|
|
| (36 intermediate revisions by 3 users not shown) |
| Line 1: |
Line 1: |
| | __NOTOC__ | | __NOTOC__ |
| | | | |
| − | [[Image:OWASP Lascon Logo.gif|LASCON 2010 Banner]] | + | [[Image:Lascon800x191.png|800px]] |
| | | | |
| | ===== Click [http://www.owasp.org/index.php/Lonestar_Application_Security_Conference_2010 here] for information on LASCON 2010. ===== | | ===== Click [http://www.owasp.org/index.php/Lonestar_Application_Security_Conference_2010 here] for information on LASCON 2010. ===== |
| Line 7: |
Line 7: |
| | ===== SAVE THE DATE: LASCON 2011 is happening on October 28th, 2011 in Austin, TX ===== | | ===== SAVE THE DATE: LASCON 2011 is happening on October 28th, 2011 in Austin, TX ===== |
| | | | |
| − | [http://guest.cvent.com/d/vdqf7g/4W Registration Link] | Speaker List Posted! | [http://twitter.com/LASCONATX Follow LASCONATX on Twitter] | [http://www.norriscenters.com/Austin/ Norris Conference Center]
| + | [http://twitter.com/LASCONATX Follow LASCONATX on Twitter] | [http://www.norriscenters.com/Austin/ Norris Conference Center] |
| | | | |
| | <br> <!-- Header --> | | <br> <!-- Header --> |
| Line 19: |
Line 19: |
| | |- | | |- |
| | | style="width: 95%; color: rgb(0, 0, 0);" | | | | style="width: 95%; color: rgb(0, 0, 0);" | |
| − | '''Who Should Attend LASCON 2010:''' | + | '''Who Should Attend LASCON 2011:''' |
| | | | |
| | *Application Developers | | *Application Developers |
| Line 30: |
Line 30: |
| | *IT Professionals Interested in Improving IT Security<br> | | *IT Professionals Interested in Improving IT Security<br> |
| | | | |
| − | <br> | + | <br> |
| − | [[Image:LACON2010Schedule.png|800px|link=http://www.lascon.org|LASCON 2010 Schedule]]
| |
| − | | |
| − | '''[http://guest.cvent.com/d/vdqf7g/4W You can register for the conference here]''' <!-- Mediawiki needs all these spaces -->
| |
| | | | |
| − | <br>
| + | [http://www.regonline.com/954716 https://www.owasp.org/images/c/c5/LASCON_Register_Now.gif] |
| | | | |
| | |} | | |} |
| Line 59: |
Line 56: |
| | == Registration Is Now Open! == | | == Registration Is Now Open! == |
| | | | |
| − | [http://guest.cvent.com/d/vdqf7g/4W Register Here] | + | OWASP [[Membership]] ($50 annual membership fee) gets you a discount on registration. |
| | | | |
| − | OWASP [[Membership]] ($50 annual membership fee) gets you a discount on registration.
| + | [http://www.regonline.com/954716 https://www.owasp.org/images/c/c5/LASCON_Register_Now.gif] |
| | | | |
| | {| | | {| |
| | |- | | |- |
| − | | Non-Members (Includes a 1 year OWASP membership) | + | | [https://www.regonline.com/?eventID=954716&rTypeID=480930 Non-Members (Includes a 1 year OWASP membership)] |
| − | | $150 Until 10/26/2010 | + | | $125 Until 7/31/2011 |
| − | | $200 After 10/26/2010 | + | | $175 Until 9/30/2011 |
| | + | | $225 After 9/30/2011 |
| | |- | | |- |
| − | | OWASP Members | + | | [https://www.regonline.com/?eventID=954716&rTypeID=480929 OWASP Members] |
| − | | $100 Until 10/26/2010 | + | | $75 Until 7/31/2011 |
| − | | $200 After 10/26/2010 | + | | $125 Until 9/30/2011 |
| | + | | $175 After 9/30/2011 |
| | |- | | |- |
| − | | Students with valid Student ID (must be shown at the door) | + | | [https://www.regonline.com/?eventID=954716&rTypeID=480932 Students with valid Student ID (must be shown at the door)] |
| − | | $80 Until 10/26/2010 | + | | $50 Until 7/31/2011 |
| − | | $2000 After 10/26/2010 | + | | $75 Until 9/30/2011 |
| | + | | $100 After 9/30/2011 |
| | |} | | |} |
| | | | |
| − | '''Who Should Attend LASCON 2010:''' | + | '''Who Should Attend LASCON 2011:''' |
| | | | |
| | *Application Developers | | *Application Developers |
| Line 91: |
Line 91: |
| | <br> For student discount, you must present proof of current enrollment when picking up your badge. No exceptions. | | <br> For student discount, you must present proof of current enrollment when picking up your badge. No exceptions. |
| | | | |
| − | ==== Sessions ==== | + | ==== Training ==== |
| | + | |
| | + | We are pleased to announce that this year we will be adding on two different training classes the day before the Lonestar Application Security Conference (LASCON) on '''Thursday, October 27, 2011'''. These training classes are unlike those you see at most conferences both in content and cost. If you have already registered for LASCON, simply go to http://www.regonline.com/lascon2011 and select the "Already Registered?" link. Log in with the e-mail address you registered with and then select to edit your "Agenda". Place a check mark in the box for the training you would like to attend (or the FREE happy hour) and select "Continue" to check out. If you have not already registered for LASCON, you will have the ability to add the training of your choice on the "Agenda" screen of registration. The trainings are as follows:<br> |
| | + | |
| | + | '''<u>TRAINING 1 ($250):</u>'''<br> |
| | + | '''Title: Advanced Threat Tactics with Armitage and Metasploit'''<br> |
| | + | |
| | + | Metasploit is a powerful exploit framework and a must-have tool for penetration testers. Armitage builds a workflow on top of the Metasploit framework and exposes its most advanced capabilities. This demonstration and lab oriented session will teach you Metasploit and Armitage for the purpose of emulating adversary tactics. This course will start with the basics and quickly take you into the workflow of modern threats. You'll learn how to create trojan files, manage covert HTTP and HTTPS communications, set up social engineering attacks, and use pivoting to take over a network.<br> |
| | + | |
| | + | To participate in the labs, you must have VMWare Player, VMWare Fusion, or VMWare Workstation installed.<br> |
| | + | |
| | + | Raphael has put up some additional information on this class on his website at http://www.fastandeasyhacking.com/threats.<br> |
| | + | |
| | + | '''Biography:'''<br> |
| | + | Raphael Mudge is a Washington, DC, based code hacker working on a new startup effort. He is the developer of the open source Armitage for Metasploit. Raphael regularly writes and speaks on security topics. His work has appeared in USENIX ;login:, Linux Journal, and Hakin9. Previously, Raphael worked as a security researcher, software engineer, penetration tester, and system administrator.<br> |
| | + | |
| | + | '''<u>TRAINING 2 ($250):</u>'''<br> |
| | + | '''Title: Bootstrapping Your Application Security Program'''<br> |
| | + | |
| | + | This training class is for new managers & leads accountable for integrating Application Security into their enterprise. The course will walk through various success factors, including a mixture of strategy, policy, and technology considerations. The course will help attendees develop incremental plans they can employ to make both short-term and long-term measurable improvements to their enterprise Application Security.<br> |
| | | | |
| − | == Keynote ==
| + | Topics that will be covered include:<br> |
| − | '''<font color=red>Matt Tesauro</font>'''<br>
| + | *Goal Setting |
| − | '''<font color=brown>Keynote</font>'''<br>
| + | *Running effective pilot programs |
| − | '''Video:''' [http://vimeo.com/17822489 Link]<br>
| + | *Working with vendors |
| − | <br>
| + | *Roles & responsibilities in application security |
| − | == Technical Track ==
| + | *Getting buy-in from management, development, business, IT, etc. |
| − | '''<font color=red>James Flom</font>'''<br>
| + | *Meeting compliance needs (PCI & others) |
| − | '''<font color=brown>[http://www.owasp.org/images/6/68/LASCON2010_Flom.pdf Why ha.ckers.org Doesn’t Get Hacked]</font>'''<br>
| + | *Measuring success & ROI |
| − | <br>
| + | *Reporting to management |
| − | Ha.ckers.org has suffered nearly every attack a website can. These attacks include robots, sophisticated web-based attacks, brute force, denial of service, and network based attacks. This speech will explain the other side of protecting high risk websites - the configurations, operating system, and network.<br>
| + | *Scaling your program |
| − | <br>
| |
| − | '''<font color=red>Charles Henderson and Garrett Held</font>'''<br>
| |
| − | '''<font color=brown>Anatomy of a Logic Flaw</font>'''<br>
| |
| − | <br>
| |
| − | Traditional vulnerabilities like SQL Injection, buffer overflows, etc, have well established techniques for discovery and prevention. On the other hand, logic flaws are incredibly diverse and often unique to the specific application or business organization. Because of this, logic flaws have taken on a near mythical status. In the myth, logic flaws are nearly impossible to find until the elite of the elite hackers launch an attack to completely own the application. The reality is far different; logic flaws are not the complex nightmare that many have made them out to be. This presentation will use real-world examples to show how logic flaws are typically introduced into an application, how they can be consistently detected during testing, and how they can be prevented during development. Instead of hoping for magic, repeatable processes will be outlined for each of those items. This will prove beneficial to anyone responsible for application security: programmers, architects, managers, and pen testers.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Chris Eng</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/0/05/LASCON2010_Eng.pdf Deconstructing ColdFusion]</font>'''<br>
| |
| − | <br>
| |
| − | ColdFusion is a somewhat forgotten but still very prevalent web application development platform. This presentation is a technical survey of ColdFusion security that will be of interest mostly to code auditors, penetration testers, and developers. In the talk, we'll cover the history of the ColdFusion platform and its relevance to today's security landscape. We'll describe basics of ColdFusion markup, control flow, functions, and components and demonstrate how to identify common web application vulnerabilities in the source code. We'll also delve into ColdFusion J2EE internals, showing what CFML pages and components look like when compiled down to Java, and describing some of the unusual behavior we've observed at that level. We'll discuss open-source tools to aid reverse engineers in working with ColdFusion's proprietary classfile format.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Robert Hansen and Josh Sokol</font>'''<br>
| |
| − | '''<font color=brown>HTTPS Can Byte Me</font>'''<br>
| |
| − | '''Video:''' [http://vimeo.com/17822849 Link]<br>
| |
| − | <br>
| |
| − | HTTPS was created to protect confidentiality and prove integrity of content passed over the web. It has essentially become the de-facto standard for internet commerce transport security. Over the years a number of exploits have attacked the principle, underlying PKI infrastructure and overall design of HTTPS. This presentation will drive another nail in the HTTPS coffin through a number of new exploitation techniques leveraging man-in-the-middle attacks; the goal of which is to break confidentiality and integrity of HTTPS traffic. The impact of these flaws suggests a need for changes in the ways we protect the transmission of data online.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Samy Kamkar</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/6/61/LASCON2010_Kamkar.pdf How I Met Your Girlfriend]</font>'''<br>
| |
| − | '''Video:''' [http://vimeo.com/17822912 Link]<br>
| |
| − | <br>
| |
| − | How I Met Your Girlfriend: The discovery and execution of entirely new classes of attacks executed from the Web in order to meet your girlfriend. This includes newly discovered attacks inclduing HTML5 client-side XSS (without XSS hitting the server!), PHP session hijacking and weak random numbers (accurately guessing PHP session cookies), browser protocol confusion (turning a browser into an SMTP server), firewall and NAT penetration via Javascript (turning your router against you), remote iPhone Google Maps hijacking (iPhone penetration combined with HTTP man-in-the-middle), extracting extremely accurate geolocation information from a Web browser (not using IP geolocation), and more.<br>
| |
| − | <br>
| |
| | | | |
| − | == Management Track ==
| + | '''Biography:'''<br> |
| − | '''<font color=red>Charlie Scott and Jay Paz</font>'''<br>
| + | Bankim Tejani specializes in helping large companies stand up application security programs. Currently a Managing Consultant ofat Fortify, An HP Company, Bankim works with leading financials, technology companies, government agencies, and other corporations. He helps them strategically inject application security processes and technologies into their SDLCs while trying to minimize impact on time to market and maximize ROI. His prior experience begins with software development and transitions to network security research, red teaming, information security research, and application security consulting & training.<br> |
| − | '''<font color=brown>[http://www.owasp.org/images/6/6f/LASCON2010_Scott_Paz.pdf Conducting an Instiution-Wide, Multi-Department Application Security Assessment]</font>'''<br>
| |
| − | <br>
| |
| − | From early 2009 until mid-2010, the Information Security Office at the University of Texas at Austin conducted a security assessment of over 250 web applications, spanning over 30 departments. The objectives of this assessment were to provide a thorough security review of existing applications, and act as an education and awareness exercise for the application developers. This presentation covers the political, technical, and scheduling challenges encountered on this assessment, how they were overcome, the results of the assessment and the changes they brought about, and lessons learned by the assessment team.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Joe Jarzombek</font>'''<br>
| |
| − | '''<font color=brown>Mitigating Business Risks with Application Security</font>'''<br>
| |
| − | '''Video:''' [http://vimeo.com/17822614 Link]<br>
| |
| − | <br>
| |
| − | With today’s global IT software supply chain, project management and software/systems engineering processes must explicitly address security risks posed by exploitable software. Traditionally, these disciplines have not clearly and directly focused on software security risks that can be passed from projects to the organization. Software security assurance processes and practices span development and acquisition and can be used to enhance project management and quality assurance activities. Mr. Jarzombek explains the critical need for adherence to the practices, guidelines, rules, and principles used to build security into every phase of software development.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Michael Howard</font>'''<br>
| |
| − | '''<font color=brown>Everything useful I learned about software security, I learned at Microsoft!</font>'''<br>
| |
| − | '''Video:''' [http://vimeo.com/17822721 Link]<br>
| |
| − | <br>
| |
| − | In this talk, Michael will discuss some of the things he has learned over the last 10 years working on software security at Microsoft. The Wins. The Losses, but most importantly, the Wisdom learned!<br>
| |
| − | <br>
| |
| − | '''<font color=red>Erik Pace Birkholz</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/8/80/LASCON2010_Birkholz.pdf Security Religions and Risk Windows]</font>'''<br>
| |
| − | <br>
| |
| − | There is a difference between what is possible and what is probable, something we often lose sight of in the world of information security. For example, a vulnerability represents a possible way for an attacker to exploit an asset, but remember not all vulnerabilities are created equal. Obviously, we must also keep in mind that a vulnerability's mere existence does not necessarily mean it will be exploited, or indicate by whom or to what extent. Some vulnerabilities are more difficult to exploit than others and therefore attract different attackers. Autonomous worms & viruses may attack one type of issue, while a sentient targeted attacker may prefer another path. Better understanding of these factors enables us to make informed business decisions about website risk management and what is probable.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Pete Perfetti</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/b/b7/LASCON2010_Perfetti.pdf Technology and Business Risk Management: How Application Security Fits In]</font>'''<br>
| |
| − | <br>
| |
| − | This presentation demonstrates how important application security is to the overall stability and security of the infrastructure and the ultimately, the business. Presented from the Information Security Officer/Risk Manager point of view, it shows how a strong information security program reduces levels of reputational, operational, legal, and strategic risk by limiting vulnerabilities, increasing stability, and maintaining customer confidence and trust. It focuses on the top concerns of risk managers and how application security fits into the overall risk management process. The audience will be given recommendations on how to improve cost effectiveness and efficiency to achieve business, security, audit, and compliance objectives relative to applications.<br>
| |
| − | <br> | |
| | | | |
| − | == OWASP Etc Track ==
| + | Seats in these trainings will be very limited and registrants will be accepted on a first-come, first-served basis. Sign up today! |
| − | '''<font color=red>Dean Bushmiller</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/6/63/LASCON2010_Bushmiller.pdf OWASP Top 10: What is it all about?]</font>'''<br>
| |
| − | <br>
| |
| − | Everyone knows exactly what the OWASP top ten security threats are, right? Well sort of... I ask people if they have heard of the top ten they say yes. I ask them to name a few they pause, then they blurt out 2-3. Then I ask them to explain those 2-3 and they look at me like a deer-in-the-headlights. I want to make sure that everyone who walks out of the presentation can clearly define the top ten and be able to communicate to another what each of the top ten vulnerabilites are.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Brad Causey</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/5/55/LASCON2010_Causey.ppt Automating Web Testing Beyond OWASP Webscarab Using Python] ([http://www.owasp.org/images/3/33/LASCON2010_Causey_Python_files.zip Python Files])</font>'''<br>
| |
| − | <br>
| |
| − | This presentation will illustrate ways to improve web security assessments by using advanced features in OWASP Webscarab and extending your options with automation using Python.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Noa Bar-yosef</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/7/7f/LASCON2010_BarYosef.pdf Tell Me Your IP and I Will Tell You Who You Are]</font>'''<br>
| |
| − | <br>
| |
| − | IP addresses have been traditionally considered an unreliable method for attack detection. The unreliability is attributed to the use of web proxies, NAT and non-static IP addresses for end-stations. This session will demonstrate how information derived from IP addresses can in fact be used to dramatically improve attack detection capabilities. The presentation will discuss attributes such as Geo Location, Reverse DNS Lookup, Anonymous Proxy lists and more. We discuss how IP intelligence can be used to increase detection effectiveness (ratio of false positives to false negatives) by "ruling" on otherwise indecisive anomalies. We also discuss certain scenarios in which IP intelligence is crucial for even detecting anomalies. The presentation is supported by corroborative evidence derived from actual log data and demonstrates some of the tools that can be used for analysis.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Karen Lu and Asad Ali</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/5/5b/LASCON2010_Lu_Ali.pdf Enhancing Web Application Security Using another Factor]</font>'''<br>
| |
| − | <br>
| |
| − | As web applications have become a necessity of contemporary societies, there is an increasing need to secure access to these applications. This talk explains how web applications can add the "what-you-have" factor to strengthen user authentication and enhance the security, without compromising the ease of use generally associated with the traditional username/password method. In particular, we will describe smart card based authentication methods, including OTP, TLS mutual authentication, and X.509 certificate-based challenge/response. Although these methods have their strengths and weaknesses in terms ofsecurity and usability, they all significantly enhance the authentication for web applications.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Ernest Mueller</font>'''<br>
| |
| − | '''<font color=brown>[http://www.owasp.org/images/c/c5/LASCON2010_Mueller.pdf Why The Cloud Is More Secure Than Your Existing Systems]</font>'''<br>
| |
| − | <br>
| |
| − | Security is frequently cited as the #1 hindrance to the adoption of cloud computing. Much of this concern is generated by the fact that security is frequently cited as the #1 hindrance to the adoption of cloud computing. Come cut through the FUD and hear about ways in that cloud systems are actually way more secure than what you already have running in your enterprise, and how you as a security professional can benefit from the cloud when creating secure systems.<br>
| |
| − | <br>
| |
| | | | |
| − | ==== Speakers ==== | + | ==== Sessions ==== |
| | | | |
| − | '''<font color=red>Asad Ali</font>''' is a senior researcher at Gemalto Technology & Innovation group and is currently working on next-generation smart card products. His research interests include smart card operating systems, application frameworks, security protocols, embedded file systems, smart card usability, and secure portable tokens. He is co-inventor of the xID architecture for plug-n-play smart cards, and the Network Card technology that won Card Technology 2005 "Breakthrough Award for Innovation." He holds several patents in the field of Smart Card connectivity and their ubiquitous use, and has published extensively on these topics. Mr. Ali has a Master's degree in Engineering from MIT.<br>
| + | See http://lascon.org/ |
| − | <br>
| |
| − | '''<font color=red>Noa Bar-Yosef</font>''' is a Senior Security Strategist at Imperva. Previously, she held the position of a senior security researcher with the Imperva Application Defense Center. She conducted research on database and Web application vulnerabilities. Prior to Imperva, she has held TA positions in courses on programming and network security at Tel Aviv University and Open University. She has also been a software engineer with educational software vendor Sunburst Technology. Bar-Yosef holds a MSc degree (specializing in information security) from Tel-Aviv University, School of Computer Science and a BSc degree from The Hebrew University, School of Computer Science. During her work in Imperva, Noa has discovered multiple vulnerabilities in various commercial applications and worked with software vendors on their resolutions.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Erik Pace Birkholz</font>''', CISSP is the author of the best-selling book SPECIAL OPS: Host and Network Security and a contributing author of five international best-selling books for Osborne/McGraw-Hill including SQL Server Security, Hacking Windows 2000 Exposed and Hacking Exposed: Network Security Secrets and Solutions. Erik is an award-winning speaker who has presented to audiences worldwide, including NATO, the Pentagon, the NSA, and five of the Black Hat Briefings. In late 2006, Birkholz became the Manager of Global Information Security Assurance for Dell. Since January 2010, Erik has worked as a Director for WhiteHat Security (www.whitehatsec.com). conferences around the world (including past Black Hat, SOURCE, IAFCI, OWASP AppSec USA, OWASP AppSec Europe, and Merchant Risk Council events) on various subject matters relating to application security.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Dean Bushmiller</font>''' has taught for 12 years. He is the recipient of five Mission Coins from various military branches. He has led national certification organizations in development, policy, and educational materials for over 10 years. He has presented, consulted, and instructed government, education, military, and private organizations. Dean has worked for SANS, ISC2, and other security training organizations. He has bee the keynote speaker at information security conferences as well as state and local colleges. He is now Director of Training for Expanding Security.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Brad Causey</font>''' is an active member of the security and forensics community worldwide. Brad tends to focus his time on Web Application security as it applies to global and enterprise arenas. He is currently employed at a major international financial institution as a security analyst. Brad is the President of the OWASP Alabama chapter, a member of the OWASP Global Projects Committee and a contributor to the OWASP Live CD. He is also the President of the International Information Systems Forensics Association chapter in Alabama. Brad is an avid author and writer with hundreds of publications and several books. Brad currently holds certifications in the following arenas: MCSA, MCDBA, MCSE, MCT, MCP, GBLC, GGSC100, C|EH, CIFI, CCNA,IT Project Management+, Security+, A+, Network+, CISSP, CGSP.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Chris Eng</font>''' is Senior Director of Research at Veracode, where he helps define and implement the security analysis capabilities of Veracode's service offerings. He is a regular speaker at information security conferences including BlackHat, OWASP, and RSA, and has presented on a diverse set of application security topics ranging from attacking cryptography to building an SDLC. Chris' professional experience includes stints at Symantec, @stake, and the US Department of Defense, where he specialized in software security assessments, penetration testing, and vulnerability research. Along with experts from more than 30 US and international cyber security organizations, he recently helped develop the CWE/SANS Top 25 Most Dangerous Programming Errors.<br>
| |
| − | <br>
| |
| − | '''<font color=red>James Flom</font>''' has been working in the computer industry for the past sixteen years and has spent the last twelve heavily involved in computer and network security. As lead operations engineer of Pilot Network Services' security department he researched network and computer threats on a daily basis protecting some of the largest companies and organizations in the world. He designed and implemented what was believed to be at the time, the largest network intrusion detection system in the world, protecting over half a million computers. Mr. Flom later joined Digital Island (acquired by Cable & Wireless and merged with Exodus), where he created new product offerings for the Security Operations Center he was brought on to build. After the merger with Exodus James joined the Cyber Attack Tiger Team and assisted with the detection and recovery of several global network security compromises. Mr. Flom later became the director of consulting services for Kliosystems before co-founding SecTheory. He is a member of IACSP.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Robert “RSnake” Hansen</font>''', CISSP is the founder of SecTheory and has worked for Digital Island, Exodus Communications and Cable & Wireless in varying roles from Sr. Security Architect and eventually product managing many of the managed security services product lines. He also worked at eBay as a Sr. Global Product Manager of Trust and Safety, focusing on anti-phishing, anti-DHTML malware and anti-virus strategies. Later he worked as a director of product management for Realtor.com. Robert sits on the advisory board for the Intrepidus Group, Just Thrive, previously sat on the technical advisory board of ClickForensics and currently contributes to the security strategy of several startup companies.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Garrett Held</font>''' is a Senior Security Consultant at Trustwave. He is a member of Trustwave's SpiderLabs - the advanced security team focused on penetration testing, incident response, and application security. He has been involved in the Information Technology industry for more than 14 years, with over 7 years specializing in Information Security. Prior to Trustwave he worked as a Security Consultant for Deloitte & Touche, where he worked with Fortune 500 corporations and state governments.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Charles Henderson</font>''' is the Director of Application Security Services in Trustwave's SpiderLabs. He has been in the information security industry for over fifteen years. His team specializes in application security including application penetration testing, code review, and training in secure development techniques. The team's clients range from the largest of the Fortune lists to small and midsized companies interested in improving their application security posture. Charles routinely speaks at various conferences around the world (including past Black Hat, SOURCE, IAFCI, OWASP AppSec USA, OWASP AppSec Europe, and Merchant Risk Council events) on various subject matters relating to application security.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Michael Howard</font>''' is a principal security program manager on the Trustworthy Computing (TwC) Group’s Security Engineering team at Microsoft, where he is responsible for managing secure design, programming, and testing techniques across the company. He is an architect of the Security Development Lifecycle (SDL), a process for improving the security of Microsoft’s software. He is also an editor of IEEE Security & Privacy, a frequent speaker at security-related conferences and he regularly publishes articles on secure coding and design, Howard is the co-author of six security books, including the award-winning Writing Secure Code, 19 Deadly Sins of Software Security, The Security Development Lifecycle and his most recent release, Writing Secure Code for Windows Vista.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Joe Jarzombek</font>''' is the Director for Software Assurance in the National Cyber Security Division of the U.S. Department of Homeland Security (DHS). He leads government interagency efforts with industry, academia, and standards organizations to shift the security paradigm away from patch management by addressing security needs in work force education and training, more comprehensive diagnostic capabilities, and security-enhanced development and acquisition practices. After retiring from the U.S. Air Force as a Lt. Col. in program management, Joe Jarzombek worked in the cyber security industry as vice president for product and process engineering. He served in two software-related positions within the Office of the Secretary of Defense prior to accepting his current DHS position. Throughout his career he has actively lead process improvement initiatives, including serving on the CMMI Product Development Team and later on the CMMI Steering Group. He has continued to co-lead efforts to integrate safety and security into integrated Capability Maturity Models (CMMs).<br>
| |
| − | <br>
| |
| − | '''<font color=red>Samy Kamkar</font>''' is best known for the Samy worm, the first XSS worm, infecting over one million users on MySpace in less than 24 hours. A co-founder of Fonality, Inc., an IP PBX company, Samy previously led the development of all top-level domain name server software and systems for Global Domains International (.ws). In the past 10 years, Samy has focused on evolutionary and genetic algorithmic software development, Voice over IP software development, automated security and vulnerability research in network security, reverse engineering, and network gaming.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Dr. Karen Lu</font>''' is a principal research engineer at Gemalto, a digital security company. Her research interests include cloud security, Internet security, web application security, networking, communications, and smart card applications. She has published over 50 papers and holds 8 patents. Karen has a PhD in Computer and Electrical Engineering from the University of Pittsburgh in the United States. She is a Certified Information System Security Professional (CISSP), a senior member of IEEE, and a member of OWASP.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Ernest Mueller</font>''' got in trouble for security scanning his company’s systems during his first college internship back in 1990. After graduating from Rice University, he did systems work for FedEx corporate IT back when Cops, Crack, and SATAN were the hot security tools. After working for a Web startup, he moved to Austin to manage the Web Systems team at National Instruments. Currently, Ernest is the Web systems architect on the LabVIEW team for NI’s cloud-based SaaS products. He is active in the DevOps movement, the Austin chapter of OWASP, the Austin Cloud Computing Users Group, and writes for theagileadmin.com.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Jay Paz</font>''', SCJP, GSEC, GSSP-Java, a web application developer for over 10 years, joined the UT Austin Information Security Office as an Information Security Analyst in July of 2008. With his experience and knowledge of the UT development environment, he was able to make an immediate impact on the ISO Risk Management team. His main focus is application security, however the team is tasked with assessing risk for the entire enterprise. From printers to credit card terminals, from border devices to CAT I compliant servers, they take care of it all.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Pete Perfetti</font>''' has been working in information security for fifteen years. He has been involved in IT Security for the financial services industry for ten years where he has worked as an Information Security Officer as well as having been responsible for vulnerability and threat management, and security engineering. Mr. Perfetti worked for Viacom and MTV as the Manager of Systems Administration and was the Director of IT Risk Management for the National Basketball Association. He has a broad range of experience in both operations and security. He was formerly the VP of the NY/NJ Metro Chapter of OWASP and is currently a board member of the local chapter. Mr. Perfetti’s accomplishments have been discussed in two books on achieving high performing, stable, and secure infrastructure. Currently Mr. Perfetti operates IMPACT Security LLC, a private security contractor firm, that specializes in Incident & Audit Response, Prevention, and Recovery; as well as developing, enhancing, and implementing Security and Risk Management programs.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Charlie Scott</font>''', CISSP, GSEC, GCIH, GCPM, has worked in information security for over ten years. He joined the UT Austin Information Security Office as a Sr. Information Security Analyst in 2006, after working for the City of Austin and several Internet data centers. He has a strong background in network and system security, and finds application security fun and challenging-especially in a distributed campus environment. Charlie is currently pursuing his MS in Information Security Engineering.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Josh Sokol</font>''', CISSP graduated from the University of Texas at Austin with a BS in Computer Science in 2002. Since that time, he has worked for several large companies including AMD and BearingPoint, spent some time as a military contractor, and is currently employed as the Information Security Program Owner at National Instruments. In his current role, Josh manages all compliance, security architecture, risk management, and vulnerability management activies for NI.<br>
| |
| − | <br>
| |
| − | '''<font color=red>Matt Tesauro</font>''' is a security consultant for Praetorian, an independent security firm that built its reputation on its expertise, integrity, professionalism, and client satisfaction. He has worked in Information Technology for more than 10 years. His focus has been in application security including testing, code reviews, design reviews and training. Matt is currently on the board of the OWASP Foundation and is the project leader of the OWASP WTE (Web Testing Environment) which produces Live CDs and Virtual Machines. Matt has presented and provided training at industry events including DHS Software Assurance Workshop, AppSec EU, AppSec US, and AppSec Brazil.<br>
| |
| − | <br>
| |
| | | | |
| | ==== Volunteers ==== | | ==== Volunteers ==== |
| Line 251: |
Line 157: |
| | {| | | {| |
| | |- | | |- |
| − | | '''YOUR COMPANY NAME AND LOGO COULD BE HERE''' | + | | [[Image:Symantec.png|250px|link=http://www.symantec.com]] |
| | + | | [[Image:Fortify.png|250px|link=http://www.fortify.com]] |
| | |- | | |- |
| | | | | | |
| Line 258: |
Line 165: |
| | {| | | {| |
| | |- | | |- |
| − | | [[Image:Gemalto.jpg|185px|link=http://www.gemalto.com]] | + | | [[Image:Impactsecurityllc.png|150px|link=http://www.impactsecurityllc.net]] |
| − | | [[Image:Whitehat.jpg|274px|link=http://www.whitehatsec.com]] | + | <br>'''Impact Security LLC''' |
| − | | [[Image:Splunk.jpg|link=http://www.splunk.com]] | + | | [[Image:IBM.png|150px|link=http://www.ibm.com]] |
| − | | [[Image:Impactsecurityllc.png|link=http://www.impactsecurityllc.net]]<br>'''Impact Security LLC''' | + | | [[Image:Imperva_2color_RGB.jpg|250px|link=http://www.imperva.com]] |
| | + | | [[Image:Whitehat.gif|250px|link=http://www.whitehatsec.com]] |
| | |- | | |- |
| | | | | | |
| Line 268: |
Line 176: |
| | {| | | {| |
| | |- | | |- |
| − | | [[Image:K2share.gif|150px|link=http://www.k2share.com]] | + | | [[Image:Gemalto.jpg|185px|link=http://www.gemalto.com]] |
| − | | [[Image:Dexa.jpg|150px|link=http://www.dexasystems.com]] | + | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] |
| − | | [[Image:Expandingsecurity.jpg|150px|link=http://www.expandingsecurity.com]]<br>'''Expanding Security''' | + | | [[Image:radware.png|150px|link=http://www.radware.com]] |
| − | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] | + | | [[Image:Cigital.png|150px|link=http://www.cigital.com]] |
| | |- | | |- |
| − | | [[Image:Fortify.png|150px|link=http://www.fortify.com]] | + | | [[Image:Atsec.png|150px|link=http://www.atsec.com]] |
| − | | [[Image:Veracode.gif|150px|link=http://www.veracode.com]] | + | | [[Image:Fireeye.png|150px|link=http://www.fireeye.com]] |
| − | | [[Image:Praetorian.jpg|150px|link=http://www.praetorian.com]] | + | | [[Image:Symplified.png|150px|link=http://www.symplified.com]] |
| − | | [[Image:Denim-group.png|150px|link=http://www.denimgroup.com]] | + | | |
| | |} | | |} |
| − | | + | == Lanyard Sponsor == |
| − | == Badge Sponsor == | |
| | {| | | {| |
| | |- | | |- |
| − | | [[Image:Gemalto.jpg|185px|link=http://www.gemalto.com]] | + | | [[Image:Praetorian.png|200px|link=http://www.praetorian.com]] |
| | |- | | |- |
| | | | | | |
| | + | |} |
| | + | == Happy Hour Sponsor == |
| | + | {| |
| | + | |- |
| | + | | [[Image:Trustwave.jpg|150px|link=http://www.trustwave.com]] |
| | + | |} |
| | + | == Breakfast Taco Sponsor == |
| | + | {| |
| | + | |- |
| | + | | [[Image:Honeyapps.jpg|150px|link=http://www.honeyapps.com]] |
| | |} | | |} |
| | | | |
| Line 292: |
Line 209: |
| | == Norris Conference Center == | | == Norris Conference Center == |
| | | | |
| − | LASCON 2010 will be taking place at the [http://www.norriscenters.com/Austin/ Norris Conference Center] in Austin, TX. | + | LASCON 2011 will be taking place at the [http://www.norriscenters.com/Austin/ Norris Conference Center] in Austin, TX. |
| | | | |
| | <br> | | <br> |
| Line 302: |
Line 219: |
| | ==== Hotel ==== | | ==== Hotel ==== |
| | | | |
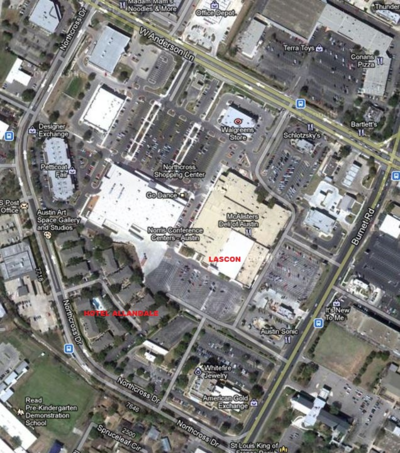
| − | We have partnered with the Embassy Suites in the Arboretum and you can book rooms at using the discount code: LAS at 1-800-362-2779 begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting or you can | + | We have partnered with the Hotel Allandale, located right next to the Norris Conference Center, for this year's conference. You can call the hotel and mention that you would like the $90/night LASCON rate and they should be able to assist you.<br> |
| − | [http://embassysuites.hilton.com/en/es/groups/personalized/AUSESES-LAS-20101025/index.jhtml?WT.mc_id=POG Book your room online.]
| |
| | | | |
| − | Embassy Suites Austin - Arboretum
| + | Hotel Allandale<br> |
| − | 9505 Stonelake Boulevard
| + | 7685 Northcross Drive<br> |
| − | Austin, Texas | + | Austin, TX 78757<br> |
| − | 78759
| + | <br> |
| − |
| + | http://hotelallandale.com<br> |
| − | The rooms are $139 for a double or queen, includes hot breakfast and shuttle to/from the event. | + | <br> |
| | + | The rooms are $90 for a King size room and includes a full breakfast daily and a social hour Monday-Thursday. Hotel Allandale is walking distance from the Norris Conference Center! |
| | | | |
| − | [http://embassysuites.hilton.com/en/es/groups/personalized/AUSESES-LAS-20101025/index.jhtml?WT.mc_id=POG Book your room online with the LASCON discount.] | + | [[Image:Allandale.png|400px]] |
| | | | |
| | ==== Sponsorship Options ==== | | ==== Sponsorship Options ==== |
| | | | |
| − | We are currently soliciting sponsors for the LASCON 2010 Conference. Please refer to our [http://www.owasp.org/images/2/24/LASCON_Sponsorship_Options.pdf List of Sponsorship Opportunities]
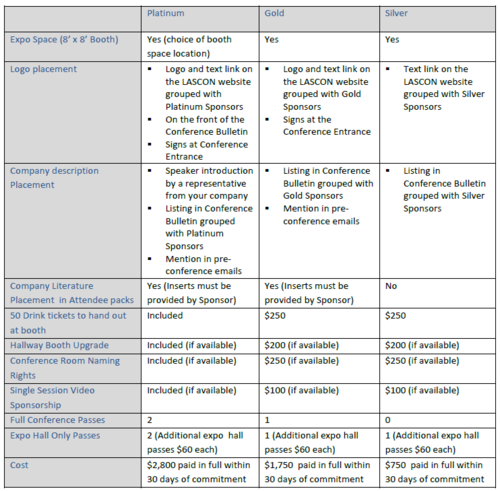
| + | == Booth Sponsorship Opportunities == |
| | + | [[Image:Lascon_2011_booth_sponsorships.png|500px]] |
| | | | |
| − | Please contact [mailto:james.wickett@owasp.org James Wickett] for more information.
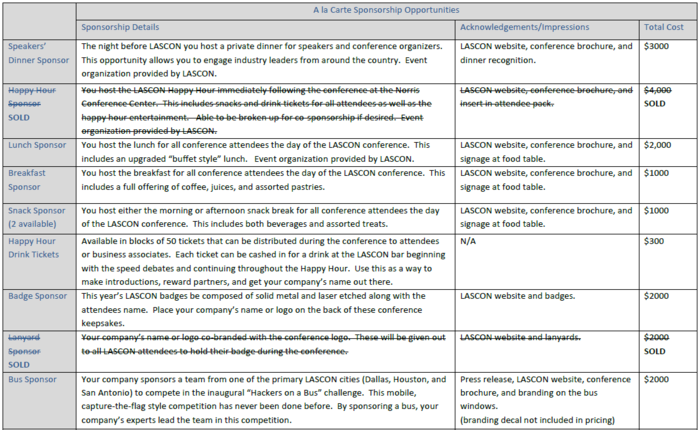
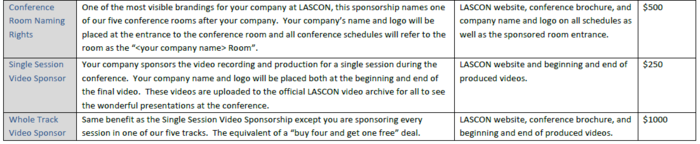
| + | == A La Carte Sponsorship Opportunities == |
| | + | [[Image:Lascon_2011_a_la_carte_1.png|700px]] |
| | + | [[Image:Lascon_2011_a_la_carte_2.png|700px]] |
| | | | |
| − | Slots are going fast so contact us to sponsor today!
| + | Please [mailto:lascon@owasp.org contact us] for more information. |
| − | | |
| − | [[Image:LASCON_2010_Sponsors.jpg]]
| |
| − | | |
| − | [[Image:LASCON_2010_Additional.jpg]]
| |
| | | | |
| | ==== Call for Papers ==== | | ==== Call for Papers ==== |
| | | | |
| − | '''Sorry, the CFP has ended for LASCON 2010. Maybe next year?'''
| + | OWASP is currently soliciting papers for the Lonestar Application Security Conference (LASCON) 2011 that will take place at the Norris Conference Center in Austin, TX on October 28, 2011. |
| − | <!--
| |
| − | OWASP is currently soliciting papers for the Lonestar Application Security Conference (LASCON) 2010 that will take place at the Norris Conference Center in Austin, TX on October 29, 2010. | |
| | | | |
| − | Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2010 | + | Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2011 |
| | | | |
| | We are seeking people and organizations that want to present on any of the following topics (in no particular order): | | We are seeking people and organizations that want to present on any of the following topics (in no particular order): |
| Line 361: |
Line 275: |
| | - Any supporting research/tools (will not be released outside of CFP committee) | | - Any supporting research/tools (will not be released outside of CFP committee) |
| | | | |
| − | <br> Submission deadline is August 30th at 12PM PST (GMT -8) | + | <br> Submission deadline is August 19th at 12PM CST (GMT -6) |
| | | | |
| | | | |
| | Not everyone who submits a proposal will be able to get to present at LASCON due to limited timeslots. Also, in no way does sponsorship factor into the CFP committee's selection. Speaking slots are not for sale. | | Not everyone who submits a proposal will be able to get to present at LASCON due to limited timeslots. Also, in no way does sponsorship factor into the CFP committee's selection. Speaking slots are not for sale. |
| | | | |
| − | Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2010 Conference Website: http://www.owasp.org/index.php/Lonestar_Application_Security_Conference_2010 | + | Submit Proposals to: http://www.easychair.org/conferences/?conf=lascon2011 |
| | + | <br> |
| | + | Conference Website: http://www.lascon.org |
| | | | |
| | <br> Please forward to all interested practitioners and colleagues. | | <br> Please forward to all interested practitioners and colleagues. |
| | | | |
| | <br> | | <br> |
| − | -->
| |
| | | | |
| | <headertabs /> | | <headertabs /> |
| | | | |
| − | [[Category:OWASP_AppSec_Conference]] [[Category:OWASP_AppSec_USA]] | + | [[Category:OWASP_Chapter/Events]] [[Category:OWASP_AppSec_USA]] |
We are pleased to announce that this year we will be adding on two different training classes the day before the Lonestar Application Security Conference (LASCON) on Thursday, October 27, 2011. These training classes are unlike those you see at most conferences both in content and cost. If you have already registered for LASCON, simply go to http://www.regonline.com/lascon2011 and select the "Already Registered?" link. Log in with the e-mail address you registered with and then select to edit your "Agenda". Place a check mark in the box for the training you would like to attend (or the FREE happy hour) and select "Continue" to check out. If you have not already registered for LASCON, you will have the ability to add the training of your choice on the "Agenda" screen of registration. The trainings are as follows:
Metasploit is a powerful exploit framework and a must-have tool for penetration testers. Armitage builds a workflow on top of the Metasploit framework and exposes its most advanced capabilities. This demonstration and lab oriented session will teach you Metasploit and Armitage for the purpose of emulating adversary tactics. This course will start with the basics and quickly take you into the workflow of modern threats. You'll learn how to create trojan files, manage covert HTTP and HTTPS communications, set up social engineering attacks, and use pivoting to take over a network.
To participate in the labs, you must have VMWare Player, VMWare Fusion, or VMWare Workstation installed.
This training class is for new managers & leads accountable for integrating Application Security into their enterprise. The course will walk through various success factors, including a mixture of strategy, policy, and technology considerations. The course will help attendees develop incremental plans they can employ to make both short-term and long-term measurable improvements to their enterprise Application Security.
Seats in these trainings will be very limited and registrants will be accepted on a first-come, first-served basis. Sign up today!
We will take all the help we can get to pull off the best Web Application Security Conference of the year! Volunteers get free admission. This is your chance to rub elbows with the big players and mingle with potential networking contacts or even future employers!
We have partnered with the Hotel Allandale, located right next to the Norris Conference Center, for this year's conference. You can call the hotel and mention that you would like the $90/night LASCON rate and they should be able to assist you.
OWASP is currently soliciting papers for the Lonestar Application Security Conference (LASCON) 2011 that will take place at the Norris Conference Center in Austin, TX on October 28, 2011.
We are seeking people and organizations that want to present on any of the following topics (in no particular order):