This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Defenders"
From OWASP
(Created page with "==== OWASP Defenders ==== {| width="100%" |- ! width="66%" | ! width="33%" | |- valign="top" | '''Defenders Community''' A community of security professionals and stakehol...") |
|||
| Line 2: | Line 2: | ||
{| width="100%" | {| width="100%" | ||
| − | |||
| − | |||
| − | |||
|- valign="top" | |- valign="top" | ||
| | | | ||
'''Defenders Community''' | '''Defenders Community''' | ||
| − | A community of security professionals and | + | A community of security professionals and stakeholders with the common goal of advancing the state of security in the area of application defense, including the tools and techniques that enable the detection and response to application layer attacks. |
| − | |||
| − | '''Examples''' | + | <br> '''Examples''' |
AppSensor, ModSecurity, Real Time Log Analysis, Application Trending Techniques | AppSensor, ModSecurity, Real Time Log Analysis, Application Trending Techniques | ||
| − | + | <br> '''Target Audience''' | |
| − | '''Target Audience''' | ||
Application Security Professionals, Infrastructure Security Teams, Developers looking to integrate defensive technologies | Application Security Professionals, Infrastructure Security Teams, Developers looking to integrate defensive technologies | ||
| | | | ||
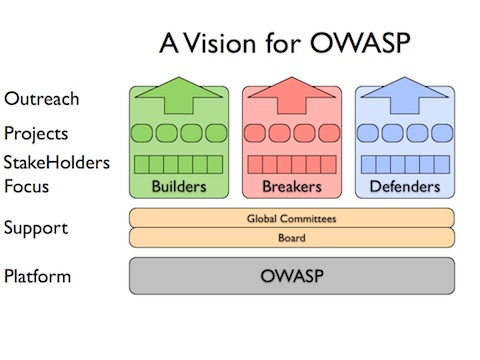
| − | [[Image: | + | [[Image:OWASP-vision.jpg]] |
|} | |} | ||
| Line 28: | Line 23: | ||
==== The Community ==== | ==== The Community ==== | ||
| − | ==== | + | <br> |
| + | |||
| + | {| cellspacing="1" cellpadding="1" style="width: 404px; height: 413px;" | ||
| + | |- | ||
| + | | [[Image:MichaelCoates-OWASP.jpg]] <br> | ||
| + | | '''Michael Coates''' <br> Mozilla <br> [email protected] <br> http://michael-coates.blogspot.com <br> @_mwc | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | [[Image:JohnMelton-OWASP.jpg]] <br> | ||
| + | | '''John Melton''' <br> Wells Fargo <br> [email protected] <br> http://www.jtmelton.com <br> | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | [[Image:IvanRistic-OWASP.jpg]] <br> | ||
| + | | '''Ivan Ristic''' <br> Qualys <br> [email protected] <br> http://blog.ivanristic.com/ <br> @ivanristic | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | [[Image:ColinWatson-OWASP.jpg]] <br> | ||
| + | | '''Colin Watson''' <br> Watson Hall Ltd. <br> [email protected] <br> http://www.clerkendweller.com <br> @clerkendweller | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | [[Image:RyanBarnett-OWASP.jpg]] <br> | ||
| + | | '''Ryan Barnett'''<br> Trustwave <br> [email protected] <br> http://tacticalwebappsec.blogspot.com/ <br> @ryancbarnett | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | | ||
| + | | '''Chen King'''<br> <br> <br> | ||
| + | | | ||
| + | | | ||
| + | |- | ||
| + | | | ||
| + | | '''Fernando A. Damião'''<br> <br> <br> | ||
| + | | | ||
| + | | | ||
| + | |} | ||
| + | |||
| + | <br> | ||
| + | |||
| + | ==== Roadmap ==== | ||
| + | *Determine the current market need. This requires involvement from people in enterprise that are tacking these problems. No guessing about what we think people need. | ||
| + | *Evaluate current OWASP projects to understand match with market need and quality of projects | ||
| + | *Identify 3-4 projects that will be focused on for growth and promotion | ||
| + | *Archive other projects that are abandoned or not inline with market need | ||
| + | *Cross training - We should all be able to help out to advance our 3-4 core projects | ||
| + | |||
| + | ==== Official Defender Projects ==== | ||
| + | |||
| + | To be determined - see roadmap | ||
__NOTOC__ <headertabs /> <br> | __NOTOC__ <headertabs /> <br> | ||
Revision as of 04:38, 23 February 2011
OWASP Defenders
|
Defenders Community A community of security professionals and stakeholders with the common goal of advancing the state of security in the area of application defense, including the tools and techniques that enable the detection and response to application layer attacks.
AppSensor, ModSecurity, Real Time Log Analysis, Application Trending Techniques
Application Security Professionals, Infrastructure Security Teams, Developers looking to integrate defensive technologies |
The Community
 |
Michael Coates Mozilla [email protected] http://michael-coates.blogspot.com @_mwc |
||
 |
John Melton Wells Fargo [email protected] http://www.jtmelton.com |
||
 |
Ivan Ristic Qualys [email protected] http://blog.ivanristic.com/ @ivanristic |
||
 |
Colin Watson Watson Hall Ltd. [email protected] http://www.clerkendweller.com @clerkendweller |
||
 |
Ryan Barnett Trustwave [email protected] http://tacticalwebappsec.blogspot.com/ @ryancbarnett |
||
| Chen King |
|||
| Fernando A. Damião |
Roadmap
- Determine the current market need. This requires involvement from people in enterprise that are tacking these problems. No guessing about what we think people need.
- Evaluate current OWASP projects to understand match with market need and quality of projects
- Identify 3-4 projects that will be focused on for growth and promotion
- Archive other projects that are abandoned or not inline with market need
- Cross training - We should all be able to help out to advance our 3-4 core projects
Official Defender Projects
To be determined - see roadmap