This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP URL Checker"
Mr Craig Fox (talk | contribs) |
Mr Craig Fox (talk | contribs) m (minor tweak) |
||
| (3 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
=Main= | =Main= | ||
| − | <div style="width:100%;height:160px;border:0,margin:0;overflow: hidden;">[[ | + | <div style="width:100%;height:160px;border:0,margin:0;overflow: hidden;">[[Image:OWASP Inactive Banner.jpg|800px| link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Inactive_Projects]] </div> |
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| Line 19: | Line 19: | ||
==Description== | ==Description== | ||
| − | This tool will check a user defined website for potentially exploitable/ vulnerable URL's by comparing them against the URL extensions in the database, for instance if your target is http://google.com and in the database you have /wp-login.php it would then check if: http://google.com/wp-login.php is available on that site by checking the response. It's a form of of scanning to help you exploit and find weaknesses within the web server. The first time you run the tool it will create a database "restuls.txt" for you, and add a few URL parameters to get you started. But you can add to or change the database as much as you wish and therefore, it's as powerful as you'd like it to be. It gives you real time feedback and the option to save all the successful results. You'll also be happy to know it's open source, and I've also included a win32 compiled version (requires .NET 3.5+). | + | This tool will check a user defined website for potentially exploitable/ vulnerable URL's by comparing them against the URL extensions in the database, for instance if your target is http://google.com and in the database you have /wp-login.php it would then check if: http://google.com/wp-login.php is available on that site by checking the response. It's a form of of scanning to help you exploit and find weaknesses within the web server. The first time you run the tool it will create a database "restuls.txt" for you, and add a few URL parameters to get you started. But you can add to or change the database as much as you wish and therefore, it's as powerful as you'd like it to be. It gives you real time feedback and the option to save all the successful results. You'll also be happy to know it's open source, and I've also included a win32 compiled version (requires .NET 3.5+). |
| − | |||
==Licensing== | ==Licensing== | ||
| Line 41: | Line 40: | ||
[mailto:[email protected] Craig Fox (OWASP email)] | [mailto:[email protected] Craig Fox (OWASP email)] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Quick Download == | == Quick Download == | ||
| − | |||
[http://www.softpedia.com/dyn-postdownload.php/fe910f128856e49ea01d2e3fcb37a1bc/53a9f7bf/3c191/4/1 Softpedia Secure Download (US)] | [http://www.softpedia.com/dyn-postdownload.php/fe910f128856e49ea01d2e3fcb37a1bc/53a9f7bf/3c191/4/1 Softpedia Secure Download (US)] | ||
| Line 61: | Line 48: | ||
| − | |||
| − | |||
Latest revision as of 17:44, 17 December 2018
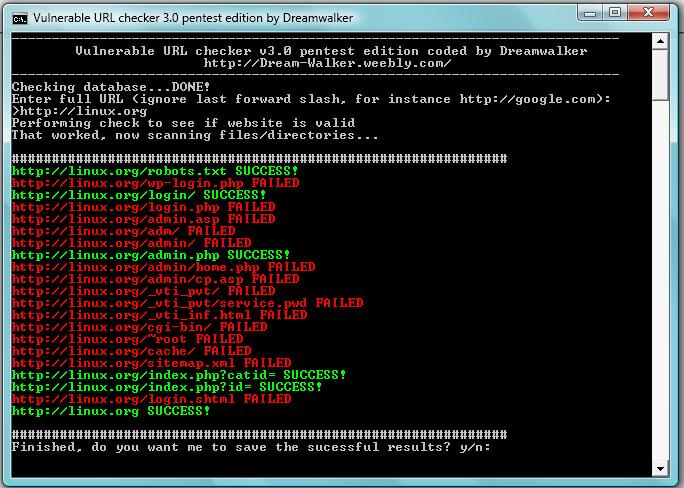
OWASP URL CheckerScreen shot:
IntroductionAn open source editable tool to scan websites for URL's which may lead to information divulging, exploits and common attack patterns. DescriptionThis tool will check a user defined website for potentially exploitable/ vulnerable URL's by comparing them against the URL extensions in the database, for instance if your target is http://google.com and in the database you have /wp-login.php it would then check if: http://google.com/wp-login.php is available on that site by checking the response. It's a form of of scanning to help you exploit and find weaknesses within the web server. The first time you run the tool it will create a database "restuls.txt" for you, and add a few URL parameters to get you started. But you can add to or change the database as much as you wish and therefore, it's as powerful as you'd like it to be. It gives you real time feedback and the option to save all the successful results. You'll also be happy to know it's open source, and I've also included a win32 compiled version (requires .NET 3.5+). LicensingOWASP URL Checker is free to use. It is licensed under the GNU GPL v3 license, so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one.
|
What is URL Checker?OWASP URL Checker provides:
Project Leader
Quick DownloadSoftpedia Secure Download (US) Softpedia Secure Download (UK)
Classifications
| |||||||
Coming soon
Volunteers
URL Checker is developed by a worldwide team of volunteers. The primary contributors to date have been:
Lead developer Craig Fox
Others
TBC
As of June 2014, the priorities are:
Involvement in the development and promotion of URL Checker is actively encouraged! You do not have to be a security expert in order to contribute. Some of the ways you can help:
Build upon the source, ensuring it's approved, tested and original credits are maintained. Use in testing, give feedback and distribute as much as possible Contribute ideas and suggestions
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||