This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Lonestar Application Security Conference 2010
LASCON is happening on October 29th, 2010 in Austin, TX
Registration Link | Speaker List Posted! | Follow LASCONATX on Twitter | Norris Conference Center
Welcome
|
|
|
Registration
Registration Is Now Open!
OWASP Membership ($50 annual membership fee) gets you a discount on registration.
| Non-Members (Includes a 1 year OWASP membership) | $150 Until 10/26/2010 | $200 After 10/26/2010 |
| OWASP Members | $100 Until 10/26/2010 | $200 After 10/26/2010 |
| Students with valid Student ID (must be shown at the door) | $80 Until 10/26/2010 | $2000 After 10/26/2010 |
Who Should Attend LASCON 2010:
- Application Developers
- Application Testers and Quality Assurance
- Application Project Management and Staff
- Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, Deputies, Associates and Staff
- Chief Financial Officers, Auditors, and Staff Responsible for IT Security Oversight and Compliance
- Security Managers and Staff
- Executives, Managers, and Staff Responsible for IT Security Governance
- IT Professionals Interesting in Improving IT Security
For student discount, you must present proof of current enrollment when picking up your badge. No exceptions.
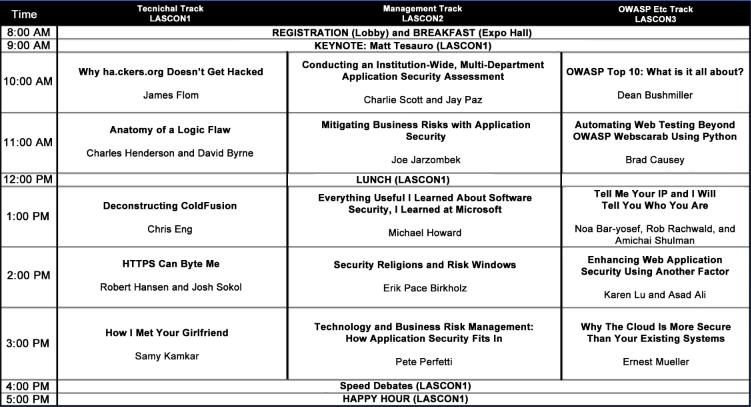
Sessions
Technical Track
James Flom
Why ha.ckers.org Doesn’t Get Hacked
Ha.ckers.org has suffered nearly every attack a website can. These attacks include robots, sophisticated web-based attacks, brute force, denial of service, and network based attacks. This speech will explain the other side of protecting high risk websites - the configurations, operating system, and network.
Charles Henderson
Anatomy of a Logic Flaw
Traditional vulnerabilities like SQL Injection, buffer overflows, etc, have well established techniques for discovery and prevention. On the other hand, logic flaws are incredibly diverse and often unique to the specific application or business organization. Because of this, logic flaws have taken on a near mythical status. In the myth, logic flaws are nearly impossible to find until the elite of the elite hackers launch an attack to completely own the application. The reality is far different; logic flaws are not the complex nightmare that many have made them out to be. This presentation will use real-world examples to show how logic flaws are typically introduced into an application, how they can be consistently detected during testing, and how they can be prevented during development. Instead of hoping for magic, repeatable processes will be outlined for each of those items. This will prove beneficial to anyone responsible for application security: programmers, architects, managers, and pen testers.
Management Track
Charlie Scott and Jay Paz
Conducting an Instiution-Wide, Multi-Department Application Security Assessment
From early 2009 until mid-2010, the Information Security Office at the University of Texas at Austin conducted a security assessment of over 250 web applications, spanning over 30 departments. The objectives of this assessment were to provide a thorough security review of existing applications, and act as an education and awareness exercise for the application developers. This presentation covers the political, technical, and scheduling challenges encountered on this assessment, how they were overcome, the results of the assessment and the changes they brought about, and lessons learned by the assessment team.
Joe Jarzombek
Mitigating Business Risks with Application Security
With today’s global IT software supply chain, project management and software/systems engineering processes must explicitly address security risks posed by exploitable software. Traditionally, these disciplines have not clearly and directly focused on software security risks that can be passed from projects to the organization. Software security assurance processes and practices span development and acquisition and can be used to enhance project management and quality assurance activities. Mr. Jarzombek explains the critical need for adherence to the practices, guidelines, rules, and principles used to build security into every phase of software development.
OWASP Etc Track
Dean Bushmiller
OWASP Top 10: What is it all about?
Everyone knows exactly what the OWASP top ten security threats are, right? Well sort of... I ask people if they have heard of the top ten they say yes. I ask them to name a few they pause, then they blurt out 2-3. Then I ask them to explain those 2-3 and they look at me like a deer-in-the-headlights. I want to make sure that everyone who walks out of the presentation can clearly define the top ten and be able to communicate to another what each of the top ten vulnerabilites are.
Brad Causey
Automating Web Testing Beyond OWASP Webscarab Using Python
This presentation will illustrate ways to improve web security assessments by using advanced features in OWASP Webscarab and extending your options with automation using Python.
Speakers
Asad Ali Noa Bar-yosef Erik Pace Birkholz Dean Bushmiller Brad Causey Chris Eng James Flom Robert Hansen Charles Henderson Michael Howard Joe Jarzombek Samy Kamkar Karen Lu Ernest Mueller Jay Paz Pete Perfetti Rob Rachwald Charlie Scott Amichai Shulman Josh Sokol
Volunteers
Volunteers Needed!
Get involved!
We will take all the help we can get to pull off the best Web Application Security Conference of the year! Volunteers get free admission. This is your chance to rub elbows with the big players and mingle with potential networking contacts or even future employers!
Please contact james.wickett(at)owasp.org to volunteer for a specific area:
- Room Monitors
- Speakers and Trainers
- Vendors
- Registration
- Facilities
More opportunities and areas will be added as time goes on. Our File:Volunteer Sheet.doc can be downloaded which outlines some of the responsibilities and available positions. Note: this document references the the DC conference last year, this is just for a general guideline. Updated document coming soon.
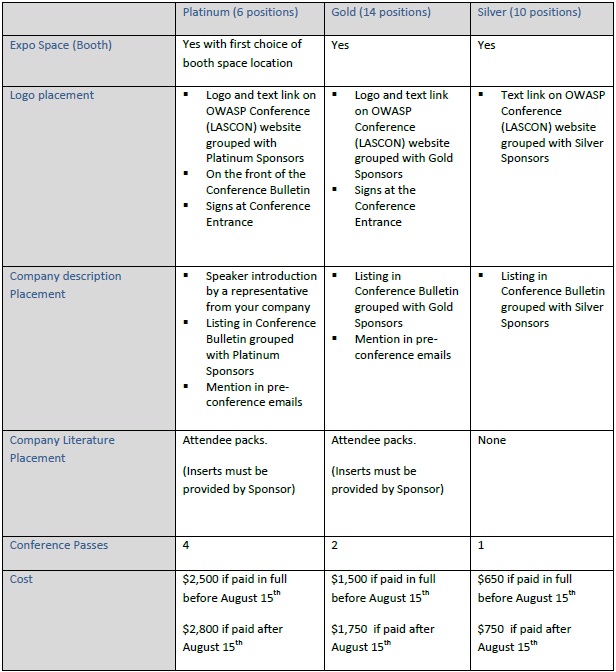
Sponsors
Platinum Sponsors
| YOUR COMPANY NAME AND LOGO COULD BE HERE |
Gold Sponsors

|

|

|
 Impact Security LLC |
Silver Sponsors

|

|
 Expanding Security |
|
| |
|

|
|
Badge Sponsor

|
Venue
Norris Conference Center
LASCON 2010 will be taking place at the Norris Conference Center in Austin, TX.
Travel
Traveling to the Austin Metro Area
Hotel
We have partnered with the Embassy Suites in the Arboretum and you can book rooms at using the discount code: LAS at 1-800-362-2779 begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting begin_of_the_skype_highlighting 1-800-362-2779 end_of_the_skype_highlighting or you can Book your room online.
Embassy Suites Austin - Arboretum 9505 Stonelake Boulevard Austin, Texas 78759
The rooms are $139 for a double or queen, includes hot breakfast and shuttle to/from the event.
Book your room online with the LASCON discount.
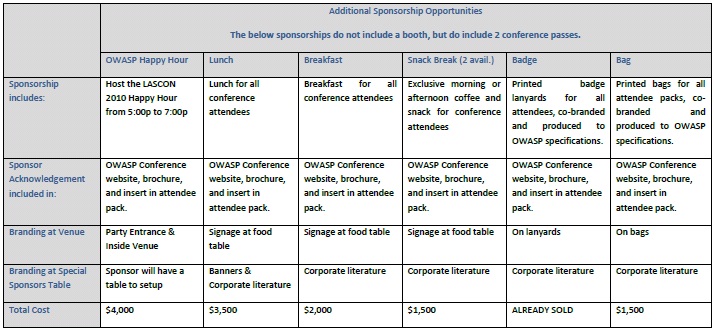
Sponsorship Options
We are currently soliciting sponsors for the LASCON 2010 Conference. Please refer to our List of Sponsorship Opportunities
Please contact James Wickett for more information.
Slots are going fast so contact us to sponsor today!
Call for Papers
Sorry, the CFP has ended for LASCON 2010. Maybe next year?