This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
OWASP Israel 2010 02
The meeting will be held at 16:45 on Tuesday, Feb 9th, 2010.
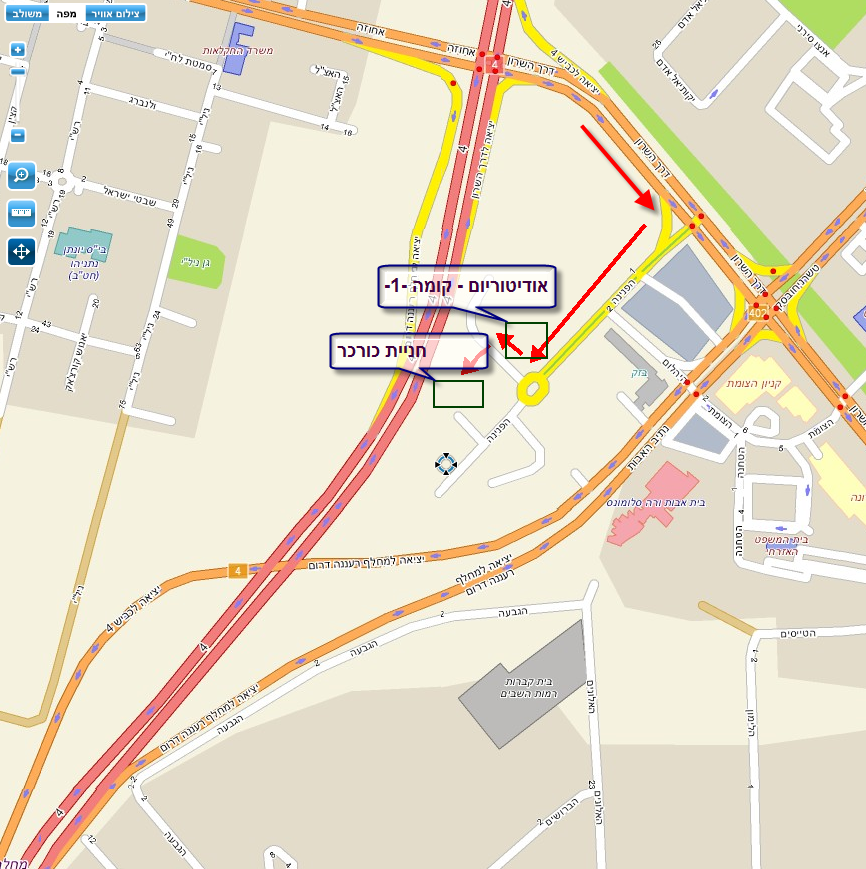
Location: Amdocs Ra'anana, HaPnina St. 8 in Amdocs Auditorium.
Parking can be found at the adjacent unpaved parking lot. Please refer to map at bottom of page.
PLEASE NOTE: YOU MUST CONFIRM YOUR ARRIVAL IN ADVANCE
The guard at the entrance will have a list of everybody who confirmed.
You will not be allowed into Amdocs premises without confirming arrival.
Please confirm your arrival by email to [email protected].
- 1 Agenda
- 2 16:45 - 17:05 : Gathering, Mingling & Refreshments
- 3 17:05 - 17:10 : Opening Notes
- 4 17:10 - 17:20 : Opening Notes
- 5 17:20 - 18:00 : Cloud Security Topics
- 6 18:00 - 18:35 : SaaS as a Security Hazard: The Google Docs Example
- 7 18:35 - 19:10 : SAML
- 8 19:10 - 19:40 : XSHM - Cross Site History Manipulation
- 9 Map
Agenda
16:45 - 17:05 : Gathering, Mingling & Refreshments
17:05 - 17:10 : Opening Notes
Ofer Maor, Hacktics
17:10 - 17:20 : Opening Notes
Avi Brener, Amdocs
17:20 - 18:00 : Cloud Security Topics
Shalom Carmel, Venera
As more and more services move into the cloud, security of these resources becomes significant. In this lecture Shalom will review various topics relating to cloud security, including:
- Short Introduction to XaaS
- Challenges in Cloud Security - Management, Process, Data, Communications, Connection to Enterprise
- Differences Between Security of Leading Cloud Providers
- Regulation in the Cloud - Is It Feasible?
18:00 - 18:35 : SaaS as a Security Hazard: The Google Docs Example
Ofer Shezaf, Better Place
As the borderline between a web site and an application blurs, so does the division between the enterprise IT and the internet. More and more enterprises adapt core applications which are provided as a service over the Internet. Until recently those where limited to vertical applications such as salesforce.com for sales automation and monster.com for recruiting, both of which have already suffered major security issues that compromises customer data. Google software push has led to enterprise adaption of general purpose cloud services including office tools, mail and knowledge management, which presents an entirely new risk level.
In this presentation we will discuss the security risks unique to SaaS (Software as a service) and some past attacks on such services. We will than dissect the security implications of using Google sites (which includes Google docs and Gmail) as an example for a SaaS. We will go over a checklist of things to examine in a SaaS before subscribing to ensure that it provides sufficient security and will discuss the solutions offered (or not) by Google to the items listed.
18:35 - 19:10 : SAML
David Movshovitz
SAML is one of the protocols that have been developed to secure web services, and has been become very popular especially to implement Web SSO and SaaS SSO. In the lecture we will describe the principals of the protocol and demonstrate how it is used to implement Web SSO.
19:10 - 19:40 : XSHM - Cross Site History Manipulation
Alex Roichman, Checkmarx
In this presentation I will introduce a newly discovered SOP (Same Origin Policy) security breach identified as Cross-Site History Manipulation (XSHM). Cross-Site History Manipulation breach is based on our research findings that the client-side browser history object is not properly partitioned on a per-site basis. Manipulating browser history may lead to SOP compromising, allow bi-directional CSRF and other exploitations such as: user privacy violation, login status detection, resource mapping, sensitive information inferring, users' activity tracking and URL parameter stealing. In the presentation I will show how XSHM can be executed, what applications are vulnerable to it, how to detect the flaw and consequently remediate it.