This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "OAT-006 Expediting"
m (→Cross-References) |
(→Indicative Diagram) |
||
| Line 19: | Line 19: | ||
===Indicative Diagram=== | ===Indicative Diagram=== | ||
| − | + | [[File:OAT-006_Expediting.png|500px|link=]] | |
=== Description === | === Description === | ||
Latest revision as of 15:06, 16 February 2018
This is an automated threat. To view all automated threats, please see the Automated Threat Category page. The OWASP Automated Threat Handbook - Wed Applications (pdf, print), an output of the OWASP Automated Threats to Web Applications Project, provides a fuller guide to each threat, detection methods and countermeasures. The threat identification chart helps to correctly identify the automated threat.
Definition
OWASP Automated Threat (OAT) Identity Number
OAT-006
Threat Event Name
Expediting
Summary Defining Characteristics
Perform actions to hasten progress of usually slow, tedious or time-consuming actions.
Indicative Diagram
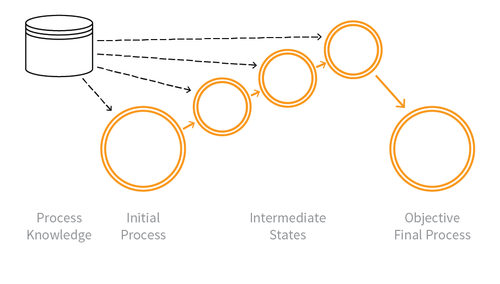
Description
Using speed to violate explicit or implicit assumptions about the application’s normal use to achieve unfair individual gain, often associated with deceit and loss to some other party.
In contrast to OAT-016 Skewing which affects metrics, Expediting is purely related to faster progression through a series of application processes. And OAT-017 Spamming is different to Expediting, since the focus of spam is to add information, and may not involve the concept of process progression.
Other Names and Examples
Algorithmic trading; Automated stock trading; Betting automation; Game automation; Gaming bot; Gold farming; Financial instrument dealing; High frequency trading; Last look trade; Mining; Purchase automation; Ticketing automation; Trading automation; Virtual wealth generation bot
See Also
Cross-References
CAPEC Category / Attack Pattern IDs
- 210 Abuse of Functionality
CWE Base / Class / Variant IDs
- 841 Improper Enforcement of Behavioral Workflow
WASC Threat IDs
- 21 Insufficient Anti-Automation
- 42 Abuse of Functionality