This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP AppSec Iberia 2009"
| Line 1: | Line 1: | ||
__NOTOC__ | __NOTOC__ | ||
| − | = 1st. Iberic Web Application Security Conference (IBWAS09) = | + | = 1st. Iberic Web Application Security Conference (IBWAS09) = |
| − | [[Image: | + | [[Image:Ibwas09 logo.png]] |
| − | [http://www. | + | [http://www.euitt.upm.es/ Escuela Universitaria de Ingeniería Técnica de Telecomunicación, Universidad Politécnica de Madrid] | [http://www.ibwas.com/site/registration.html Registration] |
| − | <br> <!-- Header --> | + | <br> <!-- Header --> |
| − | ====Welcome==== | + | |
| + | ==== Welcome ==== | ||
{| style="width: 100%;" | {| style="width: 100%;" | ||
|- | |- | ||
| style="width: 100%; color: rgb(0, 0, 0);" | | | style="width: 100%; color: rgb(0, 0, 0);" | | ||
| − | {| style="border: 0px | + | {| style="border: 0px solid ; background: transparent none repeat scroll 0% 0%; width: 100%; -moz-background-clip: border; -moz-background-origin: padding; -moz-background-inline-policy: continuous;" |
|- | |- | ||
| style="width: 95%; color: rgb(0, 0, 0);" | | | style="width: 95%; color: rgb(0, 0, 0);" | | ||
| Line 36: | Line 37: | ||
'''You can register for the conference [http://guest.cvent.com/i.aspx?4W,M3,26bc4c77-e1ef-4bad-be46-eb7b0124276c here].''' | '''You can register for the conference [http://guest.cvent.com/i.aspx?4W,M3,26bc4c77-e1ef-4bad-be46-eb7b0124276c here].''' | ||
| − | '''On November 11th 2009 OWASP also organizes the [[Summit 2009|OWASP Global Summit 2009]].''' | + | '''On November 11th 2009 OWASP also organizes the [[Summit 2009|OWASP Global Summit 2009]].''' <!-- Mediawiki needs all these spaces --> |
| − | |||
| − | <!-- Mediawiki needs all these spaces --> | ||
<br> | <br> | ||
| Line 63: | Line 62: | ||
<!-- End Banner --> | <!-- End Banner --> | ||
==== Global Summit 09 ==== | ==== Global Summit 09 ==== | ||
| − | |||
| − | + | On November 11th 2009 OWASP leaders and Key Industry Players join forces again to discuss the latest OWASP tools and documentation projects and set the application security agenda for 2010. | |
| − | + | One day prior to the conference OWASP chapter leaders, committee members, project leaders and OWASP members will gather in Washington for the [[Summit 2009|OWASP Global Summit 2009]]. | |
| − | + | Particiation is free for OWASP chapter leaders, committee members, project leaders and OWASP [[Membership|members]] (hint: membership is only $50). | |
| − | Full details are available on page [[Summit 2009|OWASP Global Summit 2009]]. | + | Please [http://owaspsummit.eventbrite.com/ Register] upfront so we can size the venue appropriately. This does NOT provide you access to the OWASP conference, which is a seperate registration. |
| + | |||
| + | Full details are available on page [[Summit 2009|OWASP Global Summit 2009]]. | ||
==== Registration ==== | ==== Registration ==== | ||
| Line 129: | Line 129: | ||
*Facilities -- [mailto:doug.wilson(at)owasp.org Doug Wilson] and [mailto:barry.austin(at)owasp.org Barry Austin] | *Facilities -- [mailto:doug.wilson(at)owasp.org Doug Wilson] and [mailto:barry.austin(at)owasp.org Barry Austin] | ||
| − | More opportunities and areas will be added as time goes on. Our [http://www.owasp.org/images/f/f1/OWASP_DCAppSec_Vol_Guide.pdf Volunteer Guide] can be downloaded which outlines some of the responsibilities and available positions. | + | More opportunities and areas will be added as time goes on. Our [http://www.owasp.org/images/f/f1/OWASP_DCAppSec_Vol_Guide.pdf Volunteer Guide] can be downloaded which outlines some of the responsibilities and available positions. |
Or, you can e-mail the organizers at mark.bristow(at)owasp.org, doug.wilson(at)owasp.org or rex.booth(at)owasp.org. | Or, you can e-mail the organizers at mark.bristow(at)owasp.org, doug.wilson(at)owasp.org or rex.booth(at)owasp.org. | ||
| Line 137: | Line 137: | ||
==== Schedule ==== | ==== Schedule ==== | ||
| − | + | == The conference schedule has been moved [[OWASP AppSec DC 2009 Schedule|here]] == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ==The conference schedule has been moved [[OWASP AppSec DC 2009 Schedule|here]]== | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==== Training ==== | ==== Training ==== | ||
| − | There are a total of five classrooms over two days or 10 training days available at the conference. Two classrooms hold 30 students and the other three have a capacity of 24 students. The cost for two day training is $1350 USD and the cost for one day training is $675 USD. | + | There are a total of five classrooms over two days or 10 training days available at the conference. Two classrooms hold 30 students and the other three have a capacity of 24 students. The cost for two day training is $1350 USD and the cost for one day training is $675 USD. |
== 2 Day Training: November 10 and November 11 == | == 2 Day Training: November 10 and November 11 == | ||
| Line 183: | Line 169: | ||
<br> '''Foundations of Web Services and XML Security''' The movement towards Web Services and Service Oriented architecture (SOA) paradigms requires new security paradigms to deal with new risks posed by these architectures. This session takes a pragmatic approach towards identifying Web Services security risks and selecting and applying countermeasures to the application, code, web servers, databases, application, and identity servers and related software. This course does not require a laptop though a windows based machine is useful for participating in exercises. | <br> '''Foundations of Web Services and XML Security''' The movement towards Web Services and Service Oriented architecture (SOA) paradigms requires new security paradigms to deal with new risks posed by these architectures. This session takes a pragmatic approach towards identifying Web Services security risks and selecting and applying countermeasures to the application, code, web servers, databases, application, and identity servers and related software. This course does not require a laptop though a windows based machine is useful for participating in exercises. | ||
| − | '''Instructor: [[User:Wichers|Dave Wichers]]''', [http://www.aspectsecurity.com Aspect Security] | + | '''Instructor: [[User:Wichers|Dave Wichers]]''', [http://www.aspectsecurity.com Aspect Security] |
<br> '''Applying the OWASP Testing Guide with the OWASP Live CD''' | <br> '''Applying the OWASP Testing Guide with the OWASP Live CD''' | ||
| Line 189: | Line 175: | ||
The OWASP Live CD provides the necessary tools to test web applications. The OWASP Testing Guide provides a testing framework. You're testing web applications currently, now what? Time to take your testing to the next level. This class will offer information on how to use the OWASP Live CD tools together for greater accuracy and speed, how to feed the results of one tool into another, and how to automate the more tedious aspects of web application testing. The training is focused not on what or how to test, but how to get more out of the testing time you have. Lets face it, testing time frames are always shorter then they should be, so how can you squeeze the most into the engagement time you have. After attending this training, you'll have some tricks in your bag to optimize your testing. | The OWASP Live CD provides the necessary tools to test web applications. The OWASP Testing Guide provides a testing framework. You're testing web applications currently, now what? Time to take your testing to the next level. This class will offer information on how to use the OWASP Live CD tools together for greater accuracy and speed, how to feed the results of one tool into another, and how to automate the more tedious aspects of web application testing. The training is focused not on what or how to test, but how to get more out of the testing time you have. Lets face it, testing time frames are always shorter then they should be, so how can you squeeze the most into the engagement time you have. After attending this training, you'll have some tricks in your bag to optimize your testing. | ||
| − | '''Instructor: Matt Tesauro:''' | + | '''Instructor: Matt Tesauro:''' |
== 1 Day Training November 11 == | == 1 Day Training November 11 == | ||
| Line 199: | Line 185: | ||
'''Instructor: Robert Zakon:''' Robert Zakon is a technology consultant and developer who has been programming web applications since the Web's infancy, over 15 years ago. In addition to developing web applications for web sites receiving millions of daily hits, he works with organizations in an interim CTO capacity, and advises corporations, non‐profits and government agencies on technology, information, and security architectures and infrastructures. He has presented at numerous conferences and taught a handful of courses and tutorials. Robert is a former Principal Engineer with MITRE's Information Security Center, CTO of an Internet consumer portal and application service provider, and Director of a university research lab. He is a Senior Member of the IEEE, and holds BS & MS degrees from Case Western Reserve University in Computer Engineering & Science with concentrations in Philosophy & Psychology. His interests are diverse and can be explored at www.Zakon.org where a full vitae is available. | '''Instructor: Robert Zakon:''' Robert Zakon is a technology consultant and developer who has been programming web applications since the Web's infancy, over 15 years ago. In addition to developing web applications for web sites receiving millions of daily hits, he works with organizations in an interim CTO capacity, and advises corporations, non‐profits and government agencies on technology, information, and security architectures and infrastructures. He has presented at numerous conferences and taught a handful of courses and tutorials. Robert is a former Principal Engineer with MITRE's Information Security Center, CTO of an Internet consumer portal and application service provider, and Director of a university research lab. He is a Senior Member of the IEEE, and holds BS & MS degrees from Case Western Reserve University in Computer Engineering & Science with concentrations in Philosophy & Psychology. His interests are diverse and can be explored at www.Zakon.org where a full vitae is available. | ||
| − | + | <br> | |
<br> '''Leader and Manager Training - Leading the Development of Secure Applications''' | <br> '''Leader and Manager Training - Leading the Development of Secure Applications''' | ||
| − | Through a series of case studies and scenarios, John will provide awareness of application security vulnerabilities and verification techniques, compare pros/cons of remediation approaches taken, and provide a practical and tried method in establishing a positive application security program. | + | Through a series of case studies and scenarios, John will provide awareness of application security vulnerabilities and verification techniques, compare pros/cons of remediation approaches taken, and provide a practical and tried method in establishing a positive application security program. A program based on four simple balanced focus areas that leverage people, process, and technology to build the capability to reliably produce secure applications. Together, these areas with established practices will enable your organization to successfully manage, improve and sustain an application security initiative in a cost effective and regulatory compliant manner. |
| + | |||
| + | '''Instructor: John Pavone:''' John Pavone is Aspect's Vice President of Acceleration Services, specializing in the enablement of application security within organizations. John has been an IT professional for over 20 years. In the last 14 years, John has concentrated solely on Information and IT Infrastructure Security. | ||
| − | + | John held various security related management positions, including the chief security architect for a large financial services firm. In this role, John established an enterprise–wide IT security program utilizing a quantitative risk assessment and mitigation approach with a direct line of sight to the organization’s corporate dashboard. Other major accomplishments include the development and mainstreaming of an IT risk management process, the creation of an application vulnerability testing lab, and the security design and implementation of an enterprise single sign-on and authorization system. | |
| − | + | <br> | |
| − | |||
==== Venue ==== | ==== Venue ==== | ||
| Line 218: | Line 205: | ||
The convention center is located over the [http://www.wmata.com/rail/station_detail.cfm?station_id=70 Mount Vernon Square/Convention Center Metro stop] on the Green and Yellow lines of the [http://www.wmata.com DC Metro], and only a few blocks from our convention hotel, the [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] (reserve rooms [https://resweb.passkey.com/Resweb.do?mode=welcome_ei_new&eventID=1401279&fromResdesk=true here]). | The convention center is located over the [http://www.wmata.com/rail/station_detail.cfm?station_id=70 Mount Vernon Square/Convention Center Metro stop] on the Green and Yellow lines of the [http://www.wmata.com DC Metro], and only a few blocks from our convention hotel, the [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] (reserve rooms [https://resweb.passkey.com/Resweb.do?mode=welcome_ei_new&eventID=1401279&fromResdesk=true here]). | ||
| − | [http://www.dcconvention.com/ | + | [http://www.dcconvention.com/ [[Image:|Screen_shot_2009-10-03_at_12.55.55_PM.png]]] |
==== Hotel ==== | ==== Hotel ==== | ||
| Line 224: | Line 211: | ||
== Grand Hyatt Washington DC == | == Grand Hyatt Washington DC == | ||
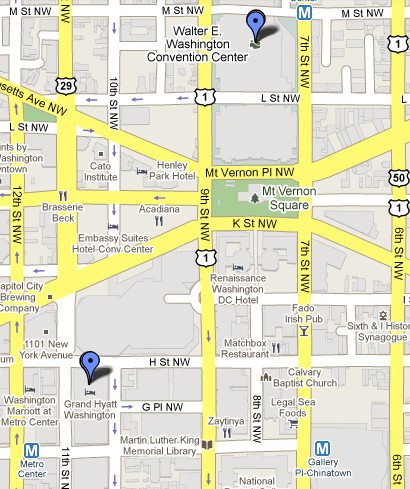
| − | [[Image: | + | [[Image:Hotel Map.png|left]] |
We've partnered with the [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] to bring you luxury accommodations at a reasonable price for your stay during our conference. | We've partnered with the [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] to bring you luxury accommodations at a reasonable price for your stay during our conference. | ||
| Line 232: | Line 219: | ||
Our [https://resweb.passkey.com/Resweb.do?mode=welcome_ei_new&eventID=1401279&fromResdesk=true convention rate for reservations] can also be applied shortly before or after the conference, if you wish to stay longer and enjoy the Washington DC Metropolitan Area. | Our [https://resweb.passkey.com/Resweb.do?mode=welcome_ei_new&eventID=1401279&fromResdesk=true convention rate for reservations] can also be applied shortly before or after the conference, if you wish to stay longer and enjoy the Washington DC Metropolitan Area. | ||
| − | You can register for a room at our convention rate of $209/night '''SOLD OUT''' | + | You can register for a room at our convention rate of $209/night '''SOLD OUT''' |
| − | The [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] is one block from the [http://www.wmata.com/rail/station_detail.cfm?station_id=1 Metro Center] metro station, and three blocks from the [http://www.wmata.com/rail/station_detail.cfm?station_id=21 Gallery Place/Chinatown] metro station. | + | The [http://grandwashington.hyatt.com/hyatt/hotels/index.jsp Grand Hyatt Washington] is one block from the [http://www.wmata.com/rail/station_detail.cfm?station_id=1 Metro Center] metro station, and three blocks from the [http://www.wmata.com/rail/station_detail.cfm?station_id=21 Gallery Place/Chinatown] metro station. |
==== Sponsors ==== | ==== Sponsors ==== | ||
| Line 244: | Line 231: | ||
Slots are going fast so contact us to sponsor today! | Slots are going fast so contact us to sponsor today! | ||
| − | {| cellspacing="10" border="0 | + | {| cellspacing="10" border="0" align="center" style="background: none repeat scroll 0% 0%; -moz-background-clip: border; -moz-background-origin: padding; -moz-background-inline-policy: continuous; color: white;" |
| − | |- | + | |- |
| − | | | + | | |
| − | |[[Image:AppSecDC2009-Sponsor-hp.gif | + | == Platinum Sponsors == |
| − | |[[Image:AppSecDC2009-Sponsor-softtek.gif | + | |
| − | | | + | | [[Image:AppSecDC2009-Sponsor-hp.gif]] |
| − | | | + | | [[Image:AppSecDC2009-Sponsor-softtek.gif]] |
| + | | | ||
| + | | | ||
|- | |- | ||
| | | | ||
|- | |- | ||
| − | | | + | | |
| − | | [[Image:AppSecDC2009-Sponsor-aod.gif | + | == Gold Sponsors == |
| − | | [[Image:AppSecDC2009-Sponsor-securicon.gif | + | |
| − | | [[Image: | + | | [[Image:AppSecDC2009-Sponsor-aod.gif]] |
| + | | [[Image:AppSecDC2009-Sponsor-securicon.gif]] | ||
| + | | [[Image:Ibmneg blurgb.jpg]] | ||
|- | |- | ||
| | | | ||
|- | |- | ||
| − | | | + | | |
| − | | [[Image:AppSecDC2009-Sponsor-aspect.gif | + | == Silver Sponsors == |
| − | | [[Image:AppSecDC2009-Sponsor-cenzic.gif | + | |
| − | | [[Image: | + | | [[Image:AppSecDC2009-Sponsor-aspect.gif]] |
| + | | [[Image:AppSecDC2009-Sponsor-cenzic.gif]] | ||
| + | | [[Image:Cigital OWASP.GIF]] | ||
|- | |- | ||
| | | | ||
| − | | [[Image:AppSecDC2009-Sponsor-core.gif | + | | [[Image:AppSecDC2009-Sponsor-core.gif]] |
| − | | [[Image:AppSecDC2009-Sponsor-cross.gif | + | | [[Image:AppSecDC2009-Sponsor-cross.gif]] |
| − | | [[Image:AppSecDC2009-Sponsor-fishnet.gif | + | | [[Image:AppSecDC2009-Sponsor-fishnet.gif]] |
| − | |||
|- | |- | ||
| − | | | + | | |
| − | | [[Image:AppSecDC2009-Sponsor-gt.gif | + | | [[Image:AppSecDC2009-Sponsor-gt.gif]] |
| − | | [[Image:AppSecDC2009-Sponsor-mandiant.gif | + | | [[Image:AppSecDC2009-Sponsor-mandiant.gif]] |
| − | | [[Image:AppSecDC2009-Sponsor-tenable.gif | + | | [[Image:AppSecDC2009-Sponsor-tenable.gif]] |
|- | |- | ||
| − | | | + | | |
| − | | [[Image:AppSecDC2009-Sponsor-veracode.gif | + | | [[Image:AppSecDC2009-Sponsor-veracode.gif]] |
| − | | [[Image:AppSecDC2009-Sponsor-whitehat.gif | + | | [[Image:AppSecDC2009-Sponsor-whitehat.gif]] |
| − | | | + | | |
|- | |- | ||
| | | | ||
| Line 288: | Line 280: | ||
| | | | ||
|- | |- | ||
| − | | | + | | |
| − | | [[Image:AppSecDC2009-Sponsor-issa.gif | + | === Organizational Sponsors === |
| − | | [[Image:Sponsor-isc2. | + | |
| + | | [[Image:AppSecDC2009-Sponsor-issa.gif]] | ||
| + | | [[Image:Sponsor-isc2.gif]] | ||
|- | |- | ||
| | | | ||
|- | |- | ||
| − | | | + | | |
| − | + | === Reception Sponsors === | |
| − | + | ||
| − | + | | [[Image:AppSecDC2009-Sponsor-cenzic.gif]] | |
| − | | [[Image:AppSecDC2009-Sponsor- | ||
| − | |||
|- | |- | ||
| + | | | ||
| + | === Coffee Sponsors === | ||
| + | |||
| + | | [[Image:AppSecDC2009-Sponsor-fyrm.gif]] | ||
| + | | [[Image:AppSecDC2009-Sponsor-denim.gif]] | ||
|} | |} | ||
Revision as of 11:10, 26 November 2009
1st. Iberic Web Application Security Conference (IBWAS09)
Escuela Universitaria de Ingeniería Técnica de Telecomunicación, Universidad Politécnica de Madrid | Registration
Welcome
|
|
Global Summit 09
On November 11th 2009 OWASP leaders and Key Industry Players join forces again to discuss the latest OWASP tools and documentation projects and set the application security agenda for 2010.
One day prior to the conference OWASP chapter leaders, committee members, project leaders and OWASP members will gather in Washington for the OWASP Global Summit 2009.
Particiation is free for OWASP chapter leaders, committee members, project leaders and OWASP members (hint: membership is only $50).
Please Register upfront so we can size the venue appropriately. This does NOT provide you access to the OWASP conference, which is a seperate registration.
Full details are available on page OWASP Global Summit 2009.
Registration
Registration is now open!
You can register here
OWASP Membership ($50 annual membership fee) gets you a discount of $50.
| $395 | General Public |
| $345 | OWASP Members |
| $195 | Students |
| $1350 | 2-Day Training Course |
| $675 | 1-Day Training Course |
Go here for details on the training courses that are available.
Who Should Attend AppSec DC 2009:
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interesting in Improving IT Security
For student discount, attendees must present proof of enrollment when picking up your badge.
Volunteer
Volunteers Needed!
Get involved!
We will take all the help we can get to pull off the best Web Application Security Conference of the year!
Please contact the appropriate arch-minion to volunteer for a specific area:
- Security -- Angel Contreras
- Speakers and Trainers -- Wade Woolwine, Jeremy Long and Josh Feinblum
- Vendors -- Dave Sachdev
- Facilities -- Doug Wilson and Barry Austin
More opportunities and areas will be added as time goes on. Our Volunteer Guide can be downloaded which outlines some of the responsibilities and available positions.
Or, you can e-mail the organizers at mark.bristow(at)owasp.org, doug.wilson(at)owasp.org or rex.booth(at)owasp.org.
Or email appsec_us_09(at)lists.owasp.org or sign up for the mailing list!
Schedule
The conference schedule has been moved here
Training
There are a total of five classrooms over two days or 10 training days available at the conference. Two classrooms hold 30 students and the other three have a capacity of 24 students. The cost for two day training is $1350 USD and the cost for one day training is $675 USD.
2 Day Training: November 10 and November 11
Assessing and Exploiting Web Applications with the open source Samurai Web Testing Framework
This course will focus on using open source tools to perform web application assessments. The course will take attendees through the process of application assessment using the open source tools included in the Samurai Web Testing Framework Live CD (Samurai-WTF). Day one will take students through the steps and open source tools used to assess applications for vulnerabilities. Day two will focus on the exploitation of web app vulnerabilities, spending half the day on server side attacks and the other half of the day on client side attacks. The latest tools and techniques will be use throughout the course, including several tools developed by the trainers themselves.
Instructor: Justin Searle: Justin Searle, a Senior Security Analyst with InGuardians, specializes in penetration testing and security architecture. Previously, Justin served as JetBlue Airway’s IT Security Architect and has provided top-tier support for the largest supercomputers in the world. In his rapidly dwindling spare time, Justin co-leads prominent open source projects including The Middler, Samurai Web Testing Framework, BASE, and the social networking pentest tools: Yokoso! and Laudnum.
Java EE Secure Code Review
The gut of any application lies in its source code. With the ever-emerging landscape of threats and attack vectors facing today’s applications, the need for secure source code has never been greater. In this course, students will be working with actual web application source code samples and discover how to pinpoint weaknesses, identify common security flaws, and discuss corrective coding controls. Major application security domains will be covered, including common authentication and access control coding errors, session management vulnerabilities, identifying injection flaws, and more. For anyone looking to learn how to identify common security weaknesses in a code base, this course is a must.
Instructor: Sahba Kazerooni: Sahba Kazerooni is Practice Lead of Software Security Services. He has a strong background in Java EE architecture and development. At Security Compass, Sahba leads the Software Security Services practice which performs penetration testing, source code review, and Threat Modeling of client applications. He also plays a critical role in the development of curriculum for and delivery of Security Compass training services. He has developed and taught courses on various topics such as Secure Coding in Java EE, Exploiting and Defending Web Applications, and Application Security Awareness. Mr. Kazerooni is also an internationally-renowned speaker on security topics. He has presented at conferences around the world including BlackHat Security Conference in Amsterdam, Security Opus in San Francisco, and IDC WebSec in Mexico City. Sahba delivers Java secure coding training at the SANS Institute, the largest source for information security training and certification, and has also provided numerous presentations through ISC2 to their elite network of certified information security professionals.
1 Day Training November 10
Threat Modeling Express The benefits of threat modeling at the design stage are well-documented, yet few organizations are able to perform this analysis technique due to time constraints. Based on our experience in real world situations, Security Compass has developed a one day approach to threat modeling .
In this class, students learn how to create a “quick and dirty” application threat model using an organization’s most valuable resource: its people. Students learn about the basics of web application security, as well as learn about and perform a real hands-on Express Threat Model. A deliverable template and list of steps will be provided as takeaways for students.
Instructor: Krishna Raja: Krishna Raja is an Application Security Consultant with an extensive background in J2EE application development. He has performed comprehensive security assessments for various clients, which involves threat analysis, source code inspection and runtime penetration testing.
Mr. Raja has also been instrumental in the development and delivery of Security Compass’ training curriculum. He has developed and taught courses in Exploiting and Defending Web Applications, Application Security Awareness and Advanced Application Attacks to architects, project managers and developers across Canada and the United States. Krishna is an emerging speaker at information security conferences, and last year spoke at Source Boston 2008 and ISSA Secure SD Symposium.
Foundations of Web Services and XML Security The movement towards Web Services and Service Oriented architecture (SOA) paradigms requires new security paradigms to deal with new risks posed by these architectures. This session takes a pragmatic approach towards identifying Web Services security risks and selecting and applying countermeasures to the application, code, web servers, databases, application, and identity servers and related software. This course does not require a laptop though a windows based machine is useful for participating in exercises.
Instructor: Dave Wichers, Aspect Security
Applying the OWASP Testing Guide with the OWASP Live CD
The OWASP Live CD provides the necessary tools to test web applications. The OWASP Testing Guide provides a testing framework. You're testing web applications currently, now what? Time to take your testing to the next level. This class will offer information on how to use the OWASP Live CD tools together for greater accuracy and speed, how to feed the results of one tool into another, and how to automate the more tedious aspects of web application testing. The training is focused not on what or how to test, but how to get more out of the testing time you have. Lets face it, testing time frames are always shorter then they should be, so how can you squeeze the most into the engagement time you have. After attending this training, you'll have some tricks in your bag to optimize your testing.
Instructor: Matt Tesauro:
1 Day Training November 11
WebAppSec.php: Developing Secure Web Applications
Web applications are the new frontier of wide‐spread security breaches. This tutorial will guide through development practices to ensure the security and integrity of web applications, in turn protecting user data and the infrastructure the application runs on. Several attack types will be reviewed, along with how the proper development practices can mitigate their damage. Although the tutorial targets the security of PHP‐based applications, much of the content is applicable to other programming languages as well.
Instructor: Robert Zakon: Robert Zakon is a technology consultant and developer who has been programming web applications since the Web's infancy, over 15 years ago. In addition to developing web applications for web sites receiving millions of daily hits, he works with organizations in an interim CTO capacity, and advises corporations, non‐profits and government agencies on technology, information, and security architectures and infrastructures. He has presented at numerous conferences and taught a handful of courses and tutorials. Robert is a former Principal Engineer with MITRE's Information Security Center, CTO of an Internet consumer portal and application service provider, and Director of a university research lab. He is a Senior Member of the IEEE, and holds BS & MS degrees from Case Western Reserve University in Computer Engineering & Science with concentrations in Philosophy & Psychology. His interests are diverse and can be explored at www.Zakon.org where a full vitae is available.
Leader and Manager Training - Leading the Development of Secure Applications
Through a series of case studies and scenarios, John will provide awareness of application security vulnerabilities and verification techniques, compare pros/cons of remediation approaches taken, and provide a practical and tried method in establishing a positive application security program. A program based on four simple balanced focus areas that leverage people, process, and technology to build the capability to reliably produce secure applications. Together, these areas with established practices will enable your organization to successfully manage, improve and sustain an application security initiative in a cost effective and regulatory compliant manner.
Instructor: John Pavone: John Pavone is Aspect's Vice President of Acceleration Services, specializing in the enablement of application security within organizations. John has been an IT professional for over 20 years. In the last 14 years, John has concentrated solely on Information and IT Infrastructure Security.
John held various security related management positions, including the chief security architect for a large financial services firm. In this role, John established an enterprise–wide IT security program utilizing a quantitative risk assessment and mitigation approach with a direct line of sight to the organization’s corporate dashboard. Other major accomplishments include the development and mainstreaming of an IT risk management process, the creation of an application vulnerability testing lab, and the security design and implementation of an enterprise single sign-on and authorization system.
Venue
Walter E. Washington Convention Center
AppSec DC 2009 will be taking place at the Walter E. Washington Convention Center in downtown Washington DC.
The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro, and only a few blocks from our convention hotel, the Grand Hyatt Washington (reserve rooms here).
[[Image:|Screen_shot_2009-10-03_at_12.55.55_PM.png]]
Hotel
Grand Hyatt Washington DC
We've partnered with the Grand Hyatt Washington to bring you luxury accommodations at a reasonable price for your stay during our conference.
The Grand Hyatt is only a few blocks from the DC Convention Center and adjacent to a wide variety of restaurants and night life in downtown DC.
Our convention rate for reservations can also be applied shortly before or after the conference, if you wish to stay longer and enjoy the Washington DC Metropolitan Area.
You can register for a room at our convention rate of $209/night SOLD OUT
The Grand Hyatt Washington is one block from the Metro Center metro station, and three blocks from the Gallery Place/Chinatown metro station.
Sponsors
Sponsors
We are currently soliciting sponsors for the AppSec DC Conference. Please refer to our sponsorship opportunities for details.
Slots are going fast so contact us to sponsor today!
Platinum Sponsors |

|

|
||
Gold Sponsors |
|
|

| |
Silver Sponsors |

|

|

| |
| |

|

| ||

|
|

| ||
| |

|
|||
Organizational Sponsors |

|

| ||
Reception Sponsors |

| |||
Coffee Sponsors |
|

|
Travel
Traveling to the DC Metro Area
The Washington DC Area is serviced by three airports -- Reagan National (DCA), Dulles (IAD), and Thurgood Marshall Baltimore/Washington International (BWI). All currently have available transportation to downtown DC via public transportation, shuttles, or cab.
Washington DC is also serviced by Amtrak, VRE, and MARC train lines, which arrive in Union Station, a few metro stops or a short cab ride away from the convention center and the Grand Hyatt.
If you live in the DC Metropolitan area, we suggest taking Metro to the event. The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro.