This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Lonestar Application Security Conference 2011"
m (category changed to OWASP Chapter/Events) |
|||
| (16 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
__NOTOC__ | __NOTOC__ | ||
| − | [[Image: | + | [[Image:Lascon800x191.png|800px]] |
===== Click [http://www.owasp.org/index.php/Lonestar_Application_Security_Conference_2010 here] for information on LASCON 2010. ===== | ===== Click [http://www.owasp.org/index.php/Lonestar_Application_Security_Conference_2010 here] for information on LASCON 2010. ===== | ||
| Line 90: | Line 90: | ||
<br> For student discount, you must present proof of current enrollment when picking up your badge. No exceptions. | <br> For student discount, you must present proof of current enrollment when picking up your badge. No exceptions. | ||
| + | |||
| + | ==== Training ==== | ||
| + | |||
| + | We are pleased to announce that this year we will be adding on two different training classes the day before the Lonestar Application Security Conference (LASCON) on '''Thursday, October 27, 2011'''. These training classes are unlike those you see at most conferences both in content and cost. If you have already registered for LASCON, simply go to http://www.regonline.com/lascon2011 and select the "Already Registered?" link. Log in with the e-mail address you registered with and then select to edit your "Agenda". Place a check mark in the box for the training you would like to attend (or the FREE happy hour) and select "Continue" to check out. If you have not already registered for LASCON, you will have the ability to add the training of your choice on the "Agenda" screen of registration. The trainings are as follows:<br> | ||
| + | |||
| + | '''<u>TRAINING 1 ($250):</u>'''<br> | ||
| + | '''Title: Advanced Threat Tactics with Armitage and Metasploit'''<br> | ||
| + | |||
| + | Metasploit is a powerful exploit framework and a must-have tool for penetration testers. Armitage builds a workflow on top of the Metasploit framework and exposes its most advanced capabilities. This demonstration and lab oriented session will teach you Metasploit and Armitage for the purpose of emulating adversary tactics. This course will start with the basics and quickly take you into the workflow of modern threats. You'll learn how to create trojan files, manage covert HTTP and HTTPS communications, set up social engineering attacks, and use pivoting to take over a network.<br> | ||
| + | |||
| + | To participate in the labs, you must have VMWare Player, VMWare Fusion, or VMWare Workstation installed.<br> | ||
| + | |||
| + | Raphael has put up some additional information on this class on his website at http://www.fastandeasyhacking.com/threats.<br> | ||
| + | |||
| + | '''Biography:'''<br> | ||
| + | Raphael Mudge is a Washington, DC, based code hacker working on a new startup effort. He is the developer of the open source Armitage for Metasploit. Raphael regularly writes and speaks on security topics. His work has appeared in USENIX ;login:, Linux Journal, and Hakin9. Previously, Raphael worked as a security researcher, software engineer, penetration tester, and system administrator.<br> | ||
| + | |||
| + | '''<u>TRAINING 2 ($250):</u>'''<br> | ||
| + | '''Title: Bootstrapping Your Application Security Program'''<br> | ||
| + | |||
| + | This training class is for new managers & leads accountable for integrating Application Security into their enterprise. The course will walk through various success factors, including a mixture of strategy, policy, and technology considerations. The course will help attendees develop incremental plans they can employ to make both short-term and long-term measurable improvements to their enterprise Application Security.<br> | ||
| + | |||
| + | Topics that will be covered include:<br> | ||
| + | *Goal Setting | ||
| + | *Running effective pilot programs | ||
| + | *Working with vendors | ||
| + | *Roles & responsibilities in application security | ||
| + | *Getting buy-in from management, development, business, IT, etc. | ||
| + | *Meeting compliance needs (PCI & others) | ||
| + | *Measuring success & ROI | ||
| + | *Reporting to management | ||
| + | *Scaling your program | ||
| + | |||
| + | '''Biography:'''<br> | ||
| + | Bankim Tejani specializes in helping large companies stand up application security programs. Currently a Managing Consultant ofat Fortify, An HP Company, Bankim works with leading financials, technology companies, government agencies, and other corporations. He helps them strategically inject application security processes and technologies into their SDLCs while trying to minimize impact on time to market and maximize ROI. His prior experience begins with software development and transitions to network security research, red teaming, information security research, and application security consulting & training.<br> | ||
| + | |||
| + | Seats in these trainings will be very limited and registrants will be accepted on a first-come, first-served basis. Sign up today! | ||
==== Sessions ==== | ==== Sessions ==== | ||
| − | + | See http://lascon.org/ | |
==== Volunteers ==== | ==== Volunteers ==== | ||
| Line 128: | Line 165: | ||
{| | {| | ||
|- | |- | ||
| − | | [[Image:Impactsecurityllc.png|150px|link=http://www.impactsecurityllc.net]]<br>'''Impact Security LLC''' | + | | [[Image:Impactsecurityllc.png|150px|link=http://www.impactsecurityllc.net]] |
| + | <br>'''Impact Security LLC''' | ||
| [[Image:IBM.png|150px|link=http://www.ibm.com]] | | [[Image:IBM.png|150px|link=http://www.ibm.com]] | ||
| + | | [[Image:Imperva_2color_RGB.jpg|250px|link=http://www.imperva.com]] | ||
| + | | [[Image:Whitehat.gif|250px|link=http://www.whitehatsec.com]] | ||
|- | |- | ||
| | | | ||
| Line 136: | Line 176: | ||
{| | {| | ||
|- | |- | ||
| − | | [[Image:Gemalto.jpg|185px|link=http://www.gemalto.com]] | + | | [[Image:Gemalto.jpg|185px|link=http://www.gemalto.com]] |
| − | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] | + | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] |
| − | | [[Image:radware.png|150px|link=http://www.radware.com]] | + | | [[Image:radware.png|150px|link=http://www.radware.com]] |
| + | | [[Image:Cigital.png|150px|link=http://www.cigital.com]] | ||
|- | |- | ||
| − | | [[Image: | + | | [[Image:Atsec.png|150px|link=http://www.atsec.com]] |
| − | | [[Image: | + | | [[Image:Fireeye.png|150px|link=http://www.fireeye.com]] |
| − | | [[Image: | + | | [[Image:Symplified.png|150px|link=http://www.symplified.com]] |
| + | | | ||
|} | |} | ||
== Lanyard Sponsor == | == Lanyard Sponsor == | ||
{| | {| | ||
|- | |- | ||
| − | | [[Image:Praetorian. | + | | [[Image:Praetorian.png|200px|link=http://www.praetorian.com]] |
|- | |- | ||
| | | | ||
| Line 155: | Line 197: | ||
|- | |- | ||
| [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] | ||
| + | |} | ||
| + | == Breakfast Taco Sponsor == | ||
| + | {| | ||
| + | |- | ||
| + | | [[Image:Honeyapps.jpg|150px|link=http://www.honeyapps.com]] | ||
|} | |} | ||
| + | |||
==== Venue ==== | ==== Venue ==== | ||
| Line 171: | Line 219: | ||
==== Hotel ==== | ==== Hotel ==== | ||
| − | We have partnered with the | + | We have partnered with the Hotel Allandale, located right next to the Norris Conference Center, for this year's conference. You can call the hotel and mention that you would like the $90/night LASCON rate and they should be able to assist you.<br> |
| − | + | Hotel Allandale<br> | |
| − | + | 7685 Northcross Drive<br> | |
| − | Austin, | + | Austin, TX 78757<br> |
| − | + | <br> | |
| − | + | http://hotelallandale.com<br> | |
| − | The rooms are $ | + | <br> |
| + | The rooms are $90 for a King size room and includes a full breakfast daily and a social hour Monday-Thursday. Hotel Allandale is walking distance from the Norris Conference Center! | ||
| − | [ | + | [[Image:Allandale.png|400px]] |
==== Sponsorship Options ==== | ==== Sponsorship Options ==== | ||
| Line 241: | Line 290: | ||
<headertabs /> | <headertabs /> | ||
| − | [[Category: | + | [[Category:OWASP_Chapter/Events]] [[Category:OWASP_AppSec_USA]] |
Latest revision as of 22:02, 10 November 2014
Click here for information on LASCON 2010.
SAVE THE DATE: LASCON 2011 is happening on October 28th, 2011 in Austin, TX
Follow LASCONATX on Twitter | Norris Conference Center
Welcome
|
|
|
Registration
Registration Is Now Open!
OWASP Membership ($50 annual membership fee) gets you a discount on registration.
| Non-Members (Includes a 1 year OWASP membership) | $125 Until 7/31/2011 | $175 Until 9/30/2011 | $225 After 9/30/2011 |
| OWASP Members | $75 Until 7/31/2011 | $125 Until 9/30/2011 | $175 After 9/30/2011 |
| Students with valid Student ID (must be shown at the door) | $50 Until 7/31/2011 | $75 Until 9/30/2011 | $100 After 9/30/2011 |
Who Should Attend LASCON 2011:
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interesting in Improving IT Security
For student discount, you must present proof of current enrollment when picking up your badge. No exceptions.
Training
We are pleased to announce that this year we will be adding on two different training classes the day before the Lonestar Application Security Conference (LASCON) on Thursday, October 27, 2011. These training classes are unlike those you see at most conferences both in content and cost. If you have already registered for LASCON, simply go to http://www.regonline.com/lascon2011 and select the "Already Registered?" link. Log in with the e-mail address you registered with and then select to edit your "Agenda". Place a check mark in the box for the training you would like to attend (or the FREE happy hour) and select "Continue" to check out. If you have not already registered for LASCON, you will have the ability to add the training of your choice on the "Agenda" screen of registration. The trainings are as follows:
TRAINING 1 ($250):
Title: Advanced Threat Tactics with Armitage and Metasploit
Metasploit is a powerful exploit framework and a must-have tool for penetration testers. Armitage builds a workflow on top of the Metasploit framework and exposes its most advanced capabilities. This demonstration and lab oriented session will teach you Metasploit and Armitage for the purpose of emulating adversary tactics. This course will start with the basics and quickly take you into the workflow of modern threats. You'll learn how to create trojan files, manage covert HTTP and HTTPS communications, set up social engineering attacks, and use pivoting to take over a network.
To participate in the labs, you must have VMWare Player, VMWare Fusion, or VMWare Workstation installed.
Raphael has put up some additional information on this class on his website at http://www.fastandeasyhacking.com/threats.
Biography:
Raphael Mudge is a Washington, DC, based code hacker working on a new startup effort. He is the developer of the open source Armitage for Metasploit. Raphael regularly writes and speaks on security topics. His work has appeared in USENIX ;login:, Linux Journal, and Hakin9. Previously, Raphael worked as a security researcher, software engineer, penetration tester, and system administrator.
TRAINING 2 ($250):
Title: Bootstrapping Your Application Security Program
This training class is for new managers & leads accountable for integrating Application Security into their enterprise. The course will walk through various success factors, including a mixture of strategy, policy, and technology considerations. The course will help attendees develop incremental plans they can employ to make both short-term and long-term measurable improvements to their enterprise Application Security.
Topics that will be covered include:
- Goal Setting
- Running effective pilot programs
- Working with vendors
- Roles & responsibilities in application security
- Getting buy-in from management, development, business, IT, etc.
- Meeting compliance needs (PCI & others)
- Measuring success & ROI
- Reporting to management
- Scaling your program
Biography:
Bankim Tejani specializes in helping large companies stand up application security programs. Currently a Managing Consultant ofat Fortify, An HP Company, Bankim works with leading financials, technology companies, government agencies, and other corporations. He helps them strategically inject application security processes and technologies into their SDLCs while trying to minimize impact on time to market and maximize ROI. His prior experience begins with software development and transitions to network security research, red teaming, information security research, and application security consulting & training.
Seats in these trainings will be very limited and registrants will be accepted on a first-come, first-served basis. Sign up today!
Sessions
Volunteers
Volunteers Needed!
Get involved!
We will take all the help we can get to pull off the best Web Application Security Conference of the year! Volunteers get free admission. This is your chance to rub elbows with the big players and mingle with potential networking contacts or even future employers!
Please contact james.wickett(at)owasp.org to volunteer for a specific area:
- Room Monitors
- Speakers and Trainers
- Vendors
- Registration
- Facilities
More opportunities and areas will be added as time goes on. Our File:Volunteer Sheet.doc can be downloaded which outlines some of the responsibilities and available positions. Note: this document references the the DC conference last year, this is just for a general guideline. Updated document coming soon.
Sponsors
Platinum Sponsors

|

|
Gold Sponsors

|

|
|
|
Silver Sponsors

|
|
|

|
| |

|
|
Lanyard Sponsor

|
Happy Hour Sponsor
| |
Breakfast Taco Sponsor

|
Venue
Norris Conference Center
LASCON 2011 will be taking place at the Norris Conference Center in Austin, TX.
Travel
Traveling to the Austin Metro Area
Hotel
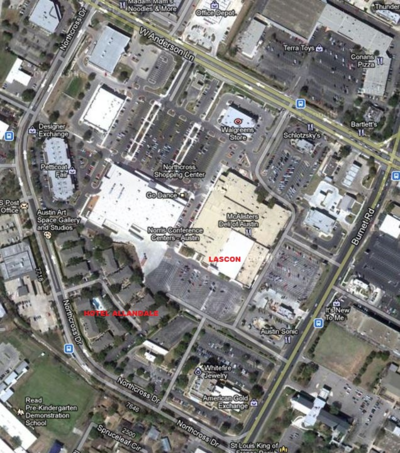
We have partnered with the Hotel Allandale, located right next to the Norris Conference Center, for this year's conference. You can call the hotel and mention that you would like the $90/night LASCON rate and they should be able to assist you.
Hotel Allandale
7685 Northcross Drive
Austin, TX 78757
http://hotelallandale.com
The rooms are $90 for a King size room and includes a full breakfast daily and a social hour Monday-Thursday. Hotel Allandale is walking distance from the Norris Conference Center!
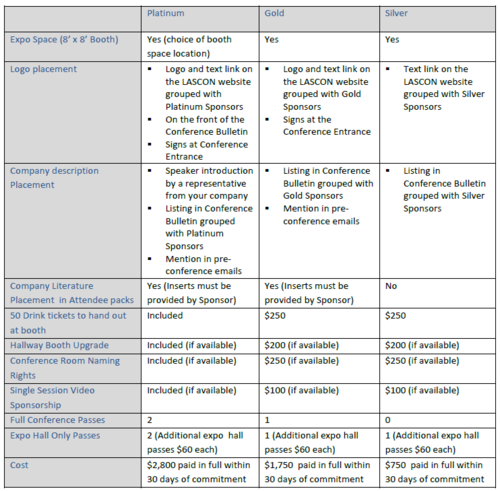
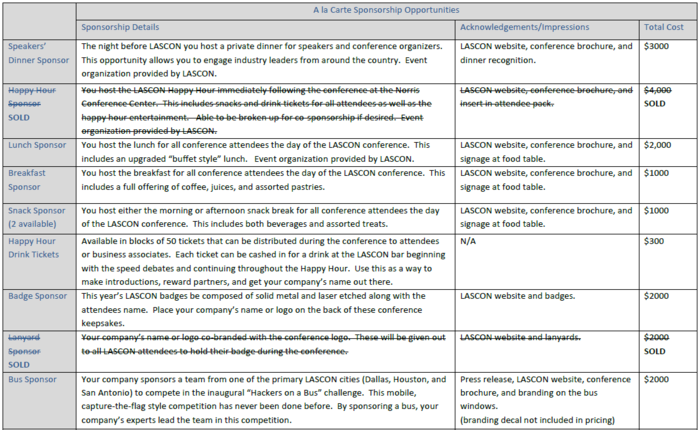
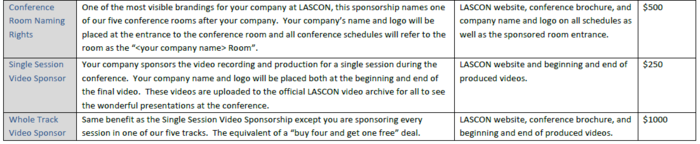
Sponsorship Options
Booth Sponsorship Opportunities
A La Carte Sponsorship Opportunities
Please contact us for more information.
Call for Papers
OWASP is currently soliciting papers for the Lonestar Application Security Conference (LASCON) 2011 that will take place at the Norris Conference Center in Austin, TX on October 28, 2011.
Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2011
We are seeking people and organizations that want to present on any of the following topics (in no particular order):
- Business Risks with Application Security - Starting and Managing Secure Development Lifecycle Programs - Web Services and XML Application Security - Metrics for Application Security - Application Threat Modeling - Hands-on Source Code Review - Web Application Security Testing - OWASP Tools and Projects - Secure Coding Practices (J2EE/.NET/Ruby) - Web Application Security countermeasures - Technology specific presentations on security such as AJAX, XML, etc - New Cutting-edge Application Security trends - Anything else relating to OWASP and Application Security
To make a submission you must include :
- Presenter(s) name(s) - Presenter(s) Email and/or Phone number(s) - Presenter(s) bio(s) - Title - One Page Abstract - Links to past presentations (if available) - Any supporting research/tools (will not be released outside of CFP committee)
Submission deadline is August 19th at 12PM CST (GMT -6)
Not everyone who submits a proposal will be able to get to present at LASCON due to limited timeslots. Also, in no way does sponsorship factor into the CFP committee's selection. Speaking slots are not for sale.
Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2011
Conference Website: http://www.lascon.org
Please forward to all interested practitioners and colleagues.