|
|
| (42 intermediate revisions by the same user not shown) |
| Line 6: |
Line 6: |
| | ==What is the Secure code assurance tool (SCAT)== | | ==What is the Secure code assurance tool (SCAT)== |
| | <h1><b>What is the SCAT</b></h1> | | <h1><b>What is the SCAT</b></h1> |
| | + | |
| | + | [https://www.linkedin.com/pulse/secure-code-assurance-tool-scat-version-20-michael-bergman/ For more information on the <b>why</b> behind the SCAT, read my linkedIn Article here] |
| | | | |
| | ==What is the SCAT== | | ==What is the SCAT== |
| Line 27: |
Line 29: |
| | </ul> | | </ul> |
| | | | |
| − | ==Process integrity and point in time in the SDLC== | + | ==Process integrity and point in time tools: How they work in the SDLC== |
| − | | |
| − | [[File:Process integrity vs point in time.png|800px|center|Process integrity vs point in time]]
| |
| − | | |
| | | | |
| − | <h1><b>Process integrity VS point in time</b></h1>
| + | [[File:Process integrity VS point in time without check.png|800px|center|Process integrity VS point in time without check]] |
| | | | |
| − | <p> | + | <h1><b>Technical Description</b></h1> |
| | | | |
| − | ==Process integrity== | + | ==Without further complicating development environment== |
| − | </p>
| |
| − | <p>
| |
| − | Answers the questions: When a vulnerability is detected
| |
| − | </p>
| |
| | <ul> | | <ul> |
| | | | |
| − | <li>Do developers <span style="text-decoration:underline;">consistently</span> uses and approved fixes? | + | <li>SCAT is a simple 5 screen MVC, C# web application with a small footprint that can be deployed without further complicating development environment |
| − | | |
| − | <li>Do testers <span style="text-decoration:underline;">consistently</span> write valid test?
| |
| | | | |
| − | <li>Can dev teams <span style="text-decoration:underline;">consistently</span> produce evidence they have done it securely? | + | <li>Integrates with Jira and runs ZAP and SonarQube in docker containers |
| − | </li>
| |
| − | </ul>
| |
| − | <p>
| |
| − | <span style="text-decoration:underline;">Consistency is important</span>: It means that when a vulnerability is detected it is fixed and <span style="text-decoration:underline;">will not reoccur</span> in the next sprint or when a new developer joins the team. Only when consistency is in place can organisations begin improving and <span style="text-decoration:underline;">maturing the process</span>
| |
| − | </p>
| |
| − | <p>
| |
| − | Process integrity tools<strong> </strong>
| |
| − | </p>
| |
| − | <ul>
| |
| | | | |
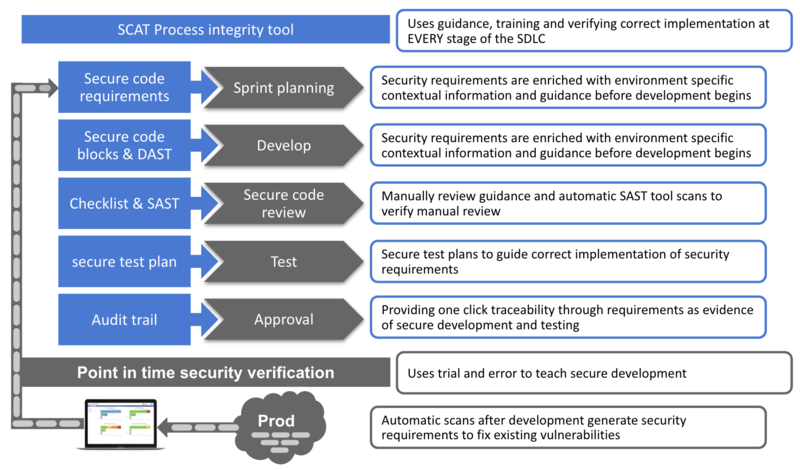
| − | <li>Vulnerability fixes are translated into security controls and built into the process of developing software. These are verified and each phase and evidence collected proving they was implemented correctly | + | <li>SCAT is part of three domains to consider when securing software development. <em>I've detailed the other domains in an article that will be published in the Nov/Dec issue of the ISC2 magazine, I will add a link here after publication.</em> |
| | | | |
| − | <li>What do we mean by “translated into security controls”?: Detected vulnerabilities are enriched with organisational specifice secure code blocks, trained, verified, evidence collected and monitored for compliance. Translating vulnerabilities into security controls has a <span style="text-decoration:underline;">higher upfront setup cost</span>
| |
| − | </li>
| |
| − | </ul>
| |
| − | <p>
| |
| − | ==Point in time security verification==
| |
| − | </p>
| |
| − | <p>
| |
| − | Answers the question: How many vulnerabilities do we have in production at this moment in time?
| |
| − | </p>
| |
| − | <p>
| |
| − | Point in time tools
| |
| − | </p>
| |
| − | <ul>
| |
| | | | |
| − | <li>Very good at periodically checking if vulnerabilities have been fixed with a low upfront setup cost
| |
| − |
| |
| − | <li>Clearly instructs as to what needs to be fixed, but gives little guidance on <span style="text-decoration:underline;">how to</span> fix vulnerabilities
| |
| − |
| |
| − | <li>Without guidance and only periodic checking, dev teams <span style="text-decoration:underline;">learn to fix vulnerabilities through trial and error</span> and rely on individual knowledge and experience
| |
| − |
| |
| − |
| |
| − |
| |
| − | <h1><b>Problems the tool address</b></h1>
| |
| − |
| |
| − | ==Low levels of compliance==
| |
| − | <ul>
| |
| − | <li> Development teams don’t have the time to study and understand the complex security requirements and don’t know how to write code or test code that implements it</li>
| |
| − | </ul>
| |
| − |
| |
| − | ==Compliance and assurance seen as blockers==
| |
| − | <ul>
| |
| − | <li>Approvers and assurance teams delay release while development teams do a post development, blind scramble for evidence to prove they have met security requirements</li>
| |
| − | </ul>
| |
| − | ==Duplication of effort and inconsistent implementation==
| |
| − | <ul>
| |
| − | <li>Complex application landscapes with multiple dev teams, application and technologies make it difficult to control and coordinate development and testing effort</li>
| |
| − | </ul>
| |
| | | | |
| | <h1><b>See how developers use SCAT</b></h1> | | <h1><b>See how developers use SCAT</b></h1> |
| Line 233: |
Line 181: |
| | <br> | | <br> |
| | | | |
| − | <h1><b> Governance, first line of defence and SCAT</b></h1> | + | <h1>Project information</h1> |
| − | | |
| − | SCAT has the following governance objectives implemented by the following “first line of defense” functions
| |
| | | | |
| − | [[File:SCATGovObj.png|thumb]]
| |
| − | === Benefits realisation: Enabling development teams to deliver at speed===
| |
| − | <ol>
| |
| − | <li>[https://www.owasp.org/index.php?title=OWASP_Security_Integration_System#Promoting_compliance_to_security_requirements Promoting compliance to security requirements]</li>
| |
| − | <li>[https://www.owasp.org/index.php?title=OWASP_Security_Integration_System#Minimising_the_impact_of_audit_and_assurance Minimising the impact of audit and assurance]</li>
| |
| − | </ol>
| |
| − | === Risk optimisation: Minimise the negative and maximise the positive consequences===
| |
| − | <ol>
| |
| − | <li>[https://www.owasp.org/index.php?title=OWASP_Security_Integration_System#Informing_risk_based_decision_making Informing risk based decision making]</li>
| |
| − | </ol>
| |
| − | === Resource optimisation: Predictable, repeatable and consistent level of security across all teams ===
| |
| − | <ol>
| |
| − | <li>[https://www.owasp.org/index.php?title=OWASP_Security_Integration_System#Integrating_security_into_the_software_development_process Integrating security into the software development process]</li>
| |
| − | </ol>
| |
| − |
| |
| − | <br>
| |
| − |
| |
| − |
| |
| − | <div style="background-color:#F2F0F0; padding-left:5pt; padding-bottom:5pt">
| |
| − | === Promoting compliance to security requirements===
| |
| − | </div>
| |
| − | [[File:Internal mapping.png|thumb]]
| |
| − | <ul>
| |
| − | <li>Understand the security requirement: The tool maintains the following internal mapping allowing organisations to translate complex security requirements into code level and testing guidance</li>
| |
| − | <ol>
| |
| − | <li>Risks mapped to technologies and secure code requirements</li>
| |
| − | <li>Secure code requirements (OWASP ASVS) mapped to secure code building block</li>
| |
| − | <li>Secure test plans (OWASP testing guide) mapped to risks</li>
| |
| − | <li>The second mapping is lifted from [[OWASP_Security_Knowledge_Framework|OWASP secure knowledge framework]] and duplicated in the SCAT. I hope to link with the SKF and remove the duplicate functionality from the SCAT tool</li>
| |
| − | </ol>
| |
| − | <li>Verify understanding: The tool also makes use of OWASP ZAP basic scan to scan localhost for vulnerabilities, confirming the correct implementation of security requirements
| |
| − | </li>
| |
| − | </ul>
| |
| − | <br>
| |
| − | <div style="background-color:#F2F0F0; padding-left:5pt; padding-bottom:5pt">
| |
| − | === Minimising the impact of audit and assurance===
| |
| − | </div>
| |
| − | <ul>
| |
| − | <li>In the testing and approval phase SCAT allows testers to stores testing evidence against the critical application function and its associated risk. Providing traceability through requirements and centrally storing and publishing test evidence</li>
| |
| − | </ul>
| |
| − |
| |
| − |
| |
| − | <div style="background-color:#F2F0F0; padding-left:5pt; padding-bottom:5pt">
| |
| − | === Informing risk based decision making===
| |
| − | </div>
| |
| − | <ul>
| |
| − | <li>For each application critical function, SCAT shows</li>
| |
| − | <ol>
| |
| − | <li>The risks that impact that application critical function</li>
| |
| − | <li>Security requirements and secure code block to protect against the risk</li>
| |
| − | <li>Test evidence proving risk has been mitigated to within tolerance</li>
| |
| − | </ol>
| |
| − | <li>Allowing risk teams see levels of exposure, easily compare it to tolerance levels. And prioritise and coordinate mitigation activities across teams and the whole application landscape</li>
| |
| − | </ul>
| |
| − | <br>
| |
| − | <div style="background-color:#F2F0F0; padding-left:5pt; padding-bottom:5pt">
| |
| − |
| |
| − | === Integrating security into the software development process===
| |
| − | </div>
| |
| − | [[File:Integrate security.png|thumb|Integrate security]]
| |
| − | <ul>
| |
| − | <li>SCAT wraps security theory, best practices and requirements into set of single purpose security screens. Then plots each of those screens to a specific software development phase</li>
| |
| − | <li>Plotting security screens to specific software development phases provides development teams with concise information when and how they need it</li>
| |
| − | </ul>
| |
| − | <br>
| |
| − | <br>
| |
| − | <br>
| |
| − | <br>
| |
| − | <br>
| |
| − | <br>
| |
| − |
| |
| − | <h1>Project information</h1>
| |
| | ==Licensing== | | ==Licensing== |
| | This program is free software: you can redistribute it and/or modify it under the terms of the [http://www.gnu.org/licenses/agpl-3.0.html link GNU Affero General Public License 3.0] as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. | | This program is free software: you can redistribute it and/or modify it under the terms of the [http://www.gnu.org/licenses/agpl-3.0.html link GNU Affero General Public License 3.0] as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. |
| | + | |
| | + | == Interested in contributing== |
| | + | [https://www.linkedin.com/in/michael-bergman-99826212a/ Please send a connect request with subject SCAT] |
| | | | |
| | == Project Resources == | | == Project Resources == |
| Line 319: |
Line 196: |
| | | | |
| | == Project Leader == | | == Project Leader == |
| − | [mailto://netblue4@googlemail.com Michael Bergman] | + | [https://www.linkedin.com/in/michael-bergman-99826212a/ Michael Bergman LinkedIn] |
| | | | |
| | ==Classifications== | | ==Classifications== |