This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Top 10 Card Game"
(Minor edit) (Tag: Visual edit) |
(Edit) |
||
| Line 156: | Line 156: | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| − | ! | + | ! Attacks !! TA Playing Card !! TA Point of View !! Proactive DC !! DC Playing Card !! DC Concepts |
|- | |- | ||
| A1 || Ace || Injection – TAs send simple text based data as part of a command or query that exploits the syntax rules of the targeted system’s interpreter. Many DC teams continue to use unsafe APIs and are lax in reviewing legacy code for injection flaws, keeping data separate from commands and limiting SQL injection mass disclosures. || C3 || 3 || Secure Database Access - Untrusted data and input is properly controlled and handled by database and platform authentication and communication controls. | | A1 || Ace || Injection – TAs send simple text based data as part of a command or query that exploits the syntax rules of the targeted system’s interpreter. Many DC teams continue to use unsafe APIs and are lax in reviewing legacy code for injection flaws, keeping data separate from commands and limiting SQL injection mass disclosures. || C3 || 3 || Secure Database Access - Untrusted data and input is properly controlled and handled by database and platform authentication and communication controls. | ||
| Line 164: | Line 164: | ||
| A2 || 2 || Broken Authentication – System flaws allow TAs to compromise passwords, keys, or session tokens, or to assume other users’ identities. Privileged accounts are frequently targeted. The prevalence of broken authentication is widespread across the DC landscape due to poor design and weak implementation of identity and access controls. Effective reconnaissance will help identify systems that may be using admin default credentials. || C6 || 6 || Implement Digital Identity - Properly configured user authentication and session management controls are in place to ensure that only legitimate users and processes are permitted. | | A2 || 2 || Broken Authentication – System flaws allow TAs to compromise passwords, keys, or session tokens, or to assume other users’ identities. Privileged accounts are frequently targeted. The prevalence of broken authentication is widespread across the DC landscape due to poor design and weak implementation of identity and access controls. Effective reconnaissance will help identify systems that may be using admin default credentials. || C6 || 6 || Implement Digital Identity - Properly configured user authentication and session management controls are in place to ensure that only legitimate users and processes are permitted. | ||
|- | |- | ||
| − | ||A3||3||Sensitive Data Exposure – TAs steal clear text data off the server, while in transit, or from the users browser. | + | ||A3||3||Sensitive Data Exposure – TAs steal clear text data off the server, while in transit, or from the users browser. Over the last few years, this attack has seen successful TA exploits. DC teams are not ensuring that the business is encrypting sensitive data. Sensitive data maybe stored or cached long after it is needed for any business purpose. When crypto is employed, weak key generation and management, and weak algorithm, protocol and cipher usage is common, particularly for weak password hashing storage techniques. For data in transit, server side weaknesses are mainly easy to detect, but hard for data at rest. |C8||8||Protect Data Everywhere - A process is in place to ensure that sensitive user; platform and application data is properly classified, encrypted and controlled. |
| − | + | |- | |
| − | Over the last few years, this attack has seen successful TA exploits. | + | || A4 || 4 || XML External Entities (XXE) - TAs upload hostile content to XML processors or documents. DC management continues to disregard this risk and frequently fails to support funding for Web Application Firewalls, XXE testing and essential developer training to identify and mitigate XXE. |
| − | |C8||8||Protect Data Everywhere - A process is in place to ensure that sensitive user; platform and application data is properly classified, encrypted and controlled. | + | || C4 || 4 || Encode and Escape Data - Applications are designed to encode and escape data to ensure that TA crafted scripts are prevented from hijacking the intended process. |
| + | |- | ||
| + | || A5 || 5 || Broken Access Control – TAs know that flawed applications and APIs may allow users to move beyond management’s intended permissions. Access control weaknesses are common due to the lack of automated detection and effective functional testing by application developers. | ||
| + | || C7 || 7 || Enforce Access Controls - Steps have been taken to ensure that user roles are properly managed and that need-to-know and data sensitivity access controls are properly configured. | ||
|- | |- | ||
| − | || | + | || A6 || 6 || Security Misconfiguration – TAs exploit unpatched flaws or access default accounts, unused pages, unprotected files and directories to gain unauthorized access or knowledge of the system. Without a robust and mature DC process, it is virtually impossible for companies to properly harden all assets resulting in application stack security misconfigurations permitting successful exploits of network services, platforms, web servers, application servers, databases, frameworks, custom code, and pre-installed virtual machines, containers, or storage. |
| + | || C1 || Ace || Define Security Requirements - Standardized security requirements are in place and supported by adequate resources to ensure that assets are properly secured, configured, patched and upgraded. | ||
|- | |- | ||
| − | || | + | || A7 || 7 || Cross-Site Scripting (XSS) – TA input is not prevented from updating a web page with malicious data resulting in hijacked user sessions, defaced web sites, redirected users and malware. DC teams are not following the OWASP XSS Prevention Cheat Sheet and TAs around the globe are leveraging this risk. It is found in approximately two-thirds of all applications. |
| + | || C4 || 4 || Encode and Escape Data - Applications are designed to encode and escape data to ensure that TA crafted scripts are prevented from hijacking the intended process. | ||
|- | |- | ||
| − | || | + | || A8 || 8 || Insecure Deserialization – TAs exploit weaknesses in applications and APIs that permit the deserialization of hostile TA data. TA exploitation of deserialization is difficult, as off the shelf exploits rarely work without changes or tweaks to the underlying exploit code. |
| + | || C5 || 5 || Validate All Inputs - Processing controls are in place to prevent the server-side handling of invalid input and design controls are in place to minimize the use of serialized data formats. | ||
|- | |- | ||
| − | || | + | || A9 || 9 || Known Vulnerabilities - TAs identify weak components through scanning or manual analysis and customize attack exploits. Prevalence of this issue in the business community is widespread. Component-heavy development patterns has resulted in development teams not understanding which components they use in their application or API, much less keeping them up to date. DC teams may be limited in their efforts to scan, identify and remove unnecessary functions and monitor libraries. |
| + | || C2 || 2 || Leverage Security Frameworks and Libraries - Only trusted frameworks and libraries with solid security features are employed. | ||
|- | |- | ||
| − | || | + | || Black Hat || Joker || Phishing attack – Phishing controls include day-to-day procedures and education and are rarely designed with the holistic view necessary to mount an effective defense. There are few DC precautions that application writers can follow to reduce this risk. DC and business management have historically been lax in addressing phishing controls. |
| + | || None || || User Education - Effective DC actions to blunt a phishing attack are limited. | ||
|- | |- | ||
| − | || | + | || A10 || 10 || 3 || 4 || 5 || This card represents additional malware that supports the attack card (A1 through A9). It is used during the attack phase. It is not a stand-alone attack card. The A10 card may be added to support the TA’s attack card during the current or subsequent attack rounds. |
| + | |||
| + | The A10 card can only be played during an Assess Web Platform Technical Weaknesses Attack or PWN Attack. | ||
| + | |||
| + | The TA’s A10 card may be any color. | ||
| + | |||
| + | |- | ||
| + | || || || || C9 || 9 || Logging and Monitoring - This card represents the effective logging and monitoring of the web platform’s operational data and application’s processing activities. | ||
| + | |||
| + | The C9 Logging and Monitoring DC card cancels TA attacks (1 through 9) unless the attack vector path (1, 2 or 3) is poisoned by the A10 malware card. | ||
| + | |||
| + | The C9 card may be any color. | ||
| + | |||
| + | The C9 defense is not effective if the TA attacking site is masked. | ||
| + | |||
| + | The C9 card can only be played during the Assess Web Platform Technical Weaknesses Attack and the PWN Attack. | ||
| + | |||
| + | |- | ||
| + | || || || || C10 || 10 || Error and Exception Handling - With this card, controls are in place to ensure that the application’s error and exception handling process does not leak system information and that it is guarded from malicious system overload. | ||
| + | |||
| + | The C10 card may be any color. | ||
| + | |||
| + | The C10 Error Handling DC card cancels TA attacks (1 through 9) unless the DC’s face card attack vector path (1, 2 or 3) is poisoned by the A10 malware card. | ||
| + | |||
| + | The C10 card can only be played during the Assess Web Platform Technical Weaknesses Attack and the PWN Attack. | ||
| + | |||
|- | |- | ||
| − | || | + | || || || || || Joker || DC White Hat Joker - The DC White Hat Joker card can be played any time while under attack to prevent a phishing attack or a pivot move in the assigned vector path. Once in play, the DC White Hat Joker card cannot be moved from the assigned position. |
|- | |- | ||
|} | |} | ||
Revision as of 00:17, 14 April 2019
OWASP Top 10 Card Game - Game DescriptionThe OWASP Top Ten card game is a fun to play poker deck card game that pits the black hats against the white hats to see who can be the first to hack their opponent’s website. OWASP Top 10 Card Game - Mission StatementUsing a standard poker card deck, design a card game that combines the concepts of the OWASP Top 10 and the OWASP Top 10 Proactive Controls, for novice level learners, that can be easily converted for use with customized OWASP branded playing cards. OWASP Top 10 Card Game - Game OverviewThe game is designed to be an easy to learn introduction to the risk concepts of the OWASP Top Ten and the best practices control concepts of the OWASP Top Ten Proactive Controls at a novice level in an environment that reflects a sense realism and excitement.
The four main components of the game (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) include:
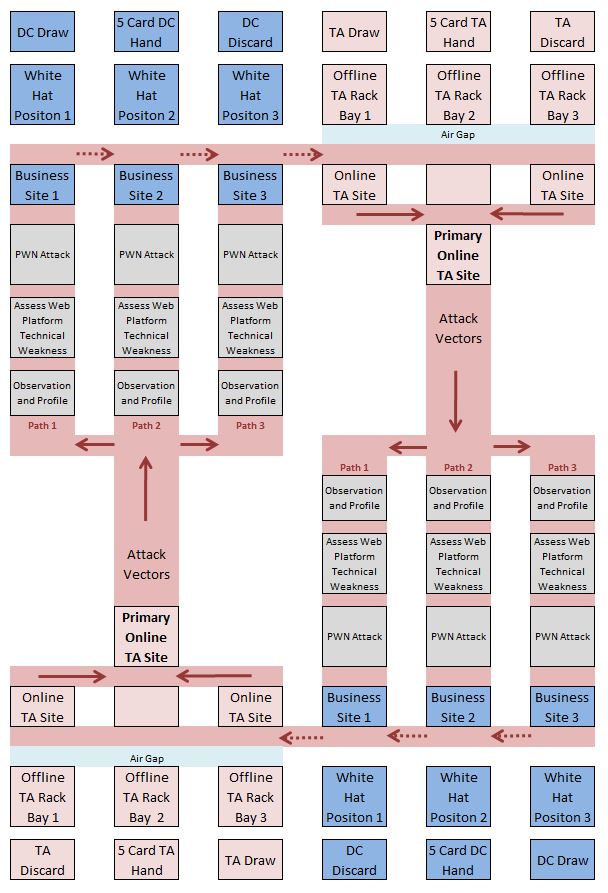
The objective of the game is to take control of (PWN) your opponent’s three business websites while protecting your business websites. It is possible to knockout all three of your opponents TA attack websites. A primary requirement for the game is that it be designed around the standard set of playing cards so that the general public is familiar with the medium facilitating internationalization. The standard two player configuration includes one TA deck and one DC deck for each gamer. The Threat Agent (TA) deck includes two Joker cards that are used to represent a Phishing attack. This brings the TA’s deck to a total of 54. The Defense Control (DC) deck also includes two joker cards that are used to represent White Hat defensive controls. This also brings the DC deck to a total of 54. During game design, a blue color deck was used to represent the DC team and a red color deck (of the same manufacture) was used to represent the malicious TA team. Cybersecurity activities and training are frequently designed around the concept of red (attacking) and blue (defending) teams. The game’s detailed play grid (See GitHub - https://github.com/OWASP/Top-10-Card-Game/) is based in part on the attack path flow diagram provided with OWASP’s Top 10 publication. The play grid is designed to help students visualize how threat agents can potentially use many different paths through your application to do harm to your business or organization. The standard two player (four deck) version of the play grid can be summarized as follows: The detailed version of the play grid contains instructional content and provides visual continuity for players: OWASP Top 10 Card Game - CardsDuring game design, four standard poker size playing card decks were used. Each player has one Threat Agent (TA) deck that represents the player’s attack team and one Defense Control (DC) deck that represents the player’s website defense team. Red TA decks and blue DC decks were used during game design. Threat Agent (TA) attack deck – 54 cards
Defense Control (DC) deck – 54 cards
Strength and weaknesses may vary among face cards (Jack, Queen, and King), suits (Clubs, Spades, Diamonds, and Hearts), card colors (black and red) and the site card’s face up/down position. Clubs and Spades are black and Diamonds and Hearts are red. Other colors can be substituted as needs require. The game is designed around the standard international, four suit, and two color (red and black) poker deck. The Masked / Unmasked status (face down / face up) of the attacking and defending sites will affect the strength and weaknesses of the opposing sites (face cards). Face down TA site cards may have more flexible attack options and may be more difficult to defense and face down DC site cards may limit some TA attacks or trigger additional TA workload counts. OWASP Top 10 Card Game - SetupThe game’s play grid should be laid out at the start of each game and each player should have ready:
OWASP Top 10 Card Game - Start of Play
OWASP Top 10 Card Game - Attack PhaseThe focus of the game is on the TA’s attack phase. The game objective is to attack and defeat (PWN) your opponent’s three DC business websites. At the start of each TA attack round, each player draws sufficient cards to ensure they have 5 cards in both the TA attack hand and the DC business hand. The TA may withdraw the current primary online attack face card and replace it with another attack face card from the online rack at no cost. Whenever a card is moved from the offline rack to the online rack, one workload counter should be added to the card moved online. There is no cost to reposition an online card or return an online card to the offline position.
The TA selects an attack card (A1 through A9). If the DC opponent is unable to defense the attack card, the attack is successful. See the instructions about TA Exploit Activities below. The TA’s attacking card (A1 through A9 and attached A10) is maintained on the grid position marking the successful exploit. The DC loser is permitted to draw one card. The DC player discards any cards in excess of 5. When the TA’s attack is defeated:
TA card status:
There are three attack vector pathways. Each pathway includes three defense-in-depth controls that must be defeated:
OWASP Top 10 Card Game - Threat Agent (TA) Exploit ActivitiesExploits are designed around five TA team activities (three attacks and two phases):
Observation Attack – This includes the concepts of profiling, research, and crafting a reconnaissance strategy. If the TA's Observation Attack is successful, the TA moves to the Weaponization phase. When an Observation exploit is defeated by an effective DC card, the attack round is over. See instructions above for when an attack is defeated. Weaponization Phase – Based on the results of the Observation phase, the TA will select the best tools and techniques to achieve a presence in the system and to eventually gain system exploit. At the beginning of the Weaponization phase, the TA has several options:
Assess Web Platform Technical Weaknesses Attack – The purpose of this attack is to evaluate the information gained from the previous phase, craft an effective attack, and assess the technical weaknesses of the opponents DC site web platform. If the attack is successful, the TA moves to the Site Application Weakness Evaluation phase. If the TA's technical weakness attack is defeated, the round is over. See instructions for when an attack phase is defeated. Site Application Weakness Evaluation – The purpose of this phase is to evaluate the information gained from the previous phases and craft an attack that will effectively implement the TA’s goals. At the beginning of the Site Application Weakness Evaluation phase, the TA has several options:
PWN Attack – The potential results and future actions following the TA’s PWN attack depend on the status of the TA's attacking face card:
If the TA's PWN exploit is defeated, the round is over. See instructions for when an attack phase is defeated. OWASP Top 10 Card Game - Attack / Defense Matrix
OWASP Top 10 Card Game - Hint TableOWASP Top 10 Card Game - LicensingThis card game is free to use. It is licensed under the Creative Commons Attribution ShareAlike 3.0 license, so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. Special customized card decks are available through OWASP. These are standard poker decks that have been modified to enhance the game’s learning experience. These decks and the related play grid contain OWASP copyrighted images and related descriptions and all rights are reserved. Generally, these decks (and play grid) are updated as the new versions of the OWASP Top 10 are released. All profit derived from the sale of the customized decks (and other related items) are used to further OWASP global efforts. See [add reference / link here] for additional information and examples. OWASP Top 10 Card Game - RoadmapPhase 1 of the project is complete and it resulted in the completion of the proof of concept, mission statement, short team goals, long team goals and a basic game prototype. Phase 2 of the project includes assistance from the OWASP foundation, setting up a project Wiki page, setting up a GitHub page, and adding the project to the OWASP project inventory (Incubator Status). Phase 3 of the project includes looking for other people to help lead and contribute to the project. Areas of need and the corresponding volunteer are listed in the “Getting Involved” section of this Wiki. Phase 4 will move the project to the Labs phase. Phase 5 will move the project to the Flagship phase. Phase 6 addresses the project’s long team goals. It will incorporate the basic OWASP Top 10 Card Game as presented in the Flagship phase along with special customized card decks that will be available through OWASP. These are standard poker decks that have been modified to enhance the game’s learning experience. These decks and the related play grid contain OWASP copyrighted images and related descriptions and all rights are reserved by OWASP. OWASP Top 10 Card Game - Getting Involved
OWASP Top 10 Card Game - Project ResourcesGitHub - https://github.com/OWASP/Top-10-Card-Game/ OWASP Top 10 Card Game - Project LeaderOWASP Top 10 Card Game - Related ProjectsNone OWASP Top 10 Card Game - Lessons Learned
|