This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Testing for IMAP/SMTP Injection (OTG-INPVAL-011)"
(→Short Description of the Issue (Topic and Explanation)) |
(→Short Description of the Issue (Topic and Explanation)) |
||
| Line 9: | Line 9: | ||
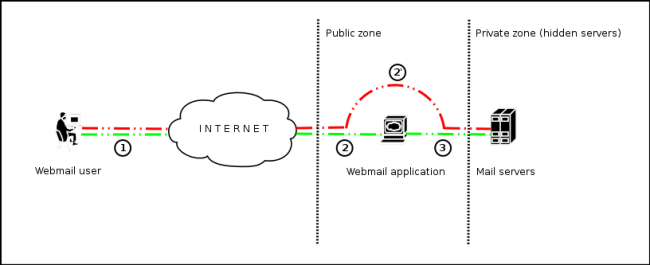
This technique facilitate that, mail servers that could not be accessibles directly from Internet, and then be not so secured and updated, become visibles and accessibles publicly to Internet users/attackers (see the scheme presented in Figure 1). | This technique facilitate that, mail servers that could not be accessibles directly from Internet, and then be not so secured and updated, become visibles and accessibles publicly to Internet users/attackers (see the scheme presented in Figure 1). | ||
| + | |||
<center>[[Image:imap-smtp-injection.png]] | <center>[[Image:imap-smtp-injection.png]] | ||
| + | |||
Figure 1 - Communication with the mail servers using the IMAP/SMTP Injection technique.</center> | Figure 1 - Communication with the mail servers using the IMAP/SMTP Injection technique.</center> | ||
Revision as of 18:38, 1 November 2006
OWASP Testing Guide v2 Table of Contents
Short Description of the Issue (Topic and Explanation)
This threat affect all those applications that they communicate with mail servers (IMAP/SMTP), generally webmail applications.
The aim of this test is to verify the capacity to inject arbitrary IMAP/SMTP commands into the mail servers with that one communicates the web application, due to input data that they have not been sanitized correctly.
The IMAP/SMTP Injection technique is really useful if the mail servers, which the webmail application communicates, are not directly accessible from Internet. In other cases, this technique is nonsense and results more practise do a direct connection to those servers, without using the webmail applications.
This technique facilitate that, mail servers that could not be accessibles directly from Internet, and then be not so secured and updated, become visibles and accessibles publicly to Internet users/attackers (see the scheme presented in Figure 1).
Black Box testing and example
Testing for Topic X vulnerabilities:
...
Result Expected:
...
Gray Box testing and example
Testing for Topic X vulnerabilities:
...
Result Expected:
...
References
Whitepapers
...
Tools
...
OWASP Testing Guide v2
Here is the OWASP Testing Guide v2 Table of Contents OWASP Testing Guide v2 Table of Contents
This article is a stub. You can help OWASP by expanding it or discussing it on its Talk page.