This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Security Integration System"
From OWASP
MB netblue4 (talk | contribs) (→Sprint planning phase) |
MB netblue4 (talk | contribs) |
||
| Line 48: | Line 48: | ||
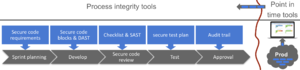
See below how the Secure code assurance tool integrates security into software development phases | See below how the Secure code assurance tool integrates security into software development phases | ||
<ul> | <ul> | ||
| − | |||
==Sprint planning phase == | ==Sprint planning phase == | ||
| − | |||
<b>Objective</b>: Ensures security requirements are understood <br> | <b>Objective</b>: Ensures security requirements are understood <br> | ||
</div> | </div> | ||
| Line 68: | Line 66: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | |||
| − | + | == <li>Development phase</li> == | |
<b>Objective</b>: Ensure correct implementation of security requirements<br> | <b>Objective</b>: Ensure correct implementation of security requirements<br> | ||
| − | |||
<ul> | <ul> | ||
<li><b>Developers</b> use the <b>Secure development</b> screen to<br> | <li><b>Developers</b> use the <b>Secure development</b> screen to<br> | ||
| Line 86: | Line 82: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | |||
| − | + | == <li>Secure code review phase</li> == | |
<b>Objective</b>: Ensure correct implementation of security requirements<br> | <b>Objective</b>: Ensure correct implementation of security requirements<br> | ||
| − | + | ||
<ul> | <ul> | ||
<li><b>Code reviewers</b> use the <b>Secure code review </b> screen to<br> | <li><b>Code reviewers</b> use the <b>Secure code review </b> screen to<br> | ||
| Line 101: | Line 96: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | |||
| − | + | == <li>Testing phase</li> == | |
<b>Objective</b>: Ensure valid security testing<br> | <b>Objective</b>: Ensure valid security testing<br> | ||
| − | |||
<ul> | <ul> | ||
<li><b>Testers</b> use the <b>Secure testing</b> screen to<br> | <li><b>Testers</b> use the <b>Secure testing</b> screen to<br> | ||
| Line 116: | Line 109: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | < | + | == <li>Approval phase</li> == |
| − | + | <b>Objective</b>: Streamline the approval and audit process<br> | |
| − | |||
| − | |||
<ul> | <ul> | ||
<li><b>Approvers</b> use the <b>Assurance evidence </b> screen to<br> | <li><b>Approvers</b> use the <b>Assurance evidence </b> screen to<br> | ||
| Line 131: | Line 122: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | + | == <li>Risk management</li> == | |
| − | + | <b>Objective</b>: Enable risk managers to prioritise, plan and monitor mitigation efforts<br> | |
| − | |||
| − | |||
| − | |||
| − | |||
<ul> | <ul> | ||
<li><b>Risk managers</b> use the <b>Application risk exposure</b> screen to<br> | <li><b>Risk managers</b> use the <b>Application risk exposure</b> screen to<br> | ||
| Line 155: | Line 142: | ||
When developing secure software we need to consider both standard secure code and client specific architectural requirements | When developing secure software we need to consider both standard secure code and client specific architectural requirements | ||
| − | + | == <b>Standard secure code requirements</b>== | |
| − | + | ||
| − | |||
<ul> | <ul> | ||
<li>SCAT comes out the box with a standard OWASP secure code requirements map. This mapping need to be modified to the specific organisation requirements</li> | <li>SCAT comes out the box with a standard OWASP secure code requirements map. This mapping need to be modified to the specific organisation requirements</li> | ||
| Line 170: | Line 156: | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | + | == <b>Client specific architectural requirements</b>== | |
| − | |||
| − | |||
</div> | </div> | ||
<ul> | <ul> | ||
Revision as of 11:21, 30 September 2019
|
|