This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Key Project Information:OWASP PCI Project"
(→OWASP PCI Toolkit) |
|||
| (35 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
==OWASP PCI Toolkit== | ==OWASP PCI Toolkit== | ||
| + | |||
OWASP PCI toolkit is an Open Source C# .NET Windows form project, that will help you to scope the PCI-DSS requirements for your System Components. | OWASP PCI toolkit is an Open Source C# .NET Windows form project, that will help you to scope the PCI-DSS requirements for your System Components. | ||
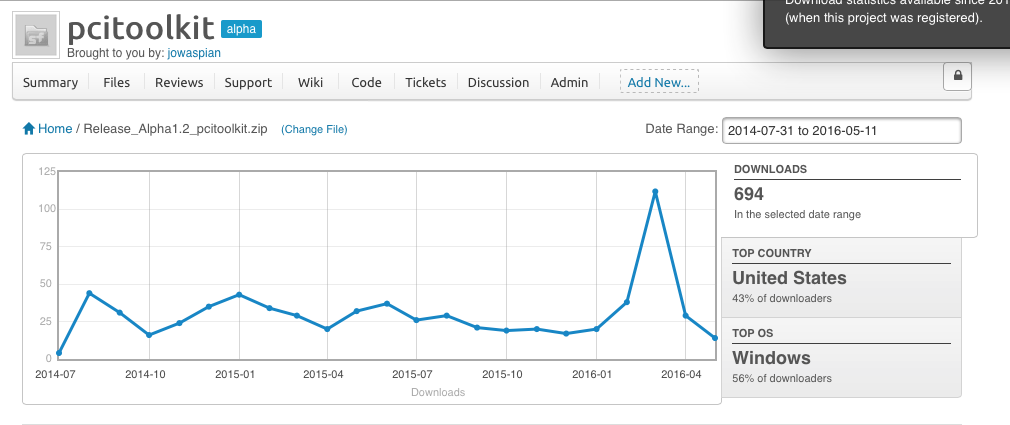
| − | Alpha version of this tool was released May 2014 | + | Alpha version of this tool was released May 2014. So far it had 694 Downloads |
| + | [[File:Screenshot_2016-05-11_18.27.07.png]] | ||
| + | |||
| + | The new version of this tool will be remake in Electron: http://electron.atom.io | ||
| + | To allow a multi platform version. | ||
| + | |||
| + | Final Release :November 2016 | ||
| + | |||
| + | We have had a total of 694 Downloads. Time for a new version with cooler features. We are working to make a Beta -Release for July 2016 | ||
==Introduction== | ==Introduction== | ||
| Line 18: | Line 27: | ||
==Preview tool== | ==Preview tool== | ||
| − | |||
| + | [[File:Screenshot_2014-07-31_10.49.24.png|688px|thumb|left|alt=Printscreen|OWASP PCI Toolkit ''[[PCI Toolkit]]''.]] | ||
| + | |||
| + | ==Download == | ||
| + | |||
| + | latest release: | ||
| + | https://sourceforge.net/projects/pcitoolkit/ | ||
| + | [[File:Project_Type_Files_TOOL.jpg]] | ||
| + | |||
| + | ==User Guide== | ||
| + | Go to: | ||
| + | https://sourceforge.net/p/pcitoolkit/wiki/Home/ | ||
== Presentation == | == Presentation == | ||
| Line 30: | Line 49: | ||
== Related Projects == | == Related Projects == | ||
| + | * https://www.owasp.org/index.php/Category:OWASP_Code_Review_Project | ||
| + | * [[:Category:OWASP Application Security Verification Standard Project|OWASP Application Security Verification Standard]] | ||
| − | + | Based on the PCI Scoping toolkit methodology: | |
| − | + | http://www.isaca.org/Groups/Professional-English/pci-compliance/GroupDocuments/OpenPCIScopingToolkit.pdf | |
== Repository== | == Repository== | ||
https://github.com/owaspjocur/OwaspPciToolkit | https://github.com/owaspjocur/OwaspPciToolkit | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== News and Events == | == News and Events == | ||
| − | + | * BlackHat 2014 Arsenal- 7 August 2014 | |
https://www.blackhat.com/us-14/arsenal.html#Curiel | https://www.blackhat.com/us-14/arsenal.html#Curiel | ||
| − | + | * APPSEC EU 2014 | |
For more info visit: https://www.owasp.org/index.php/OWASP_Project_Summit_2014/Home#tab=Tracks_and_Sessions | For more info visit: https://www.owasp.org/index.php/OWASP_Project_Summit_2014/Home#tab=Tracks_and_Sessions | ||
| − | == | + | ==PCI-DSS related projects== |
[[File:Cornucopia-pcidss-ecommerce-guidelines-small.jpg|link=https://www.pcisecuritystandards.org/pdfs/PCI_DSS_v2_eCommerce_Guidelines.pdf]] | [[File:Cornucopia-pcidss-ecommerce-guidelines-small.jpg|link=https://www.pcisecuritystandards.org/pdfs/PCI_DSS_v2_eCommerce_Guidelines.pdf]] | ||
| Line 85: | Line 89: | ||
= How to = | = How to = | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<b>Important Notice</b> | <b>Important Notice</b> | ||
| − | Understanding of security vulnerabilities | + | Understanding of security vulnerabilities as explained in the OWASP top ten or SANS Top 25 is essential for using properly this scoping tool. |
| − | The tool helps | + | The tool helps to identify if the application falls within the PCI-DSS scope in order to become compliant however it is essential to identify if your organization has the necessary tools and know-how to be able to create a scope |
| − | *Knowledge of the | + | *Knowledge of the most common security vulnerabilities in Web Applications |
*Knowledge of penetration tests and tools as advised by the PCI security council (ASV vendors) | *Knowledge of penetration tests and tools as advised by the PCI security council (ASV vendors) | ||
| + | |||
| + | Please check the guideline at: | ||
| + | https://sourceforge.net/p/pcitoolkit/wiki/Home/ | ||
=FAQs= | =FAQs= | ||
| Line 137: | Line 125: | ||
= Road Map and Getting Involved = | = Road Map and Getting Involved = | ||
| − | A prototype of the tool | + | A prototype of the tool was released in May 2014 |
| − | - | + | -Alpha version 1.0 features |
| − | + | *Series of Questions and answers regarding the Web application to be analyzed | |
| − | Series of Questions and answers regarding the Web application to be analyzed | + | *For each application present in the environment to be analyzed, |
| − | For each application present in the environment to be analyzed, | ||
*Analysis and report of Card Holder Data present | *Analysis and report of Card Holder Data present | ||
| − | + | ||
| − | + | Alpha Release 1.1 Plan for Begin November 2015 | |
| + | A complete remake of the Tool in Electron : http://electron.atom.io | ||
| + | It will include: | ||
*Analysis Report of Testing Environment process and procedures | *Analysis Report of Testing Environment process and procedures | ||
| + | * Reports in PDF format | ||
| + | * Integration with OWASP OWFT and OWASP ZAP for preliminary analysis of web application vulnerabilities | ||
| − | |||
| − | |||
| − | |||
==Feedback== | ==Feedback== | ||
| − | + | Please email johanna[dot]curiel [at] owasp.org for feedback or submit issues at https://github.com/owaspjocur/OwaspPciToolkit/issues | |
__NOTOC__ <headertabs /> | __NOTOC__ <headertabs /> | ||
| − | [[Category:OWASP Project]] [[Category:OWASP_Builders]] [[Category:OWASP_Defenders]] | + | [[Category:OWASP Project]] [[Category:OWASP_Builders]] [[Category:OWASP_Defenders]] [[Category:OWASP_Download]] |
Latest revision as of 22:35, 11 May 2016
OWASP PCI ToolkitOWASP PCI toolkit is an Open Source C# .NET Windows form project, that will help you to scope the PCI-DSS requirements for your System Components.
Alpha version of this tool was released May 2014. So far it had 694 Downloads
The new version of this tool will be remake in Electron: http://electron.atom.io To allow a multi platform version. Final Release :November 2016 We have had a total of 694 Downloads. Time for a new version with cooler features. We are working to make a Beta -Release for July 2016 IntroductionThe PCI toolkit is based on a decision tree assessment methodology, which helps you identify if your web applications are part of the PCI-DSS scope and how to apply the PCI-DSS requirements. By decomposing , one by one , you will be able to create an assessment and a final report of your scope delimitation and which OWASP guidelines must be used LicensingOWASP PCI Toolkit is free to use. It is licensed under the Creative Commons Attribution-ShareAlike 3.0 license, so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. Preview tool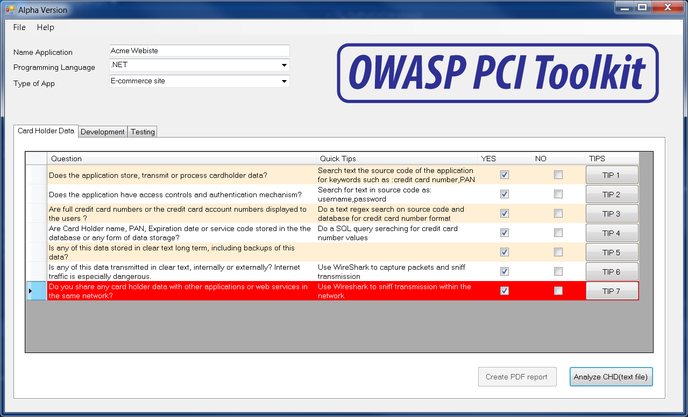 OWASP PCI Toolkit PCI Toolkit. Downloadlatest release:
https://sourceforge.net/projects/pcitoolkit/
User GuideGo to: https://sourceforge.net/p/pcitoolkit/wiki/Home/ Presentationhttps://www.owasp.org/index.php/File:Pci-dss.pdf Project Leader(s)Related Projects
Based on the PCI Scoping toolkit methodology: http://www.isaca.org/Groups/Professional-English/pci-compliance/GroupDocuments/OpenPCIScopingToolkit.pdf Repositoryhttps://github.com/owaspjocur/OwaspPciToolkit
News and Events
https://www.blackhat.com/us-14/arsenal.html#Curiel
For more info visit: https://www.owasp.org/index.php/OWASP_Project_Summit_2014/Home#tab=Tracks_and_Sessions
OWASP Cornucopia Ecommerce Website Edition is referenced in the new Payment Card Industry Security Standards Council information supplement PCI DSS E-commerce Guidelines v2, January 2013 Classifications
| |||||
Important Notice
Understanding of security vulnerabilities as explained in the OWASP top ten or SANS Top 25 is essential for using properly this scoping tool. The tool helps to identify if the application falls within the PCI-DSS scope in order to become compliant however it is essential to identify if your organization has the necessary tools and know-how to be able to create a scope
- Knowledge of the most common security vulnerabilities in Web Applications
- Knowledge of penetration tests and tools as advised by the PCI security council (ASV vendors)
Please check the guideline at: https://sourceforge.net/p/pcitoolkit/wiki/Home/
What is PCI-DSS?
The PCI Security Standards Council offers robust and comprehensive standards and supporting materials to enhance payment card data security. These materials include a framework of specifications, tools, measurements and support resources to help organizations ensure the safe handling of cardholder information at every step. The keystone is the PCI Data Security Standard (PCI DSS), which provides an actionable framework for developing a robust payment card data security process -- including prevention, detection and appropriate reaction to security incidents.
How does the PCI toolkit work?
The toolkit helps you identify if the application falls into the PCI-DSS scope and the necessary measures that must be taken in order to become compliant. The tool by it self does not scan your application but it guides you on the available tools, guidelines and documents related to understand much better how to properly execute the scope and test the application against security vulnerabilities
What is the purpose of this tool?
The main purposes is to offer an interactive guideline on how to determine if a web application falls into the PCI-DSS scope. The PCI-DSS requirements do not specify which guidelines , tools or how to implement the requirements, this tool helps you understand how to do it.
Volunteers
Johanna Curiel
Ignacio Salom
A prototype of the tool was released in May 2014 -Alpha version 1.0 features
- Series of Questions and answers regarding the Web application to be analyzed
- For each application present in the environment to be analyzed,
- Analysis and report of Card Holder Data present
Alpha Release 1.1 Plan for Begin November 2015
A complete remake of the Tool in Electron : http://electron.atom.io
It will include:
- Analysis Report of Testing Environment process and procedures
- Reports in PDF format
- Integration with OWASP OWFT and OWASP ZAP for preliminary analysis of web application vulnerabilities
Feedback
Please email johanna[dot]curiel [at] owasp.org for feedback or submit issues at https://github.com/owaspjocur/OwaspPciToolkit/issues