This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Security Integration System"
MB netblue4 (talk | contribs) (→OWASP Tool Project Template) |
MB netblue4 (talk | contribs) (→What is the Secure code assurance tool (SCAT)) |
||
| (495 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| − | | valign="top" style="border-right: 1px dotted | + | | valign="top" style="border-right: 1px dotted ;padding-right:25px;" | |
| − | < | + | ==What is the Secure code assurance tool (SCAT)== |
| − | + | <h1><b>What is the SCAT</b></h1> | |
| − | </ | ||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | [https://www.linkedin.com/pulse/secure-code-assurance-tool-scat-version-20-michael-bergman/ For more information on the <b>why</b> behind the SCAT, read my linkedIn Article here] | ||
| − | == | + | ==What is the SCAT== |
| − | |||
| − | |||
| − | |||
| − | + | <ul> | |
| + | <li>SCAT is a <span style="text-decoration:underline;">process integrity tool</span>, implementing a consistent, authorized and auditable software development process | ||
| − | + | <li>SCAT is used by development teams to build, verify and assure secure software | |
| + | <ul> | ||
| + | |||
| + | <li><strong>Build</strong>: uses a combination of code level guidance, on demand training and DAST tools to train, guide and verify correct implementation | ||
| + | |||
| + | <li><strong>Verify</strong>: uses a combination of manual test plans and SATS tools to guide and verify correct implementation | ||
| + | |||
| + | <li><strong>Assure</strong>: centrally stores and publishes evidence of secure development and testing as an audit trail. Providing traceability through requirements and proving that security <span style="text-decoration:underline;">controls operate efficiently over a period of time</span> | ||
| + | </li> | ||
| + | </ul> | ||
| − | + | <li>SCAT is <span style="text-decoration:underline;">not a point in time security verification tool </span>for detecting vulnerabilities after development</li> | |
| + | </ul> | ||
| − | + | ==Process integrity and point in time tools: How they work in the SDLC== | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | [[File:Process integrity VS point in time without check.png|800px|center|Process integrity VS point in time without check]] | |
| − | |||
| − | |||
| − | + | <h1><b>Technical Description</b></h1> | |
| − | + | ==Without further complicating development environment== | |
| + | <ul> | ||
| − | + | <li>SCAT is a simple 5 screen MVC, C# web application with a small footprint that can be deployed without further complicating development environment | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <li>Integrates with Jira and runs ZAP and SonarQube in docker containers | |
| − | < | ||
| − | |||
| − | |||
| − | + | <li>SCAT is part of three domains to consider when securing software development. <em>I've detailed the other domains in an article that will be published in the Nov/Dec issue of the ISC2 magazine, I will add a link here after publication.</em> | |
| − | |||
| − | |||
| − | == | + | <h1><b>See how developers use SCAT</b></h1> |
| − | < | + | See below how the Secure code assurance tool integrates security into software development phases |
| − | + | ||
| − | </ | + | ==Sprint planning phase == |
| + | <b>Objective</b>: Ensures security requirements are understood <br> | ||
| + | |||
| + | <ul> | ||
| + | <li><b>Developers</b> use the <b>Identify risks</b> screen to<br> | ||
| + | <ol> | ||
| + | <li>Select the critical function to developing/changing</li> | ||
| + | <li>Identify the technologies used</li> | ||
| + | <li>Automatically generate the security requirements and tests</li> | ||
| + | [https://youtu.be/Gpk4K5keLyw See how to use the tools and its internal mapping to generate security requirements] | ||
| + | </ol> | ||
| + | <li><b>Product owners</b> use the <b>Secure code requirements</b> screen to<br> | ||
| + | <ol> | ||
| + | <li>Create an audit trail to store evidence of secure development</li> | ||
| + | <li>Create Jira tickets for requirements and tests to manage work</li> | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| + | |||
| + | == Development phase == | ||
| + | |||
| + | <b>Objective</b>: Ensure correct implementation of security requirements<br> | ||
| + | <ul> | ||
| + | <li><b>Developers</b> use the <b>Secure development</b> screen to<br> | ||
| + | <ol> | ||
| + | <li>View and understand how to attack and prevent the risk</li> | ||
| + | <li>View the secure code requirements</li> | ||
| + | <li>View the secure code block to implement the security requirement</li> | ||
| + | <li>Manage development effort in Jira</li> | ||
| + | <li>After development run a ZAP basic scan to verify security requirements have been correctly implemented</li> | ||
| + | [https://youtu.be/1pSatE_7mEs See how the tool helps developers understand security requirements and write secure code] | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| + | |||
| + | == Secure code review phase == | ||
| + | |||
| + | <b>Objective</b>: Ensure correct implementation of security requirements<br> | ||
| + | |||
| + | <ul> | ||
| + | <li><b>Code reviewers</b> use the <b>Secure code review </b> screen to<br> | ||
| + | <ol> | ||
| + | <li>Guide manually secure code review</li> | ||
| + | <li>After manual secure code review run a Sonarqube scan to verify security requirements have been correctly implemented</li> | ||
| + | [https://youtu.be/ygre0SrWxD4 See how the tool verifies correct security requirements implementation] | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| − | + | == Testing phase== | |
| − | + | <b>Objective</b>: Ensure valid security testing<br> | |
| − | < | + | <ul> |
| − | + | <li><b>Testers</b> use the <b>Secure testing</b> screen to<br> | |
| − | < | + | <ol> |
| − | + | <li>View the test plans required to test the risk</li> | |
| − | + | <li>Manage testing effort in Jira</li> | |
| − | + | [https://youtu.be/QdbCzheceUw See how the tool helps testers test risk mitigation efforts] | |
| − | + | </ol> | |
| − | </ | + | </li> |
| + | </ul> | ||
| + | == Approval phase == | ||
| − | + | <b>Objective</b>: Streamline the approval and audit process<br> | |
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | </ | ||
| − | + | <ul> | |
| − | < | + | <li><b>Approvers</b> use the <b>Assurance evidence </b> screen to<br> |
| − | + | <ol> | |
| − | + | <li>View relevant testing evidence alongside the risk, reducing the time assurance teams need to examine and approve releases</li> | |
| − | + | <li>View verified development effort and whether it falls within risk tolerance levels</li> | |
| + | [https://youtu.be/oyKK3Mq13B4 See how the tool streamlines the approval process with centrally stored testing evidence] | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| + | == Risk management == | ||
| + | <b>Objective</b>: Enable risk managers to prioritise, plan and monitor mitigation efforts<br> | ||
| − | + | <ul> | |
| + | <li><b>Risk managers</b> use the <b>Application risk exposure</b> screen to<br> | ||
| + | <ol> | ||
| + | <li>View each application critical function and the associated risks</li> | ||
| + | <li>Identify where mitigation effort is required by viewing which risks require security requirements</li> | ||
| + | <li>Identify where development effort is required by viewing which security requirements need secure code blocks</li> | ||
| + | <li>Identify where extra testing effort is required by viewing which risks require security test plans</li> | ||
| + | [https://youtu.be/8pKxorPSq_M See how the Application landscape overview screen informs risk based decision making] | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| + | <br> | ||
| + | <br> | ||
| − | + | <h1> <b>Preparation phase</b></h1> | |
| − | < | + | When developing secure software we need to consider both standard secure code and client specific architectural requirements |
| − | |||
| − | |||
| − | + | == Standard secure code requirements== | |
| − | [https:// | + | <ul> |
| + | <li>SCAT comes out the box with a standard OWASP secure code requirements map. This mapping need to be modified to the specific organisation requirements</li> | ||
| + | <br> | ||
| + | <li><b>Information security and development team</b> use the <b>Internal mapping </b> screen to | ||
| + | <ol> | ||
| + | <li>Map the security requirements to OWASP risks</li> | ||
| + | <li>Map organisation approved secure code blocks to security requirements</li> | ||
| + | <li>Map security test plans to OWASP risks</li> | ||
| + | [https://youtu.be/EkWdAC1sbkE See how to setup the SCAT's internal mapping] | ||
| + | </ol> | ||
| + | </li> | ||
| + | </ul> | ||
| − | + | == Client specific architectural requirements== | |
| − | [https:// | + | <ul> |
| + | <li>To generate these requirements we perform a risk assessment on client application landscape and identify</li> | ||
| + | <ol> | ||
| + | <li>Critical applications and functions</li> | ||
| + | <li>Risk associated with each critical application function</li> | ||
| + | <li>Architectural security requirements to secure each critical application functions</li> | ||
| + | <li>Client specific secure code blocks to implement security requirements</li> | ||
| + | <li>Secure test plans to verify risk has been mitigated</li> | ||
| + | </ol> | ||
| + | <br> | ||
| + | <li><b>Tool administrators</b> use the <b>Internal mapping </b> screen to | ||
| + | <ol> | ||
| + | <li>Create json files of the organisation specific risks, security requirements, secure code blocks and tests</li> | ||
| + | <li>Import these into the SCAT</li> | ||
| + | [https://youtu.be/FD3O2ObYBQs See how to import organisations specific risks, security requirements, secure code blocks and tests] | ||
| + | </ol> | ||
| + | </ul> | ||
| − | + | <br> | |
| + | <br> | ||
| − | + | <h1>Project information</h1> | |
| − | [ | + | ==Licensing== |
| + | This program is free software: you can redistribute it and/or modify it under the terms of the [http://www.gnu.org/licenses/agpl-3.0.html link GNU Affero General Public License 3.0] as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. | ||
| − | [https:// | + | == Interested in contributing== |
| + | [https://www.linkedin.com/in/michael-bergman-99826212a/ Please send a connect request with subject SCAT] | ||
| − | == Project | + | == Project Resources == |
| − | + | ||
| − | + | [Installation Package] | |
| − | |||
| − | [ | + | [Source Code] |
| − | == | + | == Project Leader == |
| − | + | [https://www.linkedin.com/in/michael-bergman-99826212a/ Michael Bergman LinkedIn] | |
| − | |||
| − | |||
| − | |||
| − | |||
==Classifications== | ==Classifications== | ||
Latest revision as of 18:33, 14 October 2019
What is the Secure code assurance tool (SCAT)
For more information on the why behind the SCAT, read my linkedIn Article here What is the SCAT
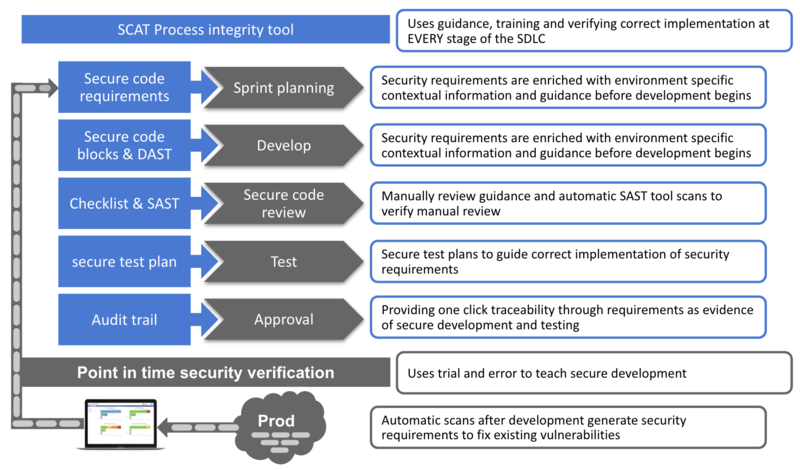
Process integrity and point in time tools: How they work in the SDLCWithout further complicating development environment
See below how the Secure code assurance tool integrates security into software development phases Sprint planning phaseObjective: Ensures security requirements are understood
Development phaseObjective: Ensure correct implementation of security requirements
Secure code review phaseObjective: Ensure correct implementation of security requirements
Testing phaseObjective: Ensure valid security testing
Approval phaseObjective: Streamline the approval and audit process
Risk managementObjective: Enable risk managers to prioritise, plan and monitor mitigation efforts
When developing secure software we need to consider both standard secure code and client specific architectural requirements Standard secure code requirements
Client specific architectural requirements
LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the link GNU Affero General Public License 3.0 as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. Interested in contributingPlease send a connect request with subject SCAT Project Resources[Installation Package] [Source Code] Project LeaderClassifications
| ||||||