This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Summit 2011"
Sarah Baso (talk | contribs) m (Reverted edits by Frank Alexander (talk) to last revision by Paulo Coimbra) |
|||
| Line 1: | Line 1: | ||
| − | + | {| | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | {| | ||
|- | |- | ||
| − | + | ! width="600" align="center" | | |
| − | + | ! width="600" align="center" | | |
|- | |- | ||
| − | | | + | | align="center" | [[Image:Final summit logo half.jpg|link=http://www.owasp.org/index.php/Summit_2011_Logo_Explained]] <br/> |
| − | + | | align="left" | | |
| − | |- | + | *[[Summit 2011/Open letter to WebAppSec Tool and Services vendors: Release your schemas and allow automation|Open letter to WebAppSec Tool and Services vendors]] |
| − | | | + | *[http://www.twitter.com/OWASPSummit http://twitter-badges.s3.amazonaws.com/twitter-a.png]<br> |
| − | + | *[[Summit 2011/Media|PRESS RELEASES & Media Mentions]]<br/> | |
| − | | | + | *[[Summit 2011 Attendee|Who is going?]]<br/> |
| − | | | + | *[[Summit 2011/Venue|Where is the venue?]]<br/> |
| − | | | + | *[[Summit_2011_Reservations|Tickets/Reservations]]<br/> |
| − | + | *[[Summit_2011_Corporate_Sponsorship|How can I become a corporate sponsor?]]<br/> | |
| + | *[[Summit_2011_FAQ|Other Frequently Asked Questions]]<br/> | ||
| + | *[[Summit_2011/Emails_To_Attendees|Emails to Attendees]]<br/> | ||
| + | *[[:Category:Summit 2011 Tracks|Summit 2011 Working Sessions]]<br/> | ||
| + | [[Image:REGISTER NOW SUMMIT 2011.jpg|link=http://www.regonline.com/owasp_global_summit_2011]]<br> | ||
| + | *[https://spreadsheets.google.com/viewform?formkey=dEptc1BoTVJSQkxBSDhhNHdSaEN1Y3c6MQ If you can't attend in person, register here for remote participation] | ||
| + | *[http://www.owasp.org/index.php/Summit_2011/Remote_Participants#Remote_Participants Video Broadcast Channels] | ||
| + | <paypal>Summit</paypal> | ||
| + | *[[Summit_2011_Archived|Summit 2011 Archived]]<br/> | ||
|} | |} | ||
| − | + | ==== Welcome! ==== | |
| − | |||
| − | |||
| − | |||
| − | == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | {{#ev:youtube|Yc7Jo8yeh0g}} | |
| − | + | ==== Creating OWASP 4.0! ==== | |
| + | {{:Summit_2011_Creating_OWASP_4dotOh}} | ||
| − | + | ==== Fixed Schedule ==== | |
| + | [[:Summit_2011_Schedule|Click HERE to view the entire summit fixed schedule. This is just a sample.<br/>]] | ||
| + | [[Image:Agenda Unvarying 2.jpg|link=Summit_2011_Schedule]] | ||
| − | + | ==== Dynamic Schedule ==== | |
| + | [[:Summit_2011_Schedule_Dynamic|Click HERE to view the entire summit dynamic schedule. This is just a sample<br/>]] | ||
| + | [[Image:Agenda Dynamic 2.JPG|link=Summit 2011 Schedule Dynamic]] | ||
| − | |||
| − | + | ==== Remote Participants ==== | |
| + | <br/> | ||
| + | [[:Summit_2011/Remote_Participants|Details on how to participate remotely are HERE.]] | ||
| − | + | __NOTOC__ | |
| + | <headertabs /> | ||
| + | *[[Summit 2011 Committee|Summit 2011 Committee]]<br/> | ||
| + | [[Category:Summit_2011]] | ||
Revision as of 21:41, 7 February 2011
Welcome!
Creating OWASP 4.0!
Call to action by Jeff Williams / OWASP Board Chair
Hi everyone,
In my mind, OWASP 1.0 was pre-wiki with lots of great work and a less great infrastructure. OWASP 2.0 was establishing the 501c3, putting in the wiki, and getting lots of great projects started. OWASP 3.0 started with the Summit in Portugal when we created the new committees and has focused on creating thriving projects instead of standalone tools. Thank you for all of your efforts growing a fun, civil, productive community.
I reach out to you now to ask you to take some time and think about what OWASP should become. The time has come to measure our success not by the number of members, projects, and conferences, but by whether we are succeeding at making the world’s software more secure. It’s time to get our message and strategy to the next level.
Help design OWASP in Portugal at the Summit!
If you consider yourself an OWASP Leader, won’t you take a few minutes of quiet time and propose a few ideas for how OWASP can retool, reorganize, refocus, and revamp itself to really achieve our mission? We will rip, mix, and burn these ideas into a new strategy for OWASP at the Portugal Summit. I encourage you to check out the resort and all the plans happening right now at https://www.owasp.org/index.php/Summit_2011.
Here are some ideas to get you started.
- We bootstrap several application security ecosystems around key technologies like mobile, cloud, REST
- We reach out to governments around the world to help them push for application security
- We raise money to fund real security enhancements to tools, browsers, protocols (e.g. OpenSSL)
- We make the OWASP materials more usable by providing a “user” site and keep the wiki for development
- We invest in marketing AppSec – How do we scale David Rice and the “greening” of AppSec
- We continue our education initiative – academies, college chapters, videos, curriculum
- We continue our browser initiative and do whatever it takes to get the browsers and frameworks talking
- We invest in getting in front of new technologies like HTML5
- We launch a no-holds barred XSS eradication campaign
- We create a set of objective AppSec *market* metrics that quantify the state of our art
- We continue to push on creating standards
- ???
We need your ideas NOW. Get yourself on the Attendee list!
In one week of thinking, arguing, coding, hacking, and writing we are going to accomplish more than the rest of the world’s appsec efforts combined. We’ll see you in Portugal ready to rock. Thanks!
--Jeff
OWASP Foundation Board Chair
Summit 2011 About
The OWASP Global Summit is the place where application security experts meet to discuss plans, projects and solutions for the future of application security. The Summit is not a conference - there are no talks or training seminars - this is an opportunity to do actual work to further the field of application security. Participants will stay in shared accommodations and collaborate to produce tangible progress towards influencing standards, establishing roadmaps, and setting the tone for OWASP and application security for the coming years.
The Summit will consist of working sessions across a variety of topics set by our community. Participants are free to attend any working session, but we encourage everyone to select working sessions for topics where they have the most to contribute.
Anyone can attend the Summit! OWASP community members, application security experts, industry players, and developers are all welcome at the Summit. If you would like to receive a personalized invitation for yourself or another person, see the promotional materials page.
Last Summit
This OWASP Global Summit is following the same model used at the OWASP EU Summit 08 which also took place in Portugal and gathered over 80 application security experts from over 20 countries. A smaller Summit 2009 was organized together with the AppSec US conference.
Fixed Schedule
Click HERE to view the entire summit fixed schedule. This is just a sample.
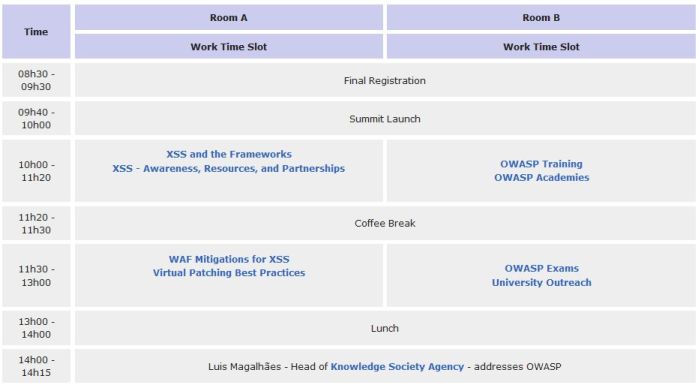
Dynamic Schedule
Click HERE to view the entire summit dynamic schedule. This is just a sample

Remote Participants
Details on how to participate remotely are HERE.


