This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "AppSec ASIA 2016"
(→Speaker Bios) |
(→Hotel) |
||
| (93 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| + | |||
| + | {| | ||
| + | |- | ||
| + | ! width="100" align="center" | <br> | ||
| + | ! width="70" align="center" | <br> | ||
| + | |- | ||
| + | | align="center" | [[File:64614893850732793245%.jpg]] | ||
| + | | align="center" | | ||
| + | |} | ||
= Welcome = | = Welcome = | ||
| Line 42: | Line 51: | ||
|} | |} | ||
| − | = | + | =CFP= |
<font size=2pt> | <font size=2pt> | ||
| − | + | '''APPSEC ASIA 2016'''<br> | |
| + | =='''Call for Paper'''== | ||
| − | + | OWASP AppSec ASIA 2016 will bring together application security experts and software engineers from all over the world on May 21, 2016. Industry and academia meet to discuss open problems and new solutions in web & mobile security. For this event, we will invite application security researchers, thought leaders and developers worldwide to submit papers for presentations looking for “the next”, cutting edge research in the context of web applications, secure development, security management and privacy. Don't miss the opportunity to share and discuss your ideas and knowledge with other experts and practitioners. | |
| − | + | The topics of interest, but not limited: | |
| + | *Web Security | ||
| + | *Mobile Security | ||
| + | *Cloud Security, specifically secure Cloud Apps | ||
| + | *Infrastructure security | ||
| + | *Secure development | ||
| + | *Application Security Testing | ||
| + | *Privacy protection in web based apps | ||
| + | *Emerging web technologies and associated security considerations | ||
| + | *Security Trainings, Certificates and CTP | ||
| − | + | Papers should describe new ideas, new implementations, or experiences related to web & mobile security. We are glad to have some leading-edge topics and ideas as well as in-depth discussion in the conference. The conference planning team will review your submission based on a descriptive abstract of your intended presentation. Feel free to attach a preliminary version of your presentation if available, or any other supporting materials. Remember: the better your description is, the better our review will be. | |
| − | |||
| − | + | '''Important dates:'''<br> | |
| + | Submission deadline: Mar 25, 2016.<br> | ||
| + | Notification of acceptance: Mar 31, 2016.<br> | ||
| + | Presentation PPT due: April 30, 2016.<br> | ||
| − | =Speaker | + | To submit a proposal please use easy chair https://easychair.org/conferences/?conf=appsecasia2016wuhanc<br> |
| − | < | + | To contact the conference planning team, please mail to [email protected][mailto:[email protected]]<br> |
| + | OWASP Speaker Agreement: https://www.owasp.org/index.php/Speaker_Agreement<br> | ||
| + | Likely we can cover travel expenses or costs for accommodations. | ||
| − | + | '''Terms'''<br> | |
| + | By your submission you agree to the OWASP Speaker Agreement. OWASP values vendor neutrality. You need to use the OWASP presentation template and you’re not allowed to place marketing pitches in your slides. All presentation slides will be published on the conference website after the conference. Please make sure that any pictures and other materials in your slides don’t violate any copyrights. You are solely liable for copyright violations. You may choose any CC license for your slides, including CC0. OWASP does suggest open licenses. | ||
| − | = | + | =Schedule= |
| − | <font size=2pt> | + | {|border="0" class="FCK__ShowTableBorders" style="width: 100%;" |
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Schedule''' </font><br> | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Duration''' </font><br> | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Topic''' </font><br> | ||
| + | | align="center" style="width: 30%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Venue''' </font><br> | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 9:00-9:15 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | Opening speech | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 9:15-9:45 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | OWASP Mobile 2016 & Self-healing apps | ||
| + | Milan Singh Thakur | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 9:45-10:15 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | Testing next-gen iOS apps | ||
| + | Prateek Gianchandani | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 10:15-10:30 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | Coffee & Tea Break | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | 大厅 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 10:30-11:00 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | Big problems with big data - Hadoop interfaces security | ||
| + | Jakub Kaluzny | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" " | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 11:00-11:30 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | OWASP CISO Survey Report – Tactical Insights for Managers | ||
| + | Tobias Gondrom | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 11:30-12:00 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | OWASP Top 10: Effectiveness of Web Application Firewalls | ||
| + | David Caissy | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:blue" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 12:00-14:00 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 120 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" |LUNCH | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | N/A | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 14:00-14:30 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | Android硬件隔离及指纹应用的安全研究 | ||
| + | 顾凌志 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 14:30-15:00 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | Cloud-ids:智能Web 入侵检测与威胁感知 | ||
| + | 刘焱 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15:00-15:30 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 35 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 企业AppLayer面临的IT安全风险与危机 | ||
| + | Dixon Ho | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15:30-15:50 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 20 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | Coffee & Tea Break | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | 大厅 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15:50-16:20 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 无人车安全剖析 | ||
| + | 云朋 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 16:20-16:50 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | Engineering better security | ||
| + | Collin Chang | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 16:50-17:20 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 30 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 移动互联网应用的服务端安全防护探讨 | ||
| + | 权小文 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:brown" | 主会场 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 14:00-14:40 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 40 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | Capture-the-Flag Secrets | ||
| + | Ivan Butler | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 人才培养分论坛 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 14:40-15:15 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 35 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 高校源代码安全教育初探 | ||
| + | 张䶮 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 人才培养分论坛 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15:15-15:50 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 35 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 新型安全人才培养模式 | ||
| + | Rip | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 人才培养分论坛 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 15:50-16:10 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 20 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | Coffee & Tea Break | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | 大厅 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 16:10-16:45 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 35 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 从软件工程师到软件安全经理 | ||
| + | 王文君 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 人才培养分论坛 | ||
| + | |- | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 16:45-17:20 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 10 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 信息安全高端人才培养实践 | ||
| + | 张绍浪 | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:green" | 人才培养分论坛 | ||
| + | |- | ||
| − | == | + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 17:20-17:30 |
| − | + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 10 | |
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | Closing speech | ||
| + | | align="center" style="width: 25%; background: none repeat scroll 0% 0% rgb(194, 194, 194);color:yellow" | 主会场 | ||
| + | |- | ||
| + | |} | ||
| − | + | =Speaker Bios= | |
| + | <font size=2pt> | ||
| − | === | + | ===Milan Singh Thakur=== |
| − | + | *OWASP Mobile 2016 & Self-healing apps | |
| + | *主会场 | ||
| − | + | Milan is very passionate about Information Security and an International Speaker. He is leading | |
| + | OWASP Mobile Security Project Globally under which Mobile Appsec Guide, Checklist and various Cheatsheets | ||
| + | are being developed. He also works as Information Security Consultant for a private firm in India. | ||
| + | His primary focus is Mobile Security. He has helped to secure mobile apps for various well known clients | ||
| + | in banking, insurance, health, e-commerce and other sectors. Recently he has done PT for Apple iWatch | ||
| + | for a client. | ||
| + | He has expertise in fields like secure code review, NFC Pentesting, Web Appsec, VAPT activities, Wireless | ||
| + | Pentesting, Payment Gateway Security Assessments and lot more. His scope of exploration is not limited | ||
| + | to these technologies. He is strong supporter of “Open-Source” terminology and has been promoting it | ||
| + | since 2010. | ||
| − | |||
| − | |||
| − | + | ===Prateek Gianchandani=== | |
| + | *Testing next-gen iOS apps | ||
| + | *主会场 | ||
| − | + | An OWASP member and contributor has been working in the infosec industry for over 5 years. During his five years, he has performed a number of penetration tests on mobile and web applications and even developed a lot of applications for the App Store. His core focus area is mobile pentesting and embedded device hacking. He is also the author of the open source vulnerable application named Damn Vulnerable iOS app. He has presented and trained at Conferences like Defcon, Blackhat USA, Brucon, Hack in paris, Phdays etc. | |
| − | |||
| − | |||
| − | |||
| − | + | ===Jakub Kaluzny=== | |
| + | *Big problems with big data - Hadoop interfaces security | ||
| + | *主会场 | ||
| − | + | A Senior IT Security Consultant at SecuRing and performs | |
| + | penetration tests of high-risk applications, systems and devices. He was | ||
| + | a speaker at many international IT Security conferences: OWASP AppSec | ||
| + | EU, BlackHat Asia, PHdays, CONFidence, HackInTheBox AMS, as well at | ||
| + | local events. Previously working for European Space Agency and internet | ||
| + | payments intermediary. Apart from testing applications, he digs into | ||
| + | proprietary network protocols, embedded devices and other enterprise | ||
| + | solutions. | ||
| − | |||
| − | |||
| − | |||
| + | ===Tobias Gondrom=== | ||
| + | *OWASP CISO Survey Report 2015 – Tactical Insights for Managers | ||
| + | *主会场 | ||
| − | + | CTO Security for global IT company. | |
| − | + | Chairman of the Board of OWASP, Chair of the IAOC. Experience asHead of Information Security, Chief Information Security Officer, CISO, IT Risk Management, Governance & Compliance | |
| + | Head of Software Development, CTO, | ||
| + | Manage in global, multinational and complex organisations, Change Management, project management, M&A, Strategy, ArchitectureSDLC, Software development processes and standards CCISO, CISSP, CSSLP. | ||
| − | |||
| + | ===David Caissy=== | ||
| + | *OWASP Top 10: Effectiveness of Web Application Firewalls | ||
| + | *主会场 | ||
| − | + | David Caissy, M. Sc., OSCP, GWAPT, GPEN, GSEC, CISSP, CEH is a web application penetration tester with in-depth developer and IT Security background spanning over 16 years. He has extensive experience in conducting vulnerability assessments and penetration tests as well as providing training globally, amongst numerous other teaching engagements. He has worked for a central bank, various government agencies and private companies. David has been teaching web application security in colleges, conferences and for many government agencies over the last 15 years. | |
| − | |||
| − | |||
| − | |||
| + | ===顾凌志=== | ||
| + | *Android硬件隔离及指纹应用的安全研究 | ||
| + | *主会场 | ||
| − | |||
| − | |||
| − | + | 华为资深安全专家,华为SDL应用创始人之一,擅长安全架构设计、威胁建模;长期从事移动、虚拟化及通信领域业务安全的分析和研究。 | |
| − | |||
| − | |||
| − | |||
| − | + | ===刘焱=== | |
| + | *Cloud-ids:智能Web 入侵检测与威胁感知 | ||
| + | *主会场 | ||
| − | + | 百度云安全部资深架构师刘焱,毕业于华中科技大学,具有近十年 bat级互联网公司甲方安全防护经验,主持或者参与了百度内部几乎全部安全监控以及防护项目,黑客入侵主动发现比例超过80%;具有多项国家信息安全专利;在国内外学术期刊、会议发表多篇论文;主持开发的安全产品在十多家国内外中大型互联网企业中使用。 | |
| − | |||
| − | |||
| − | |||
| − | + | ===Dixon Ho=== | |
| + | *企业AppLayer面临的IT安全风险与危机 | ||
| + | *主会场 | ||
| − | + | 为ISACA北京事务委员会主席、中国信息化推进联盟信息安全专业委员会副主任,主管微软大中华区信息安全领域超过8年。在2008年担任了北京市市政管理委员会奥运城市运行指挥平台安全顾问。 | |
| − | + | 信息安全领域从业时间:近20多年。 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ===云朋=== | ||
| + | *无人车安全剖析 | ||
| + | *主会场 | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | === | + | ===常颢Collin.Chang=== |
| − | + | *Engineering better security | |
| + | *主会场 | ||
| − | + | 35岁,居于上海。现就职于Raid7。毕业于复旦大学,有12年的安全经验。曾在Venustech、 McAfee、TippingPoint(HP ESP) 以及 PaloAlto Networks工作过。他也是一个PMP, 参与过中国东部的一些大项目。熟悉Anti-virus 、IPS/IDS、NGFW、脆弱性管理解决方案。 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===权小文=== | |
| − | + | 1978年,陕西人,毕业于清华大学,获得硕士学位,2005年获得高级工程师职称,拥有4年大型国企技术和管理经验,6年跨国公司技术和管理从业经验,5年国内创业经验,15年信息安全从业经验,获得5项网络安全相关的发明专利,18项软件著作权,参与国家重大科研专项6项,参与一项网络安全相关国标制定;主要从事信息安全产品研发、技术管理、产品线管理等工作。主持开发的Web安全系列产品,占有国内30%以上市场份额,并且出口到美国、印度、迪拜等国家。创建的远江盛邦(北京)网络安全科技股份有限公司,已经申报全国股转系统,并在2016年4月14日正式挂牌新三板。 | |
| − | |||
| − | |||
| − | |||
| + | ===Ivan Butler=== | ||
| + | *Capture-the-Flag Secrets | ||
| + | *人才培养分论坛 | ||
| − | + | Founder and CEO of Compass Security, a leading Swiss ethical hacking and penetration testing company. Speaker @ BlackHat Las Vegas 2008, IT Underground Warsaw 2009, Unistrategic Singapore 2010 and organizer of Swiss Cyber Storm Security Conference since 2007. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===张=== | |
| − | + | *高校源代码安全教育初探 | |
| + | *人才培养分论坛 | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ===Rip=== | ||
| + | *新型安全人才培养模式 | ||
| + | *人才培养分论坛 | ||
| − | + | Leader of OWASP China. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ===王文君=== | ||
| + | *从软件工程师到软件安全经理 | ||
| + | *人才培养分论坛 | ||
| − | + | HP Enterprise Software全球安全技术主管,负责年营业额10亿美元的软件产品线的总体安全,以及SDL(软件安全开发流程)在公司内部的实施。OWASP上海分会负责人,CWASP资深讲师,拥有CSSLP和CISSP认证,是《Web应用安全威胁与防治》的作者之一。 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===张绍浪=== | |
| + | *信息安全高端人才培养实践 | ||
| + | *人才培养分论坛 | ||
| − | + | 从事信息安全13年,多年来一直从事信息安全产品的研发和产业化,熟悉国内外的网络安全技术,北京易霖博信息技术创史人,红客训练营创史人,公司13年成立,在其带领下从公司三五人目前已经成长为50人的团队其中研发人员35人,承担国家级比赛及省赛数十项。 | |
| − | + | = Training = | |
| + | <font size=2pt> | ||
| + | {|border="0" class="FCK__ShowTableBorders" style="width: 100%;" | ||
| + | |- | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Course Name''' </font><br> | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Trainer''' </font><br> | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Course Length''' </font><br> | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Course Date(s)''' </font><br> | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Language''' </font><br> | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(64, 88, 160); color: white;" | <font size=2pt>'''Price'''</font> | ||
| + | |- | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | OWASP Top 10 Effective Safeguards | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | David Caissy | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 4H | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | May20,8:30-12:00 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | RMB 1500 | ||
| + | |- | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Mobile Application security | ||
| + | | align="center" style="width: 20%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | Prateek Gianchandani | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | 4H | ||
| + | | align="center" style="width: 15%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | May20,14:30-18:30 | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | English | ||
| + | | align="center" style="width: 10%; background: none repeat scroll 0% 0% rgb(194, 194, 194);" | RMB 1500 | ||
| + | |- | ||
| + | |} | ||
| − | == | + | == Note == |
| − | + | *Price per attendee. | |
| − | + | *15% off for OWASP Senior Member | |
| − | + | *15% off for groups of above 10 | |
| − | + | *Conference Registration is separate. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | =Registration and Fees= | ||
| + | <font size=2pt> | ||
| − | = | + | == Conference == |
| − | + | Free for OWASP China Member. | |
| − | == | + | Link to http://m.vcooline.com/app/activity_enrolls/new?aid=2569906&wxmuid=24361 |
| − | |||
| − | |||
| − | + | == Training == | |
| + | Mail to member@owasp.org.cn for training registration. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | '''Please note that conference and training Registration is separate.''' | |
| − | ''' | ||
| − | |||
| − | |||
| − | |||
= Venue = | = Venue = | ||
<font size=2pt> | <font size=2pt> | ||
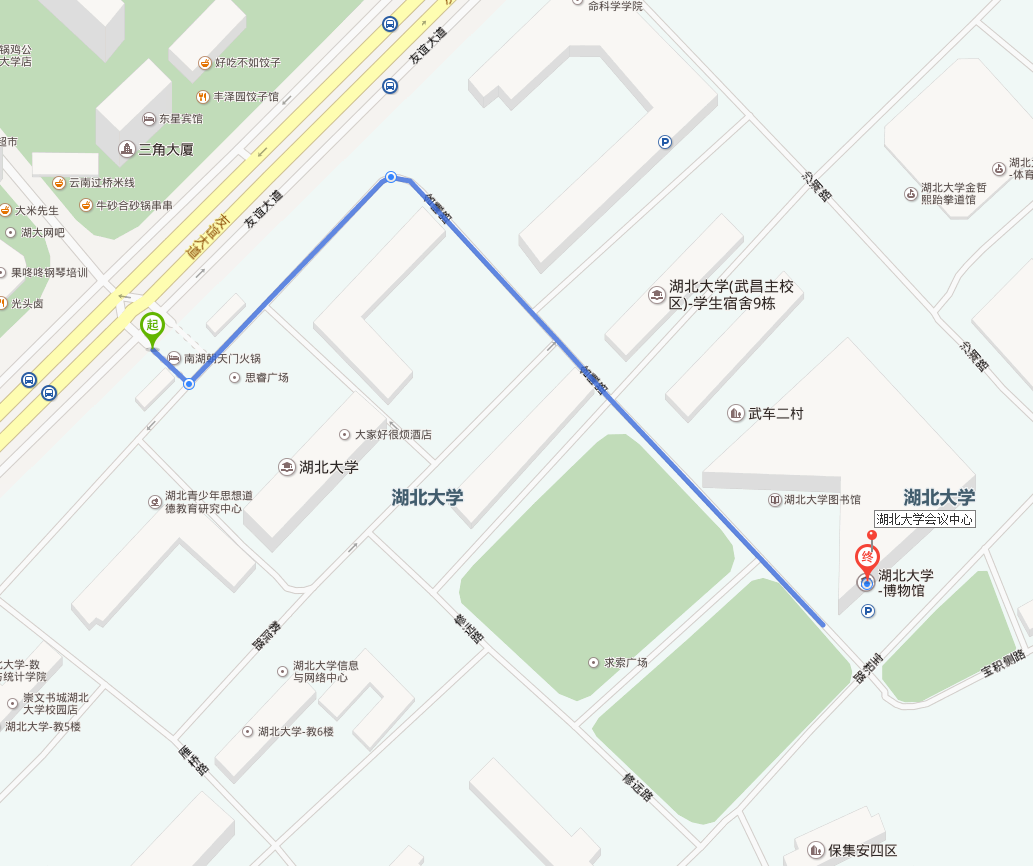
| − | AppSec | + | AppSec ASIA 2016 will be held at Hubei University, Wuhan, in China. |
| − | |||
| − | |||
| − | |||
| + | ==Hubei University== | ||
| − | + | Conference Center of HUBEI University | |
| + | Address: No.368 Youyi Avenue, Wuchang District, Wuhan, Hubei Province | ||
| − | |||
| − | |||
| − | |||
| + | https://www.owasp.org/images/3/31/Hubei_University.jpg | ||
| + | [[File:78380334258971128.png]] | ||
= Sponsoring = | = Sponsoring = | ||
<font size=2pt> | <font size=2pt> | ||
| − | We are looking for sponsors for | + | We are looking for sponsors for AppSec ASIA 2016. |
| − | |||
| − | |||
| + | If you are interested to sponsor AppSec ASIA 2016, please contact the conference team:[mailto:[email protected] [email protected]] | ||
| − | '''Sponsorship Deadline is | + | '''Sponsorship Deadline is April 10, 2016.''' |
| − | To find out more about the different sponsorship opportunities please check the document below: <br> | + | To find out more about the different sponsorship opportunities please check the document below: <br> |
| − | [https://www.owasp.org/images/ | + | [https://www.owasp.org/images/4/43/OWASP_AppSec_ASIA_2016_Sponsorship_.pdf OWASP AppSec ASIA 2016 Sponsorship] <br> |
| − | <br> | ||
| + | ===___Gold Sponsor___=== | ||
| − | |||
| + | [[File:百度2.png]] [[File:542523505630455198.jpg]] [[File:小的.png]] | ||
= Travel and Accommodation = | = Travel and Accommodation = | ||
<font size=2pt> | <font size=2pt> | ||
| − | + | ==Airport Transportation== | |
| − | |||
| − | |||
| − | |||
| − | |||
| + | Wuhan Tianhe International Airport | ||
| − | + | ==Hotel== | |
| + | Galllery. F Hotel 玉丰国际酒店 | ||
| + | Address: Wuhan Central Cultural District of Wuhan City Second District Shochiku Road No.8, 430071<br> | ||
| + | 地址:武汉中央文化区-楚河汉街第二街区,松竹路8号,430071 | ||
| − | + | Tel: +86 027 8733 7999 | |
| + | = Supporting Organization = | ||
| − | |||
| − | + | [[File:888276149172680378.png]][[File:415120780601494188小.png]] | |
| − | + | = Team = | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<font size=2pt> | <font size=2pt> | ||
| − | == | + | ==AppSec ASIA 2016 Conference Planning Team== |
| − | + | * Miya Xu | |
| − | + | * Ivy Zhang | |
| − | + | * Xiaoli Tan | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | '''Do you want to volunteer for AppSec ASIA 2016?'''[mailto:2016@owasp.org.cn Conference Planning Team] | |
| − | + | ==AppSec ASIA 2016 Volunteer Team== | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | * Ankit Giri | ||
| + | * Samit Anwer | ||
==OWASP Staff Support== | ==OWASP Staff Support== | ||
| − | * | + | * Laura Grau |
| − | |||
* Kelly Santalucia | * Kelly Santalucia | ||
* Kate Hartmann | * Kate Hartmann | ||
| − | * | + | * Noreen Whysel |
| − | Contact us at [mailto: | + | Contact us at [mailto:2016@owasp.org.cn Conference Planning Team] |
| + | |||
</font> | </font> | ||
<headertabs /> | <headertabs /> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 02:59, 6 May 2016
| |
|
|---|---|

|
- Welcome
- CFP
- Schedule
- Speaker Bios
- Training
- Registration and Fees
- Venue
- Sponsoring
- Travel and Accommodation
- Supporting Organization
- Team
|
APPSEC ASIA 2016
Call for Paper
OWASP AppSec ASIA 2016 will bring together application security experts and software engineers from all over the world on May 21, 2016. Industry and academia meet to discuss open problems and new solutions in web & mobile security. For this event, we will invite application security researchers, thought leaders and developers worldwide to submit papers for presentations looking for “the next”, cutting edge research in the context of web applications, secure development, security management and privacy. Don't miss the opportunity to share and discuss your ideas and knowledge with other experts and practitioners.
The topics of interest, but not limited:
- Web Security
- Mobile Security
- Cloud Security, specifically secure Cloud Apps
- Infrastructure security
- Secure development
- Application Security Testing
- Privacy protection in web based apps
- Emerging web technologies and associated security considerations
- Security Trainings, Certificates and CTP
Papers should describe new ideas, new implementations, or experiences related to web & mobile security. We are glad to have some leading-edge topics and ideas as well as in-depth discussion in the conference. The conference planning team will review your submission based on a descriptive abstract of your intended presentation. Feel free to attach a preliminary version of your presentation if available, or any other supporting materials. Remember: the better your description is, the better our review will be.
Important dates:
Submission deadline: Mar 25, 2016.
Notification of acceptance: Mar 31, 2016.
Presentation PPT due: April 30, 2016.
To submit a proposal please use easy chair https://easychair.org/conferences/?conf=appsecasia2016wuhanc
To contact the conference planning team, please mail to [email protected][1]
OWASP Speaker Agreement: https://www.owasp.org/index.php/Speaker_Agreement
Likely we can cover travel expenses or costs for accommodations.
Terms
By your submission you agree to the OWASP Speaker Agreement. OWASP values vendor neutrality. You need to use the OWASP presentation template and you’re not allowed to place marketing pitches in your slides. All presentation slides will be published on the conference website after the conference. Please make sure that any pictures and other materials in your slides don’t violate any copyrights. You are solely liable for copyright violations. You may choose any CC license for your slides, including CC0. OWASP does suggest open licenses.
| Schedule |
Duration |
Topic |
Venue |
| 9:00-9:15 | 15 | Opening speech | 主会场 |
| 9:15-9:45 | 30 | OWASP Mobile 2016 & Self-healing apps
Milan Singh Thakur |
主会场 |
| 9:45-10:15 | 30 | Testing next-gen iOS apps
Prateek Gianchandani |
主会场 |
| 10:15-10:30 | 15 | Coffee & Tea Break | 大厅 |
| 10:30-11:00 | 30 | Big problems with big data - Hadoop interfaces security
Jakub Kaluzny |
主会场 |
| 11:00-11:30 | 30 | OWASP CISO Survey Report – Tactical Insights for Managers
Tobias Gondrom |
主会场 |
| 11:30-12:00 | 30 | OWASP Top 10: Effectiveness of Web Application Firewalls
David Caissy |
主会场 |
| 12:00-14:00 | 120 | LUNCH | N/A |
| 14:00-14:30 | 30 | Android硬件隔离及指纹应用的安全研究
顾凌志 |
主会场 |
| 14:30-15:00 | 30 | Cloud-ids:智能Web 入侵检测与威胁感知
刘焱 |
主会场 |
| 15:00-15:30 | 35 | 企业AppLayer面临的IT安全风险与危机
Dixon Ho |
主会场 |
| 15:30-15:50 | 20 | Coffee & Tea Break | 大厅 |
| 15:50-16:20 | 30 | 无人车安全剖析
云朋 |
主会场 |
| 16:20-16:50 | 30 | Engineering better security
Collin Chang |
主会场 |
| 16:50-17:20 | 30 | 移动互联网应用的服务端安全防护探讨
权小文 |
主会场 |
| 14:00-14:40 | 40 | Capture-the-Flag Secrets
Ivan Butler |
人才培养分论坛 |
| 14:40-15:15 | 35 | 高校源代码安全教育初探
张䶮 |
人才培养分论坛 |
| 15:15-15:50 | 35 | 新型安全人才培养模式
Rip |
人才培养分论坛 |
| 15:50-16:10 | 20 | Coffee & Tea Break | 大厅 |
| 16:10-16:45 | 35 | 从软件工程师到软件安全经理
王文君 |
人才培养分论坛 |
| 16:45-17:20 | 10 | 信息安全高端人才培养实践
张绍浪 |
人才培养分论坛 |
| 17:20-17:30 | 10 | Closing speech | 主会场 |
Milan Singh Thakur
- OWASP Mobile 2016 & Self-healing apps
- 主会场
Milan is very passionate about Information Security and an International Speaker. He is leading OWASP Mobile Security Project Globally under which Mobile Appsec Guide, Checklist and various Cheatsheets are being developed. He also works as Information Security Consultant for a private firm in India. His primary focus is Mobile Security. He has helped to secure mobile apps for various well known clients in banking, insurance, health, e-commerce and other sectors. Recently he has done PT for Apple iWatch for a client. He has expertise in fields like secure code review, NFC Pentesting, Web Appsec, VAPT activities, Wireless Pentesting, Payment Gateway Security Assessments and lot more. His scope of exploration is not limited to these technologies. He is strong supporter of “Open-Source” terminology and has been promoting it since 2010.
Prateek Gianchandani
- Testing next-gen iOS apps
- 主会场
An OWASP member and contributor has been working in the infosec industry for over 5 years. During his five years, he has performed a number of penetration tests on mobile and web applications and even developed a lot of applications for the App Store. His core focus area is mobile pentesting and embedded device hacking. He is also the author of the open source vulnerable application named Damn Vulnerable iOS app. He has presented and trained at Conferences like Defcon, Blackhat USA, Brucon, Hack in paris, Phdays etc.
Jakub Kaluzny
- Big problems with big data - Hadoop interfaces security
- 主会场
A Senior IT Security Consultant at SecuRing and performs penetration tests of high-risk applications, systems and devices. He was a speaker at many international IT Security conferences: OWASP AppSec EU, BlackHat Asia, PHdays, CONFidence, HackInTheBox AMS, as well at local events. Previously working for European Space Agency and internet payments intermediary. Apart from testing applications, he digs into proprietary network protocols, embedded devices and other enterprise solutions.
Tobias Gondrom
- OWASP CISO Survey Report 2015 – Tactical Insights for Managers
- 主会场
CTO Security for global IT company. Chairman of the Board of OWASP, Chair of the IAOC. Experience asHead of Information Security, Chief Information Security Officer, CISO, IT Risk Management, Governance & Compliance Head of Software Development, CTO, Manage in global, multinational and complex organisations, Change Management, project management, M&A, Strategy, ArchitectureSDLC, Software development processes and standards CCISO, CISSP, CSSLP.
David Caissy
- OWASP Top 10: Effectiveness of Web Application Firewalls
- 主会场
David Caissy, M. Sc., OSCP, GWAPT, GPEN, GSEC, CISSP, CEH is a web application penetration tester with in-depth developer and IT Security background spanning over 16 years. He has extensive experience in conducting vulnerability assessments and penetration tests as well as providing training globally, amongst numerous other teaching engagements. He has worked for a central bank, various government agencies and private companies. David has been teaching web application security in colleges, conferences and for many government agencies over the last 15 years.
顾凌志
- Android硬件隔离及指纹应用的安全研究
- 主会场
华为资深安全专家,华为SDL应用创始人之一,擅长安全架构设计、威胁建模;长期从事移动、虚拟化及通信领域业务安全的分析和研究。
刘焱
- Cloud-ids:智能Web 入侵检测与威胁感知
- 主会场
百度云安全部资深架构师刘焱,毕业于华中科技大学,具有近十年 bat级互联网公司甲方安全防护经验,主持或者参与了百度内部几乎全部安全监控以及防护项目,黑客入侵主动发现比例超过80%;具有多项国家信息安全专利;在国内外学术期刊、会议发表多篇论文;主持开发的安全产品在十多家国内外中大型互联网企业中使用。
Dixon Ho
- 企业AppLayer面临的IT安全风险与危机
- 主会场
为ISACA北京事务委员会主席、中国信息化推进联盟信息安全专业委员会副主任,主管微软大中华区信息安全领域超过8年。在2008年担任了北京市市政管理委员会奥运城市运行指挥平台安全顾问。 信息安全领域从业时间:近20多年。
云朋
- 无人车安全剖析
- 主会场
常颢Collin.Chang
- Engineering better security
- 主会场
35岁,居于上海。现就职于Raid7。毕业于复旦大学,有12年的安全经验。曾在Venustech、 McAfee、TippingPoint(HP ESP) 以及 PaloAlto Networks工作过。他也是一个PMP, 参与过中国东部的一些大项目。熟悉Anti-virus 、IPS/IDS、NGFW、脆弱性管理解决方案。
权小文
1978年,陕西人,毕业于清华大学,获得硕士学位,2005年获得高级工程师职称,拥有4年大型国企技术和管理经验,6年跨国公司技术和管理从业经验,5年国内创业经验,15年信息安全从业经验,获得5项网络安全相关的发明专利,18项软件著作权,参与国家重大科研专项6项,参与一项网络安全相关国标制定;主要从事信息安全产品研发、技术管理、产品线管理等工作。主持开发的Web安全系列产品,占有国内30%以上市场份额,并且出口到美国、印度、迪拜等国家。创建的远江盛邦(北京)网络安全科技股份有限公司,已经申报全国股转系统,并在2016年4月14日正式挂牌新三板。
Ivan Butler
- Capture-the-Flag Secrets
- 人才培养分论坛
Founder and CEO of Compass Security, a leading Swiss ethical hacking and penetration testing company. Speaker @ BlackHat Las Vegas 2008, IT Underground Warsaw 2009, Unistrategic Singapore 2010 and organizer of Swiss Cyber Storm Security Conference since 2007.
张
- 高校源代码安全教育初探
- 人才培养分论坛
Rip
- 新型安全人才培养模式
- 人才培养分论坛
Leader of OWASP China.
王文君
- 从软件工程师到软件安全经理
- 人才培养分论坛
HP Enterprise Software全球安全技术主管,负责年营业额10亿美元的软件产品线的总体安全,以及SDL(软件安全开发流程)在公司内部的实施。OWASP上海分会负责人,CWASP资深讲师,拥有CSSLP和CISSP认证,是《Web应用安全威胁与防治》的作者之一。
张绍浪
- 信息安全高端人才培养实践
- 人才培养分论坛
从事信息安全13年,多年来一直从事信息安全产品的研发和产业化,熟悉国内外的网络安全技术,北京易霖博信息技术创史人,红客训练营创史人,公司13年成立,在其带领下从公司三五人目前已经成长为50人的团队其中研发人员35人,承担国家级比赛及省赛数十项。
| Course Name |
Trainer |
Course Length |
Course Date(s) |
Language |
Price |
| OWASP Top 10 Effective Safeguards | David Caissy | 4H | May20,8:30-12:00 | English | RMB 1500 |
| Mobile Application security | Prateek Gianchandani | 4H | May20,14:30-18:30 | English | RMB 1500 |
Note
- Price per attendee.
- 15% off for OWASP Senior Member
- 15% off for groups of above 10
- Conference Registration is separate.
Conference
Free for OWASP China Member.
Link to http://m.vcooline.com/app/activity_enrolls/new?aid=2569906&wxmuid=24361
Training
Mail to [email protected] for training registration.
Please note that conference and training Registration is separate.
We are looking for sponsors for AppSec ASIA 2016.
If you are interested to sponsor AppSec ASIA 2016, please contact the conference team:[email protected]
Sponsorship Deadline is April 10, 2016.
To find out more about the different sponsorship opportunities please check the document below:
OWASP AppSec ASIA 2016 Sponsorship
___Gold Sponsor___
Airport Transportation
Wuhan Tianhe International Airport
Hotel
Galllery. F Hotel 玉丰国际酒店
Address: Wuhan Central Cultural District of Wuhan City Second District Shochiku Road No.8, 430071
地址:武汉中央文化区-楚河汉街第二街区,松竹路8号,430071
Tel: +86 027 8733 7999
AppSec ASIA 2016 Conference Planning Team
- Miya Xu
- Ivy Zhang
- Xiaoli Tan
Do you want to volunteer for AppSec ASIA 2016?Conference Planning Team
AppSec ASIA 2016 Volunteer Team
- Ankit Giri
- Samit Anwer
OWASP Staff Support
- Laura Grau
- Kelly Santalucia
- Kate Hartmann
- Noreen Whysel
Contact us at Conference Planning Team