This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OWASP AppSec Iberia 2009"
(→Panel Speakers) |
|||
| Line 181: | Line 181: | ||
=== Panel Speakers === | === Panel Speakers === | ||
| + | == Justin Clarke == | ||
| + | '''Title''': SQL Injection - how far does the rabbit hole go? | ||
| + | |||
| + | '''Abstract''': SQL Injection has been around for over 10 years, and yet it is still to this day not truly understood by many security professionals and developers. With the recent mass attacks against sites across the world, and well publicised data breaches with SQL Injection as a component, it has again come to the fore of vulnerabilities under the spotlight, however many consider it to only be a data access issue, or parameterized queries to be a panacea. This talk explores the deeper, darker areas of SQL Injection, hybrid attacks, SQL Injection worms, and exploiting database functionality. Explore what kinds of things we can expect in future. | ||
| + | |||
| + | '''Bio''': Justin Clarke is a co-founder and Director at Gotham Digital Science, based in the United Kingdom. He has over twelve years of experience in assessing the security of networks, web applications, and wireless networks for large financial, retail, technology and government clients in the United States, the United Kingdom and New Zealand. | ||
| + | Justin is the lead author and technical editor of "SQL Injection Attacks and Defense" (Syngress 2009), co-author of "Network Security Tools: Writing, Hacking, and Modifying Security Tools" (O¹Reilly 2005), and a contributing author to "Network Security Assessment: Know Your Network, 2nd Edition" (O'Reilly 2007), as well as a speaker at a number of conferences and events on security topics, including Black Hat USA, BruCON, EuSecWest, OSCON, ISACA, RSA, SANS, OWASP, and the British Computer Society. He is the author of the open source SQLBrute blind SQL injection testing tool, and is the Chapter Leader for the London chapter of OWASP. | ||
| + | |||
| + | == Dinis Cruz == | ||
| + | '''Title''': OWASP O2 Platform - Open Platform for automating application security knowledge and workflows | ||
| + | |||
| + | '''Abstract''': In this talk Dinis Cruz will show the OWASP O2 Platform which is an open source toolkit specifically designed for developers and security consultants to be able to perform quick, effective and thorough 'source-code-driven' application security reviews. The OWASP O2 Platform (http://www.owasp.org/index.php/OWASP_O2_Platform) consumes results from the scanning engines from Ounce Labs, Microsoft's CAT.NET tool, FindBugs, CodeCrawler and AppScan DE, and also provides limited support for Fortify and OWASP WebScarab dumps. In the past, there has been a very healthy skepticism on the usability of Source Code analysis engines to find commonly found vulnerablities in real world applications. This presentation will show that with some creative and powerful tools, it IS possible to use O2 to discover those issues. This presentation will also show O2's advanced support for Struts and Spring MVC. | ||
| + | |||
| + | '''Bio''': Dinis Cruz is the Chief OWASP Evangelist and a Security Consultant based in London (UK) and specialized in: ASP.NET Application Security, Active Directory deployments, Application Security audits and .NET Security Curriculum Development. | ||
| + | Since the 1.1 release of the .Net Framework, Dinis has been one of the strongest proponents of the need to write .Net applications that can be executed in secure Partially Trusted .Net environments, and has done extensive research on: Rooting the CLR, exposing the dangers of Full Trust Asp.Net Code, Type Confusion vulnerabilities in Full Trust (i.e. non verifiable) code, creating .Net Security Protection Layers and using Reflection to dynamically manipulate .Net Client applications. | ||
| + | Dinis is the current [Owasp .Net Project] and [OWASP Autumn of Code] project's leader and the main developer of several of OWASP .Net tools ([SAM'SHE], [ANBS], [SiteGenerator], Owasp Report Generator, [Asp.Net Reflector]). | ||
| + | Dinis is a active trainer on .Net security having written and delivered courses for IOActive, Foundstone, Intense School and KPMG . His latest course is the two day training course [Advanced Asp.Net Exploits and Countermeasures, which was delivered at the Black Hat 2006 conference and will be presented on the fortcomming [OWASP AppSec Conference] in Seattle. | ||
| + | |||
| + | == Luis Corrons == | ||
| + | '''Title''': | ||
| + | |||
| + | '''Abstract''': The growth and complexity of the underground cybercrime economy has grown significantly over the past couple of years due to a variety of factors including the rise of social media tools, the global economic slowdown, and an increase in the total number of internet users. For the past 3 years, PandaLabs has monitored the ever-evolving cybercrime economy to discover its tactics, tools, participants, motivations and victims to understand the full extent of criminal activities and ultimately bring an end to the offenses. In October of 2008, PandaLabs published findings from a comprehensive study on the rogueware economy which concluded that the cybercriminals behind fake antivirus software applications were generating upwards of $15 million per month. In July of 2009, it released a follow-on study that proved monthly earnings had more than doubled to approximately $34 million through rougeware attacks distributed via Facebook, MySpace, Twitter, Digg and targeted Blackhat SEO. This session will reveal the latest results from PandaLabs’ ongoing study of the cybercrime economy by illustrating the latest malware strategies used by criminals, examining the changes in their attack strategies over time. The goal of this presentation is to raise the awareness of this growing underground economy. | ||
| + | |||
| + | '''Bio''': Luis Corrons has been working for Panda Security since 1999. He started in the technical support department, helping home and corporative users with virus incidents. A year later, he joined the international technical support team assisting Panda's technical support belonging to their partners distributed over 50 countries around the world. In 2002, he became PandaLabs' director as well as malware alerts coordinator in worldwide infection situations, dealing with worm such as Klez, SQLSlammer, Sobig, Blaster. Sasser, Mydoom, etc. During this time, he has coordinated several automated projects related with malware, such as the automatic analisys and response system, and the malware automatic information system. He's a speaker in several security conferences such as RSA, Virus Bulletin, SecurityBSides, RAID, etc. | ||
| + | |||
| + | == Marc Chisinevski == | ||
| + | '''Title''': The OWASP Logging Project | ||
| + | |||
| + | '''Abstract''': The goals of the Logging Project are: | ||
| + | *To provide tools for software developers in order to help them define and provide meaningful logs | ||
| + | *To provide code audit tools to ensure that log messages are consistent and complete (content, format, timestamps) | ||
| + | *To facilitate the integration of logs from different sources | ||
| + | *To facilitate attack reconstruction | ||
| + | *To facilitate information sharing around security events <br> | ||
| + | The talk will explore these areas, as well as provide details on existing tools and on related OWASP projects. Research directions for the future will also be discussed. A teaser for the presentation (with sound) can be found here: http://animoto.com/play/zel3bnvPCde7tcqBG3e9Cw | ||
| + | |||
| + | '''Bio''': Marc Chisinevski has worked in web application development and security since 2000. Outside his current position as security manager, he is the project lead for the OWASP Logging Project. He is a Certified Information System Security Professional (CISSP) and is active in the opensource community | ||
| + | (Asset, inventory and risk management project at http://sourceforge.net/projects/assetmng/). Experienced in malware analysis, Marc also takes part in reverse engineering challenges (http://lists.immunitysec.com/pipermail/dailydave/2009-September/005889.html). | ||
| + | |||
| + | == Justin Clarke == | ||
| + | '''Title''': | ||
| + | |||
| + | '''Abstract''': | ||
| + | |||
| + | '''Bio''': | ||
| + | |||
| + | == Justin Clarke == | ||
| + | '''Title''': | ||
| + | |||
| + | '''Abstract''': | ||
| + | |||
| + | '''Bio''': | ||
| + | |||
| + | == Justin Clarke == | ||
| + | '''Title''': | ||
| + | |||
| + | '''Abstract''': | ||
| + | |||
| + | '''Bio''': | ||
| + | |||
| + | == Justin Clarke == | ||
| + | '''Title''': | ||
| + | |||
| + | '''Abstract''': | ||
| + | |||
| + | '''Bio''': | ||
| + | |||
| + | |||
==== Venue ==== | ==== Venue ==== | ||
Revision as of 12:23, 26 November 2009
1st. Iberic Web Application Security Conference (IBWAS09)
Escuela Universitaria de Ingeniería Técnica de Telecomunicación, Universidad Politécnica de Madrid | Registration
www.ibwas.com (official web-site)
Welcome
|
|
Organization and Program Committee
IBWAS09 Chairs and Organization
Vicente Aguilera Díaz, Internet Security Auditors, OWASP Spain, Spain
Carlos Serrão, ISCTE-IUL Instituto Universitário de Lisboa, OWASP Portugal, Portugal
Fabio Cerullo, OWASP Global Education Commitie, OWASP Ireland, Ireland
IBWAS09 Program Committee
André Zúquete, Universidade De Aveiro, Portugal
Candelaria Hernández-Goya, Universidad De La Laguna, Spain
Carlos Costa, Universidade De Aveiro, Portugal
Carlos Ribeiro, Instituto Superior Técnico, Portugal
Eduardo Neves, OWASP Education Committee, OWASP Brazil, Brazil
Francesc Rovirosa i Raduà, Universitat Oberta de Catalunya (UOC), Spain
Gonzalo Álvarez Marañón, Consejo Superior de Investigaciones Científicas (CSIC), Spain
Isaac Agudo, University of Malaga, Spain
Jaime Delgado, Universitat Politecnica De Catalunya, Spain
Javier Hernando, Universitat Politecnica De Catalunya, Spain
Javier Rodríguez Saeta, Barcelona Digital, Spain
Joaquim Castro Ferreira, Universidade de Lisboa, Portugal
Joaquim Marques, Instituto Politécnico de Castelo Branco, Portugal
Jorge Dávila Muro, Universidad Politécnica de Madrid (UPM), Spain
Jorge E. López de Vergara, Universidad Autónoma de Madrid, Spain
José Carlos Metrôlho, Instituto Politécnico de Castelo Branco, Portugal
José Luis Oliveira, Universidade De Aveiro, Portugal
Kuai Hinojosa, OWASP Global Education Committee, New York University, United States
Leonardo Chiariglione, Cedeo, Italy
Leonardo Lemes, Unisinos, Brasil
Manuel Sequeira, ISCTE-IUL Instituto Universitário de Lisboa, Portugal
Marco Vieira, Universidade de Coimbra, Portugal
Mariemma I. Yagüe, University of Málaga, Spain
Miguel Correia, Universidade de Lisboa, Portugal
Miguel Dias, Microsoft, Portugal
Nuno Neves, Universidade de Lisboa, Portugal
Osvaldo Santos, Instituto Politécnico de Castelo Branco, Portugal
Panos Kudumakis, Queen Mary University of London, United Kingdom
Paulo Sousa, Universidade de Lisboa, Portugal
Rodrigo Roman, University of Malaga, Spain
Rui Cruz, Instituto Superior Técnico, Portugal
Rui Marinheiro, ISCTE-IUL Instituto Universitário de Lisboa, Portugal
Sérgio Lopes, Universidade do Minho, Portugal
Tiejun Huang, Pekin University, China
Víctor Villagrá, Universidad Politécnica de Madrid (UPM), Spain
Vitor Filipe, Universidade de Trás-os-Montes e Alto Douro, Portugal
Vitor Santos, Microsoft, Portugal
Vitor Torres, Universitat Pompeu Fabra, Spain
Wagner Elias, OWASP Brazil Chapter Leader, Brazil
Registration
Registration is now open!
You can register here
OWASP Membership ($50 annual membership fee) gets you a discount of $50.
| $395 | General Public |
| $345 | OWASP Members |
| $195 | Students |
| $1350 | 2-Day Training Course |
| $675 | 1-Day Training Course |
Agenda/Schedule
The conference schedule has been moved here
Speakers
Keynote Speakers
Bruce Schneier
Bruce Schneier is an internationally renowned security technologist and author. Described by The Economist as a "security guru," he is best known as a refreshingly candid and lucid security critic and commentator. When people want to know how security really works, they turn to Schneier.
His first bestseller, Applied Cryptography, explained how the arcane science of secret codes actually works, and was described by Wired as "the book the National Security Agency wanted never to be published." His book on computer and network security, Secrets and Lies, was called by Fortune "[a] jewel box of little surprises you can actually use." Beyond Fear tackles the problems of security from the small to the large: personal safety, crime, corporate security, national security. His current book, Schneier on Security, offers insight into everything from the risk of identity theft (vastly overrated) to the long-range security threat of unchecked presidential power and the surprisingly simple way to tamper-proof elections.
Regularly quoted in the media, he has testified on security before the United States Congress on several occasions and has written articles and op eds for many major publications, including The New York Times, The Guardian, Forbes, Wired, Nature, The Bulletin of the Atomic Scientists, The Sydney Morning Herald, The Boston Globe, The San Francisco Chronicle, and The Washington Post.
Schneier also publishes a free monthly newsletter, Crypto-Gram, with over 150,000 readers. In its ten years of regular publication, Crypto-Gram has become one of the most widely read forums for free-wheeling discussions, pointed critiques, and serious debate about security. As head curmudgeon at the table, Schneier explains, debunks, and draws lessons from security stories that make the news.
Schneier is the Chief Security Technology Officer of BT.
Jorge Martín
Jorge Martín is an inspector of the Spanish National Police, and currently the Head of the Logical Security Group from the High-Tech Crime Unit in the Comisaria General de Policía Judicial.
He his a Computer Systems Technical Engineer and since five years now dedicates himself to police investigation in the technological area, focusing his activity on crimes related to intrusions, different types of attacks, malware creation and dissemination and other related issues. He has also a large experience on the filed of computer forensics.
He has participated on different courses and conferences, both in Spain and abroad. Regularly participates on training initiatives with other law enforcement forces on different countries, several Interpol projects about technological investigation techniques and on different European Union studies on the obtaining and manipulation of digital evidences.
Panel Speakers
Justin Clarke
Title: SQL Injection - how far does the rabbit hole go?
Abstract: SQL Injection has been around for over 10 years, and yet it is still to this day not truly understood by many security professionals and developers. With the recent mass attacks against sites across the world, and well publicised data breaches with SQL Injection as a component, it has again come to the fore of vulnerabilities under the spotlight, however many consider it to only be a data access issue, or parameterized queries to be a panacea. This talk explores the deeper, darker areas of SQL Injection, hybrid attacks, SQL Injection worms, and exploiting database functionality. Explore what kinds of things we can expect in future.
Bio: Justin Clarke is a co-founder and Director at Gotham Digital Science, based in the United Kingdom. He has over twelve years of experience in assessing the security of networks, web applications, and wireless networks for large financial, retail, technology and government clients in the United States, the United Kingdom and New Zealand. Justin is the lead author and technical editor of "SQL Injection Attacks and Defense" (Syngress 2009), co-author of "Network Security Tools: Writing, Hacking, and Modifying Security Tools" (O¹Reilly 2005), and a contributing author to "Network Security Assessment: Know Your Network, 2nd Edition" (O'Reilly 2007), as well as a speaker at a number of conferences and events on security topics, including Black Hat USA, BruCON, EuSecWest, OSCON, ISACA, RSA, SANS, OWASP, and the British Computer Society. He is the author of the open source SQLBrute blind SQL injection testing tool, and is the Chapter Leader for the London chapter of OWASP.
Dinis Cruz
Title: OWASP O2 Platform - Open Platform for automating application security knowledge and workflows
Abstract: In this talk Dinis Cruz will show the OWASP O2 Platform which is an open source toolkit specifically designed for developers and security consultants to be able to perform quick, effective and thorough 'source-code-driven' application security reviews. The OWASP O2 Platform (http://www.owasp.org/index.php/OWASP_O2_Platform) consumes results from the scanning engines from Ounce Labs, Microsoft's CAT.NET tool, FindBugs, CodeCrawler and AppScan DE, and also provides limited support for Fortify and OWASP WebScarab dumps. In the past, there has been a very healthy skepticism on the usability of Source Code analysis engines to find commonly found vulnerablities in real world applications. This presentation will show that with some creative and powerful tools, it IS possible to use O2 to discover those issues. This presentation will also show O2's advanced support for Struts and Spring MVC.
Bio: Dinis Cruz is the Chief OWASP Evangelist and a Security Consultant based in London (UK) and specialized in: ASP.NET Application Security, Active Directory deployments, Application Security audits and .NET Security Curriculum Development. Since the 1.1 release of the .Net Framework, Dinis has been one of the strongest proponents of the need to write .Net applications that can be executed in secure Partially Trusted .Net environments, and has done extensive research on: Rooting the CLR, exposing the dangers of Full Trust Asp.Net Code, Type Confusion vulnerabilities in Full Trust (i.e. non verifiable) code, creating .Net Security Protection Layers and using Reflection to dynamically manipulate .Net Client applications. Dinis is the current [Owasp .Net Project] and [OWASP Autumn of Code] project's leader and the main developer of several of OWASP .Net tools ([SAM'SHE], [ANBS], [SiteGenerator], Owasp Report Generator, [Asp.Net Reflector]). Dinis is a active trainer on .Net security having written and delivered courses for IOActive, Foundstone, Intense School and KPMG . His latest course is the two day training course [Advanced Asp.Net Exploits and Countermeasures, which was delivered at the Black Hat 2006 conference and will be presented on the fortcomming [OWASP AppSec Conference] in Seattle.
Luis Corrons
Title:
Abstract: The growth and complexity of the underground cybercrime economy has grown significantly over the past couple of years due to a variety of factors including the rise of social media tools, the global economic slowdown, and an increase in the total number of internet users. For the past 3 years, PandaLabs has monitored the ever-evolving cybercrime economy to discover its tactics, tools, participants, motivations and victims to understand the full extent of criminal activities and ultimately bring an end to the offenses. In October of 2008, PandaLabs published findings from a comprehensive study on the rogueware economy which concluded that the cybercriminals behind fake antivirus software applications were generating upwards of $15 million per month. In July of 2009, it released a follow-on study that proved monthly earnings had more than doubled to approximately $34 million through rougeware attacks distributed via Facebook, MySpace, Twitter, Digg and targeted Blackhat SEO. This session will reveal the latest results from PandaLabs’ ongoing study of the cybercrime economy by illustrating the latest malware strategies used by criminals, examining the changes in their attack strategies over time. The goal of this presentation is to raise the awareness of this growing underground economy.
Bio: Luis Corrons has been working for Panda Security since 1999. He started in the technical support department, helping home and corporative users with virus incidents. A year later, he joined the international technical support team assisting Panda's technical support belonging to their partners distributed over 50 countries around the world. In 2002, he became PandaLabs' director as well as malware alerts coordinator in worldwide infection situations, dealing with worm such as Klez, SQLSlammer, Sobig, Blaster. Sasser, Mydoom, etc. During this time, he has coordinated several automated projects related with malware, such as the automatic analisys and response system, and the malware automatic information system. He's a speaker in several security conferences such as RSA, Virus Bulletin, SecurityBSides, RAID, etc.
Marc Chisinevski
Title: The OWASP Logging Project
Abstract: The goals of the Logging Project are:
- To provide tools for software developers in order to help them define and provide meaningful logs
- To provide code audit tools to ensure that log messages are consistent and complete (content, format, timestamps)
- To facilitate the integration of logs from different sources
- To facilitate attack reconstruction
- To facilitate information sharing around security events
The talk will explore these areas, as well as provide details on existing tools and on related OWASP projects. Research directions for the future will also be discussed. A teaser for the presentation (with sound) can be found here: http://animoto.com/play/zel3bnvPCde7tcqBG3e9Cw
Bio: Marc Chisinevski has worked in web application development and security since 2000. Outside his current position as security manager, he is the project lead for the OWASP Logging Project. He is a Certified Information System Security Professional (CISSP) and is active in the opensource community (Asset, inventory and risk management project at http://sourceforge.net/projects/assetmng/). Experienced in malware analysis, Marc also takes part in reverse engineering challenges (http://lists.immunitysec.com/pipermail/dailydave/2009-September/005889.html).
Justin Clarke
Title:
Abstract:
Bio:
Justin Clarke
Title:
Abstract:
Bio:
Justin Clarke
Title:
Abstract:
Bio:
Justin Clarke
Title:
Abstract:
Bio:
Venue
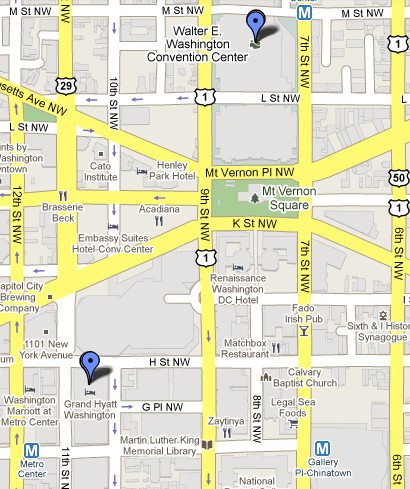
Walter E. Washington Convention Center
AppSec DC 2009 will be taking place at the Walter E. Washington Convention Center in downtown Washington DC.
The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro, and only a few blocks from our convention hotel, the Grand Hyatt Washington (reserve rooms here).
[[Image:|Screen_shot_2009-10-03_at_12.55.55_PM.png]]
Hotels
Grand Hyatt Washington DC
We've partnered with the Grand Hyatt Washington to bring you luxury accommodations at a reasonable price for your stay during our conference.
The Grand Hyatt is only a few blocks from the DC Convention Center and adjacent to a wide variety of restaurants and night life in downtown DC.
Our convention rate for reservations can also be applied shortly before or after the conference, if you wish to stay longer and enjoy the Washington DC Metropolitan Area.
You can register for a room at our convention rate of $209/night SOLD OUT
The Grand Hyatt Washington is one block from the Metro Center metro station, and three blocks from the Gallery Place/Chinatown metro station.
Sponsors
Sponsors
We are currently soliciting sponsors for the AppSec DC Conference. Please refer to our sponsorship opportunities for details.
Slots are going fast so contact us to sponsor today!
Platinum Sponsors |

|

|
||
Gold Sponsors |
|
|

| |
Silver Sponsors |

|

|

| |
| |

|

| ||

|
|

| ||
| |

|
|||
Organizational Sponsors |

|

| ||
Reception Sponsors |

| |||
Coffee Sponsors |
|

|
Travel
Traveling to the DC Metro Area
The Washington DC Area is serviced by three airports -- Reagan National (DCA), Dulles (IAD), and Thurgood Marshall Baltimore/Washington International (BWI). All currently have available transportation to downtown DC via public transportation, shuttles, or cab.
Washington DC is also serviced by Amtrak, VRE, and MARC train lines, which arrive in Union Station, a few metro stops or a short cab ride away from the convention center and the Grand Hyatt.
If you live in the DC Metropolitan area, we suggest taking Metro to the event. The convention center is located over the Mount Vernon Square/Convention Center Metro stop on the Green and Yellow lines of the DC Metro.