This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "AppSecAsiaPac2013"
Sarah Baso (talk | contribs) |
|||
| (33 intermediate revisions by 3 users not shown) | |||
| Line 13: | Line 13: | ||
| − | |||
| Line 25: | Line 24: | ||
<font size=2pt> | <font size=2pt> | ||
| − | We are | + | We are proud to announce the AppSecAPAC2013. AppSecAPAC2013 conference dedicated to application security, with an emphasis on secure architecture and development techniques to help developers build more secure applications. |
| − | + | Who is it for? | |
| + | * Web Developers: There will be a choice of two streams in the morning. First stream covering introductory talks to application security, second stream covering deeper technical topics. Afternoon sessions will cover various defensive topics, with a DevSecOps cluster of talks in stream two after afternoon tea break. | ||
| + | * Security Professionals and Enthusiasts: Technical sessions later in the day will showcase new and interesting attack and defence topics. | ||
<br> '''Who Should Attend Global AppSec APAC 2013:''' | <br> '''Who Should Attend Global AppSec APAC 2013:''' | ||
| Line 77: | Line 78: | ||
| − | {|border="0" class="FCK__ShowTableBorders" style="width: | + | {|border="0" class="FCK__ShowTableBorders" style="width: 100%;" |
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Course Name''' </font><br> | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Course Name''' </font><br> | ||
| Line 85: | Line 86: | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Language''' </font><br> | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Language''' </font><br> | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Price'''</font> | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Price'''</font> | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Slides'''</font> | ||
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Advanced Android and iOS Hands-on Exploitation Course | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Advanced Android and iOS Hands-on Exploitation Course | ||
| − | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Aditya Gupta and Subho Halder ( | + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Aditya Gupta(XYSec) and Subho Halder (TCS) |
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 2 Days | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 2 Days | ||
| align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Tuesday and Wednesday, Feb 19-20 | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Tuesday and Wednesday, Feb 19-20 | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $800 USD | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $800 USD | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | [mailto:[email protected] Contact Trainer] | ||
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | HACKED - The OWASP Top 10 - Incident Response | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | HACKED - The OWASP Top 10 - Incident Response | ||
| Line 99: | Line 102: | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $800 USD | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $800 USD | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | [mailto:[email protected] Contact Trainer] | ||
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | CISO training: Managing Web & Application Security for senior manager | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | CISO training: Managing Web & Application Security for senior manager | ||
| Line 106: | Line 110: | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $400 USD | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $400 USD | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | [mailto:[email protected] Contact Trainer] | ||
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | HTML 5 | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | HTML 5 | ||
| Line 113: | Line 118: | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Korean | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Korean | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $400 USD | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | $400 USD | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | [mailto:[email protected] Contact Trainer] | ||
|- | |- | ||
| align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Developer Workshop: Approaching Secure Code – Where do I start? | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Developer Workshop: Approaching Secure Code – Where do I start? | ||
| Line 120: | Line 126: | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | FREE | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | FREE | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | [https://www.owasp.org/index.php/File:Access_Control_Pitfalls_v1.5.pptx Access Control Pitfalls], [https://www.owasp.org/images/d/d7/OWASP_Top_Ten_Defenses_v5.pdf OWASP Top 10 Defenses] | ||
|- | |- | ||
|} | |} | ||
| Line 131: | Line 138: | ||
===Advanced Android and iOS Hands-on Exploitation Course=== | ===Advanced Android and iOS Hands-on Exploitation Course=== | ||
| − | '''Trainers:''' Aditya Gupta and Subho Halder ( | + | '''Trainers:''' Aditya Gupta (XYSec) and Subho Halder (TCS)<br> |
'''Audience:''' Management, Technical, DevOps, Developers <br> | '''Audience:''' Management, Technical, DevOps, Developers <br> | ||
'''Level:''' Basic, Intermediate <br> | '''Level:''' Basic, Intermediate <br> | ||
| Line 154: | Line 161: | ||
| − | '''Subho Halder''' is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks. | + | '''Subho Halder''' is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks, and currently working at Tata Consultancy Services. |
| Line 288: | Line 295: | ||
'''Jim Manico''' is an OWASP volunteer who leads the OWASP Cheat Sheet Series and produces the OWASP Podcast Series. Jim is also the VP of Security Architecture at WhiteHat Security. Jim provides secure coding and developer awareness training for WhiteHat Security using his 8+ years of experience delivering developer-training courses for SANS, Aspect Security and others. He brings 16 years of database-driven Web software development and analysis experience to WhiteHat and OWASP. | '''Jim Manico''' is an OWASP volunteer who leads the OWASP Cheat Sheet Series and produces the OWASP Podcast Series. Jim is also the VP of Security Architecture at WhiteHat Security. Jim provides secure coding and developer awareness training for WhiteHat Security using his 8+ years of experience delivering developer-training courses for SANS, Aspect Security and others. He brings 16 years of database-driven Web software development and analysis experience to WhiteHat and OWASP. | ||
| + | |||
| + | |||
| + | =Schedule= | ||
| + | |||
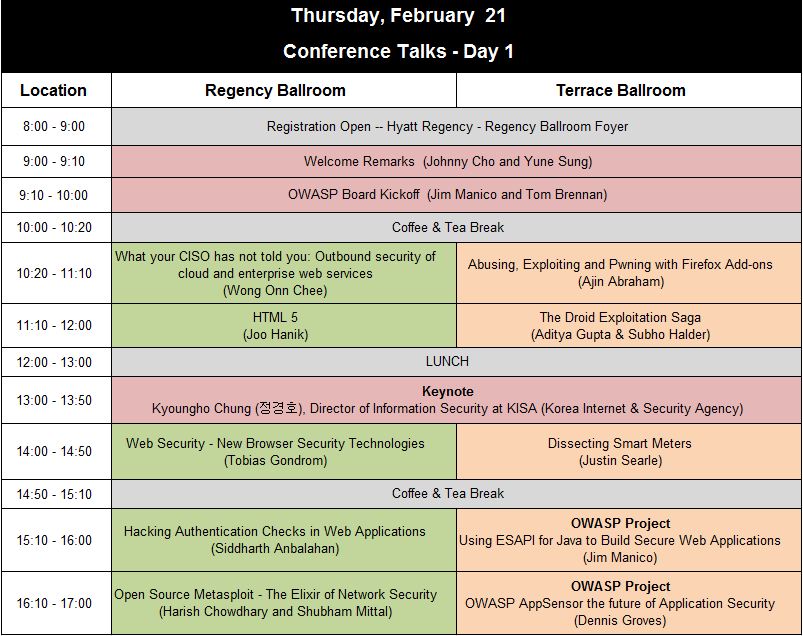
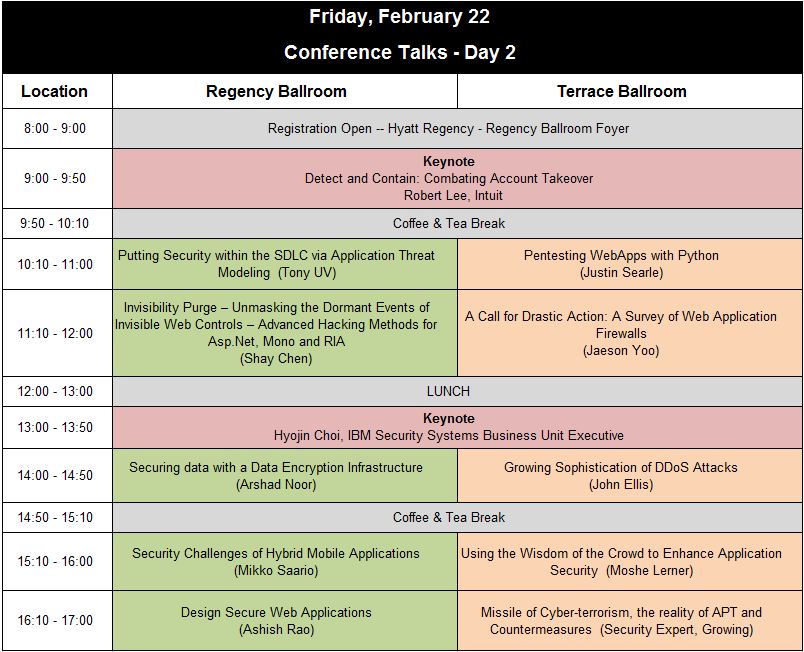
| + | '''[https://www.owasp.org/images/a/a2/APAC13_Thurs_Schedule.pdf PDF of Schedule Day 1 (Thursday)] | [https://www.owasp.org/images/9/9f/APAC13_Friday_Schedule.pdf PDF of Schedule Day 2 (Friday)]''' | ||
| + | |||
| + | |||
| + | |||
| + | [[Image:APAC13_Conference_Talks_Thursday.JPG|link=https://www.owasp.org/images/a/a2/APAC13_Thurs_Schedule.pdf]] | ||
| + | |||
| + | |||
| + | [[Image:APAC13_Conference_Talks_Friday.JPG|link=https://www.owasp.org/images/9/9f/APAC13_Friday_Schedule.pdf]] | ||
| Line 299: | Line 318: | ||
! width="1000" align="center" | <br> | ! width="1000" align="center" | <br> | ||
|- | |- | ||
| − | | align="center" | | + | | align="center" | [[Image:Kychung.png|100px]] |
| − | | align="justify" | <font size=3pt>'''Kyoungho Chung(정경호), | + | | align="justify" | <font size=3pt>'''Kyoungho Chung (정경호), Executive Vice President of KISA (Korea Internet & Security Agency) - User Perspective of security and privacy technology: Usability design for security [https://owasp.org/images/d/d3/Keynote-KISA.pdf (Download the Presentation)]'''</font> |
| + | |||
| + | The conventional definition of information security has only related to the confidentiality, integrity. | ||
| + | However, one the apparent failure of information security stem from the failure of usability. | ||
| + | |||
| + | The lack of an understandable conceptual model, security will be always hard to understand | ||
| + | for users and administrators. A new approach in designing | ||
| + | security and usability for information technology is needed. | ||
| + | |||
| + | '''Kyungho Chung''' is an executive vice president of Korea Internet & Security Agency (KISA) and in charge of information security group. He majored in Industrial and Systems Engineering and received the B.S. degree from Hanyang University, the M.S degree from Seoul National University, and the Ph. D. degree from Virginia Polytechnic Institute and State University. | ||
| + | He also served as a information security project manager of Korea Communications Commission (KCC) from 2009 to 2011. | ||
| + | He has involved many national R&D projects for cybersecurity and long-term IT strategies. | ||
| − | |||
|} | |} | ||
| − | |||
{| style="background-color: transparent" | {| style="background-color: transparent" | ||
| Line 311: | Line 339: | ||
! width="1000" align="center" | <br> | ! width="1000" align="center" | <br> | ||
|- | |- | ||
| − | | align="center" | | + | | align="center" | [[Image:HJ Choi.png|100px]] |
| − | | align="justify" | <font size=3pt>'''Hyojin Choi | + | | align="justify" | <font size=3pt>'''Hyojin Choi (IBM Security Systems Business Unit Executive)''' - '''Global Security Trend in 2013 and the Importance of IBM Security Philosophy "Secure by Design" [https://owasp.org/images/b/b2/APAC13_Keynote_HyojinChoi.pdf (Download the Presentation)]'''</font> |
| + | |||
| + | Review four major global security trend, cloud computing, big data, mobile, APT and Security Intelligence, | ||
| + | and understand IBM security philosophy "Secure by Design" that emphasizes on the importance of security from the beginning of designing business and IT | ||
| + | |||
| + | From IBM Security Systems business unit perspective, four major security trend , big data, cloud, mobile(BYOD) and APT & security intelligence are drawing significant attention from security officials. At this point in time, it is imperative to pay attention to security and secure coding from its business and IT designing stage so that customer trust and development productivity will increase and cost will go down. | ||
| + | |||
| − | + | '''Hyojin Choi''' is seasoned security expert spending his 16 year career at CA, Oracle and IBM with security business insight. | |
| + | He is currently leading IBM Korea security business as Security Systems Business Unit Executive. In his tenure, he has launched and succeeded in implementing a number of strategic business initiatives and one of the typical successes is quick start of SIEM business introduction that was initiated by Q1 Labs merger by IBM in October 2011. | ||
|} | |} | ||
| − | |||
{| style="background-color: transparent" | {| style="background-color: transparent" | ||
| Line 325: | Line 359: | ||
|- | |- | ||
| align="center" | [[Image:Robertelee.jpg|100px]] | | align="center" | [[Image:Robertelee.jpg|100px]] | ||
| − | | align="justify" | <font size=3pt>'''Robert Lee''' - '''Detect and Contain: Combating Account Takeover'''</font> | + | | align="justify" | <font size=3pt>'''Robert Lee''' - '''Detect and Contain: Combating Account Takeover [https://owasp.org/images/7/7a/APAC13_Keynote_-_Robert_Lee.pdf (Download the Presentation)]'''</font> |
In your environment, do you really know Who is doing What, from Where? How confident are you in your authentication controls? Does your behavior monitoring solution have the right input to give you relevant actionable findings? Are you overly burdening your users in the name of security, while still leaving them unprotected? | In your environment, do you really know Who is doing What, from Where? How confident are you in your authentication controls? Does your behavior monitoring solution have the right input to give you relevant actionable findings? Are you overly burdening your users in the name of security, while still leaving them unprotected? | ||
| Line 358: | Line 392: | ||
| − | = | + | =Speaker Bios= |
<font size=2pt> | <font size=2pt> | ||
| Line 407: | Line 441: | ||
Raised in Seoul and Los Angeles, Jaeson holds a BA from Occidental College in California, and was selected for the California Executive Fellowship program and Phi Beta Kappa. | Raised in Seoul and Los Angeles, Jaeson holds a BA from Occidental College in California, and was selected for the California Executive Fellowship program and Phi Beta Kappa. | ||
| + | |||
| + | |||
| + | ===John Ellis=== | ||
| + | John Ellis is Director of Enterprise Security, Asia Pacific & Japan (APJ) for Akamai Technologies. He is responsible for driving Akamai's Enterprise Security program to help meet the security needs of its customers in the region. | ||
| + | |||
| + | With over eighteen years of IT Security experience, John has developed an innate understanding of the complex challenges that face today's hyper connected world. John's career initially started in the military and has transitioned through several major industries such as financial services and telecommunications. John's exposure to multiple industry verticals has allowed him to hone his skills to better understand how organizations can balance their IT security investments to minimize risk yet maximize their opportunities. | ||
| + | |||
| + | Hailing from New Zealand, John relocated to Singapore in 2006, and now calls it home. Prior to Singapore, John had lived in Australia in addition to his homeland of New Zealand. Now that he's based in Asia, John has taken the opportunity to "try" and learn to speak, read, and write conversational Mandarin, and is continuing to improve his understanding of Asian culture. | ||
| Line 415: | Line 457: | ||
===Mikko Saario=== | ===Mikko Saario=== | ||
Mikko Saario is a senior security manager at Nokia overseeing security for developing and operating key internet-based services. He drives the secure development practices, security testing and internal training efforts of the unit and in addition spends his ample free time to arrange OWASP Helsinki, Finland chapter activities, contributes to the SAFECode security guidance efforts and messes with technologies such as Windows Phone 8 and the Qt project. | Mikko Saario is a senior security manager at Nokia overseeing security for developing and operating key internet-based services. He drives the secure development practices, security testing and internal training efforts of the unit and in addition spends his ample free time to arrange OWASP Helsinki, Finland chapter activities, contributes to the SAFECode security guidance efforts and messes with technologies such as Windows Phone 8 and the Qt project. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 450: | Line 486: | ||
He recently conducted training on “Advanced Secure Code Review Techniques” at OWASP India 2012. | He recently conducted training on “Advanced Secure Code Review Techniques” at OWASP India 2012. | ||
| + | |||
| + | |||
| + | ===Shubham Mittal=== | ||
| + | Shubham Mittal is an active security researcher having keen interests in Penetration testing and Malware Analysis. Having expertise in Network and Web Application Security, he has actively contributed to many security research advisories like Exploit-DB, Packetstormsecurity, garage4hackers,. with his security based research papers. Also he has spoken in two National Level paper presentations and submitted a paper in an international journal too. Apart from this, he has discovered and reported flaws in many of the critical and prestigious websites and servers. He has performed Security Audits on many popular websites and web servers with complexity level up to hosting of 250 sites. He has given training to professionals from DRDO, CBI, Air force, IGI Technical Head, HCL technologies, Convergys, Adobe, Headstrong. He enjoys developing hacking tools, writing security articles, working on new techniques, attending professional meets, etc. meanwhile sharing his experience and skills with the Hackers community. Being an active member of Null - Open Information Security Community, he has been a regular speaker with his innovative ideas among the National Hackers. | ||
===Subho Halder=== | ===Subho Halder=== | ||
| − | Subho Halder is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks. | + | Subho Halder is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks, and currently working at Tata Consultancy Services. |
| Line 476: | Line 516: | ||
Tony currently leads the OWASP Atlanta Chapter, where he manages monthly workshops and events for the Atlanta web application security community. He is also serves on the OWASP Global Membership Board and regularly provides talks to other chapters nationwide, primarily on the topic of application threat modeling. Aside from the OWASP organization, Tony has helped to organize BSides Atlanta – an underground grassroots effort aimed at providing 100%, unsolicited security content to Atlanta Information Security professionals. | Tony currently leads the OWASP Atlanta Chapter, where he manages monthly workshops and events for the Atlanta web application security community. He is also serves on the OWASP Global Membership Board and regularly provides talks to other chapters nationwide, primarily on the topic of application threat modeling. Aside from the OWASP organization, Tony has helped to organize BSides Atlanta – an underground grassroots effort aimed at providing 100%, unsolicited security content to Atlanta Information Security professionals. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 499: | Line 535: | ||
===송인혁(SONG IHN-HYUK)=== | ===송인혁(SONG IHN-HYUK)=== | ||
| − | + | He has 6 years of experience in Information-security party with various institutions, for example, military's security, public institutions' security, financial-security and private companies' security. On the technology side, it's possible to do troubleshoot via strong skills; solved many complex technical problems. | |
| − | + | Through accident analysis he looks for a solution. Furthermore it's excellent to make a precautions. Recently he is a studying convergence-security and researching a physical-security solutions. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===주한익(Han-Ik Joo)=== | |
| − | + | Han-Ik Joo is a team leader in security team of Coresecurity Inc. and a Korean certified instructor who has taught about certification course in EC-Council. He likes to be consistently researching about malware analysis and vulnerability of software, web application and computer systems. He has a variety of experiences of lectures and conference on many companies and government agencies like SATTI (Samsung Advanced Technology Training Institute), Cyber Terror Response Center, army, navy and air force, Cyber Command, Defense Security Command and ETRI(Electronics Telecommunications Research institute). | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | = Talk Abstracts = | + | = Talk Abstracts and Presentations = |
<font size=2pt> | <font size=2pt> | ||
===Abusing, Exploiting and Pwning with Firefox Add-ons=== | ===Abusing, Exploiting and Pwning with Firefox Add-ons=== | ||
| − | '''Ajin Abraham''' | + | '''Ajin Abraham''' [https://docs.google.com/a/owasp.org/file/d/0B5Z9zE0hx0LNZWI0UC1MbjZCSEE/edit (Download the Presentation)] |
The talk is about abusing and exploiting Firefox add-on Security model and explains how JavaScript functions, XPCOM and XPConnect interfaces, technologies like CORS and WebSocket, Session storing and full privilege execution can be abused by a hacker for malicious purposes. The widely popular browser add-ons can be targeted by hackers to implement new malicious attack vectors resulting in confidential data theft and full system compromise. This paper is supported by proof of concept add-ons which abuse and exploits the add-on coding in Firefox 17, the release which Mozilla boasts to have a more secure architecture against malicious plugins and add-ons. The proof of concept includes the implementation of a Local keylogger, a Remote keylogger, stealing Linux password files, spawning a Reverse Shell, stealing the authenticated Firefox session data, and Remote DDoS attack. All of these attack vectors are fully undetectable against anti-virus solutions and can bypass protection mechanisms. | The talk is about abusing and exploiting Firefox add-on Security model and explains how JavaScript functions, XPCOM and XPConnect interfaces, technologies like CORS and WebSocket, Session storing and full privilege execution can be abused by a hacker for malicious purposes. The widely popular browser add-ons can be targeted by hackers to implement new malicious attack vectors resulting in confidential data theft and full system compromise. This paper is supported by proof of concept add-ons which abuse and exploits the add-on coding in Firefox 17, the release which Mozilla boasts to have a more secure architecture against malicious plugins and add-ons. The proof of concept includes the implementation of a Local keylogger, a Remote keylogger, stealing Linux password files, spawning a Reverse Shell, stealing the authenticated Firefox session data, and Remote DDoS attack. All of these attack vectors are fully undetectable against anti-virus solutions and can bypass protection mechanisms. | ||
| Line 548: | Line 554: | ||
===A Call for Drastic Action: A Survey of Web Application Firewalls=== | ===A Call for Drastic Action: A Survey of Web Application Firewalls=== | ||
| − | '''Jaeson Yoo''' | + | '''Jaeson Yoo''' [https://owasp.org/images/2/2b/APAC13_Jaeson_Yoo.pdf (Download the Presentation)] |
Web application firewalls (WAFs) have become an unquestioned necessity in the modern world. | Web application firewalls (WAFs) have become an unquestioned necessity in the modern world. | ||
| Line 578: | Line 584: | ||
===Design Secure Web Applications=== | ===Design Secure Web Applications=== | ||
| − | '''Ashish Rao''' | + | '''Ashish Rao''' [https://www.owasp.org/images/f/f4/APAC13_Ashish_Rao.pdf (Download the Presentation)] |
| + | |||
| + | |||
| + | [https://www.owasp.org/images/f/f7/Checklist_For_Design.pdf Checklist for securing web application design] | ||
| + | |||
We are all aware of “secure coding” and practice it to great extent while developing applications. But do we give equal attention to – “Secure Design”? Most of us would probably say, NO. Design level flaws are lesser known concepts but their presence is a very big risk to the applications. Such flaws are hard to find in static or dynamic application scans and instead require deep understanding of application architecture and layout to uncover them manually. With increasing business needs the complexities in application design and architecture are also increasing. There is a rise in the use of custom design techniques and diverse technologies in the applications today. But in the midst of all this, have we ever thought about design level security? | We are all aware of “secure coding” and practice it to great extent while developing applications. But do we give equal attention to – “Secure Design”? Most of us would probably say, NO. Design level flaws are lesser known concepts but their presence is a very big risk to the applications. Such flaws are hard to find in static or dynamic application scans and instead require deep understanding of application architecture and layout to uncover them manually. With increasing business needs the complexities in application design and architecture are also increasing. There is a rise in the use of custom design techniques and diverse technologies in the applications today. But in the midst of all this, have we ever thought about design level security? | ||
| Line 590: | Line 600: | ||
===Dissecting Smart Meters=== | ===Dissecting Smart Meters=== | ||
| − | '''Justin Searle''' | + | '''Justin Searle''' [https://owasp.org/images/2/2a/APAC13_Justin_Searle_-_Dissecting_Smart_Meters_v4.pdf (Download the Presentation)] |
The Smart Grid brings greater benefits for electric utilities and customer alike, however these benefits come at a cost from a security perspective. This presentation will explore the architecture of most Smart Meters, the protocols they use, a breakdown of their embedded components, and the functionality their headend servers contain. We'll explain the methodologies we've developed to perform penetration testing these AMI systems, enumerate the types of vulnerabilities we commonly find, and discuss the solutions we recommend to Smart Meter vendors. We will even demonstrate at least one of the attacks we commonly perform in our penetration tests. This will be done without the FUD and over-hyped framing that we usually find in the media and other Smart Grid presentations. | The Smart Grid brings greater benefits for electric utilities and customer alike, however these benefits come at a cost from a security perspective. This presentation will explore the architecture of most Smart Meters, the protocols they use, a breakdown of their embedded components, and the functionality their headend servers contain. We'll explain the methodologies we've developed to perform penetration testing these AMI systems, enumerate the types of vulnerabilities we commonly find, and discuss the solutions we recommend to Smart Meter vendors. We will even demonstrate at least one of the attacks we commonly perform in our penetration tests. This will be done without the FUD and over-hyped framing that we usually find in the media and other Smart Grid presentations. | ||
| Line 596: | Line 606: | ||
===The Droid Exploitation Saga=== | ===The Droid Exploitation Saga=== | ||
| − | '''Aditya Gupta & Subho Halder''' | + | '''Aditya Gupta & Subho Halder''' [https://drive.google.com/a/owasp.org/?tab=mo#folders/0B5Z9zE0hx0LNZmgtazBya0dFMnc (Download the Presentation)] |
| − | + | In this talk, we will be discussing about the recent trends in Android Security Exploitation, as well as we will be carrying out all the possible attacks using a framework which we've designed called as Android Framework for Exploitation. | |
We will show how easy it could get to break into any Android Device, either using any exploit, or creating a malware using AFE. Also, in case the malware gets detected by any of the anti malwares, you 'll have the option to make it Fully Undetectable again and again, using the framework. | We will show how easy it could get to break into any Android Device, either using any exploit, or creating a malware using AFE. Also, in case the malware gets detected by any of the anti malwares, you 'll have the option to make it Fully Undetectable again and again, using the framework. | ||
| Line 605: | Line 615: | ||
We will be covering each topic with live demonstrations and will also discuss the case studies of vulnerabilities in some of the most popular android applications. | We will be covering each topic with live demonstrations and will also discuss the case studies of vulnerabilities in some of the most popular android applications. | ||
| + | |||
| + | |||
| + | ===Growing sophistication of DDoS attacks=== | ||
| + | '''John Ellis''' [https://owasp.org/images/6/68/APAC13_John_Ellis.pdf (Download the Presentation)] | ||
| + | |||
| + | 2012 saw the unprecedented growth in DDoS attacks, not only in volume but also in sophistication. | ||
| + | |||
| + | Gone are the days where DDoS attacks were the simple cheap and nasty, simplistic syn floods. Now they have evolved into a powerful cyber weapon, a weapon of choice for: | ||
| + | cyber extortion, aiding cyber criminals in their fraud activities, and hacktivists in pushing their cause. | ||
| + | |||
| + | Join John Ellis as he takes a deep dive into the growing sophistication of DDoS attack and examines:latest tools like 'itsoknoproblembro'the migration from the botnet to the Virtual Private Systems (VPS) as the attack platform of choice evolving C2 architecture the use of multi-vector attacks and the increasing attacks against and over SSL | ||
| + | common approaches to defending against these attacks, whats worked and what hasn't what organisations should be thinking about next; and ideas on how to build a protect and perform strategy along with the message to senior management to secure funding. | ||
===Hacking Authentication Checks in Web Applications=== | ===Hacking Authentication Checks in Web Applications=== | ||
| − | '''Siddharth Anbalahan''' | + | '''Siddharth Anbalahan''' [https://www.owasp.org/images/c/c2/APAC13_Siddharth_Anabalahan.pdf (Download the Presentation)] |
Authentication is one of the most coveted and targeted features for security attacks. Despite its importance and sensitivity we still fail to see robust implementations of this control in our applications. Developers just don’t seem to get it right and security researchers just cannot stop identifying flaws in them. In this talk we will look at 4 insecure authentication control implementation in web applications that will leave you astounded and make you understand why most of the applications will be prone to these flaws. | Authentication is one of the most coveted and targeted features for security attacks. Despite its importance and sensitivity we still fail to see robust implementations of this control in our applications. Developers just don’t seem to get it right and security researchers just cannot stop identifying flaws in them. In this talk we will look at 4 insecure authentication control implementation in web applications that will leave you astounded and make you understand why most of the applications will be prone to these flaws. | ||
| − | === | + | ===HTML 5 === |
| − | ''' | + | '''Han-Ik Joo''' [https://www.owasp.org/images/6/6c/APAC13_JooHanik.pdf (Download the Presentation)] |
| + | |||
| + | HTML5 unlike the predecessors HTML that was impossible to implement features is the next generation standard language. However, vulnerability also is extended, and the fact that it is now possible to bypass existing countermeasures for Web-based security threats. In this talk, We will handle Demonstrations and the presentation of the security threats that can occur in the browser with the newly added features in HTML5. This talk include the following information as below: | ||
| − | + | *CSRF Using XHR Level2 | |
| − | *XHR Level2 | + | *XSS using Newly added tag in HTML5 |
| − | *HTML5 | + | *Web Storage using information extraction |
| − | * | + | *WebSQL Information extraction using JavaScript |
| − | * | + | *Web Worker Injection |
| − | *Web Worker | ||
===Invisibility Purge – Unmasking the Dormant Events of Invisible Web Controls – Advanced Hacking Methods for Asp.Net, Mono and RIA=== | ===Invisibility Purge – Unmasking the Dormant Events of Invisible Web Controls – Advanced Hacking Methods for Asp.Net, Mono and RIA=== | ||
| − | '''Shay Chen''' | + | '''Shay Chen''' [https://owasp.org/images/6/6d/APAC13_ShayChen.pdf (Download the Presentation)] |
Web Controls have become common in many popular platforms, enhancing the software lifecycle by speeding up development, and enabling developers to reuse custom content. | Web Controls have become common in many popular platforms, enhancing the software lifecycle by speeding up development, and enabling developers to reuse custom content. | ||
| Line 649: | Line 672: | ||
===Missile of Cyber-terrorism, the reality of APT and Countermeasures=== | ===Missile of Cyber-terrorism, the reality of APT and Countermeasures=== | ||
| − | '''Security Expert, Growing''' | + | '''Security Expert, Growing''' [https://owasp.org/images/9/9f/APAC13_Ihn-Hyuk._Song.pdf (Download the Presentation)] |
APT’s attack is represented intelligented and sophisticated Hacking. As a result APT can be used to disturb the tackets. Here, this paper proposed to understand the reality of APT. In other words, APT’s definitions, properties, and Life-Cycle. Depending on derived properties, Security defense strategy is suggested differently. | APT’s attack is represented intelligented and sophisticated Hacking. As a result APT can be used to disturb the tackets. Here, this paper proposed to understand the reality of APT. In other words, APT’s definitions, properties, and Life-Cycle. Depending on derived properties, Security defense strategy is suggested differently. | ||
| − | ===Open Source Metasploit - The Elixir of Network Security=== | + | === Open Source Metasploit - The Elixir of Network Security=== |
| − | '''Harish Chowdhary and Shubham Mittal''' | + | '''Harish Chowdhary and Shubham Mittal''' |
| + | |||
| + | <span style="color:red"> Talk Cancelled </span> | ||
Today every organization intensely relies on the communication. Every part of an organization ought to operate closely & ought to be interconnected for the benefit of the organization. The term interconnected & communication signifies one of the most vital a part of an organization primarily of an IT organization is the Computer NETWORK. | Today every organization intensely relies on the communication. Every part of an organization ought to operate closely & ought to be interconnected for the benefit of the organization. The term interconnected & communication signifies one of the most vital a part of an organization primarily of an IT organization is the Computer NETWORK. | ||
| Line 662: | Line 687: | ||
What is Metaspliot, how to use Metasploit for Penetration testing & its various advantages, how to customize you pen test. It will additionally also put lights on, how to find the intrusion in the network & mitigation techniques to keep away from the cyber assaults. Whole, the objective of this paper is to provide a detailed understanding of what is Metasploit and how to utilize it as a security professional. | What is Metaspliot, how to use Metasploit for Penetration testing & its various advantages, how to customize you pen test. It will additionally also put lights on, how to find the intrusion in the network & mitigation techniques to keep away from the cyber assaults. Whole, the objective of this paper is to provide a detailed understanding of what is Metasploit and how to utilize it as a security professional. | ||
| + | |||
| + | ===Pentesting Web Apps with Python=== | ||
| + | '''Justin Searle''' [https://owasp.org/images/5/58/APAC13_Justin_Searle_Python_Basics_for_Web_App_Pentesters.pdf (Download the Presentation)] | ||
| + | |||
| + | |||
| + | Interested in expanding your scripting skills to further customize your penetration testing approach? The goal of this talk is to teach you basic python skills you can use every day. Join one of the SamuraiWTF project leads and learn how to interact with websites using | ||
| + | python scripts and python shells. Understand the differences between the major HTTP libraries like httplib and urllib2. Walk through sample code that performs username harvesting and dictionary attacks. Learn how to use Python's multithreaded features to speed up your scripts. And most importantly, discover PyCIT, a new opensource | ||
| + | project that provides simple, documented, and functional python templates to accelerate your python scripting efforts. | ||
===Putting Security within the SDLC via Application Threat Modeling=== | ===Putting Security within the SDLC via Application Threat Modeling=== | ||
| − | '''Tony UV''' | + | '''Tony UV''' [https://owasp.org/images/0/0b/APAC13_TonyUV.pdf (Download the Presentation)] |
As delusions of effective risk management for application environments continue to spread, companies continue to bleed large amounts of security spending without truly knowing if the amount is warranted, effective, or even elevating security at all. In parallel, hybrid, thought provoking security strategies are moving beyond conceptual ideas to practical applications within ripe environments. Application Threat Modeling is one of those areas where, beyond the hype, provides practical and sensible security strategy that leverages already existing security efforts for an improved threat model of what is lurking in the shadows. | As delusions of effective risk management for application environments continue to spread, companies continue to bleed large amounts of security spending without truly knowing if the amount is warranted, effective, or even elevating security at all. In parallel, hybrid, thought provoking security strategies are moving beyond conceptual ideas to practical applications within ripe environments. Application Threat Modeling is one of those areas where, beyond the hype, provides practical and sensible security strategy that leverages already existing security efforts for an improved threat model of what is lurking in the shadows. | ||
| Line 677: | Line 710: | ||
===Securing data with a Data Encryption Infrastructure=== | ===Securing data with a Data Encryption Infrastructure=== | ||
| − | '''Arshad Noor''' | + | '''Arshad Noor''' [https://owasp.org/images/0/04/APAC13_Arshad_Noor.pdf (Download the Presentation)] |
As companies are challenged to keep up with an increasing number of data-security regulations worldwide, encryption of sensitive data has become the universal ""safe-harbor"", the last bastion of defense against unauthorized disclosure of data, mandated or highly recommended in every regulation. | As companies are challenged to keep up with an increasing number of data-security regulations worldwide, encryption of sensitive data has become the universal ""safe-harbor"", the last bastion of defense against unauthorized disclosure of data, mandated or highly recommended in every regulation. | ||
| Line 703: | Line 736: | ||
===Security Challenges of Hybrid Mobile Applications=== | ===Security Challenges of Hybrid Mobile Applications=== | ||
| − | '''Mikko Saario''' | + | '''Mikko Saario''' [https://owasp.org/images/2/29/APAC13_Mikko_Saario.pdf (Download the Presentation)] |
Mobile application development leveraging a hybrid technology stack is an accelerated way to bring new apps to market reusing existing competencies. Hybrid technology essentially refers to using several different coding languages instead of just the ""native"" one - whatever it may be in each case. Often existing code and services are reused to avoid expensive development for each distinctive platform. This way the ‘desktop web’ and the ‘mobile web’ are converging quickly - code can be shared and reused more and more. The focus technologies in this presentation are Windows Phone 8 and the Qt framework. Mikko will take a look into what kind of fundamental security mechanisms or threats do or do not exist in the two platforms to protect the user and the application from attacks when mixing several technology stacks. The expanding availability of development technologies opens up new attack surface, often with old attacks, to mobile applications: For instance, Windows Phone 8 introduced the possibility to implement applications in C++ in addition to the existing C#/Silverlight + web technologies. Are buffer overflows back? Qt is built on top of C++ and implements for instance the WebKit and QtQuick (QML with inline JavaScript) technologies for quickly developing cross-platform applications. The combination of these multiple stacks provide ample attack surface against mobile applications. | Mobile application development leveraging a hybrid technology stack is an accelerated way to bring new apps to market reusing existing competencies. Hybrid technology essentially refers to using several different coding languages instead of just the ""native"" one - whatever it may be in each case. Often existing code and services are reused to avoid expensive development for each distinctive platform. This way the ‘desktop web’ and the ‘mobile web’ are converging quickly - code can be shared and reused more and more. The focus technologies in this presentation are Windows Phone 8 and the Qt framework. Mikko will take a look into what kind of fundamental security mechanisms or threats do or do not exist in the two platforms to protect the user and the application from attacks when mixing several technology stacks. The expanding availability of development technologies opens up new attack surface, often with old attacks, to mobile applications: For instance, Windows Phone 8 introduced the possibility to implement applications in C++ in addition to the existing C#/Silverlight + web technologies. Are buffer overflows back? Qt is built on top of C++ and implements for instance the WebKit and QtQuick (QML with inline JavaScript) technologies for quickly developing cross-platform applications. The combination of these multiple stacks provide ample attack surface against mobile applications. | ||
| Line 710: | Line 743: | ||
During the testing vulnerabilities were discovered in both the WP8 and Qt platforms and these will be demoed in cases where the vendor has either fixed the issue or the information is otherwise already public. | During the testing vulnerabilities were discovered in both the WP8 and Qt platforms and these will be demoed in cases where the vendor has either fixed the issue or the information is otherwise already public. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
===Using the Wisdom of the Crowd to Enhance Application Security=== | ===Using the Wisdom of the Crowd to Enhance Application Security=== | ||
| − | '''Moshe Lerner''' | + | '''Moshe Lerner''' [https://owasp.org/images/6/69/APAC13_Moshe_Lerner.pdf (Download the Presentation)] |
Security-oriented source code analysis tools detect vulnerabilities only for well-defined hacks and tend to return many results which are hard to remediate. Two problems result: One, how can we overcome the lack of coverage? And two, how can we improve the ability to fix? | Security-oriented source code analysis tools detect vulnerabilities only for well-defined hacks and tend to return many results which are hard to remediate. Two problems result: One, how can we overcome the lack of coverage? And two, how can we improve the ability to fix? | ||
| Line 732: | Line 759: | ||
===Web Security - New Browser Security Technologies=== | ===Web Security - New Browser Security Technologies=== | ||
| − | '''Tobias Gondrom''' | + | '''Tobias Gondrom''' [https://owasp.org/images/b/b8/APAC13_TobiasGondrom.pdf (Download the Presentation)] |
This is cutting edge and will talk about new browser security technologies that have recently been developed and/or will be coming up in the coming months to counter risks that became apparent from the current trust model used in browsers. This will be improving channel protection and enabling better protection against XSS, Clickjacking and XSRF. | This is cutting edge and will talk about new browser security technologies that have recently been developed and/or will be coming up in the coming months to counter risks that became apparent from the current trust model used in browsers. This will be improving channel protection and enabling better protection against XSS, Clickjacking and XSRF. | ||
| Line 745: | Line 772: | ||
===What your CISO has not told you - Outbound security of cloud and enterprise web services=== | ===What your CISO has not told you - Outbound security of cloud and enterprise web services=== | ||
| − | '''Wong Onn Chee''' | + | '''Wong Onn Chee''' [https://owasp.org/images/4/4b/APAC13_Wong_Onn_Chee.pdf (Download the Presentation)] |
This presentation will cover an important topic which no CISO ever mentions. Cloud and enterprise e-services are accessible 24x7 by anyone across the world, especially via mobile devices. Yet, efforts for past decades have sorely neglected the outbound risks of enterprise e-services and, in recent years, cloud and mobile services. Without outbound protection, incidents such as leaking private data, infecting visitors with malware and displaying defaced web pages are often reported by the press, damaging reputation and customer confidence. With tighter data privacy laws, many organisations are risking hefty legal penalties if they continue to neglect this risk area. | This presentation will cover an important topic which no CISO ever mentions. Cloud and enterprise e-services are accessible 24x7 by anyone across the world, especially via mobile devices. Yet, efforts for past decades have sorely neglected the outbound risks of enterprise e-services and, in recent years, cloud and mobile services. Without outbound protection, incidents such as leaking private data, infecting visitors with malware and displaying defaced web pages are often reported by the press, damaging reputation and customer confidence. With tighter data privacy laws, many organisations are risking hefty legal penalties if they continue to neglect this risk area. | ||
| − | This talk will highlight the growing trend of web sites being used to leak information, transmit malware and display defaced content. The speaker will walk through a number of case studies and share with the audience on the lessons learnt from each case study. The speaker will also explain how the lack of outbound security protection contributed to the | + | This talk will highlight the growing trend of web sites being used to leak information, transmit malware and display defaced content. The speaker will walk through a number of case studies and share with the audience on the lessons learnt from each case study. The speaker will also explain how the lack of outbound security protection contributed to the realized risk in each case study. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 786: | Line 784: | ||
== == | == == | ||
| − | ==OWASP Project Track Talks== | + | ==OWASP Project Track Talks == |
===OWASP AppSensor the future of Application Security=== | ===OWASP AppSensor the future of Application Security=== | ||
| − | '''Dennis Groves''' | + | '''Dennis Groves''' [https://owasp.org/images/8/88/APAC13_Dennis_Groves.pdf (Download the Presentation)] |
The OWASP AppSensor is commonly described as an application layer intrusion detection system. However, it is far more that this. It is also an architecture design pattern, as well as a development practice and an operations methodology. I propose the following outline for my talk: | The OWASP AppSensor is commonly described as an application layer intrusion detection system. However, it is far more that this. It is also an architecture design pattern, as well as a development practice and an operations methodology. I propose the following outline for my talk: | ||
| Line 804: | Line 802: | ||
===Using ESAPI for Java to Build Secure Web Applications=== | ===Using ESAPI for Java to Build Secure Web Applications=== | ||
| − | '''Jim Manico''' | + | '''Jim Manico''' [https://owasp.org/images/5/57/APAC13_Jim_Manico.pdf (Download the Presentation)] |
We cannot “firewall” or “patch” our way to secure websites. In the past, security professionals thought firewalls, Secure Sockets Layer (SSL), patching, and privacy policies were enough. Today, however, these methods are outdated and ineffective, as attacks on prominent, well-protected websites are occurring every day. Organizations around the world rely on web security services to maintain the safety of their websites in today’s hostile online environment. Website developers must also learn to code in a secure fashion to have any chance of providing organizations with proper defenses in the current threat-scape. The session will provide specific tips and guidelines to make website code both low risk and less vulnerable using the OWASP ESAPI for Java project. | We cannot “firewall” or “patch” our way to secure websites. In the past, security professionals thought firewalls, Secure Sockets Layer (SSL), patching, and privacy policies were enough. Today, however, these methods are outdated and ineffective, as attacks on prominent, well-protected websites are occurring every day. Organizations around the world rely on web security services to maintain the safety of their websites in today’s hostile online environment. Website developers must also learn to code in a secure fashion to have any chance of providing organizations with proper defenses in the current threat-scape. The session will provide specific tips and guidelines to make website code both low risk and less vulnerable using the OWASP ESAPI for Java project. | ||
| Line 812: | Line 810: | ||
<font size=2pt> | <font size=2pt> | ||
AppSec APAC 2013 will be held at the [http://jeju.regency.hyatt.com Hyatt Regency] in Jeju, South Korea. | AppSec APAC 2013 will be held at the [http://jeju.regency.hyatt.com Hyatt Regency] in Jeju, South Korea. | ||
| + | |||
| + | |||
| + | The conference training and talk will be held in the Regency Ballroom and Terrace Ballroom. Exhibitor booths will be set up in the foyer outside the ballrooms on Thursday and Friday. | ||
| + | |||
| + | |||
| + | [[Image:APAC13_Floorplan.JPG]] | ||
| Line 837: | Line 841: | ||
| + | '''[https://www.owasp.org/images/5/51/Exhibitor_Kit_-_AppSec_APAC_2013.pdf Conference Exhibitor Information Pack]''' | ||
| Line 849: | Line 854: | ||
| − | Additionally, the [mailto: | + | Additionally, the [mailto:appsecapac2013@owasp.org Conference Planning Team] is available to answer any questions! |
| Line 862: | Line 867: | ||
'''Hyatt Regency Jeju'''<br> | '''Hyatt Regency Jeju'''<br> | ||
114, Jungmungwangwang-ro 72 beon-gil, Seogwipo-si<br> | 114, Jungmungwangwang-ro 72 beon-gil, Seogwipo-si<br> | ||
| − | + | Jeju Special Self-Governing Province <br> | |
South Korea 697-130 <br> | South Korea 697-130 <br> | ||
| Line 968: | Line 973: | ||
==2013 AppSec APAC Conference Volunteer Team== | ==2013 AppSec APAC Conference Volunteer Team== | ||
| − | |||
| − | |||
| − | |||
| − | '''Do you want to volunteer for AppSec APAC 2013?''' [ | + | |
| + | '''Do you want to volunteer for AppSec APAC 2013?''' [Click here to sign up] | ||
==OWASP Staff Support== | ==OWASP Staff Support== | ||
| − | * | + | * Laura Grau |
| − | |||
* Kelly Santalucia | * Kelly Santalucia | ||
* Kate Hartmann | * Kate Hartmann | ||
| − | + | ||
| Line 990: | Line 992: | ||
<headertabs /> | <headertabs /> | ||
| − | + | ||
[[Category:OWASP_AppSec_Conference]] | [[Category:OWASP_AppSec_Conference]] | ||
Latest revision as of 10:12, 28 June 2017
| |
|
|---|---|

|
- Welcome
- Training
- Schedule
- Keynotes
- Speaker Bios
- Talk Abstracts and Presentations
- Open Source Projects
- Venue
- Registration and Fees
- Sponsoring
- Travel and Accommodation
- Networking Events
- Chapter Leader Workshop
- Team
|
|
Overview of the training classes: Scroll down for details on each course and trainer bios.
| Course Name |
Trainer |
Course Length |
Course Date(s) |
Language |
Price | Slides |
| Advanced Android and iOS Hands-on Exploitation Course | Aditya Gupta(XYSec) and Subho Halder (TCS) | 2 Days | Tuesday and Wednesday, Feb 19-20 | English | $800 USD | Contact Trainer |
| HACKED - The OWASP Top 10 - Incident Response | Jonathan Spruill (Trustwave Spiderlabs) | 2 Days | Tuesday and Wednesday, Feb 19-20 | English | $800 USD | Contact Trainer |
| CISO training: Managing Web & Application Security for senior manager | Tobias Gondrom (Thames Stanley) | 1 Day | Wednesday, Feb 20 | English | $400 USD | Contact Trainer |
| HTML 5 | Kim TI (Core Security) | 1 Day | Wednesday, Feb 20 | Korean | $400 USD | Contact Trainer |
| Developer Workshop: Approaching Secure Code – Where do I start? | Jim Manico | 1/2 Day (4 hours) | Wednesday, Feb 20 | English | FREE | Access Control Pitfalls, OWASP Top 10 Defenses |
Two Day Training Courses
Two day training courses will take place on Tuesday & Wednesday, February 19-20, 2013. Training will run from 9am to 5pm each day with a 1 hour break for lunch.
Advanced Android and iOS Hands-on Exploitation Course
Trainers: Aditya Gupta (XYSec) and Subho Halder (TCS)
Audience: Management, Technical, DevOps, Developers
Level: Basic, Intermediate
Language: Training will be conducted in English
Course Summary:
This fast-paced workshop will get you familiar with the various Android as well as iOS exploitation techniques, and bypassing most of the existing security models in both of the platforms. We will also discuss about a framework, which we have made for Android Exploitation, named as the Android Framework for Exploitation, which will help security researchers to perform automated and in-depth analysis of bug hunting and security assessment of Android Application and platforms.
For iOS, we will be looking into the application security assessment, creating a pentest environment, present sandboxing model, and much more. We will also be looking into Android rooting and iOS jailbreaking exploits, and recreate the scenario from the scratch.
Aditya Gupta is a renowned mobile security expert and information security researcher. Also being the lead developer and co-creator of Android Framework for Exploitation, he has done a lot of in-depth research on the security of mobile devices including Android, iOS and Blackberry.
He has also discovered serious security flaws in websites such as Google, Apple, Microsoft, Adobe, Skype and many more. In his work with XYSEC, he is committed to perform VAPT and Mobile Application Security Analysis. He has also been working with government clients and intelligence agencies in India, as well as providing them trainings and services on Malware Analysis, Exploit Development and Advanced Web App Hacking.
He has also previously spoken at a bunch of conferences including BlackHat, Toorcon, ClubHack, Nullcon, THC, Defcon India Chapter and many more.
Subho Halder is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks, and currently working at Tata Consultancy Services.
HACKED - The OWASP Top 10 - Incident Response
Trainer: Jonathan Spruill (Trustwave Spiderlabs)
Audience: Management, Technical, Operations, DevOps, Law Enforcement
Level: Intermediate, Advanced
Language: Training will be conducted in English
Course Summary:
After completing this course, you will possess the skills to successfully conduct a basic network intrusion investigation that adheres to a formal methodology to ensure the admissibility of evidence in a court of law and ultimately increases the chances of apprehending the intruder. You will engage in hands-‐on labs and instructor demos of network intrusion concepts in a “real-‐world” environment. The real-‐world environment is made possible through the use of Virtual Machines (VMs). Each VM is pre-‐configured to mimic the different Operating Systems(OSs), network environments and intrusion issues that you may encounter.
Note: Students must furnish their own laptop running a version of Microsoft Windows. VMware Workstation or Server will also be required in order to participate in the hands-‐on labs. Laptop should have at least 20GB of free space.
Jonathan Spruill is a Security Consultant at Trustwave. He is a member of Trustwave's SpiderLabs - the advanced security team focused on penetration testing, incident response, and application security. He has over 9 years of investigative experience in computer crimes and intrusion cases. Prior to joining SpiderLabs, Jon was a Special Agent with the United States Secret Service. During this time he was an active member of the Electronic Crimes Special Agent Program and is an expert in computer and cellular phone forensics. The results of Jon's investigations and examinations resulted in the successful prosecution of numerous cases at both the federal and state levels.
Jonathan is an EnCase Certified Examiner (EnCE), Offensive Security Wireless Professional(OSWP) and holds a Top Secret (TS) clearance. He is currently working towards the CISSP certification and OSCP certifications.
Jonathan has conducted extensive research on Apple's iOS operating system and other cell phone artifacts. He has presented to numerous private and
law enforcement entities on topics ranging from counterfeit currency detection to advanced forensic analysis.
One Day Training Courses
One Day Training Courses will take place on Wednesday, February 20, 2013. Training will run from 9am to 5pm with a 1 hour break for lunch.
CISO training: Managing Web & Application Security for senior managers
Trainer: Tobias Gondrom (Thames Stanley)
Audience: Management
Level: Basic, Intermediate, Advanced
Language: Training will be conducted in English
Course Summary:
Setting up, managing and improving your global information security organisation using mature OWASP projects and tools. Achieving cost-effective application security and bringing it all together on the management level. How to use and leverage OWASP and other common best practices to improve your security programs and organization. The workshop will also discuss a number of quick wins and how to effectively manage global security initiatives and use OWASP tools inside your organisation. The author has extensive experience of managing his own secure development organization as well as advising to improve a number of global secure development organisations and processes.
Topics:
- Managing Web & Application Security in large global organisations
- OWASP Top-10 and OWASP projects - how to use within your organisation
- Risk management and threat modeling methods (OWASP risk analysis, ISO-27005,...)
- Benchmarking & Maturity Models
- Organisational Design and managing change for global information security programs
- Secure SDLC
- Training: OWASP Secure Coding Practices - Quick Reference Guide, Development Guide, Training tools for developers
- Measuring & Verification: ASVS (Application Security Verification Standard) Project, Code Review Guide, Testing Guide
- Development & Operation: Frameworks and Tools, e.g. AppSensor
All discussion and issues raised by participants at the workshop will be under the confidentiality under the Chatham House Rule (http://en.wikipedia.org/wiki/Chatham_House_Rule).
Tobias Gondrom is Managing Director of Thames Stanley, a CISO and Information Security & Risk Management Advisory based in Hong Kong, United Kingdom and Germany. He has fifteen years of experience in software development, application security, cryptography, electronic signatures and global standardisation organisations working for independent software vendors and large global corporations in the financial, technology and government sector, in America, EMEA and APAC. As the Global Head of the Security Team at Open Text (2005-2007) and from 2000-2004 as the lead of the Security Task Force at IXOS Software AG, he was responsible for security, risk and incident management and introduced and implemented a secure SDLC used globally by development departments in the US, Canada, UK and Germany.
Since 2003 he is the chair of working groups of the IETF (www.ietf.org) in the security area, member of the IETF security directorate, and since 2010 chair of the formed web security WG at the IETF, and a former chapter lead of the German OWASP chapter from 2007 to 2008, and currently board member of OWASP London and member of the OWASP Global Industry Committee. Tobias is the author of the international standards RFC 4998 and RFC 6283 (Evidence Record Syntax) and co-author and contributor to a number of internet standards and papers on security and electronic signatures, as well as the co-author of the book „Secure Electronic Archiving“ (ISBN 3-87081-427-6) and the OWASP CISO guide and frequent presenter at conferences and publication of articles (e.g. AppSec, IETF, ISSE, Moderner Staat, VOI-booklet “Electronic Signature“, iX).
HTML 5
강사명: Kim TI (Core Security) 김태일 (코어시큐리티)
교육 참가자: 기술, 개발 및 운영, 개발자
참가자의 기술 요구 수준: 중간 단계
가능한 언어: 한국어
교육 요약:
HTML5 에서 새롭게 추가된 기능들을 이용하여 웹 어플리케이션에서 발생할 수 있는 보안 위협/ 대응 및 완화 방법.
- XHR Level2 를 이용한 CSRF & CORS 우회
- HTML5 에 새롭게 추가된 테그 및 속성을 이용한 XSS
- 자바스크립트를 이용한 Web Storage 정보 추출
- 자바스크립트를 이용한 WebSQL 정보 추출
교육 경험:
실무 / 강의 경력 13년
정보보안 기술교육을 중심으로 공공기관, 기업, 대학 강의
CEH /CHFI 해킹 및 컴퓨터포렌식 국제공인강사
IPv6 프로토콜 변환기 개발 참여 (2001년, I2Soft)
주민번호대체수단 I-PIN 모의해킹 수행 (2007년 한국정보보호진흥원)
現 ㈜코어시큐리티 대표이사 (CEO)
現 경찰수사연수원 외래교수
前 ㈜FSK시큐리티 지식사업부 부장
前 SH Information System 기술연구소 지식사업팀
前 보안 프리랜서 강사
[보유자격증]
CEH / CHFI /ECSA /LPT / CEI
Half Day Developer Workshop
This 4 hour developer workshop will take place on Wednesday, February 20, from 1pm-5pm. The Workshop is complementary for Conference Attendees.
Approaching Secure Code – Where do I start?
Trainer: Jim Manico
Audience: Developers (dev managers welcome, assign people from your team to attend). Bring yourself, no materials required.
Level: Basic
Language: Training will be conducted in English
Course Summary:
Regardless of your chosen/mandated framework for building web applications: Spring, Struts, Rails, PHP, Python, etc., you want to make your life easier, and potentially less embarrassing. Don’t be the one who left the door open for hackers. Learn handy tips from one of the world’s leading AppSec experts.
Jim Manico is an OWASP volunteer who leads the OWASP Cheat Sheet Series and produces the OWASP Podcast Series. Jim is also the VP of Security Architecture at WhiteHat Security. Jim provides secure coding and developer awareness training for WhiteHat Security using his 8+ years of experience delivering developer-training courses for SANS, Aspect Security and others. He brings 16 years of database-driven Web software development and analysis experience to WhiteHat and OWASP.
| |
|
|---|---|

|
Kyoungho Chung (정경호), Executive Vice President of KISA (Korea Internet & Security Agency) - User Perspective of security and privacy technology: Usability design for security (Download the Presentation)
The conventional definition of information security has only related to the confidentiality, integrity. However, one the apparent failure of information security stem from the failure of usability. The lack of an understandable conceptual model, security will be always hard to understand for users and administrators. A new approach in designing security and usability for information technology is needed. Kyungho Chung is an executive vice president of Korea Internet & Security Agency (KISA) and in charge of information security group. He majored in Industrial and Systems Engineering and received the B.S. degree from Hanyang University, the M.S degree from Seoul National University, and the Ph. D. degree from Virginia Polytechnic Institute and State University. He also served as a information security project manager of Korea Communications Commission (KCC) from 2009 to 2011. He has involved many national R&D projects for cybersecurity and long-term IT strategies. |
| |
|
|---|---|

|
Hyojin Choi (IBM Security Systems Business Unit Executive) - Global Security Trend in 2013 and the Importance of IBM Security Philosophy "Secure by Design" (Download the Presentation)
Review four major global security trend, cloud computing, big data, mobile, APT and Security Intelligence, and understand IBM security philosophy "Secure by Design" that emphasizes on the importance of security from the beginning of designing business and IT From IBM Security Systems business unit perspective, four major security trend , big data, cloud, mobile(BYOD) and APT & security intelligence are drawing significant attention from security officials. At this point in time, it is imperative to pay attention to security and secure coding from its business and IT designing stage so that customer trust and development productivity will increase and cost will go down.
|
| |
|
|---|---|

|
Robert Lee - Detect and Contain: Combating Account Takeover (Download the Presentation)
In your environment, do you really know Who is doing What, from Where? How confident are you in your authentication controls? Does your behavior monitoring solution have the right input to give you relevant actionable findings? Are you overly burdening your users in the name of security, while still leaving them unprotected? This talk will not cover application code reviews, or new advanced exploitation techniques. For this talk, I assume that you already have a mature SSDLC and Vulnerability Management practice. This talk will instead shine a light on very common identity, authentication, and link-analysis practices that inhibit you from properly detecting threats, and ultimately, containing them.
Robert is affiliated with the non-profit ISECOM organization and has contributed to open source projects such as OSSTMM, Unicornscan, and Sockstress. His current focus is on security controls that can help curb fraud in online applications. |
| |
|
|---|---|

|
Tom Brennan and Jim Manico (OWASP Global Board) - OWASP 2013 Update - Where we are.. Where we are going
https://www.owasp.org/index.php/User:Brennan
|
Aditya Gupta
Aditya Gupta is a renowned mobile security expert and information security researcher. Also being the lead developer and co-creator of Android Framework for Exploitation, he has done a lot of in-depth research on the security of mobile devices including Android, iOS and Blackberry.
He has also discovered serious security flaws in websites such as Google, Apple, Microsoft, Adobe, Skype and many more. In his work with XYSEC, he is commited to perform VAPT and Mobile Application Security Analysis. He has also been working with government clients and intelligence agencies in India, as well as providing them trainings and services on Malware Analysis, Exploit Development and Advanced Web App Hacking.
Ajin Abraham
Ajin Abraham is an Information Security Researcher. He is the creator of OWASP Xenotix XSS Exploit Framework. He had published different whitepapers and tools in the scope of Information Security. He is one among the top 10 in Chakravyuh 2012, India’s Biggest Ethical Hacking Competition. His area of interest includes web application penetration testing, coding tools, exploit development and fuzzing. He has been a speaker at many security conferences including Defcon Bangalore-India Chapter , ClubHack , nullcon Goa and many more.
Arshad Noor
Arshad Noor is the CTO of StrongAuth, Inc., a Silicon Valley based company focused on encryption and key-management since 2001. He is the creator of the industry's first open-source Symmetric Key Management System, the creator of the StrongKey CryptoEngine, an open-source library for securing data in the Cloud and the author of the Regulatory Compliant Cloud Computing (RC3) web-application architecture (presented at OWASP AppSec 2012).
Ashish Rao
Ashish Rao is a Senior Security Consultant and Project Manager at Paladion Networks Pvt. Ltd. He has a good application development background and is an expert in performing secure code reviews for J2EE and ASP.Net applications. He has reviewed many complex multi-tiered web and standalone applications of different frameworks and programming languages.
He has authored articles and blogs about secure coding and security best practices. He has also worked closely with development teams across the globe and has helped them to secure applications at the design and architecture level.
He also has the working knowledge of many static code analysis tools and has contributed immensely to enhance Paladion’s automated review capabilities by writing various easy-to-use code review scripts.
Other than secure code reviews, he possesses extensive knowledge regarding Penetration Tests and Vulnerability Assessment projects, and has conducted various internal and external trainings for Paladion.
He recently conducted trainings on “Advanced Secure Code Review Techniques” (including Application Design Flaws), at OWASP India 2012 and on Mobile Application Security at Clubhack 2012.
Dennis Groves
Dennis Groves is the founder of OWASP. He is a well known thought leader in application security who's work focuses on multidisciplinary approaches to information security risk management. He holds an MSc in Information Security from Royal Holloway, University of London. He is currently an expert for the UK mirror of ISO subcommittee 27, WG4.
Harish Chowdhary
Harish Chaudhary is a young, motivated and dynamic Software Quality Engineer at Aricent Group. He’s passionate for Security and Penetration Testing to safeguard Data from hackers. He’s a keen orator and has won himself a position by participating in testing conference organized at QA InfoTech Pvt Ltd. He is a member of Codeproject.com since 2008 and working as a freelance Technical writer. His articles have also made it to a Software Testing Magazine – ‘Testing Circus’.He is information security researcher and penetration tester, also working with PenTest and Hak9 magazine.His research paper on “Assuring Data Security by Penetration Testing” is selected for the presentation in the 11th International Software Testing Conference organized by QAI Global (STC 2011).He also presented his Research Paper on ""Databse Security in the light of Injection Attacks-A web Approach"" at ""Techno Tryst 2012"" National conference on Database Security, organised by Delhi Institute of Advanced Studies,Guru Gobind Singh Inderaprashta University.
Harish is an MCA from Delhi Institute Of Advanced studies, affiliated to Guru Gobind Singh IndraPrastha University. Harish holds Diploma in Software Engineering and Software Testing (QAI GLOBAL) and is also Microsoft certified SQL 2005 professional.He has given training to more than 1000 college students about information security at various universities and colleges.
Jaeson Yoo
Jaeson Yoo, Head of Global Business, Penta Security Systems, Inc.
Jaeson is responsible for managing Penta Security’s international business operations in all areas outside of South Korea and Japan, where the company has its headquarters and subsidiary office, respectively. Penta Security currently has global partners in Singapore, Malaysia, Thailand, Indonesia and Australia. Jaeson oversees business development, sales, marketing and technical support services for equipping enterprise- and medium-sized organizations with Penta Security’s innovative security solutions, including its web application firewall and database encryption/access control software.
Prior to joining Penta Security, Jaeson served as president of Rusko Co., Ltd., a private equity firm in Seoul that specializes in government projects in Russia, with participation from Korea’s public and private sectors. Jaeson has extensive experience in management consulting and investment banking, helping dozens of companies obtain capital injections and/or achieve operational efficiency.
Raised in Seoul and Los Angeles, Jaeson holds a BA from Occidental College in California, and was selected for the California Executive Fellowship program and Phi Beta Kappa.
John Ellis
John Ellis is Director of Enterprise Security, Asia Pacific & Japan (APJ) for Akamai Technologies. He is responsible for driving Akamai's Enterprise Security program to help meet the security needs of its customers in the region.
With over eighteen years of IT Security experience, John has developed an innate understanding of the complex challenges that face today's hyper connected world. John's career initially started in the military and has transitioned through several major industries such as financial services and telecommunications. John's exposure to multiple industry verticals has allowed him to hone his skills to better understand how organizations can balance their IT security investments to minimize risk yet maximize their opportunities.
Hailing from New Zealand, John relocated to Singapore in 2006, and now calls it home. Prior to Singapore, John had lived in Australia in addition to his homeland of New Zealand. Now that he's based in Asia, John has taken the opportunity to "try" and learn to speak, read, and write conversational Mandarin, and is continuing to improve his understanding of Asian culture.
Justin Searle
Justin is a Managing Partner of UtiliSec, specializing in Smart Grid security architecture design and penetration testing. Justin led the Smart Grid Security Architecture group in the creation of NIST Interagency Report 7628 and currently plays key roles in the Advanced Security Acceleration Project for the Smart Grid (ASAP-SG), National Electric Sector Cybersecurity Organization Resources (NESCOR), and Smart Grid Interoperability Panel (SGIP). Justin has taught courses in hacking techniques, forensics, networking, and intrusion detection for multiple universities, corporations, and security conferences, and is currently an instructor for the SANS Institute. In addition to electric power industry conferences, Justin frequently presents at top security conferences such as Black Hat, DEFCON, OWASP, and AusCERT. Justin co-leads prominent open source projects including the Samurai Web Testing Framework, Middler, Yokoso!, and Laudanum. Justin has an MBA in International Technology and is a CISSP and SANS GIAC certified Incident Handler (GCIH), Intrusion Analyst (GCIA), and Web Application Penetration Tester (GWAPT).
Mikko Saario
Mikko Saario is a senior security manager at Nokia overseeing security for developing and operating key internet-based services. He drives the secure development practices, security testing and internal training efforts of the unit and in addition spends his ample free time to arrange OWASP Helsinki, Finland chapter activities, contributes to the SAFECode security guidance efforts and messes with technologies such as Windows Phone 8 and the Qt project.
Moshe Lerner
Moshe Lerner is VP of Product Strategy and Corporate Development at Checkmarx, a leading provider of a secure testing solutions using innovative source code analysis platforms.
Moshe has over 20 years of global experience in the software industry where he served in different executive and professional roles at leading companies. Prior to Checkmarx, Moshe held the position of VP of Product Management and Business Development at ItemField (acquired by Informatica) and before that, as VP of Product and Delivery at Sapiens (Nasdaq: SPNS).
Moshe holds B.S.C in Information systems from Israel’s Institute of Technology (Tecnion)
Shay Chen
Shay Chen is the CTO of Hacktics, an advanced security center of Ernst & Young.
As the co-author of the platforms ""Diviner"" and ""WAVSEP"", he was involved in the publication of several large-scale researches in the field of automated security scanners (including the latest 2012 comparison of 61 web application scanners).
After a decade of exposure to tons of common vulnerabilities, the law of familiarity caused his researches to revolve around abnormal hacking methodologies and new application-level attack vectors, usually the type that bypasses the known spectrum of security mechanisms.
He is also a prominent blogger and researcher, and is responsible for many security publications, including new application-level attacks, open source projects, testing methodologies and various security tools comparison initiatives.
Shay is an experienced speaker, and has been instructing a wide variety of information security courses for the past 7 years, including appearances in international conferences such as Hacktivity, ZeroNights, and AppSecUSA, as well as multiple appearances in various OWASP conferences.
He has over twelve years in information technology and security, including a strong background in software development.
Siddharth Anbalahan
Siddharth Anbalahan is a Senior Security Consultant and Head of the Secure Code Review and Mobile Application Security Testing Division at Paladion Networks Pvt. Ltd. He has a rich experience of over 6 years in IT security and an overall experience of 10 years in the IT industry. He has conducted many secure coding and application security trainings at various organizations across the globe and has been consulting organizations to build and practice a secure development lifecycle. He had co-presented at OWASP Australia 2009 “Advanced Code Review Techniques” and is also the Co-Author of the book “Application Security in the ISO 27001 Environment”. He has immensely contributed to the field of application security by writing blogs, security articles and secure coding guidelines for different platforms.
He recently conducted training on “Advanced Secure Code Review Techniques” at OWASP India 2012.
Shubham Mittal
Shubham Mittal is an active security researcher having keen interests in Penetration testing and Malware Analysis. Having expertise in Network and Web Application Security, he has actively contributed to many security research advisories like Exploit-DB, Packetstormsecurity, garage4hackers,. with his security based research papers. Also he has spoken in two National Level paper presentations and submitted a paper in an international journal too. Apart from this, he has discovered and reported flaws in many of the critical and prestigious websites and servers. He has performed Security Audits on many popular websites and web servers with complexity level up to hosting of 250 sites. He has given training to professionals from DRDO, CBI, Air force, IGI Technical Head, HCL technologies, Convergys, Adobe, Headstrong. He enjoys developing hacking tools, writing security articles, working on new techniques, attending professional meets, etc. meanwhile sharing his experience and skills with the Hackers community. Being an active member of Null - Open Information Security Community, he has been a regular speaker with his innovative ideas among the National Hackers.
Subho Halder
Subho Halder is a Programmer, Security Researcher and Penetration Tester. He loves writing exploits and programming in PHP, Java, Perl and Python. He is well equipped and has a deep understanding of Android and Blackberry frameworks, and currently working at Tata Consultancy Services.
Tobias Gondrom
Tobias Gondrom is Managing Director of an Information Security & Risk Management Advisory based in the United Kingdom, Germany and Hong Kong. He has fifteen years of experience in software development, application security, cryptography, electronic signatures and global standardisation organisations working for independent software vendors and large global corporations in the financial, technology and government sector, in America, EMEA and APAC. As the Global Head of the Security Team at Open Text (2005-2007) and before as the lead of the Security Task Force at a global Independent Software Vendor, he was responsible for information security, risk and incident management globally.
Since 2003 he is the chair of working groups of the IETF (www.ietf.org) in the security area, member of the IETF security directorate, and since 2010 chair of the web security WG at the IETF, and currently invited expert member at the W3C WebAppSec working group, board member of OWASP London and chair of the OWASP global industry committee. Tobias is a frequent CISO trainer, the author of international standards RFC 4998, RFC 6283 and co-author and contributor to a number of internet standards and papers on web and application security and electronic signatures, as well as the co-author of the OWASP CISO guide and the book „Secure Electronic Archiving“, and frequent presenter at conferences and publication of articles (e.g. AppSec, CISO Forum, IETF, ISSE, Moderner Staat, iX). He is also certified as CISSP, CSSLP and CCISO.
Tobias has post-graduate degrees in Theoretical Physics from the Technical University of Munich and the senior management M.Sc. from London Business School (Sloan Masters in Leadership and Strategy) with his thesis focusing on leading and managing global change programs.
Tony UcedaVelez "Tony UV"
An experienced security management professional, Tony has more than 14 years of hands-on information security and technology expertise across technical and operational areas. He has worked and consulted for numerous firms within the Fortune 500, as well as U.S federal agencies on the subjects of security risk management, application security, human hacking, and security architecture. He is the founder of VerSprite and consults across several different industries on a myriad of security topics using a hybrid style that encompasses both technical and process based security insights.
His diverse IT background in software development, security architecture, and network security, coupled with his expertise in process engineering and security risk management has allowed Tony to be a recognized leader in developing strategic security solutions that are multi-faceted in their approach to addressing enterprise risk. From both the commercial and government sectors, Tony has applied his expertise across multiple control frameworks (ITIL, NIST, ISO, CoBIT, COSO, etc) in order to help mature security programs built around both automated and manual control sets.
In the realm of application security, Tony is a threat modeling evangelist and has provided numerous talks domestically and globally on its many benefits and application. He has served as a guest mentor to teams participating in Kennesaw State University’s annual Cybercrime capture the flag event as well as a Cybercrime speaker for Southern Polytechnic University in Atlanta (2009). He has also served as a guest speaker on the subject of application threat modeling during ISACA’s annual Geek Week event and has also served as a keynote speaker on the subject for ISACA’s Global Symposium web cast series. Additional articles include articles related to CoBIT and the ValIT model (ISACA’s Journal), application threat modeling within the SDLC (InSecureMagazine), and security process engineering for a ROSI (return on security investment) (Journal of Finance).
Tony is also well regarded in the field of FISMA compliance, having worked with various federal entities and their respective certification & accreditation groups in order to manage compliance requirements against both NIST and FIPS requirements for ensuring data and system level security. NIST has invited Tony to speak twice at their annual SCAP conference in Baltimore on the subject of sustaining compliance across large federal information enterprises.
Prior to VerSprite, Tony served as Sr. Director of Security Risk Management to a Fortune 50 organization where he led security assessments against global application environments. His work encompassed web application security testing, security architecture reviews, and analysis for business logic exploits. He applied effective ways to introduce the subject of application risk to information owners by effectively mapping them to operational business components. Previous to this role, he spent more than 5 years in the field of application security across other Fortune 500 organizations within the banking, telecom, and information service industry segments.
Tony currently leads the OWASP Atlanta Chapter, where he manages monthly workshops and events for the Atlanta web application security community. He is also serves on the OWASP Global Membership Board and regularly provides talks to other chapters nationwide, primarily on the topic of application threat modeling. Aside from the OWASP organization, Tony has helped to organize BSides Atlanta – an underground grassroots effort aimed at providing 100%, unsolicited security content to Atlanta Information Security professionals.
Wong Onn Chee
Onn Chee is currently working as the Managing Director in Infotect Security and the Chief Technology Officer of Resolvo Systems. His areas of expertise include information leakage protection, web/cloud security and security strategy. Onn Chee is also one of the co-inventors for at least six international PCT patent rights (http://www.wipo.int), besides several US, EU and Singapore patents.
He had published his works in the area of information leakage protection and application of evidence laws when designing IT systems in the ISSA Journal (Information Systems Security Association). He is also a current active contributor to the Center of Internet Security (US) (http://www.cisecurity.org) security benchmarks.
Onn Chee is the current Singapore chapter lead of Open Web Application Security Project (OWASP) (http://www.owasp.org/) and the main organiser of the Security Meetup Group in Singapore.
In addition, he is the Cloud Security Working Group Chair of Security & Privacy Technical Committee under IT Standards Committee in Singapore. He is one of the contributors to Singapore first Technical Reference on public computing services, namely TR 31: 2012. He is also a member of the International Standardisation Council in Cloud Security Alliance (CSA).
Other than being a information security professional, Onn Chee is also trained in BS 7799/ISO 17799, ISO 9000 and ITIL. He is a certified PRINCE2 Practitioner and was a former certified Project Management Professional (PMP).
In 2007, Onn Chee was appointed as the President of International Association of Software Architect (IASA), Singapore Chapter. In 2010, Onn Chee was selected as one of the honorees for ISC2's Asia Pacific Information Security Leadership Achievements - Senior Information Security Professional Category.
His work on the HTTP POST Layer 7 DDOS was voted by his peers around the world to be the top 7 technique in the Top 10 Web Hacking Techniques of 2010 (http://jeremiahgrossman.blogspot.com/2011/01/top-ten-web-hacking-techniques-of-2010.html).
송인혁(SONG IHN-HYUK)
He has 6 years of experience in Information-security party with various institutions, for example, military's security, public institutions' security, financial-security and private companies' security. On the technology side, it's possible to do troubleshoot via strong skills; solved many complex technical problems. Through accident analysis he looks for a solution. Furthermore it's excellent to make a precautions. Recently he is a studying convergence-security and researching a physical-security solutions.
주한익(Han-Ik Joo)
Han-Ik Joo is a team leader in security team of Coresecurity Inc. and a Korean certified instructor who has taught about certification course in EC-Council. He likes to be consistently researching about malware analysis and vulnerability of software, web application and computer systems. He has a variety of experiences of lectures and conference on many companies and government agencies like SATTI (Samsung Advanced Technology Training Institute), Cyber Terror Response Center, army, navy and air force, Cyber Command, Defense Security Command and ETRI(Electronics Telecommunications Research institute).
Abusing, Exploiting and Pwning with Firefox Add-ons
Ajin Abraham (Download the Presentation)
The talk is about abusing and exploiting Firefox add-on Security model and explains how JavaScript functions, XPCOM and XPConnect interfaces, technologies like CORS and WebSocket, Session storing and full privilege execution can be abused by a hacker for malicious purposes. The widely popular browser add-ons can be targeted by hackers to implement new malicious attack vectors resulting in confidential data theft and full system compromise. This paper is supported by proof of concept add-ons which abuse and exploits the add-on coding in Firefox 17, the release which Mozilla boasts to have a more secure architecture against malicious plugins and add-ons. The proof of concept includes the implementation of a Local keylogger, a Remote keylogger, stealing Linux password files, spawning a Reverse Shell, stealing the authenticated Firefox session data, and Remote DDoS attack. All of these attack vectors are fully undetectable against anti-virus solutions and can bypass protection mechanisms.
A Call for Drastic Action: A Survey of Web Application Firewalls
Jaeson Yoo (Download the Presentation)
Web application firewalls (WAFs) have become an unquestioned necessity in the modern world.
According to Gartner, 75% of all IT threats target the web application layer. The Ponemon Institute announced earlier this year that 93% of organizations hacked in the past two years were breached via insecure web applications. These are astounding figures, illustrating the vulnerability of web servers, through which we conduct so much of our daily business, as well as the significance of WAFs in addressing this vulnerability.
So why have so many businesses been reluctant to install WAFs? After all, they were designed specifically to deal with web application attacks. WAFs have been proven to block web attacks, and in some cases, provide effective countermeasures against them.
By taking a closer look at first- and second-generation web application firewalls, it seems to me that we can begin to find answers to this question. Until now, WAFs have been undermined by modified attacks, false positives, and an inordinate amount of burden to those who are entrusted to manage them.
First generation WAFs were based on a pattern-matching scheme, and brought about the advent of the Black List. The IT security administration would add a known attack pattern, and compile similar patterns to form the Black List. In so doing, the first-generation WAF could compare web traffic to its updated patterns, analyzing them at the application level. This list was static, meaning that there was no detection system put into place for new or modified attacks against the web application layer.
The first generation WAFs were not particular successful in the IT security market. Perhaps most companies wanted to stick with their Intrusion Detection/Prevention Systems, ignoring the fact that these components did painfully little for the OSI Layer 7, or the web application layer. Perhaps companies wanted to actualize a return-on-investment on their legacy purchases.
But this does not mean that the first generation WAFs themselves didn’t have something to do with their disappointing sales. First, the heavy workload was a drawback. Administrators constantly had to update known attack patterns on the black list. This meant many hours for the WAF administration team, assuming that the end-user even had such a team. More often, it meant having to hire more people, an especially unattractive prospect for smaller, cash-strapped organizations. In other words, not only did you have to invest in WAFs, you also had to invest in an expensive, highly-trained IT staff to run them.
If first-generation WAFs provided top-notch security, perhaps the additional investments could have been digested. But WAFs did not protect against new or modified attacks. They also produced a significant number of false positives. Most significantly, all this work for marginal security also resulted in poor performance. If you put more than 3,000 signature-based rules, system performance begins to slow. More than 5,000 signatures means that you may have to delete some old rules, just to make rooms for new ones.
In light of these limitations, WAF providers came up with a second-generation solution to address some of these problems. Second-generation WAFs came with a white list, or a list that includes all permissible traffic. By using the white list along with the black list, these updated WAFs were supposed to make things easier for the WAF administrator, since the white list would essentially serve as an automated security policy.
Unfortunately, second-generation WAFs did little to alleviate manpower requirements. In fact, these updated WAFs resulted in a heavier workload for the administrator. The white list would take up to two weeks to implement. Also, in spite of the fact that these automated security policies were supposed to make things easier for the administrator, second-generation WAFs still needed manual configuration. All of this meant more work, not less.
Again, if all this meant greater web security, perhaps all of these problems could have been overlooked. But this wasn’t the case. It was still a pattern-matching solution, meaning that it was vulnerable to unknown or modified attacks. It still produced false positives at a significant rate. And with the white list, it now worsened the system performance problem.
WAFs were and are definitely necessary. But these first- and second-generation solutions were coming up significantly short. More importantly, hackers were becoming increasingly sophisticated with every new day. So what was needed?
A whole new breed of WAF, an intelligent WAF, based on an entirely new concept, is needed. This new breed should be capable of analyzing web traffic, and detect attacks by analyzing and classifying their modus operandi. After detecting attacks, WAFs needed to apply appropriate countermeasures to block the threat. And finally, for practically purposes (especially for smaller companies that can’t hire a whole brigade of security administrators), WAFs needed to do all this without continual administrative involvement. In other words, a new solution was needed to provide much better security, while lessening the administrative burden for customers.
Design Secure Web Applications
Ashish Rao (Download the Presentation)
Checklist for securing web application design
We are all aware of “secure coding” and practice it to great extent while developing applications. But do we give equal attention to – “Secure Design”? Most of us would probably say, NO. Design level flaws are lesser known concepts but their presence is a very big risk to the applications. Such flaws are hard to find in static or dynamic application scans and instead require deep understanding of application architecture and layout to uncover them manually. With increasing business needs the complexities in application design and architecture are also increasing. There is a rise in the use of custom design techniques and diverse technologies in the applications today. But in the midst of all this, have we ever thought about design level security?
Will only secure coding practices help to keep a multi-tiered custom designed application safe?
If that question gets you thinking this presentation will help fetch you an answer for it.
This presentation focuses on highlighting some important secure design principles that developers and architects must adapt to build a secure application design. With the help of some design flaws we will see the areas of design that are exposed to security risks and what measures can be taken to avoid them in our design.
Dissecting Smart Meters
Justin Searle (Download the Presentation)
The Smart Grid brings greater benefits for electric utilities and customer alike, however these benefits come at a cost from a security perspective. This presentation will explore the architecture of most Smart Meters, the protocols they use, a breakdown of their embedded components, and the functionality their headend servers contain. We'll explain the methodologies we've developed to perform penetration testing these AMI systems, enumerate the types of vulnerabilities we commonly find, and discuss the solutions we recommend to Smart Meter vendors. We will even demonstrate at least one of the attacks we commonly perform in our penetration tests. This will be done without the FUD and over-hyped framing that we usually find in the media and other Smart Grid presentations.
The Droid Exploitation Saga
Aditya Gupta & Subho Halder (Download the Presentation)
In this talk, we will be discussing about the recent trends in Android Security Exploitation, as well as we will be carrying out all the possible attacks using a framework which we've designed called as Android Framework for Exploitation.
We will show how easy it could get to break into any Android Device, either using any exploit, or creating a malware using AFE. Also, in case the malware gets detected by any of the anti malwares, you 'll have the option to make it Fully Undetectable again and again, using the framework.
The things you would be able to steal with the help of AFE-created malwares, aren't limited to Contacts, Call Logs or Text messages, but you could also steal the application specific information (contained within the database files or saved using Content Providers).
We will be covering each topic with live demonstrations and will also discuss the case studies of vulnerabilities in some of the most popular android applications.
Growing sophistication of DDoS attacks
John Ellis (Download the Presentation)
2012 saw the unprecedented growth in DDoS attacks, not only in volume but also in sophistication.
Gone are the days where DDoS attacks were the simple cheap and nasty, simplistic syn floods. Now they have evolved into a powerful cyber weapon, a weapon of choice for: cyber extortion, aiding cyber criminals in their fraud activities, and hacktivists in pushing their cause.
Join John Ellis as he takes a deep dive into the growing sophistication of DDoS attack and examines:latest tools like 'itsoknoproblembro'the migration from the botnet to the Virtual Private Systems (VPS) as the attack platform of choice evolving C2 architecture the use of multi-vector attacks and the increasing attacks against and over SSL common approaches to defending against these attacks, whats worked and what hasn't what organisations should be thinking about next; and ideas on how to build a protect and perform strategy along with the message to senior management to secure funding.
Hacking Authentication Checks in Web Applications
Siddharth Anbalahan (Download the Presentation)
Authentication is one of the most coveted and targeted features for security attacks. Despite its importance and sensitivity we still fail to see robust implementations of this control in our applications. Developers just don’t seem to get it right and security researchers just cannot stop identifying flaws in them. In this talk we will look at 4 insecure authentication control implementation in web applications that will leave you astounded and make you understand why most of the applications will be prone to these flaws.
HTML 5
Han-Ik Joo (Download the Presentation)
HTML5 unlike the predecessors HTML that was impossible to implement features is the next generation standard language. However, vulnerability also is extended, and the fact that it is now possible to bypass existing countermeasures for Web-based security threats. In this talk, We will handle Demonstrations and the presentation of the security threats that can occur in the browser with the newly added features in HTML5. This talk include the following information as below:
- CSRF Using XHR Level2
- XSS using Newly added tag in HTML5
- Web Storage using information extraction
- WebSQL Information extraction using JavaScript
- Web Worker Injection
Invisibility Purge – Unmasking the Dormant Events of Invisible Web Controls – Advanced Hacking Methods for Asp.Net, Mono and RIA
Shay Chen (Download the Presentation)
Web Controls have become common in many popular platforms, enhancing the software lifecycle by speeding up development, and enabling developers to reuse custom content.
In platforms such as ASP.Net and Mono, the implementations of Web controls are packed with features that can enhance the security of applications, usually with minimum effort.
There are many ways to restrict the access to web controls, including privilege validation, deletion from pages that were duplicated for low privileged users, disabling controls, or even by making them invisible to anyone but users with pre-defined roles.
However, the event activation mechanism can also be a double-edged sword.
Invisibility, by definition, is in the eyes of the observer.
An object might be invisible to some eyes, while still being visible to instruments that were designed to locate it.
A new research reveals several methods that attackers can harness to unmask, enumerate and activate events of hidden web controls, even in popular platforms such as ASP.Net and Mono.
The slightest mistake or the right conditions can make this development model a fertile ground for attacks, enabling the attacker to completely ignore the security features of controls, and gain access to restricted and dormant server side events.
Locating invisible controls, Unmasking hidden events and activating them in-spite of various default and custom security measures – once only in theory, and now a step by step methodology that could be performed manually, or using designated tools.
This presentation will demonstrate several methods that can be used to locate invisible web controls, unmask secret events and activate dormant code. It will also discuss designated modules which are embedded into the upcoming release of the Diviner extension, an extension of the OWASP ZAP proxy project.
Missile of Cyber-terrorism, the reality of APT and Countermeasures
Security Expert, Growing (Download the Presentation)
APT’s attack is represented intelligented and sophisticated Hacking. As a result APT can be used to disturb the tackets. Here, this paper proposed to understand the reality of APT. In other words, APT’s definitions, properties, and Life-Cycle. Depending on derived properties, Security defense strategy is suggested differently.
Open Source Metasploit - The Elixir of Network Security
Harish Chowdhary and Shubham Mittal
Talk Cancelled
Today every organization intensely relies on the communication. Every part of an organization ought to operate closely & ought to be interconnected for the benefit of the organization. The term interconnected & communication signifies one of the most vital a part of an organization primarily of an IT organization is the Computer NETWORK. Network is the backbone of an IT organizations Network security is a crucial concern for enterprises, government agencies, and organizations of all sizes. Today’s advanced threats demand an organized approach to network security. Information within a network has same importance like blood in our veins. But the increasing incidence of the network breaches leading to the critical information loss, finally loss of business & credibility, clearly indicates that computers networks are not secured as they seem. Therefore they must be tested for their security. The aim of this paper is to present the most effective open-source Framework for network security testing-METASPLOIT. This paper will provide the focused views on.
What is Metaspliot, how to use Metasploit for Penetration testing & its various advantages, how to customize you pen test. It will additionally also put lights on, how to find the intrusion in the network & mitigation techniques to keep away from the cyber assaults. Whole, the objective of this paper is to provide a detailed understanding of what is Metasploit and how to utilize it as a security professional.
Pentesting Web Apps with Python
Justin Searle (Download the Presentation)
Interested in expanding your scripting skills to further customize your penetration testing approach? The goal of this talk is to teach you basic python skills you can use every day. Join one of the SamuraiWTF project leads and learn how to interact with websites using
python scripts and python shells. Understand the differences between the major HTTP libraries like httplib and urllib2. Walk through sample code that performs username harvesting and dictionary attacks. Learn how to use Python's multithreaded features to speed up your scripts. And most importantly, discover PyCIT, a new opensource
project that provides simple, documented, and functional python templates to accelerate your python scripting efforts.
Putting Security within the SDLC via Application Threat Modeling
Tony UV (Download the Presentation)
As delusions of effective risk management for application environments continue to spread, companies continue to bleed large amounts of security spending without truly knowing if the amount is warranted, effective, or even elevating security at all. In parallel, hybrid, thought provoking security strategies are moving beyond conceptual ideas to practical applications within ripe environments. Application Threat Modeling is one of those areas where, beyond the hype, provides practical and sensible security strategy that leverages already existing security efforts for an improved threat model of what is lurking in the shadows.
This presentation seeks to walk though practical applications and exercises associated with application threat modeling. Integration to multi-security focused disciplines will be included, such as dynamic analysis, static analysis, incident monitoring, vulnerability management, social engineering, penetration testing, and more.
The objective of the presentation is to illustrate the efficiency and effectiveness of application threat modeling in properly integrating and leveraging security information in order to evolve beyond a broken risk analysis model for application security today. The PASTA (Process for Attack Simulation & Threat Analysis) methodology will be introduced as part of this talk.
The target audience will encompass motley of both IS and IT professional, ideally providing a cross section of developers, project managers, system administrators, quality assurance engineers, security analysts, pen testers, network engineers, security risk analysts, and even compliance professionals. Due to the level of depth to be covered in the presentation which will go over Data Flow Diagramming, Application Decomposition exercises, correlation to existing frameworks such as Building Security-In Maturity Modeling, Software Assurance Maturity Modeling, and more.
Securing data with a Data Encryption Infrastructure
Arshad Noor (Download the Presentation)
As companies are challenged to keep up with an increasing number of data-security regulations worldwide, encryption of sensitive data has become the universal ""safe-harbor"", the last bastion of defense against unauthorized disclosure of data, mandated or highly recommended in every regulation.
While the protection of structured data-elements such as Credit Card Numbers, Bank Account numbers, etc., is addressed by applications on a case-by-case basis, we are entering an era where unstructured sensitive data are becoming equally attractive targets. Military documents, medical data, blueprints of new products, financial and legal documents, etc. are just as valuable as credit card numbers to attackers depending on their motiviation and backers.
While it is feasible for companies to address the protection of such documents on a case-by-case basis, it is far more effective to deploy a ubiquitous network service that addresses all of the following requirements:
- Provide a single point/protocol for commuication to the service (much like DNS or DHCP);
- Is accessible to any platform or programming environment;
- Provides automated scheduling of cryptographic operations (synchronous and asynchronous);
- Provides automated key-management (generation, escrow, recovery, etc.);
- Auto-scales cryptographic capability to address peaks/valleys of processing loads;
- Integrates with existing Identity and Access Management (IAM) infrastructure;
- Integrates with existing public/private Cloud services;
- Provides load-balancing and is highly-available; and
- Meets regulatory requirements of any data-security regulation anywhere.
While sounding more like a pipe-dream, this paper presents a case-study of a real-world implementation of such a network service to protect structured and unstructured content worth hundreds of millions of dollars, for one of the largest e-commerce companies in the world.
The Regulatory Compliant Cloud Computing (RC3) - a web-application architecture for secure cloud-computing - was presented at OWASP AppSec APAC 2012 in Sydney by this author, where it was fairly well received (to the best of my knowledge). RC3 is gaining attention worldwide, with IBM having translated the paper into Chinese, Portuguese and Russian for the BRIC markets on its developerWorks web-site (http://ibm.co/rc3dw), and the paper presented at various other conferences around the world (after AppSec APAC 2012).
This paper continues the discussion to present, for the first time, a real-world RC3 implementation, and discusses how the experience can be leveraged by others to address data-protection requirements. It will include details of the architecture, technology components (FOSS), and performance data to support the tenets described in the original RC3 paper from 2012.
Security Challenges of Hybrid Mobile Applications
Mikko Saario (Download the Presentation)
Mobile application development leveraging a hybrid technology stack is an accelerated way to bring new apps to market reusing existing competencies. Hybrid technology essentially refers to using several different coding languages instead of just the ""native"" one - whatever it may be in each case. Often existing code and services are reused to avoid expensive development for each distinctive platform. This way the ‘desktop web’ and the ‘mobile web’ are converging quickly - code can be shared and reused more and more. The focus technologies in this presentation are Windows Phone 8 and the Qt framework. Mikko will take a look into what kind of fundamental security mechanisms or threats do or do not exist in the two platforms to protect the user and the application from attacks when mixing several technology stacks. The expanding availability of development technologies opens up new attack surface, often with old attacks, to mobile applications: For instance, Windows Phone 8 introduced the possibility to implement applications in C++ in addition to the existing C#/Silverlight + web technologies. Are buffer overflows back? Qt is built on top of C++ and implements for instance the WebKit and QtQuick (QML with inline JavaScript) technologies for quickly developing cross-platform applications. The combination of these multiple stacks provide ample attack surface against mobile applications.
The presentation will cover security pitfalls when mixing native code and JavaScript in the Qt/QML stack, Qt-specific XSS and other injection issues, deploying code in webviews in both platforms - and the lack of common user security indicators in them, how malicious code can identify native methods exposed to a hybrid environment, how the same origin policy and code sandboxing differ from the typical desktop browser, how to leak your geolocation in Windows Phone, surprising differences in using a headless browser vs. IE Mobile in the older Windows Phone 7.5 and much more. Using a live demo application I will walk through several hybrid platform issues and threats in Windows Phone 8.
During the testing vulnerabilities were discovered in both the WP8 and Qt platforms and these will be demoed in cases where the vendor has either fixed the issue or the information is otherwise already public.
Using the Wisdom of the Crowd to Enhance Application Security
Moshe Lerner (Download the Presentation)
Security-oriented source code analysis tools detect vulnerabilities only for well-defined hacks and tend to return many results which are hard to remediate. Two problems result: One, how can we overcome the lack of coverage? And two, how can we improve the ability to fix?
These problems are all the more pressing considering today’s short development cycles through Agile methodologies, the ever-increasing requirement for continuous deployment and large applications containing vast amounts of source code. In these environments, automation and accuracy are absolute necessities in order to achieve high rates of vulnerability detection and furthermore, taking the right preventive actions.
To address these challenges our research turned to the field of Big Data analysis to integrate their advanced technologies into our research. In this talk we present our research methodology and findings. In particular, we show how to:
- Adopt new technologies from the Big Data realm - used to locate required data and enable proper call for action – and apply them into source code analysis
- Identify security vulnerabilities through code irregularities using the Wisdom of the Crowds (large scale apps reference)
- Optimize vulnerability remediation of large result sets using smart graph methods that pinpoint vulnerability junctions and best-fix locations
Web Security - New Browser Security Technologies
Tobias Gondrom (Download the Presentation)
This is cutting edge and will talk about new browser security technologies that have recently been developed and/or will be coming up in the coming months to counter risks that became apparent from the current trust model used in browsers. This will be improving channel protection and enabling better protection against XSS, Clickjacking and XSRF.
In the recent months global standard developing bodies and the browser vendors have in a joined effort developed and implemented many new major security capabilities in the browsers allowing web application developers to counter common security problems with comprehensive new mechanisms. This talk will be talking about:
- Channel protection: Securing SSL against Man-in-the-middle-attacks: New technologies - HTTP Strict Transport Security and and Pinning of Certs
- Protection against XSS and clickjacking: the future of X-Frame-Options and the Content Security Policy
The presented technologies are cutting edge and although some parts of the specifications are not final yet, they will be rolled-out in about 6 months time.
What your CISO has not told you - Outbound security of cloud and enterprise web services
Wong Onn Chee (Download the Presentation)
This presentation will cover an important topic which no CISO ever mentions. Cloud and enterprise e-services are accessible 24x7 by anyone across the world, especially via mobile devices. Yet, efforts for past decades have sorely neglected the outbound risks of enterprise e-services and, in recent years, cloud and mobile services. Without outbound protection, incidents such as leaking private data, infecting visitors with malware and displaying defaced web pages are often reported by the press, damaging reputation and customer confidence. With tighter data privacy laws, many organisations are risking hefty legal penalties if they continue to neglect this risk area.
This talk will highlight the growing trend of web sites being used to leak information, transmit malware and display defaced content. The speaker will walk through a number of case studies and share with the audience on the lessons learnt from each case study. The speaker will also explain how the lack of outbound security protection contributed to the realized risk in each case study.
OWASP Project Track Talks
OWASP AppSensor the future of Application Security
Dennis Groves (Download the Presentation)
The OWASP AppSensor is commonly described as an application layer intrusion detection system. However, it is far more that this. It is also an architecture design pattern, as well as a development practice and an operations methodology. I propose the following outline for my talk:
- (describe) I will describe what OWASP AppSenor is and why you would want one.
- (design) I will give a brief talk about the principles of secure architecture and design.
- I will give a brief history of IDS and NIDS, their strengths and weaknesses.
- I will then discuss how how and where AppSensor fits into that history, and how it improves upon the past for example:
- (development) The concept in implementation is roughly analogous to an intrusion detection (and prevention) system in the network security world. However, this concept can be applied inside of an application in a more specific way that (importantly) reduces false positives, which is an issue that often plagues network intrusion detection systems. This means that the core of the AppSensor system performs detection, monitoring, and (possibly) response depending on configuration settings.
- (deployment) I will the discuss deployment and operation of AppSensor.
- I will then describe why I believe this is the most important development in application security, and why everbody will develop software this way by the end of the decade.
- I will then propose future developments and enhancements for the OWASP AppSensor
Using ESAPI for Java to Build Secure Web Applications
Jim Manico (Download the Presentation)
We cannot “firewall” or “patch” our way to secure websites. In the past, security professionals thought firewalls, Secure Sockets Layer (SSL), patching, and privacy policies were enough. Today, however, these methods are outdated and ineffective, as attacks on prominent, well-protected websites are occurring every day. Organizations around the world rely on web security services to maintain the safety of their websites in today’s hostile online environment. Website developers must also learn to code in a secure fashion to have any chance of providing organizations with proper defenses in the current threat-scape. The session will provide specific tips and guidelines to make website code both low risk and less vulnerable using the OWASP ESAPI for Java project.
AppSec APAC 2013 will be held at the Hyatt Regency in Jeju, South Korea.
The conference training and talk will be held in the Regency Ballroom and Terrace Ballroom. Exhibitor booths will be set up in the foyer outside the ballrooms on Thursday and Friday.
Conference Registration is now open! Click Here to Register.
OWASP AppSec Asia Pacific features two days of training February 19-20, and two days of talks, February 21-22, 2013
Please note - all prices below appear in USD; however arrangements can be made for payment in South Korean Won.
Conference Registration Fees (not including training)
| Ticket Type |
Early (until January 18) | Regular Price |
| Non-Member | $295 USD | $395 USD |
| Non-Member plus 1-year OWASP Membership! | $295 USD | $395 USD |
| Active OWASP Member | $275 USD | $375 USD |
| Student | $75 USD | $100 USD |
| Training Only | (See pricing table below) | |
Training Fees
| Course Length |
Course Date(s) |
Price |
| 1-Day Class | Wednesday, Feb 20 | $400 USD |
| 2-Day Class | Tuesday and Wednesday, Feb 19-20 | $800 USD |
Price per attendee. Please note that conference Registration is separate.
For more information on available training courses and trainer bios, please select the "Trainers and Training Schedule" tab.
Optional Conference Events
| Item |
Date & Time |
Price |
| 1/2 Day Developer Workshop | Wednesday, Feb 20, 1-5pm | Complimentary |
| Chapter Leader Workshop | Wednesday, Feb 20, 6:30-9:30pm | Complimentary |
| Conference Networking Dinner | Thursday, Feb 21, 7-9pm | $50 USD |
Sign up for any of these optional items by registering for the conference.
Group Discounts
10% off for groups of 10-19 20% off for groups of 20-29 30% off for groups of 30 or more
Please Contact Us for more information about registering a group.
Membership Discounts
We are pleased to offer $20 off admission for active OWASP members. Multiple discounts can not be applied.
Registration for Trainers and Speakers
If you have been selected to deliver a training or talk at the conference, you should have received a discount code for complimentary admission.
If you did not receive this code or have questions, please Contact Us.
Registration for OWASP Leaders
Complimentary admission to the conference is offered to active OWASP Chapter and Project Leaders. Additionally, two seats for each of the training courses are available at no cost to active OWASP Chapter and Project Leaders (available on a first come, first serve basis). To register as an active Chapter or Project leader, please select the general event registration option and enter discount code: OWASPLEADER.
Please note: conference and training registration using the OWASPLEADER discount code will be verified by the conference team and if you are not an active OWASP Chapter or Project Leader, you will be contacted regarding your status and your registration may be subject to cancellation.
We are looking for sponsors for 2013 edition of Global AppSec APAC.
If you are interested to sponsor Global AppSec APAC 2013, please contact the conference team: [email protected]
Sponsorship Deadline is January 15, 2013.
To find out more about the different sponsorship opportunities please check the document below:
OWASP AppSec APAC 2013 Sponsorship Options - English
OWASP AppSec APAC 2013 Sponsorship Options - Korean
Conference Exhibitor Information Pack
For assistance with booking a flight or hotel, feel free to utilize OWASP's preferred travel agency:
Segale Travel Service contact information is: +1-800-841-2276
Sr. Travel Consultants:
Maria Martinez...ext 524
Linn Vander Molen...ext 520
Additionally, the Conference Planning Team is available to answer any questions!
Accommodation
We've been able to arrange for special rates at the Hyatt Regency Jeju(where the training and conference will be held).
The special room rates are available two nights either side of the event ensuring that if you are travelling domestic or international it's easy to find a room at a good rate.
Hyatt Regency Jeju
114, Jungmungwangwang-ro 72 beon-gil, Seogwipo-si
Jeju Special Self-Governing Province
South Korea 697-130
Tel: +82 64 733 1234 Fax: +82 64 732 2039
Email: [email protected]
Hotel Regency Information Sheet
To book a room at the special rate: *Add the room to your online conference registration or *Complete the Hotel Booking Form and fax or email to the address on the form.
Please notice that if you add the room to your conference registration, the rates are in USD and include all service fees and taxes.
Airport Transportation
Jeju International Airport is approximately 40 minutes by car from the Hyatt Regency. Hotel Map & Directions
Arrival by Airport Limousine Bus (Recommended)
The Airport Limousine Bus (Bus No.600) will be waiting at the Airport exit at all times during its operating hours of 6:20 am to 10:10 pm. The bus will leave the airport at 15 minute intervals, and will take around 50 minutes to reach the hotel’s main entrance. The price is KW 3,900 per person (less than $4 USD).
Arrival by private car
- Exit Jeju International Airport and enter Jungmun Highway.
- Follow the signs to Jungmun.
- Make a right from the junction where the wind power plant can be seen on the right.
- Go straight ahead to find the sign for the hotel.
- Follow the road indicated by the sign for Hyatt Regency Jeju.
Arrival by rental car
- Press the navigation code ‘4327’ for the rental car.
- Input the address: 3039-1 Saekdal-Dong Seogwipo-Si, Jeju Island.
- Input the telephone number: 064-733-1234.
Parking at the Hyatt Regency Jeju
Hyatt Regency Jeju offers the outdoor parking on hotel premises available to hotel guests at no charge.
Complimentary valet parking is also available on request. The hotel’s parking area is accessible 24 hours a day.
Information +82 64 735 8495
We will be hosting a networking dinner with Korean-style food and beverages on Thursday evening, February 21 from 7:00pm to 9:00 pm at the Hyatt Regency Jeju.
The cost of this dinner is approximately 53,000 KRW ($50 USD) and can be added to your online conference registration.
About the Workshop
When: Wednesday evening, February 20th, from 6:30 to 9:30 pm
Where: Hyatt Regency Jeju.
The Global Chapter Committee invites all chapter leaders to participate in the upcoming Chapter Leader Workshops at AppSec APAC 2013.
The Chapter Leader Workshop format will continue to follow the Q & A format used during AppSec USA and AppSec LATAM. Questions and discussion will focus on sections of the Chapter Leader Handbook, OWASP Global Chapter resources, and local chapter challenges.
Dinner will be provided for workshop participants.
Register for the Workshop
To confirm your participation in the event, register for the conference and be sure to select "Chapter Leader Workshop" as an optional registration item.
Chapter Leader Sponsorships
IMPORTANT DEADLINES
- January 7, 2013 - Appsec APAC Chapters Workshop sponsorships applications due
- January 14 - Applicants notified of status
- If you need financial assistance* to attend the Chapter Leader Workshops please contact us by the application deadline.
- Priority of sponsorships will be given to those not covered by sponsorship to attend a previous workshop. Additionally, we are looking for new or struggling chapter leaders who need assistance kick starting their chapter.
- When you apply for funding, please let us know *why we should sponsor you*. While we prefer that chapter leaders use their own chapter's funds before requesting a sponsorship, this is not a requirement for application.
- If your chapter has fund but will not be using them to sponsor your attendance, please include why you will not be using the funds for this purpose (i.e. what are the other plans for those funds?).
Questions
If any questions, please contact us
2013 AppSec APAC Conference Volunteer Team
Do you want to volunteer for AppSec APAC 2013? [Click here to sign up]
OWASP Staff Support
- Laura Grau
- Kelly Santalucia
- Kate Hartmann
Contact us at [email protected]