This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP KeyBox"
(→FAQs) |
(→FAQs) |
||
| Line 78: | Line 78: | ||
::keytool -keystore keystore -import -alias jetty -file mycert.crt | ::keytool -keystore keystore -import -alias jetty -file mycert.crt | ||
::then just replace the keystore in the jetty/etc/ directory and you set the passwords in the jetty/modules/ssl.mod file (see [http://www.eclipse.org/jetty/documentation/current/configuring-security-secure-passwords.html Configuring Security Secure Passwords] to set the password format) | ::then just replace the keystore in the jetty/etc/ directory and you set the passwords in the jetty/modules/ssl.mod file (see [http://www.eclipse.org/jetty/documentation/current/configuring-security-secure-passwords.html Configuring Security Secure Passwords] to set the password format) | ||
| − | ::More information can be found at | + | ::More information can be found at [http://wiki.eclipse.org/Jetty/Howto/Configure_SSL How to Configure SSL] |
Revision as of 11:18, 29 March 2015
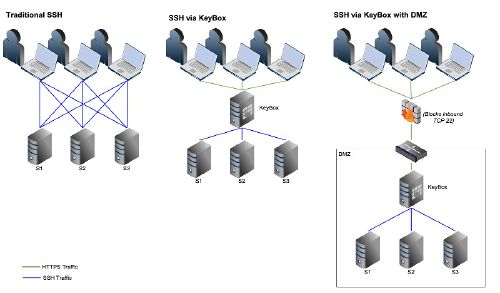
OWASP KeyBox ProjectKeyBox is a web-based SSH console that centrally manages administrative access to systems. It combines key management and administration through profiles assigned to defined users. KeyBox layers TLS/SSL on top of SSH and can act as a bastion host. DescriptionKeyBox is a web-based SSH console that centrally manages administrative access to systems. KeyBox combines key management and administration through profiles assigned to defined users. Administrators can login using two-factor authentication with FreeOTP or Google Authenticator . From there they can create and manage public SSH keys or connect to their assigned systems through a web-shell. Commands can be shared across shells to make patching easier and eliminate redundant command execution. KeyBox layers TLS/SSL on top of SSH and acts as a bastion host for administration. Protocols are stacked (TLS/SSL + SSH) so infrastructure cannot be exposed through tunneling / port forwarding. More details can be found in the following whitepaper: The Security Implications of SSH. Also, SSH key management is enabled by default to prevent unmanaged public keys and enforce best practices. Licensing |
DownloadProject LeaderLinksClassifications
|
News and Events
| ||||||
- How do I import my own SSL cert?
- keytool -keystore keystore -import -alias jetty -file mycert.crt
- then just replace the keystore in the jetty/etc/ directory and you set the passwords in the jetty/modules/ssl.mod file (see Configuring Security Secure Passwords to set the password format)
- More information can be found at How to Configure SSL
- I have a reverse-proxy that already terminates TLS/SSL, how do I disable TLS/SSL?
- In the jetty directory edit the start.ini file and set
- --module=https
- to
- --module=http
- and change jetty.port=8443 to the needed port to be and restart. More information on jetty can be found - Jetty Documentation
Road Map
Add ability to save session and command line information to a large data store so it can be audited and reviewed. Compute and flag irregularities that could point security issues or improper use. Deploy to embedded network devices to act as a proxy for SSH connections.
Getting Involved
Currently packaged along with a web-server and can be downloaded from github
https://github.com/skavanagh/KeyBox/releases