This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Testing for DB Listener (OWASP-CM-002)"
m (→References) |
|||
| Line 85: | Line 85: | ||
== References == | == References == | ||
'''Whitepapers'''<br> | '''Whitepapers'''<br> | ||
| − | ...<br> | + | * Oracle Database Listener Security Guide - http://www.integrigy.com/security-resources/whitepapers/Integrigy_Oracle_Listener_TNS_Security.pdf<br> |
'''Tools'''<br> | '''Tools'''<br> | ||
* TNS Listener tool (Perl) - http://www.jammed.com/%7Ejwa/hacks/security/tnscmd/tnscmd-doc.html<br> | * TNS Listener tool (Perl) - http://www.jammed.com/%7Ejwa/hacks/security/tnscmd/tnscmd-doc.html<br> | ||
Revision as of 15:48, 23 November 2006
[Up]
OWASP Testing Guide v2 Table of Contents
Brief Summary
The Data base listener is a network daemon unique to Oracle databases. It waits for connection requests from remote clients. This daemon can be compromised and hence affect the availability of the database.
Description of the Issue
The DB listener is the entry point for remote connections to an Oracle database. It listens for connection requests and handles them accordingly. This test is possible, if the tester can access to this service: that means the test should be done from the Intranet (major Oracle installation don't expose this service to the external network).
The listener by default listens on port 1521(port 2483 is the new officially registered port for the TNS Listener and 2484 for the TNS Listener using SSL), it is good practice to change the listener from this port to another arbitrary port number.
If this listener is "turned off" remote access to the database is not possible. If this is the case ones application would fail also creating a denial of service attack.
Potential areas of attack:
- Stop the Listener - Hence creating a DoS attack.
- Set a password and prevent others from controlling the Listener - Hijack the DB.
- Write trace and log files to any file accessible to the process owner of tnslnsr (usually Oracle) - Possible information leakage.
- Obtain detailed information on the Listener, database, and application configuration.
Black Box testing and example
Upon discovering the port on which the listener resides one can assess the listener by running a tool developed by Integrigy:
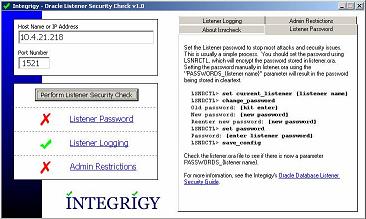
The tool above checks the following:
Listener Password
On many Oracle systems the listener password may not be set. The tool above verifies this.
If the password is not set an attacker could set the password and hijack the listener, albeit the password can be removed by locally editing the Listener.ora file.
Enable Logging
The tool above also tests to see if logging has been enabled. If it has not one would not detect any change to the listener/or have a record of it and also detection of brute force attacks on the listener would not be audited.
Admin Restrictions
If Admin restrictions are not enabled it is possible to use the "SET" commands remotely.
Example
If you find a TCP/1521 open port on a server, maybe you have an Oracle Listener that accepts connections from the outside. If the listener is not protected by an authentication mechanism, or you can find easily a credential (as said above), it is possible to exploit this vulnerability to enumerate the Oracle services. For example, using LSNRCTL(.exe) (contained in every Client Oracle installation), you can obtain the following output:
TNSLSNR for 32-bit Windows: Version 9.2.0.4.0 - Production TNS for 32-bit Windows: Version 9.2.0.4.0 - Production Oracle Bequeath NT Protocol Adapter for 32-bit Windows: Version 9.2.0.4.0 - Production Windows NT Named Pipes NT Protocol Adapter for 32-bit Windows: Version 9.2.0.4.0 - Production Windows NT TCP/IP NT Protocol Adapter for 32-bit Windows: Version 9.2.0.4.0 - Production,, SID(s): SERVICE_NAME = CONFDATA SID(s): INSTANCE_NAME = CONFDATA SID(s): SERVICE_NAME = CONFDATAPDB SID(s): INSTANCE_NAME = CONFDATA SID(s): SERVICE_NAME = CONFORGANIZ SID(s): INSTANCE_NAME = CONFORGANIZ
The Oracle Listener permits to enumerate default users on Oracle Server:
User name Password OUTLN OUTLN DBSNMP DBSNMP BACKUP BACKUP MONITOR MONITOR PDB CHANGE_ON_INSTALL
In this case, we have not founded privileged DBA accounts, but OUTLN and BACKUP accounts hold a fundamental privilege: EXECUTE ANY PROCEDURE. That means that it is possible to execute all procedures, for example the following:
exec dbms_repcat_admin.grant_admin_any_schema('BACKUP');
The execution of this command permit to obtain DBA privileges. Now the user can interact directly with the DB and execute for example:
select * from session_privs ;
The output is the following screenshot:
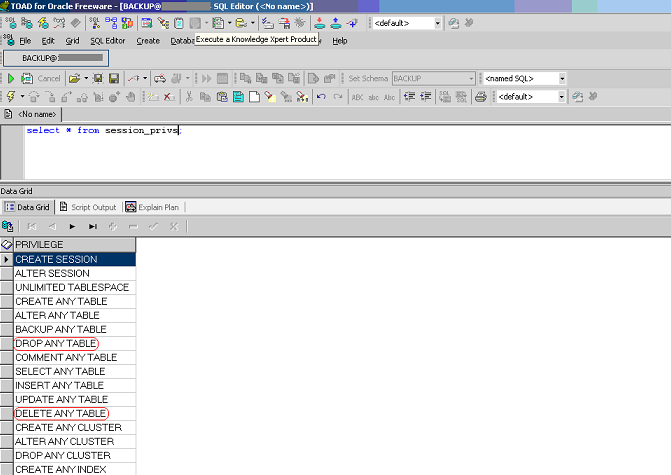
So the user can now execute a lot of operations, in particular: DELETE ANY TABLE DROP ANY TABLE.
Gray Box testing and example
Testing for Topic X vulnerabilities:
...
Result Expected:
...
References
Whitepapers
- Oracle Database Listener Security Guide - http://www.integrigy.com/security-resources/whitepapers/Integrigy_Oracle_Listener_TNS_Security.pdf
Tools
- TNS Listener tool (Perl) - http://www.jammed.com/%7Ejwa/hacks/security/tnscmd/tnscmd-doc.html
- Toad for Oracle - http://www.quest.com/toad
OWASP Testing Guide v2
Here is the OWASP Testing Guide v2 Table of Contents