This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Why you need to use a FIPS 140-2 validated cryptomodule"
| Line 1: | Line 1: | ||
| − | If you are performing an application security verification according to the [[Category:OWASP_Application_Security_Verification_Standard_Project |OWASP Application Security Verification Standard (ASVS)]] verification requirements, you will need to make sure that any cryptographic functions are being performed by a FIPS 140-2 validated cryptomodule. | + | If you are performing an application security verification according to the [[::Category:OWASP_Application_Security_Verification_Standard_Project |OWASP Application Security Verification Standard (ASVS)]] verification requirements, you will need to make sure that any cryptographic functions are being performed by a FIPS 140-2 validated cryptomodule. |
Latest revision as of 12:24, 29 March 2009
If you are performing an application security verification according to the OWASP Application Security Verification Standard (ASVS) verification requirements, you will need to make sure that any cryptographic functions are being performed by a FIPS 140-2 validated cryptomodule.
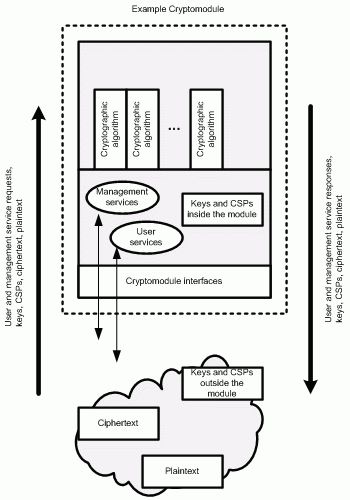
A cryptomodule, whether it is a software library or a hardware device, basically consists of three parts:
- Components that implement cryptographic algorithms (symmetric and asymmetric algorithms, hash algorithms, random number generator algorithms, and message authentication code algorithms)
- Components that call and manage cryptographic functions (inputs and outputs include cryptographic keys and so-called critical security parameters)
- A physical container around the components that implement cryptographic algorithms and the components that call and manage cryptographic functions
The security of a cryptomodule and its services depends on the correct implementation and integration of each of these three parts. While most folks understand that implementing cryptographic algorithms correctly is a hard thing to do, most do not understand that calling and managing cryptographic functions and their inputs and outputs, and ensuring the secure construction of the physical container around the components, are equally important in determining the security of a cryptomodule and its services.
Using a FIPS 140-2 validated cryptomodule provides a greater chance that the cryptomodule is providing the services that you are expecting from it.
References: