This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Romania InfoSec Conference 2013"
Oana Cornea (talk | contribs) |
Oana Cornea (talk | contribs) |
||
| (21 intermediate revisions by 2 users not shown) | |||
| Line 4: | Line 4: | ||
=Welcome= | =Welcome= | ||
| − | |||
{| style="width: 100%;" | {| style="width: 100%;" | ||
|- | |- | ||
| Line 10: | Line 9: | ||
{| style="border: 0px solid ; background: transparent none repeat scroll 0% 0%; width: 100%; -moz-background-clip: border; -moz-background-origin: padding; -moz-background-inline-policy: continuous;" | {| style="border: 0px solid ; background: transparent none repeat scroll 0% 0%; width: 100%; -moz-background-clip: border; -moz-background-origin: padding; -moz-background-inline-policy: continuous;" | ||
|- | |- | ||
| − | | style="width: 95%; color: rgb(0, 0, 0);" | | + | | style="width: 95%; color: rgb(0, 0, 0);" | |
'''Owasp Romania InfoSec Conference 2013 - October 25th''' | '''Owasp Romania InfoSec Conference 2013 - October 25th''' | ||
| + | OWASP Romania team is happy to announce the '''OWASP Romania InfoSec Conference 2013''', a one day '''Security''' and '''Hacking Conference'''. It will take place on 25th of October, 2013 - Bucharest, Romania. <br> | ||
The OWASP Romania InfoSec Conference objective is to raise awareness about application security, so that people and organizations can make informed decisions about true application security risks. Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. | The OWASP Romania InfoSec Conference objective is to raise awareness about application security, so that people and organizations can make informed decisions about true application security risks. Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. | ||
| Line 26: | Line 26: | ||
*Executives, Managers, and Staff Responsible for IT Security Governance | *Executives, Managers, and Staff Responsible for IT Security Governance | ||
*IT Professionals Interesting in Improving IT Security | *IT Professionals Interesting in Improving IT Security | ||
| − | *Anyone interested in learning about or promoting Web Application Security | + | *Anyone interested in learning about or promoting Web Application Security |
| − | |||
| − | = | + | | style="width: 110px; font-size: 95%; color: rgb(0, 0, 0);" | |
| − | + | |} | |
| − | |||
| − | = | + | | style="width: 110px; font-size: 95%; color: rgb(0, 0, 0);" | |
| + | |} | ||
{|style="vertical-align:top;width:90%;background-color:#white;padding:10px;border:1px solid silver;" align="center" cellspacing="5" | {|style="vertical-align:top;width:90%;background-color:#white;padding:10px;border:1px solid silver;" align="center" cellspacing="5" | ||
|- | |- | ||
| − | | align="center" style="background:# | + | | align="center" style="background:#CCCCEE;" colspan="2" | |
| − | '''CONFERENCE (Friday 25th of October)''' | + | '''CONFERENCE (Friday 25th of October)''' |
|- | |- | ||
|- | |- | ||
| Line 43: | Line 42: | ||
| style="width:80%" valign="middle" bgcolor="#CCCCEE" align="center" colspan="0" | '''Location''' | | style="width:80%" valign="middle" bgcolor="#CCCCEE" align="center" colspan="0" | '''Location''' | ||
|- | |- | ||
| − | | valign="middle" bgcolor="#EEEEEE" align="center" | ''' Friday 25th of October ''' | + | | valign="middle" bgcolor="#EEEEEE" align="center" | ''' Friday 25th of October<br>10:30 AM ''' |
| − | | valign="middle" bgcolor="#EEEEEE" align="left" | '''Venue Location: University "Politehnica" of Bucharest<br> | + | | valign="middle" bgcolor="#EEEEEE" align="left" | '''Venue Location: University "Politehnica" of Bucharest, Rectorship Building, AN024 Hall'''<br> |
Venue Address: Splaiul Independentei nr. 313, sector 6, Bucuresti, ROMANIA; <br> | Venue Address: Splaiul Independentei nr. 313, sector 6, Bucuresti, ROMANIA; <br> | ||
| − | Postal cod: RO-060042 | + | <!-- Postal cod: RO-060042<br> |
| − | Venue Map: [https://plus.google.com/101033585760098377632/about] | + | Venue Map: [https://plus.google.com/101033585760098377632/about] --> |
|- | |- | ||
| align="center" style="background:#CCCCEE;" colspan="2" | '''Price and registration''' | | align="center" style="background:#CCCCEE;" colspan="2" | '''Price and registration''' | ||
|- | |- | ||
| − | | align="center" style="background:#EEEEEE;" colspan="2" | This event is '''FREE''' <br> | + | | align="center" style="background:#EEEEEE;" colspan="2" | This event is '''FREE''', you need to register on the link provided below, print your ticket and present it at the entrance. <br> |
| − | ''' | + | '''Limited number of seats! Register now!''' [https://owasp-romaniachapter-infosec.eventbrite.com/ https://owasp-romaniachapter-infosec.eventbrite.com/ ] |
| − | + | |- | |
| − | + | | align="center" style="background:#CCCCEE;" colspan="2" | '''How to get there''' | |
| − | |||
|- | |- | ||
| + | | align="center" style="background:#EEEEEE;" colspan="2" | [[Image:Harta-an024.jpg|800px|]] | ||
| + | | | ||
|} | |} | ||
<br> | <br> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | = | + | =Agenda= |
| − | + | {{:OWASP_Romania_InfoSec_Conference_2013_Agenda}} | |
| − | == | + | |
| + | =Team= | ||
| + | {{:OWASP_Romania_InfoSec_Conference_2013_Team}} | ||
| − | + | <headertabs /> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | =Sponsors= | |
| + | {{:OWASP_Romania_InfoSec_Conference_2013_Sponsors}} | ||
Latest revision as of 20:50, 10 October 2013
| |
OWASP Romania InfoSec Conference |
|
|
CONFERENCE (Friday 25th of October) | ||
| Date | Location | |
| Friday 25th of October 10:30 AM |
Venue Location: University "Politehnica" of Bucharest, Rectorship Building, AN024 Hall Venue Address: Splaiul Independentei nr. 313, sector 6, Bucuresti, ROMANIA; | |
| Price and registration | ||
This event is FREE, you need to register on the link provided below, print your ticket and present it at the entrance. Limited number of seats! Register now! https://owasp-romaniachapter-infosec.eventbrite.com/ | ||
| How to get there | ||
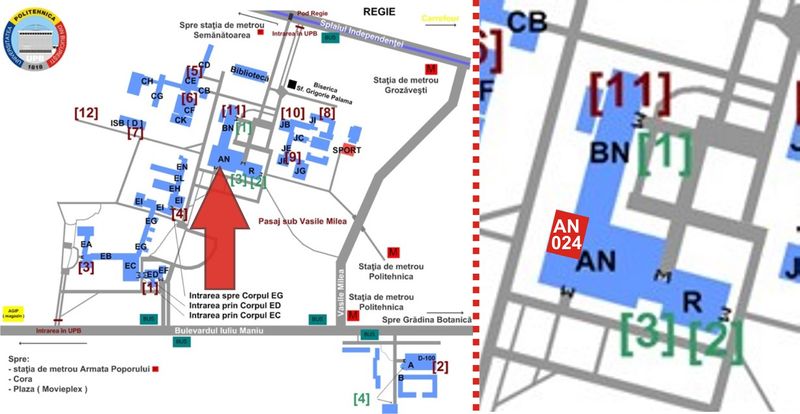
|
||
Agenda | |||||
| Time | Title | Speaker | Description | ||
| 10:30 - 11:00 (30 mins) |
Registration | ||||
| 11:00 - 11:15 (15 mins) |
Introduction & Welcome | Oana Cornea | Introduction to OWASP & Bucharest Event, Schedule for the Day | ||
| 11:15 - 12:00 (45 mins) |
Secure Development LifeCycle (aka "The good the bad and the ugly implementations") [1] |
Martin Knobloch | Software development is not THAT new anymore, but it is still a fast changing work environment. We do develop more functionality faster, and the applications do even look more pretty! | ||
| 12:05 - 12:50 (45 mins) |
Practical Defense with mod_security Web Application Firewall [2] | Marian Ventuneac | Marian will introduce the mod_security Web Application Firewall (WAF). This session will be a practical demonstration of mitigating security risks for a sample vulnerable Web application. | ||
| 12:55 - 13:40 (45 mins) |
Scanning Romania with Nessus (web part) [3] | Adrian Furtuna | This talk presents the results of a passive vulnerability scan performed against all Romanian IP addresses, targeting all web servers listening on port 80. The research was performed against multiple network packet captures selected from the output of Carna botnet, which scanned Romania in July 2012. | ||
| 13:40 - 14:30 (50 mins) |
Lunch/Coffee Break | ||||
| 14:30 - 15:15 (45 mins) |
Reading the minds [4] | Anatolie Prisacaru | In my presentation I will focus the analysis of what data web browsers, extensions and web servers keep in memory. I will start with a quick introduction on how to dump and analyse processes' random access memory maps on a Linux based operating system with basic tools and then run a quick code review to see a couple of weak points, find their Achilles' heel and finally prove why statements like "Your sensitive data is encrypted _locally_ before upload so even LastPass cannot get access to it" can be pretty misleading. | ||
| 15:20 - 16:05 (45 mins) |
Online Fraud and the part it plays in Cybercrime [5] | Alexandru Doroftei | The presentation will be about what is online fraud, what risks do companies face when they support e-commerce and the growing role fraud has in the cybercrime area. I will describe a few of the best practices against fraud, diving a little bit in the fraud industry numbers associated with fraud. | ||
| 16:10 - 16:55 (45 mins) |
Hacking the Wordpress ecosystem [6] | Dan Catalin Vasile | This talk came from the personal need of securing multiple instances of Wordpress. An OWASP Project was initiated to gather the knowledge around this subject in one place. The presentation will address the following subjects: | ||
| 17:00 - 17:45 (45 mins) |
Resolving 3 Common threats in MVC (A4 - Insecure Direct Object References , A3 - Cross-Site Scripting (XSS) , A8 - Cross-Site Request Forgery (CSRF) ) [7] | Andrei Ignat | Any website is confronted with hackers. The security measures are easy to follow - and this presentation shares to you this knowledge. | ||
Sponsors
Gold Sponsor |
||||||

|
||||||
Event Lunch/Coffee Break sponsored by |
||||||

|
||||||
Event Supporters |
||||||
| |

|
|
||||

|
|

| ||||

|

|
|||||
Educational Supporters |
||||||

|

|
