This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
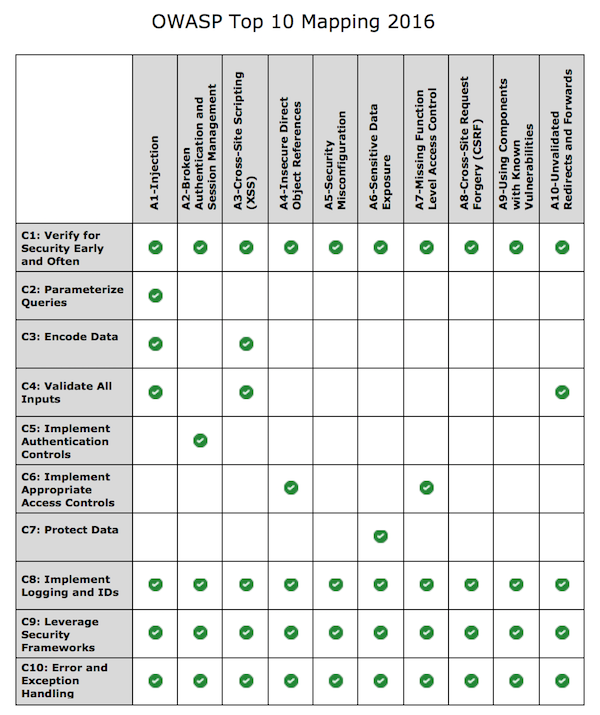
OWASP Proactive Controls 2016-Top10 Mapping
Overview
OWASP Top 10 Proactive Controls is a developer centric list of security techniques that should be included in every software development project. Each control helps preventing one or more of the OWASP Top Ten, the most critical web application security vulnerabilities.
This documents presents a summary of the mapping between the OWASP Top 10 Proactive Controls and each of the OWASP Top 10 helps to mitigate.
| OWASP Top 10 Proactive Controls | OWASP Top 10 Prevented |
|
C1: Verify for Security Early and Often Incorporate security testing as integral part of software engineering practice. Consider OWASP ASVS as a guide to define security requirements and testing. |
|
|
C2: Parameterize Queries The Parameterized queries are a way to leverage to Data Access Abstraction Layer how parameters are interpreted before executing an SQL query. It provides SQL injection protection. |
|
|
C3: Encode Data Encode data before use in a parser ( JS, CSS , XML ) |
|
|
C4: Validate All Inputs Consider all input from outside of the application as untrusted. For web applications this includes HTTP headers, cookies, and GET and POST parameters: any or all of this data could be manipulated by an attacker. |
|
|
C5: Identity and Authentication Controls Authentication is the process of verifying that an individual or an entity is who it claims to be while identity management is a broader topic which not only includes authentication, session management, but also covers advanced topics like identity federation, single sign on, password-management tools, identity repositories and more |
|
|
C6: Implement Access Controls Authorization (Access Control) is the process where requests to access a particular feature or resource should be granted or denied. The following "positive" access control design requirements should be considered at the initial stages of application development:
|
|
|
C7: Protect Data Data encryption at rest or transit |
|
| C8: Implement Logging and Intrusion Detection |
|
|
C9: Leverage Security Features and Libraries Starting from scratch when it comes to developing security controls leads to wasted time and massive security holes. Secure coding libraries help developers guard against security-related design and implementation flaws. It is critical to keep these frameworks and libraries up to date. For example:
|
Prevents:
|
|
C10: Error and Exception Handling
|
Prevents:
|