This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Mobile Top 10 2014-M1"
Jason Haddix (talk | contribs) |
m |
||
| Line 8: | Line 8: | ||
{{Top_10_2010:SummaryTableValue-1-Template|Impact|SEVERE}} | {{Top_10_2010:SummaryTableValue-1-Template|Impact|SEVERE}} | ||
{{Top_10_2010:SummaryTableHeaderEndTemplate}} | {{Top_10_2010:SummaryTableHeaderEndTemplate}} | ||
| − | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}> | + | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>Threat agents include any entity that acts as a source of untrustworthy input to a backend API service, web service, or traditional web server application. Examples of such entities include: a user, malware, or a vulnerable app on the mobile device.</td> |
| − | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>The attack vectors | + | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>The attack vectors correspond to the same attack vectors available through the traditional OWASP Top Ten.</td> |
| − | <td colspan=2 {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}> | + | <td colspan=2 {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>In order for this vulnerabiltiy to be exploited, the organization must expose a web service or API call that is consumed by the mobile app. The exposed service or API call is implemented using insecure coding techniques that produce an OWASP Top Ten vulnerability within the server. Through the mobile interface, an adversary is able to feed malicious inputs or unexpected sequences of events to the vulnerable endpoint. Hence, the adversary realizes the original OWASP Top Ten vulnerability on the server.</td> |
| − | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}> | + | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>The technical impact of this vulnerability corresponds to the technical impact of the associated vulnerability (defined in the OWASP Top Ten) that the adversary is exploiting via the mobile device. |
| − | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}> | + | For example, an adversary may exploit a Cross-Site Scripting (XSS) vulnerability via the mobile device. This corresponds to the OWASP Top Ten A3 - XSS Category with a technical impact of moderate.</td> |
| + | <td {{Template:Top 10 2010:SummaryTableRowStyleTemplate}}>The business impact of this vulnerability corresponds to the business impact of the associated vulnerability (defined in the OWASP Top Ten) that the adversary is exploiting via the mobile device. | ||
| + | For example, an adversary may exploit a Cross-Site Scripting (XSS) vulnerability via the mobile device. This corresponds to the OWASP Top Ten A3 - XSS Category's business impacts.</td> | ||
{{Top_10_2010:SummaryTableEndTemplate}} | {{Top_10_2010:SummaryTableEndTemplate}} | ||
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=1|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=1|risk=2}} | ||
| − | + | M1 encompasses almost everything that a mobile application can do badly that does not take place on the phone. Which is exactly the argument… should it be listed at all? Don’t we have a Top Ten lists for Web Applications? Don’t we have one for cloud too? | |
| − | In fact, we do. If we could be altogether sure that everyone who wanted information on mobile security also stopped by those projects… it would be a perfect world. | + | In fact, we do. If we could be altogether sure that everyone who wanted information on mobile security also stopped by those projects… it would be a perfect world. After two rounds of data collection from some of the world’s top assessment teams, server side issues are so prevalent in mobile applications that we cannot ignore them in the Mobile Top Ten 2014 listing. Experience suggests that several factors have lead to a proliferation of server-side vulnerabilities. These factors include: |
| − | * Rush to market | + | * Rush to market; |
| − | * Lack of security knowledge because of the new-ness of the languages | + | * Lack of security knowledge because of the new-ness of the languages; |
| − | * Easy access to frameworks that don’t prioritize security | + | * Easy access to frameworks that don’t prioritize security; |
| − | * Higher than average outsourced development | + | * Higher than average outsourced development; |
| − | * Lower security budgets for mobile applications | + | * Lower security budgets for mobile applications; |
| − | * Assumption that the mobile OS takes full responsibility for security | + | * Assumption that the mobile OS takes full responsibility for security; and |
| − | * Weakness due to cross-platform development and compilation | + | * Weakness due to cross-platform development and compilation. |
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=2|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=2|risk=2}} | ||
| − | Secure coding and configuration practices must be used on server-side of the mobile application. For specific vulnerability information refer to the OWASP Web Top Ten or Cloud Top Ten projects | + | Secure coding and configuration practices must be used on server-side of the mobile application. For specific vulnerability information, refer to the OWASP Web Top Ten or Cloud Top Ten projects. |
{{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=3|risk=2}} | {{Mobile_Top_10_2012:SubsectionAdvancedTemplate|type={{Mobile_Top_10_2012:StyleTemplate}}|number=3|risk=2}} | ||
| − | + | Below, you can see that there are many risks and vulnerabilities that you must mitigate in order to satisfy M1: | |
| Line 39: | Line 41: | ||
=== The Worst Offenders === | === The Worst Offenders === | ||
| − | + | Below is a list vulnerability types that OWASP sees most often within mobile applications: | |
Revision as of 23:35, 9 April 2014
| Threat Agents | Attack Vectors | Security Weakness | Technical Impacts | Business Impacts | |
|---|---|---|---|---|---|
| Application Specific | Exploitability EASY |
Prevalence COMMON |
Detectability AVERAGE |
Impact SEVERE |
Application / Business Specific |
| Threat agents include any entity that acts as a source of untrustworthy input to a backend API service, web service, or traditional web server application. Examples of such entities include: a user, malware, or a vulnerable app on the mobile device. | The attack vectors correspond to the same attack vectors available through the traditional OWASP Top Ten. | In order for this vulnerabiltiy to be exploited, the organization must expose a web service or API call that is consumed by the mobile app. The exposed service or API call is implemented using insecure coding techniques that produce an OWASP Top Ten vulnerability within the server. Through the mobile interface, an adversary is able to feed malicious inputs or unexpected sequences of events to the vulnerable endpoint. Hence, the adversary realizes the original OWASP Top Ten vulnerability on the server. | The technical impact of this vulnerability corresponds to the technical impact of the associated vulnerability (defined in the OWASP Top Ten) that the adversary is exploiting via the mobile device. For example, an adversary may exploit a Cross-Site Scripting (XSS) vulnerability via the mobile device. This corresponds to the OWASP Top Ten A3 - XSS Category with a technical impact of moderate. | The business impact of this vulnerability corresponds to the business impact of the associated vulnerability (defined in the OWASP Top Ten) that the adversary is exploiting via the mobile device. For example, an adversary may exploit a Cross-Site Scripting (XSS) vulnerability via the mobile device. This corresponds to the OWASP Top Ten A3 - XSS Category's business impacts. | |
M1 encompasses almost everything that a mobile application can do badly that does not take place on the phone. Which is exactly the argument… should it be listed at all? Don’t we have a Top Ten lists for Web Applications? Don’t we have one for cloud too?
In fact, we do. If we could be altogether sure that everyone who wanted information on mobile security also stopped by those projects… it would be a perfect world. After two rounds of data collection from some of the world’s top assessment teams, server side issues are so prevalent in mobile applications that we cannot ignore them in the Mobile Top Ten 2014 listing. Experience suggests that several factors have lead to a proliferation of server-side vulnerabilities. These factors include:
- Rush to market;
- Lack of security knowledge because of the new-ness of the languages;
- Easy access to frameworks that don’t prioritize security;
- Higher than average outsourced development;
- Lower security budgets for mobile applications;
- Assumption that the mobile OS takes full responsibility for security; and
- Weakness due to cross-platform development and compilation.
Secure coding and configuration practices must be used on server-side of the mobile application. For specific vulnerability information, refer to the OWASP Web Top Ten or Cloud Top Ten projects.
Below, you can see that there are many risks and vulnerabilities that you must mitigate in order to satisfy M1:

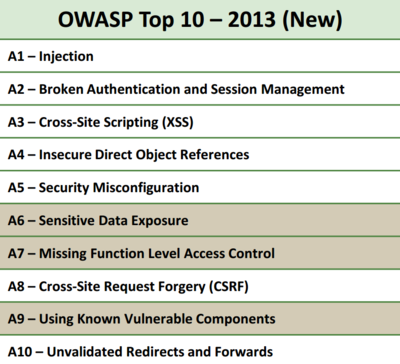
The Worst Offenders
Below is a list vulnerability types that OWASP sees most often within mobile applications:
- Poor Web Services Hardening
- Logic flaws
- Weak Authentication
- Weak or no session management
- Session fixation
- Sensitive data transmitted using GET method
- Insecure web server configurations
- Default content
- Administrative interfaces
- Injection (SQL, XSS, Command) on both web services and mobile-enabled websites
- Authentication flaws
- Session Management flaws
- Access control vulnerabilities
- Local and Remote File Includes
References