This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:Software Assurance Maturity Model"
m (Reverted edits by Frank Alexander (talk) to last revision by Pravir Chandra) |
|||
| Line 1: | Line 1: | ||
| − | + | {{OpenSAMM-NoCat}} | |
| − | + | ==== Main ==== | |
| + | <div style="display:inline; | ||
| + | width:220px; float:right; padding-left:40px; padding-bottom:40px;"> | ||
| + | <div style="padding-bottom:10px;"> | ||
| + | [http://www.opensamm.org/download/ http://www.opensamm.org/downloads/DownloadButton.png] | ||
| + | </div> | ||
| + | <div style="padding-top:10px;"> | ||
| + | [http://www.opensamm.org/ Visit the SAMM Website] | ||
| + | [http://www.opensamm.org/ http://www.owasp.org/images/4/44/SAMM-1.0-Cover.png] | ||
| + | </div> | ||
| + | </div> | ||
| − | + | The Software Assurance Maturity Model (SAMM) is an open framework to help organizations formulate and implement a strategy for software security that is tailored to the specific risks facing the organization. The resources provided by SAMM will aid in: | |
| − | + | * '''Evaluating an organization’s existing software security practices''' | |
| − | + | * '''Building a balanced software security assurance program in well-defined iterations''' | |
| − | + | * '''Demonstrating concrete improvements to a security assurance program''' | |
| + | * '''Defining and measuring security-related activities throughout an organization''' | ||
| − | + | SAMM was defined with flexibility in mind such that it can be utilized by small, medium, and large organizations using any style of development. Additionally, this model can be applied organization-wide, for a single line-of-business, or even for an individual project. Beyond these traits, SAMM was built on the following principles: | |
| + | * ''An organization’s behavior changes slowly over time'' - A successful software security program should be specified in small iterations that deliver tangible assurance gains while incrementally working toward long-term goals. | ||
| + | * ''There is no single recipe that works for all organizations'' - A software security framework must be flexible and allow organizations to tailor their choices based on their risk tolerance and the way in which they build and use software. | ||
| + | * ''Guidance related to security activities must be prescriptive'' - All the steps in building and assessing an assurance program should be simple, well-defined, and measurable. This model also provides roadmap templates for common types of organizations. | ||
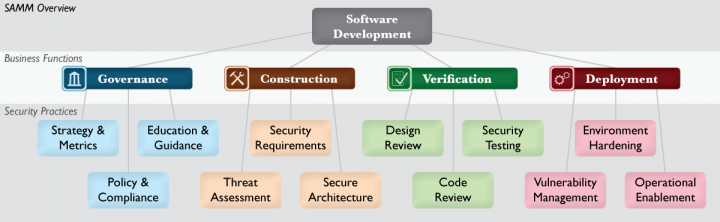
| − | {| | + | The foundation of the model is built upon the core business functions of software development with security practices tied to each (see diagram below). The building blocks of the model are the three maturity levels defined for each of the twelve security practices. These define a wide variety of activities in which an organization could engage to reduce security risks and increase software assurance. Additional details are included to measure successful activity performance, understand the associated assurance benefits, estimate personnel and other costs. |
| + | |||
| + | [[Image:SAMM-Overview.png|720px]] | ||
| + | |||
| + | |||
| + | ==== Browse Online ==== | ||
| + | ===== Click on any badge to learn more ===== | ||
| + | |||
| + | {| cellpadding="1" | ||
| + | |[http://www.owasp.org/index.php/SAMM_-_Governance http://www.opensamm.org/badges/small/G.png] | ||
| + | |- | ||
| + | |align="center"|'''Strategy & Metrics''' | ||
| + | |{{SAMM-BadgeList|name=Strategy_&_Metrics|abbr=SM|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Policy & Compliance''' | ||
| + | |{{SAMM-BadgeList|name=Policy_&_Compliance|abbr=PC|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Education & Guidance''' | ||
| + | |{{SAMM-BadgeList|name=Education_&_Guidance|abbr=EG|padding=0}} | ||
| + | |- | ||
| + | |[http://www.owasp.org/index.php/SAMM_-_Construction http://www.opensamm.org/badges/small/C.png] | ||
| + | |- | ||
| + | |align="center"|'''Threat Assessment''' | ||
| + | |{{SAMM-BadgeList|name=Threat_Assessment|abbr=TA|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Security Requirements''' | ||
| + | |{{SAMM-BadgeList|name=Security_Requirements|abbr=SR|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Secure Architecture''' | ||
| + | |{{SAMM-BadgeList|name=Secure_Architecture|abbr=SA|padding=0}} | ||
| + | |- | ||
| + | |[http://www.owasp.org/index.php/SAMM_-_Verification http://www.opensamm.org/badges/small/V.png] | ||
| + | |- | ||
| + | |align="center"|'''Design Review''' | ||
| + | |{{SAMM-BadgeList|name=Design_Review|abbr=DR|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Code Review''' | ||
| + | |{{SAMM-BadgeList|name=Code_Review|abbr=CR|padding=0}} | ||
| + | |- | ||
| + | |align="center"|'''Security Testing''' | ||
| + | |{{SAMM-BadgeList|name=Security_Testing|abbr=ST|padding=0}} | ||
| + | |- | ||
| + | |[http://www.owasp.org/index.php/SAMM_-_Deployment http://www.opensamm.org/badges/small/D.png] | ||
|- | |- | ||
| − | | | + | |align="center"|'''Vulnerability Management''' |
| − | {| | + | |{{SAMM-BadgeList|name=Vulnerability_Management|abbr=VM|padding=0}} |
|- | |- | ||
| − | | | + | |align="center"|'''Environment Hardening''' |
| − | {| | + | |{{SAMM-BadgeList|name=Environment_Hardening|abbr=EH|padding=0}} |
|- | |- | ||
| − | | | + | |align="center"|'''Operational Enablement''' |
| − | {| | + | |{{SAMM-BadgeList|name=Operational_Enablement|abbr=OE|padding=0}} |
|- | |- | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|} | |} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ==== Project Identification ==== | |
| + | {{:Key Project Information:Software Assurance Maturity Model Project}} | ||
| − | + | [[Category:OWASP Project]] | |
| + | [[Category:OWASP Document]] | ||
| + | [[Category:OWASP Alpha Quality Document]] | ||
| − | |||
| − | + | __NOTOC__ | |
| + | <headertabs/> | ||
| + | <br/>{{OWASP Book|6888083}}<br/> | ||
Revision as of 23:05, 7 February 2011

|
For the latest project news and information, join the mailing list and visit the OpenSAMM website. |
Main
The Software Assurance Maturity Model (SAMM) is an open framework to help organizations formulate and implement a strategy for software security that is tailored to the specific risks facing the organization. The resources provided by SAMM will aid in:
- Evaluating an organization’s existing software security practices
- Building a balanced software security assurance program in well-defined iterations
- Demonstrating concrete improvements to a security assurance program
- Defining and measuring security-related activities throughout an organization
SAMM was defined with flexibility in mind such that it can be utilized by small, medium, and large organizations using any style of development. Additionally, this model can be applied organization-wide, for a single line-of-business, or even for an individual project. Beyond these traits, SAMM was built on the following principles:
- An organization’s behavior changes slowly over time - A successful software security program should be specified in small iterations that deliver tangible assurance gains while incrementally working toward long-term goals.
- There is no single recipe that works for all organizations - A software security framework must be flexible and allow organizations to tailor their choices based on their risk tolerance and the way in which they build and use software.
- Guidance related to security activities must be prescriptive - All the steps in building and assessing an assurance program should be simple, well-defined, and measurable. This model also provides roadmap templates for common types of organizations.
The foundation of the model is built upon the core business functions of software development with security practices tied to each (see diagram below). The building blocks of the model are the three maturity levels defined for each of the twelve security practices. These define a wide variety of activities in which an organization could engage to reduce security risks and increase software assurance. Additional details are included to measure successful activity performance, understand the associated assurance benefits, estimate personnel and other costs.
Browse Online
Click on any badge to learn more
Project Identification
| PROJECT INFORMATION | |||||||
|---|---|---|---|---|---|---|---|
| Project Name | Software Assurance Maturity Model (SAMM) Project | ||||||
| Short Project Description |
The Software Assurance Maturity Model (SAMM) project is committed to building a usable framework to help organizations formulate and implement a strategy for application security that's tailored to the specific business risks facing the organization. The goal is to create well-defined and measurable goals that can be used by small, medium,and large sized organizations in any line of business that involves software development. | ||||||
|
Key Project Information |
Project Leader |
Project Contibutors |
Mailing List |
Project Type |
Sponsors | ||
| Release Status | Main Links | Related Projects |
|---|---|---|
| |
This project has produced a book that can be downloaded or purchased. Feel free to browse the full catalog of available OWASP books. |
Pages in category "Software Assurance Maturity Model"
The following 47 pages are in this category, out of 47 total.
S
- SAMM - Code Review - 1
- SAMM - Code Review - 2
- SAMM - Code Review - 3
- SAMM - Construction
- SAMM - Deployment
- SAMM - Design Review - 1
- SAMM - Design Review - 2
- SAMM - Design Review - 3
- SAMM - Education & Guidance - 1
- SAMM - Education & Guidance - 2
- SAMM - Education & Guidance - 3
- SAMM - Environment Hardening - 1
- SAMM - Environment Hardening - 2
- SAMM - Environment Hardening - 3
- SAMM - Governance
- SAMM - Operational Enablement - 1
- SAMM - Operational Enablement - 2
- SAMM - Operational Enablement - 3
- SAMM - Policy & Compliance - 1
- SAMM - Policy & Compliance - 2
- SAMM - Policy & Compliance - 3
- SAMM - Roadmap - Financial Services Organization
- SAMM - Roadmap - Government Organization
- SAMM - Roadmap - Independent Software Vendor
- SAMM - Roadmap - Online Service Provider
- SAMM - Secure Architecture - 1
- SAMM - Secure Architecture - 2
- SAMM - Secure Architecture - 3
- SAMM - Security Requirements - 1
- SAMM - Security Requirements - 2
- SAMM - Security Requirements - 3
- SAMM - Security Testing - 1
- SAMM - Security Testing - 2
- SAMM - Security Testing - 3
- SAMM - Strategy & Metrics - 1
- SAMM - Strategy & Metrics - 2
- SAMM - Strategy & Metrics - 3
- SAMM - Threat Assessment - 1
- SAMM - Threat Assessment - 2
- SAMM - Threat Assessment - 3
- SAMM - Verification
- SAMM - Vulnerability Management - 1
- SAMM - Vulnerability Management - 2
- SAMM - Vulnerability Management - 3
Media in category "Software Assurance Maturity Model"
The following 3 files are in this category, out of 3 total.