This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Credential stuffing"
(→Risk Factors) |
Dirk Wetter (talk | contribs) m (Defense option added) |
||
| Line 65: | Line 65: | ||
== Related Controls == | == Related Controls == | ||
* [[Authentication]] | * [[Authentication]] | ||
| + | |||
| + | == Defense === | ||
| + | |||
| + | * [[Credential Stuffing Prevention Cheat Sheet]] | ||
== References == | == References == | ||
Revision as of 21:02, 9 November 2018
- This is an Attack. To view all attacks, please see the Attack Category page.
Description
Credential stuffing is the automated injection of breached username/password pairs in order to fraudulently gain access to user accounts. This is a subset of the brute force attack category: large numbers of spilled credentials are automatically entered into websites until they are potentially matched to an existing account, which the attacker can then hijack for their own purposes.
Uniqueness
Credential stuffing is a new form of attack to accomplish account takeover through automated web injection. Credential stuffing is related to the breaching of databases; both accomplish account takeover. Credential stuffing is an emerging threat.
Credential stuffing is dangerous to both consumers and enterprises because of the ripple effects of these breaches. For more information on this please reference the Examples section showing the connected chain of events from one breach to another through credential stuffing.
Severity
Credential stuffing is one of the most common techniques used to take-over user accounts.
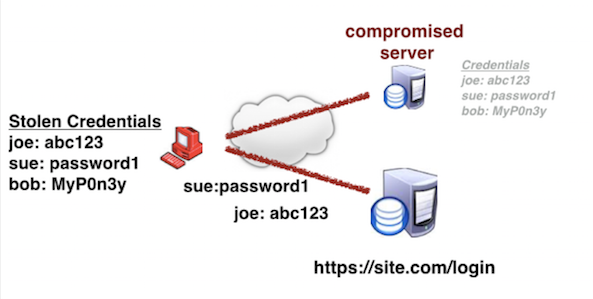
Anatomy of Attack
- The attacker acquires spilled usernames and passwords from a website breach or password dump site.
- The attacker uses an account checker to test the stolen credentials against many websites (for instance, social media sites or online marketplaces).
- Successful logins (usually 0.1-0.2% of the total login attempts) allow the attacker to take over the account matching the stolen credentials.
- The attacker drains stolen accounts of stored value, credit card numbers, and other personally identifiable information
- The attacker may also use account information going forward for other nefarious purposes (for example, to send spam or create further transactions)
Diagram
References
[1] http://michael-coates.blogspot.be/2013/11/how-third-party-password-breaches-put.html
Examples
Below are excerpts taken from publications analyzing large-scale breaches. Evidence supports that these breaches were the result of credential stuffing.
- Sony, 2011 breach: “I wish to highlight that two-thirds of users whose data were in both the Sony data set and the Gawker breach earlier this year used the same password for each system.”
- Yahoo, 2012 breach: “What do Sony and Yahoo! have in common? Passwords!”.
- Source: Troy Hunt. [3]
- Dropbox, 2012 breach: “The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the internet, including Dropbox”.
- Source: Dropbox. [4]
- JPMC, 2014 breach: “[The breached data] contained some of the combinations of passwords and email addresses used by race participants who had registered on the Corporate Challenge website, an online platform for a series of annual charitable races that JPMorgan sponsors in major cities and that is run by an outside vendor. The races are open to bank employees and employees of other corporations”.
- Source: NY Times. [5]
This connected chain of events from Sony to Yahoo to Dropbox excludes JPMC. The JPMC breach came from a separate and unrelated source. We know that the JPMC breach was caused by attackers targeting an unrelated third-party athletic race/run site for credentials to use against JPMC.