This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Front Range OWASP Conference 2013

|

|
|

|
|
|
|
- Introduction
- Registration
- Venue
- Conference Schedule
- Speakers
- Presentations
- Event Sponsors
- Hotel and Travel
- Capture the Flag
- Presentation Materials
Welcome to SnowFROC 2013 - the 5th Annual Front Range OWASP Security Conference
The Colorado OWASP chapters are proud to present the 5th annual SnowFROC. Join 300 other developers, business owners, and security professionals for a day-and-a-half of presentations, training, and Birds-of-a-Feather (BoaF) sessions. The SnowFROC 2013 keynote speaker is Neal Ziring, Technical Director of InfoProtection at NSA.
The conference will occur on Thursday, March 28th at the Denver Marriott City Center and will feature four primary tracks:
- High-Level Technical
- Deep-Dive / Hands-on Technical
- Management
- Legal
Running in parallel to the conference proceedings will be a capture the flag (CTF) hacking competition developed exclusively for SnowFROC by Boulder OWASP chapter members. The day will conclude with a moderated panel discussion featuring top industry leaders.
On Friday, March 29, Aaron Weaver will teach a course in secure coding. This training is free to SnowFROC attendees!
Friday will also offer BoaF sessions. Join like-minded industry leaders and discuss pressing issues facing the industry and you. BoaF sessions are self-lead and may address and issue you would like. Pitch your idea and get the ball rolling!
Finally, Friday will feature a postmortem of the CTF tournament. In addition to discussing solutions, techniques, and tools, we will encourage participants to attack the previously out-of-bounds CTF framework. Itching to break into the scoreboard and rack up the points? The gloves come off Friday morning.
Conference Committee
Mark Major: Director
Brad Carvalho: Sponsorship, Executive events
Craig Klosterman: Merchandise
Steve Kosten: Sponsorship, Executive events
Glen Matthes: Planning
Chris Rossi: CTF, Networking events
Greg Foss: CTF
Colorado Chapter Hosts
OWASP Boulder chapter: Mark Major
OWASP Denver chapter: Steve Kosten, Brad Carvalho (acting)
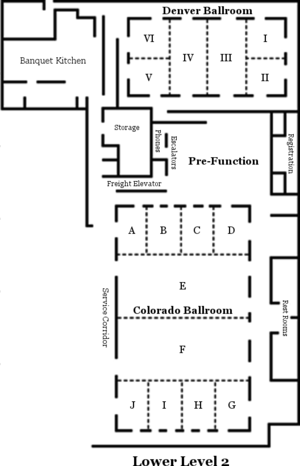
Conference Location
|
SnowFROC 2013 Schedule
Joe Brady
| Joe Brady is a Senior Solutions Architect at Veracode with over 25 years of experience in software application development, IT risk management, and security. He works consultatively with customers and prospects to help them evaluate a Veracode solution for managing their application security risk.
His professional experience includes advising customers on end point data encryption solutions at Credant Technology (now Dell); IT risk and portfolio management at Prosight (now Oracle); and, UNIX symmetric multiprocessor computing for high performance databases and parallel programming research at Sequent Computers (now IBM). In addition, he has experience architecting and developing software applications, as a developer and manager. Joe began programming as a physics undergrad and developed early microprocessor based instrumentation at Cornell, where he received a M.S. degree in Applied and Engineering Physics. |
Helen Bravo
| Helen Bravo is the Product Manager at Checkmarx. Helen has more than fifteen years of experience in software development, IT security and source-code analysis.
Prior to working at Checkmarx, Helen has worked in Comverse one of the biggest Israeli Hi-tech firms as a software engineer and product manager for security matters. Helen holds a B.A. in Economics and Business Administration from the Israeli University of Haifa and started her development career at the age of 11. |
Jason Chan
| Jason Chan is an Engineering Director at Netflix, currently working on the security of Netflix's cloud deployment. His areas of responsibility include application, infrastructure, and operational security for the Netflix streaming video service. Prior to joining Netflix, he led the information security team at VMware and spent most of his earlier career in security consulting for firms such as @stake and iSEC Partners. |
Danny Chrastil
| Danny Chrastil is a security consultant with BT Assure who has specialized in information security for over 3 years. Danny has a strong background in application development and server administration which led him into the security field after being asked to remediate a compromised server for a large eCommerce application. Using his experience as both a security consultant and programmer, Danny works with developers on the awareness of security principles and their importance within the development lifecycle. |
Larry Conklin
| Please visit Larry's OWASP profile page. |
Gregory Disney-Leugers
| Gregory Disney-Leugers is a systems engineer from Athens, OH with his wife Kait, He attended United Stares Air Force Institute of Technology and Defense Acquisition University. He is the developer of OWASPMantra OS and The Onion Server. |
Maureen Donohue Feinroth
| Maureen D. Feinroth, Esq, CIPP/IT, CIPP/E is the Founder and CEO of Capital Privacy Solutions, a consulting firm dedicated to providing clients with privacy consulting, training & education and data management services.
Maureen is a recognized subject matter expert in international compliance, particularly the EU Directive, the Hong Kong Data Protection Ordinance and transborder data flow issues in the international marketplace. She is experienced with the provisions of DNC, FOIA, ECPA, FISMA, the Federal Privacy Act, Paperwork Reduction Act, Computer Security Act, OMB Circular A-130, FISCAM, HIPAA/HITECH, GLBA, FCRA, EFTA, COPPA, ECPA, PATRIOT Act and Sarbanes-Oxley. She assisted in development of NIST standards across information security including implementation measures for HSPD 12 compliance. Her consulting responsibilities and career information security privacy experience include the identification, research and analysis of all legislation at the state, federal and international levels, as well as the self-regulatory programs. |
Andrew Earle
| Andrew Earle is a Security Solutions Architect for HP Enterprise Security Products (ESP). Andy has spent 3+ years designing and delivering application security programs, technology, and services for US Federal and commercial customers, specifically around HP's Fortify appsec products. Andy was previously the product manager for a high assurance multi-level secure operating system at BAE Systems, and Presales Engineer for various web development and mobile security firms. Early experience includes software engineering, mobile application development, and lifeguarding at his neighborhood pool. Andy has a B.S. in Systems Engineering from the University of Virginia. |
Tom Glanville
| Tom is the founder and CEO at Identity Theft Loss Prevention, LLC. Tom served in the United States Air Force as an Avionics Flight Control System Specialist during Desert Storm. He received a metal for his heroic efforts for saving lives and aircraft. Following his military service, he worked as a government contractor on highly sophisticated security systems for Classified and Top Secret information.
Due to Tom falling victim to ID Theft and Fraud 4 times between 1996 and 1998. At that time identity theft was relatively new with very few resources for victims. Learning from his personal experience, combined with his military training, Tom founded Identity Theft Loss Prevention to educate individuals, families, and businesses. The company has become nationally recognized for practice assessment, management, and training to identify and limit information exposure. Recently, Tom was invited to participate in an elite group that advises the Federal Bureau of Investigation Cyber Crimes Division and the Dept of Homeland Security on matters of national security. |
Alan Jex
| Alan is a Chief Security Architect at HP and is a CISSP. He is responsible for performing penetration tests and implementing security best practices for the PPS organization on web connected printers. Alan worked at Symantec as a Principle Software Engineer on enterprise security products. He worked at Novell as a Senior Software Engineer on desktop and server management. Alan graduated from BYU with a B.S. in Computer Science. He participates in the local Salt Lake OWASP chapter. |
Robert Lelewski
| Robert Lelewski is an Engagement Lead for IBM's Emergency Response Service and is the lead of IBM's Computer Security and Incident Response Plan (CSIRP) offering. He has worked on numerous cases involving the topics of intellectual property theft, malware analysis, embezzlement, child pornography, and other issues. He has testified before state and federal courts and has been endorsed as an expert on computer forensics.
Robert holds a Bachelor degree in Economic Crime Investigation from Syracuse University, a Masters degree in Technology Management and a certificate in Research and Development Management from the University of Denver, and is currently pursuing a Masters of Business Administration from the University of Northern Iowa. Additionally, Robert holds several computer forensic and security related certifications including the EnCE, ACE, CCE, CISSP, CISA, CISM, Security+, and CASP. |
Jim Manico
| Jim Manico is the VP of Security Architecture for WhiteHat Security, a web security firm. He authors and delivers developer security awareness training for WhiteHat Security and has a background as a software developer and architect. Jim is also a global board member for the OWASP foundation. He manages and participates in several OWASP projects, including the OWASP cheat sheet series and the OWASP podcast series. |
Jon McCoy
| Jon McCoy is focused on .NET Framework Application Security, releasing a number of tool and whitepapers in the area of .NET Framework Security. He runs www.DigitalBodyGuard.com a ThinkTank Firm that engages in development, protecting & penetration-testing digital assets from desktop applications to enterprise infrastructure. DigitalBodyGuard has a focus on .NET Application Security well beyond Reverse Engineering and Anti-Reverse Engineering. |
Dan Rojas
| Dan is a Vice President at IntraNext Systems. As Vice President and Chief Product Evangelist Mr. Rojas’ responsibilities include strategic planning, business development and execution to enable rapid growth of the IntraNext SafeData offering.
Before joining IntraNext, Mr. Rojas was a Director and Managing Director at Coalfire, a leading IT systems security and compliance company. Mr. Rojas’ was responsible for national PCI, HIPAA and Federal practices. Mr. Rojas has over 20 years of communications and information technology industry experience in the areas of Corporate Strategy, IT Operations, Business Development and Executive Management. Previously, he was Vice President of Technology at Alpine Access, a virtual BPO service provider from 2007 to 2011. At Inflow, a complex web hosting company, (1998-2005) Mr. Rojas led many major worldwide client programs delivering systems and information technology architecture, design, security and implementation for its global clients. Management of secure and highly reliable infrastructure and data network services including firewall management, operating systems management, data storage and backup, monitoring, BC/DR and consulting services around e-business and web architecture. Mr. Rojas also held executive management positions in start-up enterprises as well as product development and management positions within the U.S. Air Force. |
Jon Rose
| Hacker, developer, product manager, and trainer, Jon Rose has been working in the security industry for his entire career. His current mission is to make security accessible to developers, startups, and service providers through a variety of ventures. Outside technology, his other interests include running, camping, coffee, robots, and beer.
http://www.linkedin.com/in/jrose400 |
Russell Shumway
| Russ is the Computer Forensics Lead Aerstone. Russ has over 18 years of experience as an Information Security Consultant, providing technical incident response, computer security, forensics, and electronic discovery advice to both public and private sector organizations. Previous clients include large financial institutions in the U.S. and Europe, including 7 of the 10 largest banks in the U.S. and 13 of the top 50 in the world, as well as health care, insurance and high tech manufacturing organizations.
Prior to joining Aerstone, he spent 5 years as the Technical Director for Electronic Discovery and Forensics for SNR Denton, one of the top 25 law firms in the world, where he assisted clients and attorneys in technical investigations, discovery collection and processing, and the development of discovery protocols. His experience also includes consulting with Guardent and Global Integrity Corporations. As the Technical Director for Response Services for Global Integrity he managed the company's Open Source Monitoring Program and assisted in the development and implementation of the Information Sharing and Analysis Center (ISAC) for the financial services sector. He has provided incident response consulting on major security breaches where potential losses exceeded $50 million dollars. As a U.S. Army Reserve Officer, he performed vulnerability assessments and audits of classified and unclassified military computer networks for the Army Computer Emergency Response Team. He was the first person (military or civilian) to be certified to execute penetration tests on Army systems. Mr. Shumway is a Certified Information Systems Security Professional (CISSP). He graduated from the University of Pennsylvania in 1983 and received a M.S. in the Management of Information Systems and an M.B.A. from the Katz Graduate School of Business in 1995. Mr. Shumway has developed and taught graduate level courses at the University of Virginia and at the University of Fairfax. |
Casey Smith
| Casey is an Information Security Analyst at FirstBank. |
Aaron Weaver
| Aaron Weaver is Principal Security Analyst at Pearson Education, the leading learning and publishing company. He has played various roles including software developer, system engineer, embedded developer to IT security. He also leads OWASP Philadelphia. Experience includes mobile security, web application security, penetration testing and embedded development. Aaron has also worked on developer and QA awareness to increase security in the software development lifecycle and has held numerous training sessions.
Aaron has spoken at regional chapter events including OWASP, Infragard, ISSA, Cloud Security Alliance, Philadelphia Secure World and ISACA. When he has time Aaron likes to make sawdust in his workshop. |
Dan Wilson
| Dan is a managing consultant at IBM Security Services and directs Penetration Testing and Emergency Response Services for IBM in the North Amercian region. Dan's team assists clients in proactively identifying existing security threats to company assets and assists them in developing plans to reduce the risk of and prepare for the handling of cyber-incidents. When incidents do occur, his team will respond 24x7 to assist the client in quickly eliminating the threat.
Dan has been with IBM for 18 years, with 12 years in Information Security. He graduated with a Bachelors degree in Computer Science from Brigham Young University, and has completed an MBA with Regis University. Dan has worked in numerous areas of security at IBM including: Infrastructure security policy and best practices, malware threat prevention, vulnerability management, penetration testing and application security, and incident and forensic response. |
David Willson
| David is a leading authority in cyber security and the law. He is a licensed attorney in NY, CT, and CO, and owner of Titan Info Security Group, a Risk Management and Cyber Security law firm, focused on technology and the law, and helping companies lower the risk of a cyber-incident and reducing or eliminating the liability associated with loss or theft of information. He also assists companies with difficult legal/cyber-security issues.
David is a retired Army JAG officer. During his 20 years in the Army he provided legal advice in computer network operations, information security and international law to the DoD and NSA and was the legal advisor for what is now CYBERCOM. He has published many articles, such as, "Hacking Back In Self-Defense: Is It Legal; Should It Be?", and recently, "Cyber War or Cyber Cold War?". His speaking engagements include: the FBI ICCS conf., RSA, CSI, HTCIA, ISSA, FBCINC, the 4th Int'l Cyber Crime Conf., Australia, Cornerstones of Trust, FISSEA, ASIS, and others. He holds the CISSP & Security + certifications and has two LLM’s in International Law and in Intellectual Property law. He is a VP of his local ISSA chapter and a member of InfraGard. He was recently quoted in a Fox News Exclusive, and his recent article was published on Fox News: Is the US Already Engaged in a Cyber War? |
Zachary Wolff
| Zak is an Advanced R&D Engineer at LogRhythm Labs. |
Neal Ziring
| Mr. Neal Ziring is the Technical Director for the National Security Agency's Information Assurance Directorate (IAD), serving as a technical advisor to the IAD Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across the Information Assurance mission space. Mr. Ziring tracks technical activities, promotes technical health of the staff, and acts as liaison to various industry, intelligence, academic, and government partners. As part of his role, he guides IAD’s academic outreach program, acting as a technical liaison to several universities that are participants in the National Centers for Academic Excellence - Research (CAD-R) program. His personal expertise areas include router security, IPv6, VM-based secure systems, cloud computing, cross-domain information exchange, and mobile code security.
Mr. Ziring received B.S. degrees in computer science and electrical engineering (1985), and an M.S. in computer science (1986), all from Washington University in St. Louis. Since then, he has also taken courses from Columbia University and University of Maryland Baltimore County. Virtually Mr. Ziring’s entire government career has been based in the NSA Information Assurance Directorate. He joined NSA in late 1988, working on software tools and cryptosystem simulation. In the 1990s he began working in IA Evaluations and, except for brief tours, has been there ever since. From 2003 to 2005 he held the position of technical director for the IA Evaluations System and Network Attack Center (SNAC). Between 2006 and 2010 he was detailed to the NSA Mission Systems Development group as the security architect. Mr. Ziring is maintains his Cisco Certified Security Professional (CCSP) certificates. Prior to joining NSA, Mr. Ziring was a member of technical staff at AT&T Bell Laboratories. In addition to work, Neal enjoys martial arts, running, and playing classical guitar. He holds a 3rd degree black belt in Shorinji Kempo. |
Keynote Address: 08:30 - 09:30
Data Protection for the 21st Century
Neal Ziring
| Mr. Neal Ziring is the Technical Director for the National Security Agency's Information Assurance Directorate (IAD), serving as a technical advisor to the IAD Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across the Information Assurance mission space. Mr. Ziring tracks technical activities, promotes technical health of the staff, and acts as liaison to various industry, intelligence, academic, and government partners. As part of his role, he guides IAD’s academic outreach program, acting as a technical liaison to several universities that are participants in the National Centers for Academic Excellence - Research (CAD-R) program. His personal expertise areas include router security, IPv6, VM-based secure systems, cloud computing, cross-domain information exchange, and mobile code security.
Mr. Ziring received B.S. degrees in computer science and electrical engineering (1985), and an M.S. in computer science (1986), all from Washington University in St. Louis. Since then, he has also taken courses from Columbia University and University of Maryland Baltimore County. Virtually Mr. Ziring’s entire government career has been based in the NSA Information Assurance Directorate. He joined NSA in late 1988, working on software tools and cryptosystem simulation. In the 1990s he began working in IA Evaluations and, except for brief tours, has been there ever since. From 2003 to 2005 he held the position of technical director for the IA Evaluations System and Network Attack Center (SNAC). Between 2006 and 2010 he was detailed to the NSA Mission Systems Development group as the security architect. Mr. Ziring is maintains his Cisco Certified Security Professional (CCSP) certificates. Prior to joining NSA, Mr. Ziring was a member of technical staff at AT&T Bell Laboratories. In addition to work, Neal enjoys martial arts, running, and playing classical guitar. He holds a 3rd degree black belt in Shorinji Kempo. |
Session 1: 10:00 - 10:45
DevFu: The inner ninja in every application developer
Many times we try to draw a distinct line between developers and penetration testers. This creates a barrier that developers often feel intimidated to cross. The truth is that developers have an innate ability and perspective to become great penetration testers themselves.
Developers in the security industry carry a unique toolset as ethical hackers / security consultants that sets them apart from traditional penetration testers. By incorporating these skills as developers and combining them with the understanding and experience of building applications, developers can take web application penetration testing a step further than the rest.
This presentation will go over the various aspects to the developer DevFu toolbox including: deep programming knowledge, ability to write scripts on the fly, common shortcuts and their pitfalls, speaking the language, and secure coding practices. We will go over specific examples of scripts that increase productivity and extend functionality of existing pen testing programs.
Slides
Video
Track: Technical
Speaker: Danny Chrastil
SIP-Based Cloud Instances
This presentation will demonstrate the practical applications of SIP protocol for local cloud instances and how to create secure connections the cloud using SIP forwarding. Further it will present methods of securing cloud and data by using a Linux firmware router to host local based cloud domains, as well as showing secure methods of deploying these systems. In addition, the talk will show secure methods of using PHP and databases using Sqlite and MongoDB while using distributing computing between a Linux server and a Linux based firmware network appliance.
Several practical applications presented will include:
- Using Cloud-based SIP as replacement for Samba for file sharing in a corporate environment with S3 and WebDAV
- Creating a local domain such https://cloud.router.sip.com
- Connecting to the cloud from a mobile phone using SIP forwarding with SSL tunneling
- Using SIP based domains on VPNs to create a private clouds with a single point of access
There will be a demonstration on how to properly setup a Linux server to host local based domains for secure deployment, including proper deployment of Cherokee and Apache web servers for hosting SIP domains. Finally, the presentation will demonstrate properly configuration of SIP domains to the Linux based firmware network appliance.
At the end of the presentation a viewer will know how to properly deploy Linux server for SIP domain hosting and how to create secure cloud instances with SIP.
Slides
Video
Track: Deep Dive
Speaker: Greg Disney-Leugers
Digital Bounty Hunters - Decoding Bug Bounty Programs
Amid the growing trend to "crowd source" services, a few progressive enterprises are taking a new approach to information security. A potential game-changer, these companies are shifting the traditional model of IT risk assessment by opening their doors -- and their wallets -- to freelance hackers who break in without fear of legal repercussions. Bug Bounty Programs pay cash money to hackers for responsibly disclosing security vulnerabilities on production applications and networks.
This presentation will examine who these freelance digital bounty hunters are, their motivations, and their perspective on the value of bug bounty programs. It is equally as important to understand the perspective of the individuals that run these programs, how the programs fit into a comprehensive, information security framework, as well as key successes and failures to date of this new crowd-sourced model. As part of this, the discussion will review metrics from an existing program and highlight some of the more interesting bugs discovered.
Ultimately, what is the future for these bug bounty programs? Will they disrupt the existing marketplace for professional security consultant services by offering a cheaper, more effective crowd-sourced approach? Or are these programs simply a tool for the most advanced, most daring companies to take their security programs to the next level?
Slides
Video
Track: Management
Speaker: Jon Rose
Electronic Discovery for System Administrators
As the Federal Rules of Evidence have evolved over the last several years, and as the volume of information in digital format has overtaken traditional printed media, electronic discovery had become more important than traditional paper-based discovery in litigation. While vendors can help with production, system administrators play a key role in the acquisition and production of Electronically Stored Information (ESI).
This presentation is designed to present an overview of the discovery process, explain how it differs from traditional computer forensics, and offer tips for administrators and managers to better assist in the production of ESI in the event of litigation (and hopefully to reduce the costs associated with production).
Slides
Video
Track: Executive/Legal
Speaker: Russ Shumway
Session 2: 10:55 - 11:40
Adventures in Large Scale HTTP Header Abuse
While the technique of sending malicious data through HTTP Header fields is not new, there is a conspicuous lack of information on the topic.
This presentation explores research and testing results of random auditing of 1.6 million websites. The speaker will address the history of HTTP Header attacks, the logic that went into the creation of an HTTP Header Audit tool, and the most interestingly the findings of the test run.
How many vulnerable websites were discovered? What attacks were they most susceptible to? Which Header fields are most likely to be vulnerable?
Finally, the presentation will discuss defensive techniques around HTTP header abuse and how to efficiently audit a sites HTTP Header fields for vulnerabilities.
Slides
Video
Track: Technical
Speaker: Zak Wolff
How Malware Attacks Web Applications
Modern malware has outpaced the ability for traditional defenses to detect and contain the threats. The core of the presentation will address several techniques used by malware to attack web applications, including:
- WebInjects (aka Man-in-the-Browser)
Files that contain JavaScript and HTML in order to alter the user experience in the application. - Form-Grabbing
The technique for capturing web form data within browsers. - Session Hijacking
The ability to redirect control of a session to an attacker. - Persistence and Stealth
How does the malware go undetected, for so long? - Countermeasures
How to detect malware interacting with your web applications.
Slides
Video
Track: Deep Dive
Speaker: Casey Smith
Linking Security to Business Value in the Customer Service Industry
The value of trust cannot be understated when discussing Superior Customer Service.
"The main benefit of trust is customer loyalty, which in turn leads to a longer term relationship, greater share of wallet, and higher advocacy or word of mouth. Results from our consumer survey show that emotional and rational trust drive between 22% and 44% of customer loyalty." - Study by ESCP Europe Business School
Privacy protection is a pillar of trust. Studies show PRIVACY is of paramount importance to consumers and is growing in importance. A 2012 Ponemon Institute study on the “Most trusted companies on privacy” found that while the importance of privacy has grown over the last seven years, the loss of control over privacy has also grown as well.
The Call Center industry is at the confluence of these competing social and business priorities. On the one hand, the customer service representative (CSR) must engender competence and trustworthiness and on the other hand CSR must ask the caller for a credit card number or social security number, the most private and personal valuable pieces of information a consumer possesses.
Where there is a gap in expectations between consumers and businesses, there is an opportunity for business to differentiate themselves and fill the gap and win market share. This opportunity is being realized by emerging technology designed to satisfy Compliance standards as well as real consumer demand for privacy protections.
Call Centers as well as other types of businesses that can address consumers demand for privacy protections can improve their long term bottom line through TRUST and customer loyalty.
Slides
Video
Track: Management
Speaker: Dan Rojas
Legal Issues of Forensics in the Cloud
Have you ever thought about how you would conduct a forensic investigation on your data if it was all in the Cloud; or, if your company suffers a data breach and all your data is in the Cloud how you would get the information you need to determine what happened and the extent of the damage? The Cloud presents many issues and new challenges. The best thing you can do is be prepared, but how?
This lecture will discuss the issues associated with attempting to deal with a data breach in the Cloud as well as conducting a forensic investigation in the Cloud. How do you prepare? What needs to be included in your contract or service level agreement? Finally, if you were not able to prepare, is all lost? What can you do, legally?
Slides
Video
Track: Executive/Legal
Speaker: David Willson
Session 3: 12:40 - 13:25
Angry Cars: Hacking the "Car as Platform"
Renault announced "what it describes as a 'tablet,' an integrated Android device built into its next range of cars, effectively opening the way to the car-as-a-platform. The car is becoming a new platform. We need developers to work on apps." Not to be left behind Ford has introduced the OpenXC platform, which it sees as a channel for collaboration between Ford and 3rd party application developers.
What role will security play in shaping this newly emerging technology, when your car can tweet it needs an oil change? Cars rely heavily on small embedded microprocessors running on a network that was never designed to be secure. This talk will look at the current technologies used CAN bus, OBDII, and tire pressure monitoring systems and demonstrate their inherent weaknesses. What should be considered in the future when most cars will be connected to the Internet?
Slides
Video
Track: Technical
Speaker: Aaron Weaver
Top Ten Web Application Defenses
We cannot 'firewall' or 'patch' our way to secure websites. In the past, security professionals thought firewalls, Secure Sockets Layer (SSL), patching, and privacy policies were enough. Today, however, these methods are outdated and ineffective, as attacks on prominent, well-protected websites are occurring every day.
Citigroup, PBS, Sega, Nintendo, Gawker, AT&T, the CIA, the US Senate, NASA, Nasdaq, the NYSE, Zynga, and thousands of others have something in common – all have had websites compromised in the last year. No company or industry is immune. Programmers need to learn to build websites differently.
This talk will review the top coding techniques developers need to master in order to build a low-risk, high-security web application.
Slides
Video
Track: Deep Dive
Speaker: Jim Manico
Using SaaS and the Cloud to Secure the SDLC
This session will cover Software as a Service (SaaS) offerings and how they can be effectively utilized in web security development efforts. Over the last few years, cloud services (i.e. SaaS) have been increasingly used as both a starting point for application security efforts and as a full outsourcing of the appsec program. However, by the very nature of cloud outsourcing and delivery, it is difficult to evolve this approach into a mature secure development lifecycle. Developer involvement is a necessity, and the solution has been to bring vulnerability assessment technologies in house. But recently, organizations have started to deploy a mixture of on-premise and cloud appsec solutions as an alternative to the all or nothing paradigm of on-premise or SaaS.
Topics covered include:
- Overview of vulnerability assessment using SaaS
- Overview of on-premise vulnerability scanning in the SDLC
- Challenges of on-premise and SaaS implementations
- Private cloud variations of on-premise and SaaS offerings
- Hybrid on-premise/cloud implementations in the SDLC
- Use of automation and integration with development infrastructure to ease developer adoption of on-premise/cloud appsec implementations
- How organizations can use SaaS to get started with application security and mature into a robust software security assurance program featuring on-premise and cloud deployments.
Slides
Video
Track: Management
Speaker: Andrew Earle
CISPA Why Privacy Advocates Hate This Legislation
Reintroduced in the House of Representatives on February 13, 2013, the Cyber Intelligence Sharing and Protection Act (CISPA) is a proposed US law which would allow for the sharing of Internet traffic information between the U.S. government and certain technology and manufacturing companies. The stated aim of the bill is to help the U.S government investigate cyber threats and ensure the security of networks against cyberattack.
CISPA has been criticized by advocates of Internet privacy and civil liberties, such as the Electronic Frontier Foundation, the American Civil Liberties Union, and Avaaz.org. Those groups argue CISPA contains too few limits on how and when the government may monitor a private individual’s Internet browsing information. Additionally, they fear that such new powers could be used to spy on the general public rather than to pursue malicious hackers. CISPA has garnered favor from corporations and lobbying groups such as Microsoft, Facebook and the United States Chamber of Commerce, which look on it as a simple and effective means of sharing important cyber threat information with the government.
Some critics saw CISPA as a second attempt at strengthening digital piracy laws after the anti-piracy Stop Online Piracy Act became deeply unpopular. Intellectual property theft was initially listed in the bill as a possible cause for sharing Web traffic information with the government, though it was removed in subsequent drafts.
Slides
Video
Track: Executive/Legal
Speaker: Maureen Donohue Feinroth
Session 4: 13:35 - 14:20
DevOps and Security: It's Happening. Right Now.
How do you integrate security within a Continuous Deployment (CD) environment - where every 5 minutes a feature, an enhancement, or a bug fix needs to be released? Traditional application security tools which require lengthy periods of configuration, tuning and application learning have become irrelevant in these fast-pace environments. Yet, falling back only on the secure coding practices of the developer cannot be tolerated.
Secure coding requires a new approach where security tools become part of the development environment – and eliminate any unnecessary code analysis overhead. By collaborating with development teams, understanding their needs and requirements, you can pave the way to a secure deployment in minutes. Steps include:
- Re-evaluate existing security tools and consider their integration within a CD environment
- Deliver a secured development framework and enforce its usage
- Pinpoint precise security code flaws and provide optimal fix recommendations
Slides
Video
Track: Technical
Speaker: Helen Bravo
A Demo of and Preventing XSS in .NET Applications
This presentation will cover a variety of approaches toward discovering XSS vulnerabilities in .NET applications, including:
- Microsoft's Web Protection Library/AntiXSS
- OWASP's AntiSamy.NET project
- CAT.Net
Slides
Video
Track: Deep Dive
Speaker: Larry Conklin
Measuring Security Best Practices With OpenSAMM
Security is becoming a competitive advantage in the marketplace. How do we ensure that security is built into products for our customers?
Security vulnerabilities can be introduced at any phase of the software development life cycle (SDLC). The Open Software Assurance Maturity Model (OpenSAMM) is lightweight, flexible framework that helps prevent vulnerabilities and improve security during software development.
This talk advocates adopting OpenSAMM to measure security best practices and improve our security processes, tools, and knowledge.
Slides
Video
Track: Management
Speaker: Alan Jex
Crafting a Plan for When Security Fails
A computer security incident, whether an exposed system with protected data or a hacked application, requires a planned response to quickly address and contain the threat. We exist in a world where having a plan is a necessity. Companies in various industries possess vast amounts of regulated and confidential data; this arrangement places a great amount of responsibility on the custodian. Unfortunately, in today's world, it is almost inevitable that you will be the target of an attack or mishandle data that may cause a potential exposure. Do you have a codified plan that helps guide your response?
CSIRPs are robust documents that are difficult to create. Developing a CSIRP that takes into account organizational culture and existing structure, creates buy-in from various departments, and is applicable in a wide array of emerging and existing threats while balancing substance and brevity may be a herculean task.
This presentation will provide the basis for the need for a CSIRP, discuss pitfalls and strategies when crafting CSIRPs, explore common ways they fail, and offer tips to create a healthy, viable, and useful process to use when confronting a computer security incident.
This presentation is geared towards those wishing to learn more about creating a viable computer security incident response plan (CSIRP).
Slides
Video
Track: Executive/Legal
Speaker: Robert Lelewski
Session 5: 14:30 - 15:15
Real World Cloud Application Security
This presentation will provide the audience with a case study of how real world organizations using the public cloud are approaching application security. Netflix, one of the largest AWS and public cloud users in the world, will serve as the subject of the case study.
The discussion will cover a variety of topics of interest to application security personnel, including:
- Automating and integrating security into CI/CD environments
- Large scale vulnerability management
- Continuous security testing and monitoring, including Netflix's Security Monkey and Exploit Monkey frameworks
- Cultural integration of security in DevOps/agile organizations
Slides
Video
Track: Technical
Speaker: Jason Chan
Data Mining a Mountain of Zero Day Vulnerabilities
Every day, software developers around the world, from Bangalore to Silicon Valley, churn out millions of lines of insecure code. This presentation evaluates an anonymized vulnerability data set derived from static binary analysis on thousands of applications belonging to large enterprises, commercial software vendors, open source projects, and software outsourcers.
By mining this data we can answer some interesting questions. What types of mistakes do developers make most often? Are we making any progress at eradicating XSS and SQL injection? How long does it really take to remediate software vulnerabilities? How secure are third party software components?
The discussion will answer these questions and many others, giving you a deep dive into metrics not found anywhere else.
Slides
Video
Track: Deep Dive
Speaker: Joe Brady
Defending Desktop (.NET/C#) Applications: Mitigating in the Dark (A Case Study Remix)
This presentation is on the case study(s) of desktop applications undergoing a cracking/hacking/attacking life cycle. This is the summation of multiple software projects undergoing attacks from a detected and focused attacker. This presentation follows a Product Owner(s) and Coder(s) going from a self directed response.
Your software project has been going for years, your client base is growing, your making deadlines then one day some e-mail shows up and your world starts to crumble. Crack after Crack keeps coming out every version; Your new Upgrades/Code keep showing up in a competing product; Malware keeps hitting your clients. See the steps taken by day-to-day product Owner(s) and Coder(s) as they respond to security events that never crossed their minds as potential threats.
Slides
Video
Track: Management
Speaker: Jon McCoy
Information Control: The Critical Need for a Defensible Position - Securing the Information Ecosystem
Given an overview of Identity Theft, fraud and information exposure participants will discover that the liability of these issues is much broader than they are prepared to manage.
Given case studies and stories from field experience, participants will identify gaps in information compliance policies and practices that place every organization at risk beyond areas of commerce, compliance, and technology.
Upon completion of the session participants will recognize critical gaps in their information ecosystem that need to be addressed in order to create a defensible position in the case of a breach.
Slides
Video
Track: Executive/Legal
Speaker: Tom Glanville
Friday Sessions (3/29): 09:00-13:00
Secure Coding
Refine your skills at this expert-lead course (included in the price of the conference!). From junior developers to senior, this class is a Must for everyone who writes code.
Specific topics include remediation (in code) of:
- SQL Injection
- XSS
- Password storage strategies
- Authentication best practices
- Clickjacking
- Multifactor authentication
- CSRF defense
- WAF/Virtual Patching
Track: Training
Speaker: Aaron Weaver
Capture the Flag: Postmortem
Ask questions about challenges from Thursday's competition, give suggestions on how to improve for next year, and participate in a FLOSSHack-style assessment of the CTF's underlying infrastructure. This gloves-off pen test will target the unintended and malicious acquisition of flags, keys, hints, and points. Cheating, lying, and dirty tricks are highly encouraged as we hack away at the scoreboard and the distributed VM.
Track: Testing
Speaker: Mark Major
Current Sponsors
Aerstone
| Aerstone provides strategic and technical cyber security consulting services including assessments, planning, architecture designed incident response, regulatory compliance, and computer forensics. We provide services and products for medium to large healthcare providers, financial services organizations and legal firms, and law enforcement. Clients range from local businesses to government agencies. |
Applied Trust
| AppliedTrust provides IT infrastructure, security, and opensource consulting services. Our clients are organizations where effective IT is critical to the reputation and growth of their business, and hail from a variety of industries including healthcare, financial services, hospitality, recreation, and government. Our specialty areas include:
|
Checkmarx
| Checkmarx - Source Code Analysis Made Easy
Checkmarx is the developer of next generation Static Code Analysis (SCA) solutions. The company pioneered the concept of a query language-based solution for identifying technical and logical code vulnerabilities. Checkmarx provides the best way for organizations to introduce security into their Software Development Lifecycle (SDLC) which systematically eliminates software risk. The product enables developers and auditors to easily scan un-compiled / un-built code in all major coding languages anywhere, anytime. CxSuite's application security testing is available in both "On Premise" and "On Demand" configurations. The security testing scans for the most prevalent security vulnerabilities as determined by OWASP Top 10, SANS, and other major standards. Checkmarx was recognized by Gartner as sole visionary in their latest SAST magic quadrant and as Cool vendor in application security. Customers include Fortune 500, government organizations and SMBs in over 30 countries. |
HP
| HP is a leading provider of security and compliance solutions for the modern enterprise that wants to mitigate risk in its hybrid environment and defend against advanced threats. Based on market leading products from HP ArcSight, HP Fortify, and HP TippingPoint, the HP Security Intelligence Platform uniquely delivers the advanced correlation, application protection, and network defenses to protect today’s hybrid IT infrastructure from sophisticated cyber threats. |
Security Pursuit
| Security Pursuit provides computer security services to help organizations protect their critical information systems. Based in Denver, Colorado, Security Pursuit's services include: IT Security Risk Analysis, Data Breach Incident Response, Network Penetration Testing and Vulnerability Assessments, Website Penetration Testing and Vulnerability Assessments, Wireless Network Security, Social Engineering Prevention, Security Awareness Training, Employee Termination Assistance and Virtual CISO consulting. We have conducted hundreds of security assessments for financial institutions, healthcare providers, retailers, utilities, airports, and municipal governments; many in support of PCI, GLBA, NCUA, and HIPAA compliance requirements. Security Pursuit’s computer security services provide you with a higher level of awareness about the security posture of your organization. |
SouthSeas
| Escaping network insecurity means identifying and eliminating vulnerability at each and every level. At South Seas Corporation, we consider the big picture and the finest details of your information technology, from computers to routers to servers and the cabling between, from intranets to the internet, from mobile devices to web applications to remote networks across the globe. We also address administrative issues, including security policy and federal compliance. Of course, your budget is top of mind from the beginning. The end result is a tailored solution designed to secure every byte of information traveling through, to and around your organization at every point, installed by certified experts trained to work hand in hand with your IT department. Take a load off your mind with South Seas Corporation. |
Veracode
| Today most global enterprises live under the constant threat of being hacked, which begs this critical question – how do they innovate and rapidly release new and improved applications required to be an industry leader while still securing their organizations critical IP and data assets? Before Veracode, application security was widely thought to slow innovation, but not anymore. With the Veracode Platform, application security and innovation can go hand-in-hand. Whether applications are built, brought or outsourced, Veracode’s patented testing technology provides the intelligence needed to quickly secure them from the most common forms of attack. |
Denver Marriott City Center
|
Denver Attractions
- Monty Python's Spamalot at the Buell Theatre (3/28-30)
- World-class exhibitions at the Denver Art Museum
- Guided walking tours of downtown's microbreweries
- The Denver Nuggets host the Brooklyn Nets (3/29 @ 7pm)
- Free tours of the US Mint
- Plus all the standard downtown stuff: shopping, more shopping, an aquarium, a zoo, comedy clubs, local music, and many clubs, restaurants, and art galleries.
Colorado Attractions
Out-of-town visitors may be interested in staying for the weekend to enjoy all Colorado has to offer, including:
- Red Rocks amphitheatre
- The Butterfly Pavilion
- Garden of the Gods (Colorado Springs)
- Royal Gorge (Canyon City)
- Coors, New Belgium, and many other Colorado breweries
Skiing
The SnowFROC staff is pursuing a chartered bus and negotiated discounts for premier ski resorts and lift tickets. Check back soon for details!
Capture the Flag Overview
Test your skills with a capture the flag (CTF) hacking competition created specifically for SnowFROC by members of the Boulder OWASP chapter.
Competitors will be provided a series of web applications containing a variety of vulnerabilities. Each discovered vulnerability will earn points. The harder the hack, the more points earned. At the end of the day, the team with the most points wins.
Rules
All conference attendees may participate in the CTF tournament for no additional cost. If you would prefer to attend the general conference proceedings, the competition will be made available to attendees after SnowFROC ends.
Format
Contestants will be provided a virtual machine which will run locally on self-provided devices. This is a BYOD event and all contestants are responsible for providing their own machine. No "loaners" will be made available.
All contestant machines should have:
- A virtual machine player that supports .vmdk files, such as VMware Player, VirtualBox, or Parallels.
- Appropriate penetration testing tool (BackTrack, SamuraiWTF, Mantra OS, and OWASP ZAP will fit in well).
Acceptable behavior
Competitors are only permitted to attack targets running on their local systems. Network traffic will be monitored to ensure there will be:
- No attacking the scoreboard. Misuse will result in punitive action.
- No targeting the VM. Do not mount the VM and harvest flags from within.
- No attacking other teams, whether through coercion, DoS, theft, sabotage, or other malicious activity.
- No collusion. Work only within your own team.
Prizes
Small prizes will be awarded to winners. Anyone who worked on the project or who has access to project-related repositories is ineligible to win prizes.
Both team and individual prizes will be awarded based on merit and other achievements.
Getting Started
Content acquisition
This information will be released closer to the day of the event.
Installation and configuration instructions
- Add the following entries to your hosts file:
10.50.65.12 training.theagency.owasp, theagency.owasp 10.56.65.87 theagency.owasp, Im.theagency.owasp 10.50.65.26 www.pla.owasp, secretlogin.pla.owasp, download.pla.owasp, www.pla.pt 10.50.65.187 shadowcorp.owasp 198.19.147.198 ctf.snowfroc.com
- The first network adapter must be a bridge network adapter.
- Configure the second network adapter to be a host-only network on your VM with IP address 10.50.65.254/24
- Load the .vmdk files
- Make sure you are using a browser other than Internet Explorer which for security reasons is not supported by the scoreboard.
- Make sure you are on the CTFSnowFROC wifi network (or plugged in directly at a table).
- Start by copying VM over to your machine. While that is going on, move on to the next steps.
- Make sure hosts file has the entries provided above.
- Within VirtualBox, go to file --> preferences --> network --> add host only network adapter.
- Edit this new adapter - put in 10.50.65.254 255.255.255.0
- In the VirtualBox main page- go to New, give the VM a name, set type to BSD, click next, set mem to at least 1 GB, Use Existing Virtual HD. Point it to the ctf.vmdk file you copied onto your machine. Create.
- Select VM in the VirtualBox main window, at top click settings. go to network, adapter 1, change to "Bridged Adapter". Adpater 2, enable network adapter, make it a host only adapter and select the adapter you created earlier. Hit ok.
- Start VM. Follow directions provided in VM.
Registration instructions
Coming soon.
Gameplay instructions
2013 presentations
Keynote Address: Data Protection for the 21st Century
Panel Discussion
Technical Track
DevFu: The inner ninja in every application developer
Adventures in Large Scale HTTP Header Abuse
Angry Cars: Hacking the "Car as Platform"
DevOps and Security: It's Happening. Right Now.
Real World Cloud Application Security
Deep-Dive Track
SIP Based Cloud Instances
How Malware Attacks Web Applications
Top Ten Web Application Defenses
A Demo of and Preventing XSS in .NET Applications
Data Mining a Mountain of Zero-Day Vulnerabilities
Management Track
Digital Bounty Hunters - Decoding Bug Bounty Programs
Linking Security to Business Value in the Customer Service Industry
Using SaaS and the Cloud to Secure the SDLC
Measuring Security Best Practices With Open SAMM
Defending Desktop (.NET/C#) Applications: Mitigating in the Dark (A Case Study Remix)
Legal Track
Electronic Discovery for System Administrators
Legal Issues of Forensics in the Cloud
CISPA: Why Privacy Advocates Hate This Legislation
Crafting a Plan for When Security Fails
Information Control: The Critical Need for a Defensible Position - Securing the Information Ecosystem
Previous conferences
2012 presentations are available here.