This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Projects/OWASP Mobile Security Project - Top Ten Mobile Risks"
Jason Haddix (talk | contribs) |
m |
||
| Line 18: | Line 18: | ||
</center> | </center> | ||
== About this list == | == About this list == | ||
| − | In 2013 we polled the industry for new vulnerability statistics in the field of mobile applications. What you see here is a result of that data and a representation of the mobile application threat landscape. | + | In 2013, we polled the industry for new vulnerability statistics in the field of mobile applications. What you see here is a result of that data and a representation of the mobile application threat landscape. |
| − | Our | + | Our goals for the 2014 list included the following: |
[[File:2014-01-26 20-23-29.png|right|550px]] | [[File:2014-01-26 20-23-29.png|right|550px]] | ||
| − | * | + | * Updates to the wiki content; including cross-linking to testing guides, more visual exercises, etc; |
| + | * Generation of more data; and | ||
* A PDF release. | * A PDF release. | ||
| + | This list has been finalized after a 90-day feedback period from the community. Based on feedback, we intend on releasing a Mobile Top Ten 2015 list following a similar approach of collecting data, grouping the data in logical and consistent ways. | ||
| − | + | Feel free to visit [https://groups.google.com/a/owasp.org/forum/#!forum/owasp-mobile-top-10-risks the mailing list] as well! | |
| − | + | == Call to Action for 2015 == | |
| + | We are currently looking for vendors, consultants, or other industry experts within the appsec community that are willing to participate in the OWASP Mobile Top Ten 2015. Participation could include any of the following: gathering data, promoting awareness, etc. | ||
| − | == Top 10 Mobile Risks - | + | == Top 10 Mobile Risks - Final List 2014 == |
*[[Mobile_Top_10_2014-M1|M1: Weak Server Side Controls ]] | *[[Mobile_Top_10_2014-M1|M1: Weak Server Side Controls ]] | ||
*[[Mobile_Top_10_2014-M2|M2: Insecure Data Storage ]] | *[[Mobile_Top_10_2014-M2|M2: Insecure Data Storage ]] | ||
Revision as of 18:59, 13 August 2014
About this list
In 2013, we polled the industry for new vulnerability statistics in the field of mobile applications. What you see here is a result of that data and a representation of the mobile application threat landscape.
Our goals for the 2014 list included the following:
- Updates to the wiki content; including cross-linking to testing guides, more visual exercises, etc;
- Generation of more data; and
- A PDF release.
This list has been finalized after a 90-day feedback period from the community. Based on feedback, we intend on releasing a Mobile Top Ten 2015 list following a similar approach of collecting data, grouping the data in logical and consistent ways.
Feel free to visit the mailing list as well!
Call to Action for 2015
We are currently looking for vendors, consultants, or other industry experts within the appsec community that are willing to participate in the OWASP Mobile Top Ten 2015. Participation could include any of the following: gathering data, promoting awareness, etc.
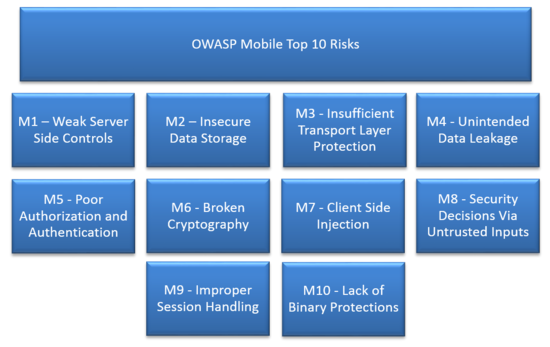
Top 10 Mobile Risks - Final List 2014
- M1: Weak Server Side Controls
- M2: Insecure Data Storage
- M3: Insufficient Transport Layer Protection
- M4: Unintended Data Leakage
- M5: Poor Authorization and Authentication
- M6: Broken Cryptography
- M7: Client Side Injection
- M8: Security Decisions Via Untrusted Inputs
- M9: Improper Session Handling
- M10: Lack of Binary Protections
Project Leads, Credit, and Contributions
Project Methodology
- We adhered loosely to the OWASP Web Top Ten Project methodology.
Archive
- The list below is the OLD release candidate v1.0 of the OWASP Top 10 Mobile Risks. This list was initially released on September 23, 2011 at Appsec USA.
- The original presentation can be found here: SLIDES
- The corresponding video can be found here: VIDEO
- 2011-12 Mobile Top Ten for archive purposes
- The original presentation can be found here: SLIDES