This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Man-in-the-middle attack"
From OWASP
m (→Examples) |
m (→Examples) |
||
| Line 5: | Line 5: | ||
==Examples == | ==Examples == | ||
| − | [[Image: | + | [[Image:MITM.jpg]] |
Image courtesy of www.arcot.com [http://www.arcot.com/mitm/images/mitm_diagram_lg.gif] | Image courtesy of www.arcot.com [http://www.arcot.com/mitm/images/mitm_diagram_lg.gif] | ||
<br> | <br> | ||
Revision as of 21:36, 29 April 2007
- This is an Attack. To view all attacks, please see the Attack Category page.
Description
A Man In The Middle (MITM) attack is a form of attack in which an evil hacker can trick end users in to thinking he is a bank or other such service in order to 'sniff' or steal the users login credentials.
Examples
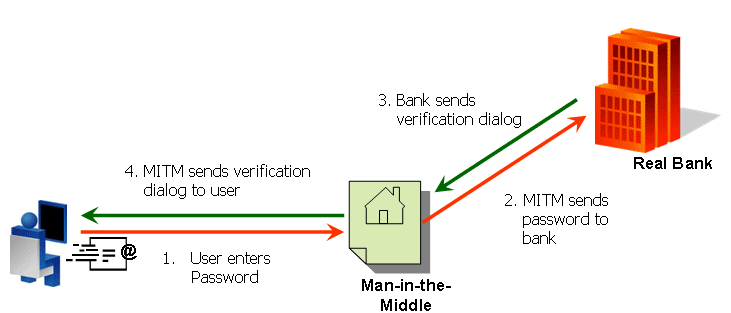 Image courtesy of www.arcot.com [1]
Image courtesy of www.arcot.com [1]
In this example you see the attacker intercepting, logging and stealing any information passed to the server.
Related Threats
Related Attacks
Related Vulnerabilities
Related Countermeasures
Categories
This article is a stub. You can help OWASP by expanding it or discussing it on its Talk page.