This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP Bywaf Project"
Depasonico (talk | contribs) m (→Quick Download) |
|||
| (19 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
=Main= | =Main= | ||
| − | <div style="width:100%;height: | + | <!-- DO NOT ALTER OR REMOVE THE TEXT ON NEXT LINE --> |
| + | <div style="width:100%;height:100px;border:0,margin:0;overflow: hidden;">[[Image:OWASP Inactive Banner.jpg|800px| link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Inactive_Projects]] </div> | ||
| + | |||
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| Line 8: | Line 10: | ||
==ByWaf== | ==ByWaf== | ||
| − | ByWaf is a | + | ByWaf is back this time we used a framework called Veil this helps us to do the main core of the system for this reason the new ByWaf is called ByWaf RE (requiem) |
| − | |||
| − | |||
==Introduction== | ==Introduction== | ||
| − | + | This framework is a platform to create, store and execute python tools for Web application penetration testing. | |
| − | + | The main concept was to create something similar to metasploit. | |
| − | + | ||
| + | |||
| + | ==Description== | ||
| + | |||
| + | As part of this framework different components are provided to help contributors to add their own tools and execute them through ByWaf RE. | ||
| + | |||
| + | ==Setup== | ||
| + | |||
| + | You need to run setup.sh to configure the tool and environment under: setup/setup.sh | ||
| + | ByWaf Re is portable using python standard libraries however for Windows environment some components and functionality is limited. | ||
| + | |||
| + | ./setup | ||
| + | |||
| + | -c|--clean = Force Clean Install Of Any Dependencies | ||
| + | -s|--silent = Automates the installation | ||
| + | -h|--help = Show This Help Menu | ||
| + | |||
| + | ==Execution== | ||
| + | ByWaf Re has two modes to operate one is a simple command line execution where the functionality is just informational. | ||
| − | + | --update Update ByWaf to the latest version at github | |
| + | --version Displays version and quits | ||
| − | The | + | The second mode is the interactive mode in order to run it: |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ./bywaf.py or python bywaf.py | |
| − | |||
| − | + | ==Features== | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | [+] Auto-tab | |
| − | |||
| − | |||
| − | + | [+] Auto-fill | |
| − | |||
| − | |||
| − | + | [+] Internal commands: | |
| − | + | [-] info | |
| − | + | [-] options | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==Licensing== | ==Licensing== | ||
| Line 87: | Line 86: | ||
* Auditing tool | * Auditing tool | ||
* so on | * so on | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 100: | Line 92: | ||
Project leader's name: | Project leader's name: | ||
| − | * Rafael Gil | + | * [mailto:[email protected] Rafael Gil] |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Quick Download == | == Quick Download == | ||
| − | * https://github.com/depasonico/ | + | * [https://github.com/depasonico/ByWaf-RE GitHub] |
| + | == Sponsors == | ||
| + | [http://wingware.com/ Wingware] | ||
== News and Events == | == News and Events == | ||
| − | * [15 | + | * Tool presented at OWASP appsec EU in Cambridge June 2014 |
| − | + | * [Nov 15 2013] Beta release | |
| − | + | * [May 4 2014] Release v1.0 | |
| − | |||
==Classifications== | ==Classifications== | ||
| Line 137: | Line 123: | ||
|} | |} | ||
| − | = | + | =Screenshots= |
| + | |||
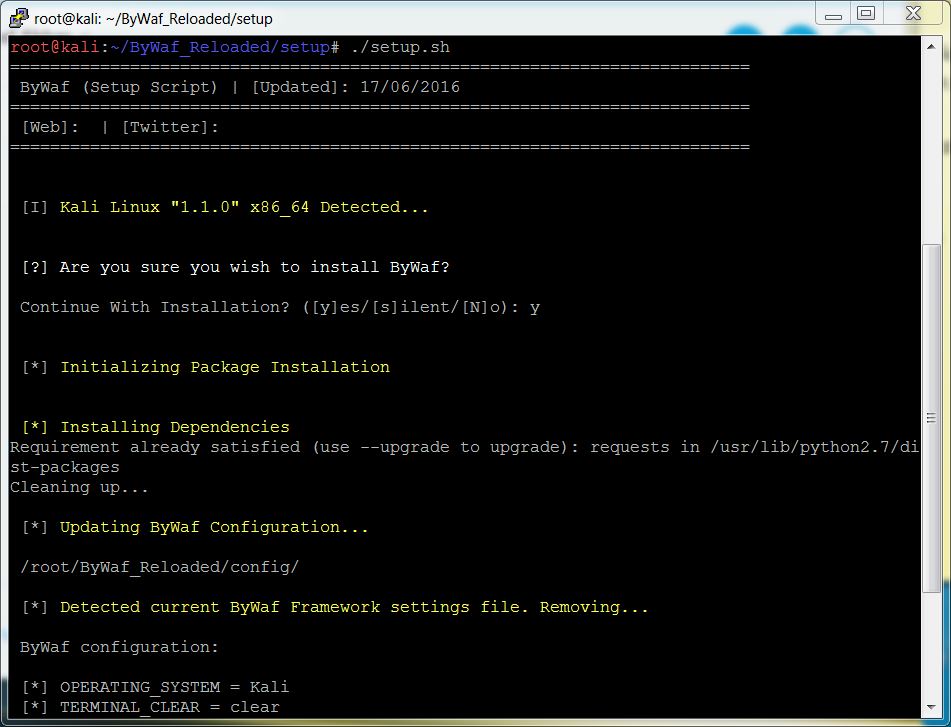
| + | [[File:Bywaf_setup.JPG]] | ||
| + | |||
| + | [+] Setup execution | ||
| + | |||
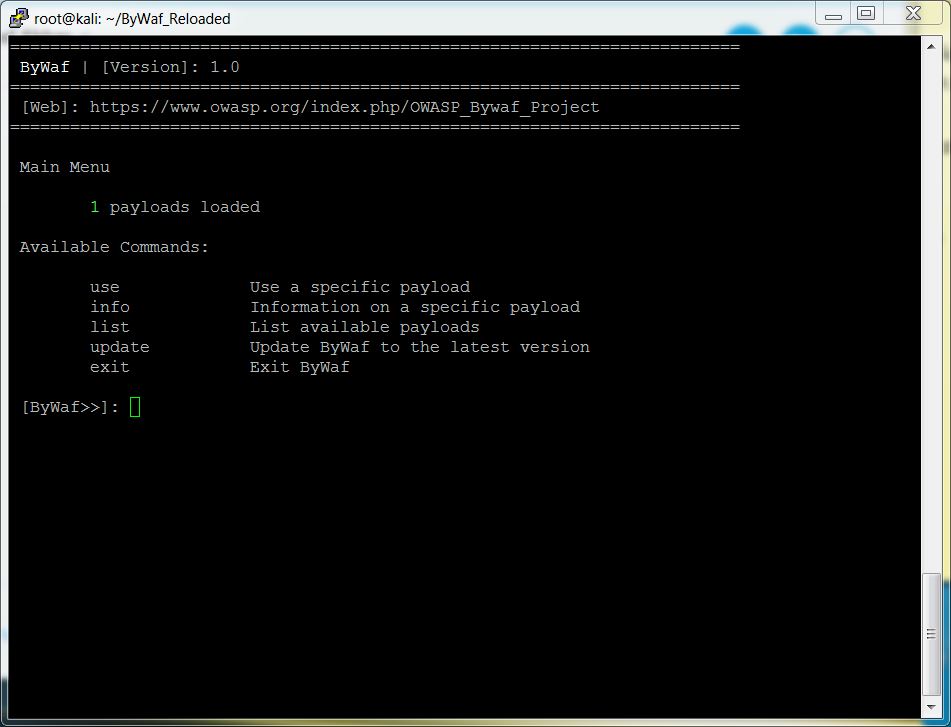
| + | [[File:ByWaf_RE_Main_Menu.jpeg]] | ||
| + | |||
| + | [+] ByWaf RE Main Menu in interactive mode | ||
| + | |||
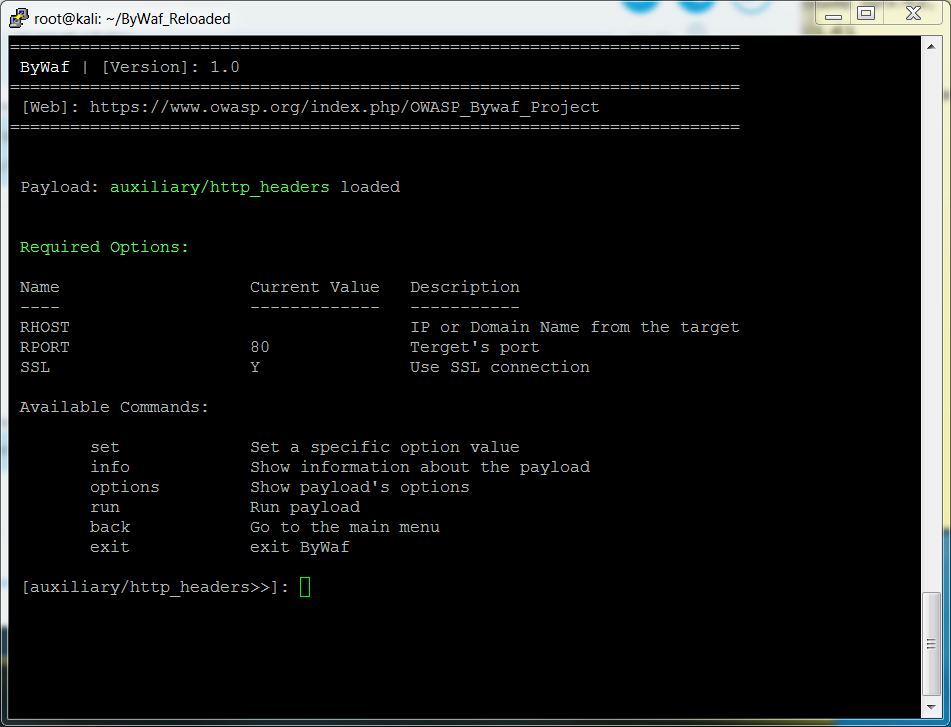
| + | [[File:Bywaf_payload_menu.JPG]] | ||
| + | |||
| + | [+] Payload menu | ||
| − | |||
= Acknowledgements = | = Acknowledgements = | ||
| Line 145: | Line 142: | ||
ByWaf is developed by a worldwide team of volunteers. The primary contributors to date have been: | ByWaf is developed by a worldwide team of volunteers. The primary contributors to date have been: | ||
| + | Veil Team: | ||
| − | + | [https://www.veil-framework.com/ Thank you All] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
= Road Map and Getting Involved = | = Road Map and Getting Involved = | ||
As of ByWaf, the priorities are: | As of ByWaf, the priorities are: | ||
| − | * | + | * Create more payloads |
| − | |||
| − | |||
Involvement in the development and promotion of ByWaf is actively encouraged! | Involvement in the development and promotion of ByWaf is actively encouraged! | ||
Latest revision as of 12:49, 29 June 2016
ByWafByWaf is back this time we used a framework called Veil this helps us to do the main core of the system for this reason the new ByWaf is called ByWaf RE (requiem) IntroductionThis framework is a platform to create, store and execute python tools for Web application penetration testing. The main concept was to create something similar to metasploit.
DescriptionAs part of this framework different components are provided to help contributors to add their own tools and execute them through ByWaf RE. SetupYou need to run setup.sh to configure the tool and environment under: setup/setup.sh ByWaf Re is portable using python standard libraries however for Windows environment some components and functionality is limited. ./setup -c|--clean = Force Clean Install Of Any Dependencies
-s|--silent = Automates the installation
-h|--help = Show This Help Menu
ExecutionByWaf Re has two modes to operate one is a simple command line execution where the functionality is just informational. --update Update ByWaf to the latest version at github --version Displays version and quits The second mode is the interactive mode in order to run it: ./bywaf.py or python bywaf.py Features[+] Auto-tab [+] Auto-fill [+] Internal commands: [-] info [-] options LicensingThis program is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or Rafael Gil any later version. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this program. If not, see <http://www.gnu.org/licenses/>. Contact: Home: https://www.owasp.org/index.php/OWASP_Bywaf_Project Mail: [email protected] skype: depasonic0 |
What is ByWaf?ByWaf provides:
Project LeaderProject leader's name: Quick DownloadSponsorsNews and Events
Classifications
| |||||||
Volunteers
ByWaf is developed by a worldwide team of volunteers. The primary contributors to date have been:
Veil Team:
As of ByWaf, the priorities are:
- Create more payloads
Involvement in the development and promotion of ByWaf is actively encouraged! You do not have to be a security expert in order to contribute. Some of the ways you can help:
- Development
- Researching
- Promoting
| PROJECT INFO What does this OWASP project offer you? |
RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||