This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Cornucopia - Ecommerce Website - AT 7"
(Created page with "{{DISPLAYTITLE:<span style="padding:2px 5px 0px 5px;color:white;background:#73abcc;">Cornucopia - Ecommerce Website - AT 7</span>}} File:Cornucopia_-_Ecommerce_Website_AT_7....") |
|||
| Line 11: | Line 11: | ||
=== Technical Note: === | === Technical Note: === | ||
| − | Attacks should be prevented from being able to | + | Attacks should be prevented from being able to obtain valid account credentials by using the application in an unintended manner. This includes credential cracking (identifying valid login credentials by trying different values for usernames and/or passwords) and credential stuffing (mass log in attempts used to verify the validity of stolen username/password pairs). |
NB: This card relates to '''passwords'''. See [[Cornucopia_-_Ecommerce_Website_-_AT_4|AT 4]] for the similar user name attacks. | NB: This card relates to '''passwords'''. See [[Cornucopia_-_Ecommerce_Website_-_AT_4|AT 4]] for the similar user name attacks. | ||
Latest revision as of 19:50, 29 March 2016
Suit: Authentication
Card/Value: 7
Description:
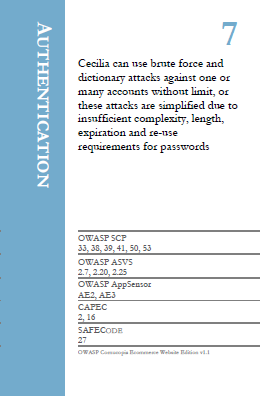
Cecilia can use brute force and dictionary attacks against one or many accounts without limit, or these attacks are simplified due to insufficient complexity, length, expiration and re-use requirements for passwords.
Technical Note:
Attacks should be prevented from being able to obtain valid account credentials by using the application in an unintended manner. This includes credential cracking (identifying valid login credentials by trying different values for usernames and/or passwords) and credential stuffing (mass log in attempts used to verify the validity of stolen username/password pairs).
NB: This card relates to passwords. See AT 4 for the similar user name attacks.
References:
| OWASP SCP | OWASP ASVS | OWASP AppSensor | CAPEC | SAFECODE |
|---|---|---|---|---|
| 33 | 2.7 | AE2 | 2 | 27 |
| 38 | 2.20 | AE3 | 16 | |
| 39 | 2.25 | |||
| 41 | ||||
| 50 | ||||
| 53 |