This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Juice Shop Project"
| Line 8: | Line 8: | ||
== OWASP Juice Shop Tool Project == | == OWASP Juice Shop Tool Project == | ||
| − | OWASP Juice Shop is an intentionally insecure webapp for | + | OWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire [[OWASP Top Ten]] and other severe security flaws. |
| − | |||
| − | |||
==Description== | ==Description== | ||
[[File:JuiceShop_Logo.png|left]] | [[File:JuiceShop_Logo.png|left]] | ||
| − | |||
| − | The application contains 28+ challenges where the user is supposed | + | Juice Shop is written in Node.js, Express and AngularJS. It was the first application written entirely in JavaScript listed in the [[OWASP_Vulnerable_Web_Applications_Directory_Project|OWASP VWA Directory]]. |
| + | |||
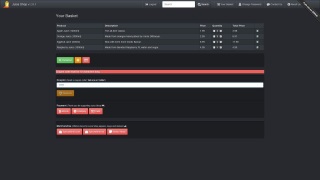
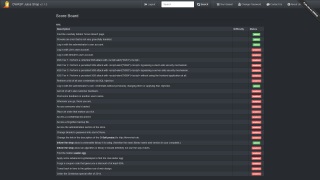
| + | The application contains 28+ challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities. The hacking progress is tracked on a score board. Finding this score board is actually one of the (easy) challenges! | ||
| + | |||
| + | Apart from the hacker and awareness training use case, pentesting proxies or security scanners can use Juice Shop as a benchmark to check how well their tools cope with Javascript-heavy application frontends and REST APIs. | ||
| + | |||
| + | <blockquote>''Translating "dump" or "useless outfit" into German yields "Saftladen" which can be reverse-translated word by word into "juice shop". Hence the project name. That the initials "JS" match with those of "Javascript" was purely coincidental!''</blockquote> | ||
| + | |||
| − | |||
| − | |||
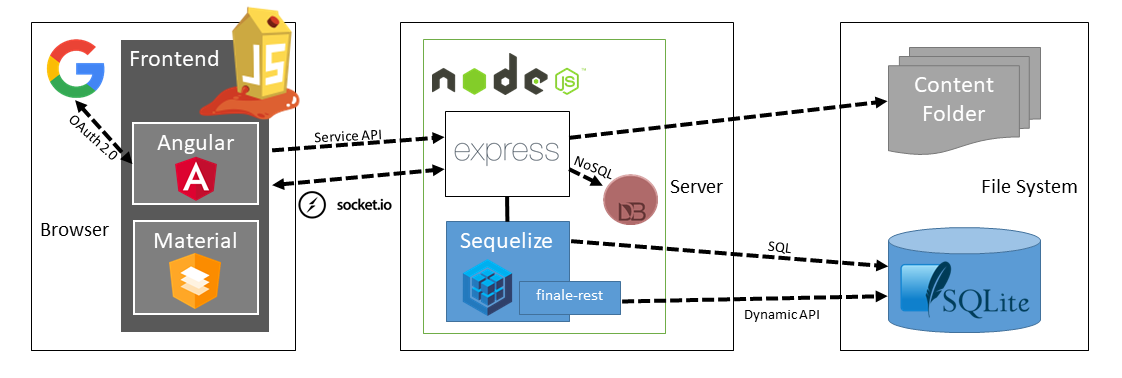
| + | == Application Architecture == | ||
| + | [[File:Architektur_JuiceShop.png]] | ||
== Screenshots == | == Screenshots == | ||
Revision as of 09:06, 29 July 2016
OWASP Juice Shop Tool ProjectOWASP Juice Shop is an intentionally insecure webapp for security trainings written entirely in Javascript which encompasses the entire OWASP Top Ten and other severe security flaws. DescriptionJuice Shop is written in Node.js, Express and AngularJS. It was the first application written entirely in JavaScript listed in the OWASP VWA Directory. The application contains 28+ challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities. The hacking progress is tracked on a score board. Finding this score board is actually one of the (easy) challenges! Apart from the hacker and awareness training use case, pentesting proxies or security scanners can use Juice Shop as a benchmark to check how well their tools cope with Javascript-heavy application frontends and REST APIs. Translating "dump" or "useless outfit" into German yields "Saftladen" which can be reverse-translated word by word into "juice shop". Hence the project name. That the initials "JS" match with those of "Javascript" was purely coincidental!
Application ArchitectureScreenshots
LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the MIT License. OWASP Juice Shop and any contributions are Copyright © by Bjoern Kimminich 2014-2016. |
<paypal>Juice Shop</paypal> InstallationSource CodeSupportMediaMerchandiseProject LeaderRelated ProjectsMiscellaneousClassifications
| |||||
Contributors
The OWASP Juice Shop is developed by a worldwide team of volunteers. A live update of project contributors is found here.
Juice Shop is already implemented, properly tested and has been promoted and demonstrated or live-hacked on various occasions including OWASP events. It has been successfully used by different companies for inhouse security trainings.
Roadmap
Functional Enhancements in 2.x
- fix known bugs
- continually adding more features/vulnerabilities to the application
Technical Evolution in 2.x
- migrate to Angular 2 (see https://github.com/bkimminich/juice-shop/issues/165)
- migrate to latest Sequelize version (see https://github.com/bkimminich/juice-shop/issues/167)
- requires to replace the discontinued sequelize-restful module
- migrate to Jasmine 2 and Frisby 2 test frameworks (see https://github.com/bkimminich/juice-shop/issues/164)
Vision for Juice Shop 3.0
- Add a CTF-mode to use Juice Shop in classroom setups competitively (see https://github.com/bkimminich/juice-shop/issues/166)
Getting Involved
Involvement in the development and promotion of OWASP Juice Shop is actively encouraged! You do not have to be a security expert or a programmer to contribute. Some of the ways you can help are as follows:
- use Juice Shop in your own hacker or awareness trainings
- provide ideas for new challenges to be added
- provide feedback via email, chat or by opening an issue on GitHub