Masato Kinugawa, Mala) | ||
| + | * 11.50am-12.40pm Secure Escaping method for the age of HTML 5. (Yoshinori Takesako)<br><br> | ||
| + | TERRACE ROOM | ||
| + | * 9.30am-10.20am Management for Security Life Cycle. (Shoji Ito) | ||
| + | * 10.30am-11.20am How to choose (or write) your own source code scanner. (Yu-Lu “Chris” Liu) | ||
| + | * 11.50am-12.40pm OWASP Japan (Open Mic Session)<br><br> | ||
| + | PLENARY SESSIONS: | ||
| + | * 1.40pm-2.30pm 1 user, 10 places, 100 seconds. (Matias Madou) | ||
| + | * 2.40pm-3.30pm DevOps. (Dave Wichers) | ||
| + | * 4.00pm-4.50pm KEYNOTE (Michael Coates) | ||
| + | * 5.00pm-5.30pm Closing Remarks (Tobias Gondrom & Riotaro Okada)<br><br> | ||
| − | = SPEAKERS = | + | = KEYNOTE SPEAKERS & OWASP BOARD MEMBER= |
==Keynote Speaker== | ==Keynote Speaker== | ||
| Line 294: | Line 390: | ||
[http://www.linkedin.com/in/gondrom LinkedIn Tobias Gondrom] | [http://www.linkedin.com/in/gondrom LinkedIn Tobias Gondrom] | ||
| + | |||
| + | =WOMEN IN APPSEC= | ||
| + | |||
| + | |||
| + | == The deadline to apply for the Women in AppSec Program for AppSec APAC has been extended until March 7th, 2014. == | ||
| + | <br> | ||
| + | <br> | ||
| + | Attendance for one woman to the '''OWASP AppSec APAC 2014''' conference, and at least one of the in-depth training sessions, will be the award for this year’s winner. The Women in AppSec Program was successfully launched at AppSec USA in 2011 and this year’s event hopes to build on that trend and further engage women in the community.<br><br> | ||
| + | |||
| + | We encourage you to take advantage of this opportunity by applying as soon as possible if you are a woman either in the software security industry, or interested in learning more about the software security industry. | ||
| + | <br><br> | ||
| + | If you are interested please use the [https://docs.google.com/a/owasp.org/forms/d/1DFNkq2RhBViYD1ItlW8rimE8rSNPIKGW3e23vQPvNlw/viewform '''APPLICATION FORM'''] to send us your details. <br><br> | ||
| + | |||
| + | OWASP’s current program objective is to encourage female students at both the undergraduate and graduate levels, instructors, and professional working-women who are dedicated to a career in information security and/or application development, to expand their skills and pursue application security. <br><br> | ||
| + | {| | ||
| + | |- | ||
| + | ! width="400" align="left" | | ||
| + | ! width="400" align="left" | | ||
| + | |- | ||
| + | | align="left" | [[Image:Owasp_summit.jpg|left|250px]] <br/> | ||
| + | | align="left" | [[Image:WIAS01.JPG|left|300px]] | ||
| + | | align="left" | [[Image:IMG_5579.JPG|left|325px]] | ||
| − | + | |} | |
| + | <br><br><br><br><br> | ||
| − | |||
| − | |||
| − | |||
| − | ==We are looking for | + | |
| + | =SPONSORSHIP OPPORTUNITIES = | ||
| + | |||
| + | ==We are looking for Silver and 'A La Carte" Sponsors for the Global AppSec APAC 2014.== | ||
<br> | <br> | ||
| Line 332: | Line 451: | ||
'''OWASP AppSec APAC 2014 Premium Sponsorship Menu''' on the following package.<br> | '''OWASP AppSec APAC 2014 Premium Sponsorship Menu''' on the following package.<br> | ||
| − | Download Sponsor Package(Updated 2014. | + | Download Sponsor Package(Updated 2014.2.20): '''[https://www.owasp.org/images/d/d8/OWASP-sponsorship2014-v2.0-English.pdf English]''' | |
| − | '''[https://www.owasp.org/images/ | + | '''[https://www.owasp.org/images/c/cd/OWASP-sponsorship2014-v2.0-Japanese.pdf Japanese]''' |
| + | <headertabs/> | ||
| + | == '''SPONSORS''' == | ||
| + | |||
| + | <h2>Diamond Sponsors</h2> | ||
| + | <p align=center> | ||
| + | [[Image:Hp_sl.png|300px|link=http://www8.hp.com/jp/ja/home.html]] | ||
| + | [[Image:Scsk_sl.png|300px|link=http://www.scsk.jp/index_en.html]] | ||
| + | </p> | ||
| + | <h2>Platinum Sponsors</h2> | ||
| + | <p align=center> | ||
| + | [[Image:Iwi_sl.png|250px|link=http://www.iwi.co.jp/en/ ]] | ||
| + | [[Image:Sst_sl.png|250px|link=http://www.securesky-tech.com/ ]] | ||
| + | [[Image:Techmatrix_sl.png|250px|link=https://www.techmatrix.co.jp/eng/index.html ]] | ||
| + | </p> | ||
| + | <h2>Gold Sponsors</h2> | ||
| + | <p align=center> | ||
| + | [[Image:Arxan sl.png|200px|link=http://www.arxan.com/ ]] | ||
| + | [[Image:Cigital sl.png|200px|link=http://www.cigital.com/]] | ||
| + | [[Image:Cyberagent_sl.png|200px|link=http://www.cyberagent.co.jp/en/]] | ||
| + | </p> | ||
| + | <p align=center> | ||
| + | [[Image:Iij_sl.png|200px|link=http://www.iij.ad.jp/en/index.html ]] | ||
| + | [[Image:Lac_sl.png|200px|link=http://www.lac.co.jp/corporate/index_en.html ]] | ||
| + | [[Image:Nec_sl.png |200px|link=http://www.nec.com/ ]] | ||
| + | </p> | ||
| + | <p align=center> | ||
| + | [[Image:Panasonic sl.png |200px|link=]] | ||
| + | [[Image:Rakuten_sl.png|200px|link=http://www.rakuten.co.jp/]] | ||
| + | [[Image:Si_sl.png|200px|link=https://securityinnovation.com/]] | ||
| + | [[Image:Sony-dna_sl.png|200px|link=http://www.sonydna.com/sdna/e/index.html ]] | ||
| + | </p> | ||
| + | <h2>Silver Sponsors</h2> | ||
| + | <p align=center> | ||
| + | [[Image:DeNA_sl.png|180px|link=http://dena.com/intl/ ]] | ||
| + | [[Image:Gehirn_sl.png|180px|link=http://www.gehirn.co.jp/ ]] | ||
| + | [[Image:Mbsd_sl.png|180px|link=http://www.mbsd.jp/english.html ]] | ||
| + | </p> | ||
| + | <h2>Supporters</h2> | ||
| + | <p align=center> | ||
| + | [[Image:Atmark-it sl.png|150px|link=http://www.atmarkit.co.jp/ ]] | ||
| + | [[Image:Codeblue-200x100.png|150px|link=http://codeblue.jp/en-index.html ]] | ||
| + | [[Image:Eyesjapan_sl.png|150px|link=http://nowhere.co.jp/ ]] | ||
| + | [[Image:Kdl_sl.png|150px|link=http://www.kdl.co.jp/ ]] | ||
| + | </p> | ||
| + | <p align=center> | ||
| + | [[Image:Health20 sl.png|150px|link=http://health2con.jp/japan/fukushima/ ]] | ||
| + | [[Image:Isc2_sl.png|150px|link=https://www.isc2.org/japan/Default.aspx ]] | ||
| + | [[Image:Jpcert sl.png|150px|link=https://www.jpcert.or.jp/ ]] | ||
| + | [[Image:Nnw_sl.png|150px|link=http://coin.nikkeibp.co.jp/coin/nikkeinetwork/ ]] | ||
| + | [[Image:Sns_sl_update.png|150px|link=http://scan.netsecurity.ne.jp/ ]] | ||
| + | </p> | ||
| + | |||
| + | ==Let us Promote AppSec APAC 2014 in Tokyo!== | ||
| + | [[Image:Appsecapac2014logo.jpg |center|400px| link=https://www.owasp.org/index.php/AppSecAsiaPac2014]] | ||
| + | The AppSec APAC logo features a Sumo wrestler representing security and defense whereas the rising sun symbolizes raising awareness of OWASP in Japan. | ||
| + | Through this we hope to create a more secure internet society not only in Japan but throughout the world. | ||
| + | We would truly appreciate your help with promoting the event and definitely want you to be involved as much as possible! | ||
| + | I look forward to seeing you in Tokyo next March! | ||
| + | - Riotaro OKADA, | ||
| + | OWASP Japan chapter | ||
| − | + | {{Social Media Links}} | |
Latest revision as of 08:34, 26 March 2014
| |
|
|---|---|

|
- WELCOME
- TEAM
- VENUE
- HOW TO GET THERE
- HOTEL RESERVATIONS
- REGISTRATION
- TRAINING SESSIONS
- CONFERENCE SESSIONS
- KEYNOTE SPEAKERS & OWASP BOARD MEMBER
- WOMEN IN APPSEC
- SPONSORSHIP OPPORTUNITIES
日本語サイト Appsec APAC 2014 Japanese site: https://appsecapac.org/2014/
We are pleased to announce that the OWASP Japan chapter will host the OWASP AppSec APAC 2014 conference in Tokyo, Japan at the Sola City Conference Center.
The event will be composed of 2 days of training (March 17-18), followed by 2 days of conference talks (March 19-20).
The Global AppSec APAC 2014 Conference will be a reunion of Information Security Asia-Pacific leaders, and will present cutting-edge ideas.
OWASP events attract a worldwide audience interested in “what’s next”. The conference is expected to draw 250-300 technologists from Government, Financial Services, Media, Pharmaceuticals, Healthcare, Technology, and many other verticals.
Should you want to REGISTRE FOR A TRAINING SESSION please send an e-mail to [email protected]
Conference Registration is CLOSED
Who Should Attend Global AppSec APAC 2014:
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interested in Improving IT Security
If you have any questions, please email the conference committee: [email protected]
OWASP PodCast 24/7
Global AppSec APAC 2014 Executive Committee
Riotaro Okada
Researcher. Born in Kobe, Hyogo Prefecture, Japan, Mr. Okada has over 20 years of experience in software development and network construction. He has been involved in network construction, software development and the implementation of information security measures at independent software development companies, the R&D divisions of manufacturing companies as well as consulting firms. Mr. Okada has also facilitated various technology-related communities such as for Linux and PHP. In 2004, he founded the Web Application Security Forum and as a member of the board became involved in the diffusion of security-related information. Moreover, he was also a researcher at the Information-technology Promotion Agency, Japan (IPA) for 8 years, and responsible for the IT strategy as well as disaster response projects at various government organizations. Mr. Okada is the co-leader of OWASP Japan since its founding, is CISA certified and holds an MBA from BBT (2009).
Sen Ueno
CEO Tricorder Inc. Japanese computer engineer and technical expert.
Majored in Information Security at the Nara Institute of Science and Technology (NAIST). After successfully listing an eCommerce venture on the TSE Mothers exchange, Mr. Ueno founder Tricorder and focused on information security education, network/web application vulnerability assessment, etc.
In addition to being the CEO of his company, Mr. Ueno is also a researcher at the Information-technology Promotion Agency, Japan (IPA), the chief editor at the information security-related magazine ScanNetSecurity and a member of the executive committee for WASForum Hardening Project. He has also been a co-leader for OWASP Japan since its inception.
Works authored by Mr. Ueno include “HTTP no Kyoukasho”, “Konya Wakaru TCP/IP”, “Mendoukusai Web Security”, etc.
Takanori Nakanowatari Mr. Nakanowatari is involved in the security management and software development at an OA device manufacturer. He has been actively involved in the overseas of OWASP as well such as participating in AppSec conferences overseas and has contributed to OWASP Meetings in Japan by sharing his various experiences. Mr. Nakanowatari is CISSP certified and since 2013 has been a member of the OWASP Japan Advisory Board.
Yosuke Hasegawa
Mr. Hasegawa is an Evangelist at Net Agent as well as a technological advisor at Secure Sky Technology, Inc. He has been instrumental in discovering various vulnerabilities in web applications such as Internet Explorer and Mozilla Firefox. He has participated in Black Hat Japan 2008 and Korea POC (Power of Community) 2008 & 2010 as well as giving lectures and speeches at various other conferences. Since its inception, Mr. Hasegawa has been a member of the OWASP Japan Advisory Board.
Robert Dracea Mr. Dracea is responsible for the global strategy of a Japanese internet service company. With the mission of better sharing Japan’s advanced technological power with the world, from a business perspective, he has successfully architected numerous alliances and tie-ups both domestically in Japan as well as overseas. Additionally, he has also, on a volunteer-basis, conducted the translation and interpretation at multilingual OWASP Meetings. Mr. Dracea has been since its founding a member of the OWASP Japan Advisory Board.
Program Selection Committee
Youki Kadobayashi, Ph.D.
Associate professor at Nara Institute of Science and Technology (NAIST). After being employed at Osaka University’s Cybermedia Center, Dr. Kadobayashi joined his current position in 2000. Since 2008 he has been involved in cyber security standardization at the International Telecommunications Union Telecommunications Standardization Sector. Dr. Kadobayashi is also actively involved in cyber security education and training programs. Additionally, he is a board member of the industry-academic-government collaborative research consortium WIDE Project and since 2013 the Japanese representative of the American-Japanese international joint research project FP7 NECOMA Project. Dr. Kadobayashi is also a member of the executive committee for the WASForum Hardening Project.
Masakazu Takahashi
Chief Security Advisor, Microsoft Japan.
After being involved in standard library, OS development and other basic development, Mr. Takahashi became involved in the security business after engaging in vulnerability assessment and intrusion detection at a security company.
At a time when penetration testing was a common practice in vulnerability assessment, Mr. Takahashi became a proponent of white box testing as a logical and repeatable inspection method. In terms of intrusion detection, he oversaw the systemization of surveillance and operations technologies and was in charge of starting numerous SOC businesses.
In November of 2006, Mr. Takahashi joined Microsoft Japan. As the chief security advisor, he is involved in attaining the secure computing that Microsoft aims for while at the same time publishing papers and conducting various lectures.
Additionally, Mr. Takahashi is actively involved in associations within the industry and is the head of a community involved in the promotion of information security measures as well as the vice president of the Japan Network Security Association (JNSA).
Keiji Takeda, Ph.D.
Lecturer at Keio University, Faculty of Environment and Information Studies.
Ph.D. from Keio University Graduate School of Media and Governance. After being employed at the Ministry of Defense, the Japan Air Self-Defense Force and Accenture, Dr. Takeda became a lecturer at Carnegie Mellon University’s school in Japan before moving on to his current position. Dr. Takeda is also a member of various information security-related committees including participating as an advisor for the Hyogo Prefectural government. In addition, he is actively involved in the information security industry through a broad array research & development, operations, personnel training and consulting activities including development assessment of intrusion detection systems, participation at various security events and the planning of organizations for the distribution of information related to security vulnerabilities.
Masafumi Negishi
Senior Engineer, Office of Emergency Response and Clearinghouse for Security Information, Internet Initiative Japan Inc.
Mr. Negishi has been involved in network construction, security inspection and security consulting, etc. at a major electronics manufacturer, a security company and foreign-affiliated computer vendor. In 2003 he became employed at IIJ Technology and placed in charge of security services, overseeing numerous security inspections. Currently he is part of the security incident support team and is primarily responsible for the collection and analysis of security information as well as taking appropriate action when security issues are discovered. Since 2007 he has been an instructor at the SANS Institute and since 2012 he has also been a member of the Advisory Board for OWASP Japan.
Yoshinari Fukumoto System Security Office Manager, Rakuten Inc. After being involved in research and development of security products at a security-related company, in 2002 Mr. Fukumoto joined Rakuten and became responsible for the internet service security for Rakuten Group. He is primarily involved in the promotion and development of secure software as well as the support of security-related operations. Mr. Fukumoto is also a Rakuten-CERT Representative. He has been a member of the OWASP Japan Advisory Board since the chapter began its activities.
AppSec APAC 2014 will be held at the SOLA CITY CONFERENCE CENTER in Tokyo, Japan.
TOKYO has two international airports, Tokyo International Airport (Haneda: HND) and Narita International Airport (NRT).
Both airports are located away from the city center but Haneda is the closer of the two.
We advise against taking a taxi from the airport since it is farther and more expensive than you might expect. To avoid high costs take the train or bus to the nearest station to your hotel or destination and then take a taxi if needed.
Please find out what the best way to reach your destination is before arriving.
- Train http://www.haneda-airport.jp/inter/en/access/train.html
- Take either the Tokyo Monorail to Hamamatsucho Station (JPY 470, 23 min) or the Airport Limited Express to Keikyu Shinagawa Station (JPY 400, 22 min)
From Narita International Airport to Tokyo Station (NRT: Narita)
- Train http://www.narita-airport.jp/en/access/train/index.html
- Take the Narita Express to Tokyo Station [approx. JPY 3,000 or JPY 4,500 for Green Car (first class), approx. 1 hour]
- From Haneda http://www.haneda-airport.jp/inter/en/access/bus.html
- From Narita http://www.narita-airport.jp/en/access/bus/index.html
There are numerous buses going to Tokyo Station and various locations and some may take you very close to your hotel or other destination. Some buses go directly to major hotels.
Please find out what your nearest station is and chose the appropriate bus from the list at the URL found above.
Depending on where your hotel is, you may choose to continue on by train or take a taxi.
Taxis in Japan are extremely reliable and you generally do not have any problems.
To avoid language issues, have the name and address of your hotel, or Sola City Conference Center and other destinations written (with a map if possible) and keep it handy at all times to show it to the driver.
The JR Yamanote Line or any stations within the Yamanote Line circle are considered downtown Tokyo.
The venue, Sola City Center, is close to Ochanomizu-Station on the JR Chuo-Line.
Tokyo boasts a variety of accommodations from Ryoakans to full-service hotels and luxury inns. Rooms may go fast on the conference days, so book early for best availability!
The conference venue, Sola City Conference Center, is located in Tokyo Central Region, Kanda/Akihabara/Ochanomizu area. The closest train station is Ochanomizu Station.
As the conference venue is not a hotel, you must reserve your accommodation. The venue is really close to JR Ochanomizu Station, and Tokyo Metro Shin-Ochanomizu station which is at the heart of downtown Tokyo.
Because of the central location, you can reach the venue relatively easily from any area in downtown Tokyo like Akihabara, Kanda and Nihonbashi, so feel free to book your hotel using any web site you like.
For your help:
- Hotel Reservation in Tokyo: Japanican Site
- Hotel reservation near the Conference Venue (Ochanomizu area): Japanican Site for Ochanomizu Area
Alternatively, if you would like to book your accommodation by contacting JTB Global Marketing and Travel they will be happy to help you with your hotel booking and provide assistance organizing your time in Tokyo.
- E-mail: [email protected]
- Phone: +81-3-5796-5445
- FAX:+81-3-5495-0685
OWASP AppSec APAC features two days of training March 17-18, and two days of talks, March 19-20, 2014.
Training Sessions Registration
Should you want to register for a Training Session please send an e-mail to [email protected]
Training Sessions Registration Fees (Please note that conference Registration is separate.)
| Course Length | Course Dates | Fee |
|---|---|---|
| 1 - day class | Monday, March 17 2014 | $400 USD (40,000 Yen) |
| 2 - day class | Tuesday, March 18 2014 | $800 USD (80,000 Yen) |
Payment will be processed in Japanese Yen but we can process invoice in USD or other currencies.
Conference Registration
Conference on-line registration is CLOSED
Conference Registration Fees (not including training)
| Ticket price | On-site Fee |
|---|---|
| Active OWASP member | $400 USD (40,000 Yen) |
| Non-Member | $450 USD (45,000 Yen) |
| Student | $120 USD (12,000 Yen) |
Payment will be processed in Japanese Yen but we can process invoice in USD or other currencies.
Cancellations, Refunds, and Substitutions All ticket sales are final and our general policy is no refunds. However, we are able to substitute registrations at no charge until February 28, 2014.
Group Discounts: 10% off for groups of 10-19; 20% off for groups of 20-29; 30% off for groups of 30 or more. Please contact us for more information about registering a group.
Membership Discounts: We are pleased to offer $20 off admission for active OWASP members. Multiple discounts can not be applied.
Registration for Trainers and Speakers: If you have been selected to deliver a training or talk at the conference, you should have received a discount code for complimentary admission. If you did not receive this code or have questions, please Contact us.
Registration for OWASP Leaders: Complimentary admission to the conference is offered to active OWASP Chapter and Project Leaders. Additionally, two seats for each of the training courses are available at no cost to active OWASP Chapter and Project Leaders (available on a first come, first serve basis).
To register as an active Chapter or Project leader, please select the general event registration option and enter discount code: OWASPLEADER.
Please note: conference and training registration using the OWASPLEADER discount code will be verified by the conference team and if you are not an active OWASP Chapter or Project Leader, you will be contacted regarding your status and your registration may be subject to cancellation.
Monday and Tuesday, March 17th - 18th
- Mobile Security: Securing Mobile Devices & Applications _ ENGLISH
Dave Wichers
ROOM A 10am-5pm
Mobile applications enable new threats and attacks which introduce significant risks to the enterprise, and many custom applications contain significant vulnerabilities that are unknown to the team that developed them.
Considering the number of mobile applications available in the Google Play and Apple AppStore is nearing 1.5 million and vulnerabilities are skyrocketing it is imperative to perform typical application security practices. But, how is mobile different?
This two-day, hands-on course enables students to understand how easily mobile devices and applications can be successfully attacked. They will learn how to identify, avoid and remediate common vulnerabilities by walking through a threat analysis and learning critical security areas such as those identified in the OWASP Top Ten Mobile Risks and Controls. Using state-of-the-art testing tools, students will learn how to secure mobile devices across the enterprise. Students will be able to choose from iOS or Android hands-on labs throughout the course, while they learn how easily the bad guy can compromise applications and the data they contain.
Monday, March 17th
- Secure Web Development _ ENGLISH
Jerry Hoff
ROOM B 10am-6pm
Web application security is the #1 security issue for most enterprises today. This class goes through fundamental security principles for Java and .NET web developers, focusing on secure development practices.
This highly interactive, intensive 2-day class provides essential Java application security training for developers, architects and software testers. The class is a combination of lecture, hands-on development and code review. Instructor bring years of hands-on security experience, and provide invaluable insight from numerous security assessments.
Participants will not only learn the most common threats against web applications, but more importantly they will learn how to also fix the problems via control based code samples and review. Each student will have their own web application they will secure and test. This class is suitable for web application software engineers, web quality assurance engineers, and web architects.
Focus will be put on covering not only the OWASP Top 10, but other common web vulnerabilities that plague modern web applications. Participants will gain a strong knowledge of web vulnerabilities, how vulnerabilities are exploited, and what security controls need to be in place to write defensible applications. Emphasis will also be placed on how these secure coding techniques relate to mobile, secure API development, and how security can be introduced throughout the SDLC.
- Hands on Simple method of the penetration testing using OWASP ZAP _ JAPANESE
Minoru Sakai and Yuho Kameda
ROOM C 10am - 6pm
This course goes through automated security testing from OWASP tools.
Tools:
OWASP Zed Attack Proxy
OWASP Broken Web Applications
Tuesday, March 18th
- CISO training: Managing Web & Application Security – OWASP for senior managers _ ENGLISH
Tobias Gondrom
ROOM C 10am - 6pm
Managing and improving your global information security organization, Leverage OWASP and common best practices to improve your security programs and organization. Achieving cost-effective application security, bringing it all together on the management level.
Considering the number of mobile applications available in the Google Play and Apple AppStore is nearing 1.5 million and vulnerabilities are skyrocketing it is imperative to perform typical application security practices. But, how is mobile different?
This two-day, hands-on course enables students to understand how easily mobile devices and applications can be successfully attacked. They will learn how to identify, avoid and remediate common vulnerabilities by walking through a threat analysis and learning critical security areas such as those identified in the OWASP Top Ten Mobile Risks and Controls. Using state-of-the-art testing tools, students will learn how to secure mobile devices across the enterprise. Students will be able to choose from iOS or Android hands-on labs throughout the course, while they learn how easily the bad guy can compromise applications and the data they contain.
- Developer Security Training _ FREE TRAINING _ ENGLISH
Jim Manico
ROOM B 1pm - 6pm
This free training session will teach a developer about the fundamentals of secure software development practices. The session is a fast-paced combination of lecture, security testing and code review. This class will also highlight production quality API's from various languages, frameworks, and 3rd party libraries that provide production quality and scalable security controls.
All conference session will be translated into English - Japanese.
Wednesday, March 19th
PLENARY SESSIONS:
- 10.00am-10.30am Welcome Address and Openening Remarks (Riotaro Okada & Tobais Gondrom)
- 10.30am-11.20am KEYNOTE (Suguru Yamaguchi)
- 11.30am-12.20pm OWASP Top 10 - 2013. KEYNOTE (Dave Wichers)
TRACK A:
- 1.30pm-2.20pm The OWASP Proactive Controls. (Jim Manico)
- 2.30pm-3.20pm OWASP documents for every people.(Chia-Lung Albert Hsieh)
- 4.00pm-4.50pm 12 Case Studies for the Access Controls of Web Application. (Takashi Honda)
- 5.00pm-5.50pm Get Ready for the Next Big Wave of Attacks: Hacking of Leading CMS Systems. (Helen Bravo, Sanjay Agnani)
TRACK B:
- 1.30pm-2.20pm Why OWASP AppSensor is the future of Application Security, and why you should be using it. (Dennis Groves)
- 2.30pm-3.20pm Inside Story of the first SaaS type WAF Service. (Kana Toko)
- 4.00pm-4.50pm The Art and Science of Configuring SSL. (Nick Galbreath)
- 5.00pm-5.50pm Bad Web Apps are Good – The Broken Web Application Project. (Mordecai Kraushar)
TERRACE ROOM
- 1.30am-2.20pm Women in AppSec
- 2.30pm-3.20pm OWASP Japan
- 4.00pm-4.50pm The fact report of attack traffic on the Internet. (Makoto Niimura)
- 5.00pm-5.50pm The investigation of Web Application Vulnerabilities in Japan. (Koki Takahashi)
Thursday, March 20th
TRACK A:
- 9.30am-10.20am eXtend Security on Xcode. (Tokuji Akamine, Raymund Pedraita)
- 10.30am-11.20am Getting a handle on mobile security. (Jerry Hoff)
- 11.50am-12.40pm Preinstalled Android application poisoning. (Yoshitaka Kato)
TRACK B:
- 9.30am-10.20am HTML 5 Security for Web Application Development. (Yoshinori Matsumoto)
- 10.30am-11.20am XSS Allstars from Japan. (Yosuke Hasegawa, Masato Kinugawa, Mala)
- 11.50am-12.40pm Secure Escaping method for the age of HTML 5. (Yoshinori Takesako)
TERRACE ROOM
- 9.30am-10.20am Management for Security Life Cycle. (Shoji Ito)
- 10.30am-11.20am How to choose (or write) your own source code scanner. (Yu-Lu “Chris” Liu)
- 11.50am-12.40pm OWASP Japan (Open Mic Session)
PLENARY SESSIONS:
- 1.40pm-2.30pm 1 user, 10 places, 100 seconds. (Matias Madou)
- 2.40pm-3.30pm DevOps. (Dave Wichers)
- 4.00pm-4.50pm KEYNOTE (Michael Coates)
- 5.00pm-5.30pm Closing Remarks (Tobias Gondrom & Riotaro Okada)
Keynote Speaker
Suguru Yamaguchi is a Professor at the Graduate School of Information Science, Nara Institute of Science and Technology (NAIST) and former Advisor on Information Security to the Cabinet of the Government of Japan. He was born in Shizuoka, Japan in 1964. He has D.E from Osaka University. In 2000, he was promoted to Professor with the Graduate School of Information Science, NAIST, Nara, Japan and since 2013, has been Director of Library for FY2013 & 2014. From April 2004 to March 2010, he held the position of Advisor on Information Security to the Cabinet of the Government of Japan.
He has been deeply involved in the design and implementation of the national master plan on information security policy and establishment for the National Information Security Center (NISC) of the Cabinet Secretariat in 2005. Furthermore, because of tight relationship with the government’s information security policy, he was also appointed Advisor to the Government Program Management Office (GPMO) at secretariat office of IT Strategic Headquarter, Government of Japan since 2006. His research interests include technologies for information sharing, multimedia communication over broadband channels, large-scale distributed computing systems including “cloud computing” technology, network security and network management for the internet. Since the mid-1980’s, he has been focused on the development of the internet in Japan and the Asia Pacific region. He has also been a member of the WIDE project, which is one of the pioneer projects for internet development since its creation in 1988. For internet development in the Asia Pacific region, he has been working for many years at the Asian Internet Interconnection Initiatives (AI3) since its creation in 1996.
He has made many contributions to internet development and network security both in Japan and overseas. He founded JPCERT/CC in 1996, which is the first national CSIRT in Japan, and is now working as one of the board of trustees. He was one of the founders of APCERT.org, a regional forum of CSIRT in the Asia Pacific region established in 2002. From 2011, he has been appointed as a member of the Steering Committee for FIRST (Forum of Incident Response and Security Teams). In this role, he is working as a liaison officer of Geographical Outreach to work together with the CSIRT teams in developing countries, mainly in Africa and the Greater Middle East region to connect to the global FIRST community. Since 2002, he has been a member of the board of trustees of the Japan Network Information Center (JPNIC), which is the national internet registry managing IP addresses and AS number allocations and registrations in Japan.
Michael Coates is the Chairman of the OWASP board, an international non-profit organization focused on advancing and evangelizing the field of application security. In addition, he is the creator of OWASP AppSensor, a project dedicated to creating attack aware applications that leverage real time detection and response capabilities.
Michael is also the Director of Product Security at Shape Security, a Silicon Valley startup developing an entirely new type of web security product to protect web sites against modern attacks.
Previously, Michael was the Director of Security Assurance at Mozilla where he founded and grew the Security Assurance and Web Security programs to 25 people.
Throughout Michael's career he has advised major corporations and governments on secure architecture and software security. He’s also performed hundreds of technical security assessments for financial, enterprise, and cellular customers worldwide. Michael also maintains a security blog at michael-coates.blogspot.com
Michael holds a Master of Science degree in Computer, Information and Network Security from DePaul University and a Bachelor of Science degree in Computer Science from the University of Illinois at Urbana-Champaign.
Dave Wichers is a cofounder and the Chief Operating Officer (COO) of Aspect Security, a consulting company that specializes in application security services. He is also a long time contributor to OWASP, helping to establish the OWASP Foundation in 2004, serving on the OWASP Board since it was formed from 2004 through 2013, served as OWASP Conferences Chair from 2005 through 2008, is a coauthor of the OWASP Top 10 and has led the project since 2007, and has contributed to numerous other important OWASP projects including WebGoat, ESAPI, ASVS, and the OWASP Cheat Sheet Series.Dave has over 25 years of experience in the information security field, and has focused exclusively on application security since 1998. At Aspect, in addition to his COO duties, he is Aspect's application security courseware lead, one of their chief instructors, and provides a wide variety of application security consulting services to Aspect's clients. Prior to starting Aspect, he ran the Application Security Services Group at Exodus Communications. Dave has a Bachelors and Masters degree in Computer Science and is a CISSP.
OWASP Board Speaker
Tobias Gondrom is CEO at Thames Stanley, a boutique Global CISO and Information Security & Risk Management Advisory operating in Asia and Europe.
He has 15 yrs of experience in information security and risk management, software development, application security, cryptography and global standardization organizations, working for independent software vendors and large global corporations in the financial, technology and government sector. Over the years, he has run various corporate information security functions and trained and advised dozens of CISOs and senior information security leaders around the globe. Tobias is a Sloan Fellow from London Business School, holding its most senior business degree, the Sloan M.Sc. in Leadership and Strategy.
Since 2003 he is the chair of working groups at the IETF (www.ietf.org), member of the IETF security directorate, and since 2010 chair of the web security WG at the IETF. He is vice-chairman for research and programs of the CSA Hong Kong and Macau chapter and an ISC2 CSSLP and CISSP Instructor.
Tobias has been in a number of OWASP project and chapter leadership roles since 2007. Today, he is a member of the OWASP Global Board and member of the London chapter board and project lead of the CISO Survey & Report project.
He has authored the Internet standards RFC 4998, 6283 and 7034, co-authored the books „Secure Electronic Archiving“ and the "OWASP CISO Guide" and is a frequent presenter at conferences and publication of articles on security (e.g. AppSec, IETF, ...).
The deadline to apply for the Women in AppSec Program for AppSec APAC has been extended until March 7th, 2014.
Attendance for one woman to the OWASP AppSec APAC 2014 conference, and at least one of the in-depth training sessions, will be the award for this year’s winner. The Women in AppSec Program was successfully launched at AppSec USA in 2011 and this year’s event hopes to build on that trend and further engage women in the community.
We encourage you to take advantage of this opportunity by applying as soon as possible if you are a woman either in the software security industry, or interested in learning more about the software security industry.
If you are interested please use the APPLICATION FORM to send us your details.
OWASP’s current program objective is to encourage female students at both the undergraduate and graduate levels, instructors, and professional working-women who are dedicated to a career in information security and/or application development, to expand their skills and pursue application security.
| |
We are looking for Silver and 'A La Carte" Sponsors for the Global AppSec APAC 2014.
This is a truly unique opportunity to increase your brand recognition as a company dedicated to the highest standards of professional technology & security not only in Japan and the Asia Pacific region but also internationally throughout the world while supporting the continued activities conducted by OWASP both in Japan and abroad.
- Sponsorship benefits for organizations specializing in IT & Security:
- Opportunity to use the latest technological trends for professional training / development
- Strengthen your company strategy by learning the latest trends in web software security
- Improve your business development strategy with leading information from the security industry
- Get networking and headhunting opportunities with world-class specialists and professionals
- Get the chance to interact with high-need discerning users to improve product development
- Increase your image as a professional company through this unique branding opportunity
- Sponsorship benefits for organizations utilizing the internet in their business:
- Opportunity to increase the international brand awareness and conduct business networking
- Strengthen your company strategy by learning the latest trends in web software security
- Improve your service development by understanding the latest trends in security issues & risks
- Contribute to information society as a company by developing safe and secure services
- Get the chance to interact with high-need discerning users to improve product development
- Opportunity to brand your company as one that focuses on the highest standards in technology
If you are interested to sponsor Global AppSec APAC 2014, please contact the conference team: [email protected]
To find out more about the different sponsorship opportunities please check:
OWASP AppSec APAC 2014 Premium Sponsorship Menu on the following package.
Download Sponsor Package(Updated 2014.2.20): English | Japanese
SPONSORS
Diamond Sponsors
Platinum Sponsors
Gold Sponsors
Silver Sponsors
Supporters
Let us Promote AppSec APAC 2014 in Tokyo!
The AppSec APAC logo features a Sumo wrestler representing security and defense whereas the rising sun symbolizes raising awareness of OWASP in Japan. Through this we hope to create a more secure internet society not only in Japan but throughout the world.
We would truly appreciate your help with promoting the event and definitely want you to be involved as much as possible! I look forward to seeing you in Tokyo next March!
- Riotaro OKADA, OWASP Japan chapter