This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OAT-005 Scalping"
(New page) |
(→Indicative Diagram) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 19: | Line 19: | ||
===Indicative Diagram=== | ===Indicative Diagram=== | ||
| − | + | [[File:OAT-005_Scalping.png|500px|link=]] | |
=== Description === | === Description === | ||
| Line 44: | Line 44: | ||
* 210 Abuse of Functionality | * 210 Abuse of Functionality | ||
| − | === CWE Base / Class / Variant | + | === CWE Base / Class / Variant IDs === |
* 799 Improper Control of Interaction Frequency | * 799 Improper Control of Interaction Frequency | ||
* 837 Improper Enforcement of a Single, Unique Action | * 837 Improper Enforcement of a Single, Unique Action | ||
| − | === WASC Threat | + | === WASC Threat IDs === |
| − | * 21 | + | * 21 Insufficient Anti-Automation |
* 42 Abuse of Functionality | * 42 Abuse of Functionality | ||
=== OWASP Attack Category / Attack IDs === | === OWASP Attack Category / Attack IDs === | ||
| − | * [[:Category:Abuse of Functionality]] | + | * [[:Category:Abuse of Functionality|Abuse of Functionality]] |
[[Category: Automated Threat]] | [[Category: Automated Threat]] | ||
Latest revision as of 15:05, 16 February 2018
This is an automated threat. To view all automated threats, please see the Automated Threat Category page. The OWASP Automated Threat Handbook - Wed Applications (pdf, print), an output of the OWASP Automated Threats to Web Applications Project, provides a fuller guide to each threat, detection methods and countermeasures. The threat identification chart helps to correctly identify the automated threat.
Definition
OWASP Automated Threat (OAT) Identity Number
OAT-005
Threat Event Name
Scalping
Summary Defining Characteristics
Obtain limited-availability and/or preferred goods/services by unfair methods.
Indicative Diagram
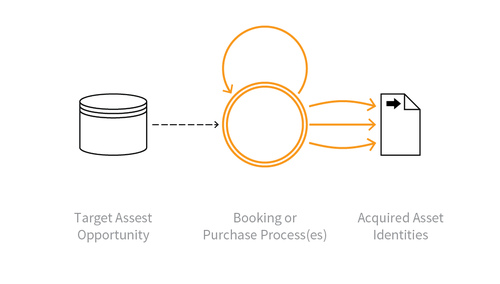
Description
Acquisition of goods or services using the application in a manner that a normal user would be unable to undertake manually.
Although Scalping may include monitoring awaiting availability of the goods or services, and then rapid action to beat normal users to obtain these, Scalping is not a "last minute" action like OAT-013 Sniping, nor just related to automation on behalf of the user such as in OAT-006 Expediting. This is because Scalping includes the additional concept of limited availability of sought-after goods or services, and is most well known in the ticketing business where the tickets acquired are then resold later at a profit by the scalpers/touts. This can also lead to a type of user denial of service, since the goods or services become unavailable rapidly.
Other Names and Examples
Bulk purchase; Purchase automaton; Purchase bot; Restaurant table/hotel room reservation speed-booking; Queue jumping; Sale stampede; Secondary ticketing; Ticket resale; Ticket scalping; Ticket touting
See Also
Cross-References
CAPEC Category / Attack Pattern IDs
- 210 Abuse of Functionality
CWE Base / Class / Variant IDs
- 799 Improper Control of Interaction Frequency
- 837 Improper Enforcement of a Single, Unique Action
WASC Threat IDs
- 21 Insufficient Anti-Automation
- 42 Abuse of Functionality