This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:OWASP Project"
Hblankenship (talk | contribs) (→Code) |
|||
| Line 1: | Line 1: | ||
| − | |||
| − | + | __NOTOC__ | |
| − | |||
| − | |||
| − | + | {| | |
| + | |- | ||
| + | ! width="700" align="center" | <br> | ||
| + | ! width="500" align="center" | <br> | ||
| + | |- | ||
| + | | | ||
| + | | align="right" | | ||
| + | |||
| + | |} | ||
| + | |||
| + | <div style="width:100%;height:160px;border:0,margin:0;overflow: hidden;">[[File:OWASP_Project_Header.jpg|link=]]</div> | ||
| + | = Welcome = | ||
| + | {| style="width: 100%;" | ||
| + | |- | ||
| + | | style="width: 100%; color: rgb(0, 0, 0);" | | ||
| + | {| style="border: 0px solid ; background: transparent none repeat scroll 0% 0%; width: 100%; -moz-background-clip: border; -moz-background-origin: padding; -moz-background-inline-policy: continuous;" | ||
| + | |- | ||
| + | | style="width: 95%; color: rgb(0, 0, 0);" | | ||
| + | <font size=2pt> | ||
| + | |||
| + | === Welcome to the OWASP Global Projects Page === | ||
| + | An OWASP project is a collection of related tasks that have a defined roadmap and team members. OWASP project leaders are responsible for defining the vision, roadmap, and tasks for the project. The project leader also promotes the project and builds the team. OWASP currently has ''''''over ''''''93'''''' active projects'''''', and new project applications are submitted every week. | ||
| + | |||
| + | This is one of the most popular divisions of OWASP as it gives members an opportunity to freely test theories and ideas with the professional advice and support of the OWASP community. Every project has an associated mail list. You can view all the lists, examine their archives, and subscribe to any project by visiting the [http://lists.owasp.org/mailman/listinfo OWASP Project Mailing Lists] page. A summary of recent project announcements is available on the [[OWASP Updates]] page. | ||
| + | |||
| + | Download the '''[[Media:PROJECT_LEADER-HANDBOOK_2014.pdf|OWASP Project Handbook 2014]]''' | ||
| + | |||
| + | Or read the wiki version: | ||
| + | '''[[OWASP_2014_Project_Handbook|OWASP Project Handbook Wiki 2014]]''' | ||
| + | |||
| + | '''[[Project_Online_Resources|Project Online Resources]]''' | ||
| + | |||
| + | === Who Should Start an OWASP Project? === | ||
| + | |||
| + | *Application Developers. | ||
| + | *Software Architects. | ||
| + | * Information Security Authors. | ||
| + | *Those who would like the support of a world wide professional community to develop or test an idea. | ||
| + | *Anyone wishing to take advantage of the professional body of knowledge OWASP has to offer. | ||
| + | |||
| + | === Contact Us=== | ||
| + | |||
| + | If you have any questions, please do not hesitate to [https://owasporg.atlassian.net/servicedesk/customer/portal/7/group/18/create/72 Contact Us] by using the form provided here. Please allow five working days for your question or comment to be answered. This is due to the large amount of queries the foundation staff receive every day. We thank you for your patience. | ||
| + | |||
| + | === Fund Information === | ||
| + | |||
| + | https://www.owasp.org/index.php/Funding | ||
| + | |||
| + | === OWASP Project Inventory === | ||
| + | |||
| + | All OWASP tools, document, and code library projects are organized into the following [[OWASP_Project_Stages|categories:]] | ||
| + | |||
| + | * '''[[OWASP_Project_Inventory#Flagship_Projects|Flagship Projects:]]''' The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole. | ||
| + | |||
| + | * '''[[OWASP_Project_Inventory#Labs_Projects|Lab Projects:]]''' OWASP Labs projects represent projects that have produced an OWASP reviewed deliverable of value. | ||
| + | |||
| + | * '''[[OWASP_Project_Inventory#Incubator_Projects|Incubator Projects:]]''' OWASP Incubator projects represent the experimental playground where projects are still being fleshed out, ideas are still being proven, and development is still underway. | ||
| + | |||
| + | === Social Media === | ||
| + | |||
| + | We recommend using the links below to find our official OWASP social media channels. These are a great way to keep in touch with the different initiatives going on at OWASP throughout the world. They are all updated regularly by chapter leaders, project leaders, the OWASP Board Members, and our OWASP Staff. If you have any questions or concerns about any of these accounts, please drop us a line using our [https://owasporg.atlassian.net/servicedesk/customer/portal/7/group/18/create/72 "Contact Us"] form. | ||
| + | |||
| + | [[Image:Blogger-32x32.png|32px|link=http://owasp.blogspot.co.uk/]] [[Image:Twitter-32x32.png|32px|link=https://twitter.com/OWASP]] [[Image:Facebook-32x32.png|32px|link=https://www.facebook.com/groups/172892372831444/]] [[Image:Linkedin-32x32.png|32px|link=http://www.linkedin.com/groups/Global-OWASP-Foundation-36874]] [[Image:Google-32x32.png|32px|link=https://plus.google.com/u/0/communities/105181517914716500346?cfem=1]] [[Image:Ning-32x32.png|32px|link=http://myowasp.ning.com/]] | ||
| + | <!-- Twitter Box --> | ||
| + | </font> | ||
| + | |||
| + | |} | ||
| + | |||
| + | | style="border: 3px solid rgb(204, 204, 204); vertical-align: top; width: 95%; font-size: 95%; color: rgb(0, 0, 0);" | | ||
| + | <div style="padding:2em;padding-bottom:0px;"><!-- DON'T REMOVE ME, I'M STRUCTURAL; also 2 empty lines between images --> | ||
| + | |||
| + | [[Image:Donate_here_banner.png|center|300px| link=http://www.regonline.com/Register/Checkin.aspx?EventID=1044369]] | ||
| + | </div> | ||
| + | |||
| + | {| | ||
| + | |||
| + | |||
| + | | style="width: 110px; font-size: 95%; color: rgb(0, 0, 0);" | | ||
| + | |} | ||
| + | |||
| + | | style="width: 110px; font-size: 95%; color: rgb(0, 0, 0);" | | ||
| + | |} | ||
| + | <!-- End Banner --> | ||
| + | |||
| + | = Project Inventory = | ||
| + | <font size=2pt> | ||
| − | + | ==Quick Guide to Projects== | |
| − | + | ===Quick Guide for Developers=== | |
| − | + | This is a Quick Guide for Developers new to OWASP projects: | |
| − | + | Infographic containing Hyperlinks to projects: | |
| + | https://magic.piktochart.com/output/6400107-untitled-infographic | ||
| − | + | Downloadable Images: | |
| − | + | [[File:Owasp_Dev_Guide.pdf ]] | |
| − | + | ==Flagship Projects== | |
| − | |- | + | [[File:Flagship_banner.jpg]] |
| − | + | ||
| − | + | The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole. | |
| − | |- | + | After a major review process [[LAB_Projects_Code_Analysis_Report|More info here]] the following projects are considered to be flagship candidate projects. These project have been evaluated more deeply to confirm their flagship status: |
| − | | | + | |
| − | ''' | + | ====Tools==== |
| + | |||
| + | * [[OWASP_Zed_Attack_Proxy_Project|OWASP Zed Attack Proxy]] | ||
| + | * [[OWASP_Web_Testing_Environment_Project|OWASP Web Testing Environment Project]] | ||
| + | * [[OWASP_OWTF|OWASP OWTF]] | ||
| + | * [[OWASP_Dependency_Check|OWASP Dependency Check]] | ||
| + | * [[OWASP_Security_Shepherd|OWASP Security Shepherd]] | ||
| + | * [[OWASP_DefectDojo_Project|OWASP DefectDojo Project]] | ||
| + | * [[OWASP_Juice_Shop_Project|OWASP Juice Shop Project]] | ||
| + | * [[OWASP_Security_Knowledge_Framework#tab=Main | OWASP Security Knowledge Framework]] | ||
| + | * [[OWASP_Dependency_Track_Project|OWASP Dependency Track Project]] | ||
| + | |||
| + | ====Code [Health Check January 2017]==== | ||
| + | * [[:Category:OWASP_ModSecurity_Core_Rule_Set_Project|OWASP ModSecurity Core Rule Set Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[:Category:OWASP_CSRFGuard_Project|OWASP CSRFGuard Project]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | ====Documentation==== | ||
| + | * [[:Category:OWASP_Application_Security_Verification_Standard_Project|OWASP Application Security Verification Standard Project]] | ||
| + | * [[:Category:Software_Assurance_Maturity_Model|OWASP Software Assurance Maturity Model (SAMM)]] | ||
| + | * [[OWASP_AppSensor_Project|OWASP AppSensor Project]] | ||
| + | * [[:Category:OWASP_Top_Ten_Project|OWASP Top Ten Project]] | ||
| + | * [[OWASP_Testing_Project|OWASP Testing Project]] | ||
| + | * [[OWASP_Cheat_Sheet_Series|OWASP Cheat Sheet Series]] | ||
| + | * [[OWASP_Mobile_Security_Testing_Guide|OWASP Mobile Security Testing Guide]] | ||
| + | |||
| + | ==Labs Projects== | ||
| + | [[File:Lab banner.jpg]] | ||
| + | |||
| + | OWASP Labs projects represent projects that have produced a deliverable of value. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are at least ready for mainstream usage. | ||
| + | |||
| + | ===Thumbs up=== | ||
| + | Thumbs up are given to LAB projects showing a steady progress in their development, had very active and continuous releases and commits, regular update of information on their wiki page and have quite complete documentation. These projects are almost ready to become flagship | ||
| + | |||
| + | ====Tools==== | ||
| + | * [[O-Saft|O-Saft]] | ||
| + | * [[:Category:OWASP_EnDe|OWASP EnDe Project]] | ||
| + | * [[OWASP_Mobile_Security_Project|OWASP Mobile Security Project]] | ||
| + | * [[OWASP_O2_Platform|OWASP O2 Platform]] | ||
| + | * [[OWASP_Passfault|OWASP Passfault]] | ||
| + | * [[:Category:OWASP WebGoat Project|OWASP WebGoat Project]] | ||
| + | * [[OWASP_Xenotix_XSS_Exploit_Framework|OWASP Xenotix XSS Exploit Framework]] | ||
| + | * [[OWASP_Code_Pulse_Project|OWASP Code Pulse Project]] | ||
| + | * [[OWASP_SeraphimDroid_Project|OWASP SeraphimDroid Project]] | ||
| + | * [[OWASP_Glue_Tool_Project|OWASP Glue Tool Project]] | ||
| + | * [[OWASP_Amass_Project|OWASP Amass Project]] | ||
| + | |||
| + | ====Documentation [Health Check January 2017]==== | ||
| + | |||
| + | * [[:Category:OWASP_Code_Review_Project|OWASP Code Review Guide Project]] | ||
| + | * [[OWASP_Cornucopia|OWASP Cornucopia]] | ||
| + | * [[OWASP_Podcast|OWASP Podcast Project]] | ||
| + | * [[OWASP_Proactive_Controls|OWASP Proactive Controls]] | ||
| + | * [[OWASP_Internet_of_Things_Top_Ten_Project|OWASP Internet of Things Top Ten Project]] | ||
| + | * [[OWASP_Top_10_Privacy_Risks_Project|OWASP Top 10 Privacy Risks Project]] | ||
| + | * [[OWASP_Snakes_and_Ladders|OWASP Snakes and Ladders Project]] | ||
| + | * [[OWASP Automated Threats to Web Applications]] | ||
| + | |||
| + | ====Contests - Health Check February 2016==== | ||
| + | *[[OWASP_University_Challenge|OWASP University Challenge]] [[File:Thumbsup.png|15px]] | ||
| + | * [[:Category:OWASP_CTF_Project|OWASP CTF Project]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | ====Code==== | ||
| + | * [[:Category:OWASP_Enterprise_Security_API|OWASP Enterprise Security API]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Security_Logging_Project|OWASP Security Logging Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[Benchmark|OWASP Benchmark]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | ==Incubator Projects== | ||
| + | [[File:Incubator_banner.jpg]] | ||
| + | |||
| + | OWASP Incubator projects represent the experimental playground where projects are still being fleshed out, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity. The label also allows project leaders to leverage the OWASP name while their project is still maturing. | ||
| + | |||
| + | ===Thumbs up=== | ||
| + | Thumbs up are given to incubator projects showing a steady progress in their development, had continuous releases and commits or have delivered a complete product, including open source repository location, basic user guidelines and documentation | ||
| + | |||
| + | |||
| + | ====Code==== | ||
| + | * [[OWASP_Java_Encoder_Project|OWASP Java Encoder Project]] [[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Java_HTML_Sanitizer|OWASP Java HTML Sanitizer Project]] [[File:Thumbsup.png|15px]] | ||
| + | * [[Projects/OWASP_Node_js_Goat_Project|OWASP Node.js Goat Project]] [[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Mth3l3m3nt_Framework_Project|OWASP Mth3l3m3nt Framework Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[CSRFProtector_Project|OWASP CSRFProtector Project]] | ||
| + | * [[WebGoatPHP|OWASP WebGoat PHP Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Secure_Headers_Project|OWASP Secure Headers Project]] | ||
| + | * [[OWASP_Vicnum_Project | OWASP Vicnum Projct]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_DeepViolet_TLS/SSL_Scanner|OWASP DeepViolet TLS/SSL_Scanner]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Off_the_record_4_Java_Project|OWASP Off the record 4 Java Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Learning_Gateway_Project|OWASP Learning Gateway Project]] | ||
| + | * [[OWASP_SonarQube_Project|OWASP SonarQube Project]] | ||
| + | * [[OWASP_Zezengorri_Code_Project|OWASP Zenzengorri Code Project]] | ||
| + | * [[OWASP_Find_Security_Bugs|OWASP Find Security Bugs]] | ||
| + | * [[OWASP_Vulnerable_Web_Application|OWASP Vulnerable Web Application]] | ||
| + | *[[OWASP_SamuraiWTF_Project|OWASP Samurai WTF]] | ||
| + | *[[OWASP_Secure_Coding_Dojo|OWASP Secure Coding Dojo]] | ||
| + | |||
| + | ====Research==== | ||
| + | |||
| + | ====Tools==== | ||
| + | * [[OWASP_Threat_Dragon | OWASP Threat Dragon]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Mutillidae_2_Project|OWASP Mutillidae 2 Project]] | ||
| + | *[[OWASP_Pyttacker_Project|OWASP Pyttacker Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_ZSC_Tool_Project|OWASP ZSC Tool Project]] [[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Basic_Expression_%26_Lexicon_Variation_Algorithms_(BELVA)_Project| OWASP Basic Expression Lexicon Variation Algorithms (Belva) Project]]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_VBScan_Project| OWASP VBScan]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_AppSec_Pipeline|OWASP Appsec Pipeline]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Bug_Logging_Tool|OWASP Bug Logging Tool]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_iGoat_Tool_Project|OWASP iGoat Tool Project]] | ||
| + | *[[OWASP_Risk_Rating_Management|OWASP Risk Rating Management]] | ||
| + | *[[OWASP_DevSlop_Project|OWASP DevSlop Project]] | ||
| + | *[[OWASP_SecurityRAT_Project|OWASP SecurityRAT Project]] | ||
| + | *[[OWASP_SecureTea_Project|OWASP SecureTea Project]] | ||
| + | *[[OWASP_Attack_Surface_Detector_Project|OWASP Attack Surface Detector Project]] | ||
| + | *[[OWASP_Nettacker|OWASP Nettacker]] | ||
| + | *[[OWASP_Serverless_Goat|OWASP Serverless Goat]] | ||
| + | *[[OWASP_Honeypot_Project|OWASP Honeypot]] | ||
| + | *[[OWASP_DVSA|OWASP DVSA]] | ||
| + | *[[OWASP_Python_Honeypot|OWASP Python Honeypot]] | ||
| + | *[[OWASP_Maryam_Project|OWASP Maryam Project]] | ||
| + | *[[OWASP_QRLJacker|OWASP QRLJacker]] | ||
| + | *[[OWASP_D4N155|OWASP D4N155]] | ||
| + | *[[OWASP_Jupiter|OWASP Jupiter]] | ||
| + | |||
| + | ====Documentation==== | ||
| + | *[[OWASP_Vulnerable_Web_Applications_Directory_Project|OWASP Vulnerable Web Applications Directory Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[:Category:OWASP_.NET_Project|OWASP .NET Project]] | ||
| + | *[[OWASP_Incident_Response_Project|OWASP Incident Response Project]][[File:Thumbsup.png|15px]]* | ||
| + | *[[OWASP_Application_Security_Program_Quick_Start_Guide_Project|OWSP_Application_Security_Program_Quick_Start_Guide_Project]] | ||
| + | *[[OWASP_SecLists_Project|OWASP SecLists Project]] | ||
| + | *[[OWASP_Knowledge_Based_Authentication_Performance_Metrics_Project|OWASP Knowledge Based Authentication Performance Metrics Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_RFP-Criteria|OWASP RFP Criteria]] | ||
| + | *[[OWASP_Web_Mapper_Project|OWASP Web Mapper Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Top_10_fuer_Entwickler|OWASP 10 Fuer Entwickler]] | ||
| + | *[[WASC_OWASP_Web_Application_Firewall_Evaluation_Criteria_Project |WASC_OWASP_Web_Application_Firewall_Evaluation_Criteria_Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Secure_Software_Development_Lifecycle_Project]] | ||
| + | *[[OWASP_Anti-Ransomware_Guide_Project|OWASP Ransomeware Guide Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Cyber_Defense_Matrix|OWASP Cyber Defense Matrix]] | ||
| + | *[[OWASP_Top_5_Machine_Learning_Risks|OWASP Top 5 Machine Learning Risks]] | ||
| + | *[[OWASP_Security_Operations_Center_(SOC)_Framework_Project|OWASP Security Operations Center SOC Framework Project]] | ||
| + | *[[OWASP_Vulnerability_Management_Guide|OWASP Vulnerability Management Guide]] | ||
| + | *[[OWASP_Embedded_Application_Security|OWASP Embedded Application Security]] | ||
| + | *[[OWASP_Application_Security_Curriculum|OWASP Application Security Curriculum]] | ||
| + | *[[OWASP_Software_Security_5D_Framework|OWASP Software Security 5D Framework]] | ||
| + | *[[OWASP_Anti-Ransomware_Guide_Project|OWASP Anti-Ransomware Guide Project]] | ||
| + | *[[OWASP_Serverless_Top_10_Project|OWASP Serverless Top 10 Project]] | ||
| + | *[[OWASP_Cloud-Native_Application_Security_Top_10|OWASP Cloud-Native Application Security Top 10]] | ||
| + | *[[OWASP_Application_Security_Guide_For_CISOs_Project_v2|OWASP Application Security Guide For CISOs Project]] | ||
| + | *[[OWASP_Cloud_Security_Project|OWASP Cloud Security Project]] | ||
| + | *[[OWASP_Docker_Top_10|OWASP Docker Top 10]] | ||
| + | *[[Blockchain_Security_Framework|OWASP Blockchain Security Framework]] | ||
| + | *[[OWASP_API_Security_Project|OWASP API Security Project]] | ||
| + | *[[:Category:PHP|OWASP PHP Project]] | ||
| + | *[[OWASP_Security_Pins_Project|OWASP Security Pins Project]] | ||
| + | *[[Risk_Assessment_Framework|OWASP Risk Assessment Framework]] | ||
| + | *[[OWASP_Container_Security_Verification_Standard_(CSVS)|OWASP Container Security Verification Standard]] | ||
| + | *[[OWASP_Top_10_Card_Game|OWASP Top 10 Card Game]] | ||
| + | *[[OWASP_DevSecOps_Maturity_Model|OWASP DevSecOps Maturity Model]] | ||
| + | *[[OWASP_Secure_Medical_Device_Deployment_Standard|OWASP Secure Medical Device Deployment Standard]] | ||
| + | |||
| + | ==Educational Initiatives== | ||
| + | ====Health Check February 2017==== | ||
| + | *[[OWASP_Student_Chapters_Program|OWASP Student Chapters Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[:Category:OWASP_Education_Project|OWASP Education Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[:Category:OWASP_Speakers_Project|OWASP Speakers Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Media_Project|OWASP Media Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_PHP_Security_Training_Project|OWASP PHP Security Training Project]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_Online_Academy#tab=Main | OWASP Online Academy]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | == Low Activity Projects == | ||
| + | [[File:low_activity.jpg]] | ||
| + | ======Low Activity (LABS)[Reviewed July 2015] Health Check February 2016====== | ||
| + | |||
| + | These projects had no releases in at least a year, however have shown to be valuable tools | ||
| + | '''Code [Low Activity]''' Health Check February 2016 | ||
| + | |||
| + | * [[OWASP_Broken_Web_Applications_Project|OWASP Broken Web Applications Project]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | '''Tools Health Check February 2016''' | ||
| + | *[[:Category:OWASP_WebScarab_Project|WebScarab]][[File:Thumbsup.png|15px]] | ||
| + | *[[OWASP_HTTP_Post_Tool|OWASP HTTP POST Tool]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | '''Documentation [Low Activity]''' '''Health Check February 2016''' | ||
| + | * [[:Category:OWASP_Legal_Project|OWASP Legal Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[Virtual_Patching_Best_Practices|Virtual Patching Best Practices]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_Secure_Coding_Practices_-_Quick_Reference_Guide|OWASP Secure Coding Practices - Quick Reference Guide]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | ==Donated Projects== | ||
| + | |||
| + | OWASP Donated Projects are inactive projects that have been donated to the OWASP Projects Infrastructure. | ||
| + | |||
| + | ====Tools==== | ||
| + | |||
| + | * [[OWASP_Excess_XSS_Project|OWASP Excess XSS Project]][[File:Thumbsup.png|15px]] | ||
| + | * [[OWASP_JOTP_Project|OWASP jOTP Project]][[File:Thumbsup.png|15px]] | ||
| + | |||
| + | ==OWASP Archived Projects== | ||
| + | OWASP Archived Projects are projects that have developed outside OWASP umbrella or have become inactive. If you are interested in pursuing any of the inactive projects (click hyperlink for list), please contact us and let us know of your interest. | ||
| + | |||
| + | '''Added New Project on February 2016''' | ||
| + | |||
| + | [[:Category:OWASP_Project_Archived_Projects]] | ||
| + | |||
| + | = Former Project Task Force = | ||
| + | |||
| + | |||
| + | ====OWASP Project Task Force==== | ||
| − | + | {{:Task_Force/OWASP_Projects}} | |
| − | |||
| − | + | = Online Resources = | |
| − | |||
| − | + | ===Project Online Resources=== | |
| − | |||
| − | + | * [https://docs.google.com/a/owasp.org/spreadsheets/d/13QM6yCqpirNuURbBdB5YZ_30mfQGbLjzBTGx0CTSNWw/edit?usp=sharing|OWASP Open Source Project Resources & Services] | |
| − | |||
| − | + | Please note that some services are 100% free and some have nominal cost. | |
| − | + | {{:Project_Online_Resources}} | |
| − | |||
| − | + | = Starting a New Project = | |
| − | + | <font size=2pt> | |
| + | == So you want to start a project... == | ||
| − | + | Starting an OWASP project is quite easy, and your desire to contribute and make it happen is essential. | |
| − | + | [[File:HowToStartProjectoWasp.png | 600px | right]] | |
| − | + | Here are some of the guidelines for running a successful OWASP project: | |
| − | |||
| − | + | -Start exploring the actual OWASP projects Inventory. Many projects handle specific areas of security it is a good idea to start looking how other successful projects do this (LABS/Flagship) | |
| − | + | -Place your idea or project on the [[Project_Ideas_Board#From_Idea_to_Project_Incubator|Project Ideas Board]]. This phase will help you to define the project goals and also explore and exchange with other OWASP leaders and volunteers how to develop the idea into a tangible project | |
| − | |||
| − | + | -Explore and research if your idea covers a unique segment in the Security arena. Think of your project as a product, if you really want people using it, think how this project will cover a necessity in the security area you are working on | |
| − | + | -Define what kind of project you would like to start. Is it a code, tool or documentation? | |
| − | |||
| − | + | -Communicate through the Project leader mailing list about your idea and get feedback and meet potential contributors | |
| − | |||
| − | + | -Develop your project based on the type of project. For example if you are willing to start a documentation project, begin by defining a Table of Content and work it through with potential contributors. First of all begin by creating a Road-map for your project. This is essential to submit your project. We highly recommend to read documentation such as "[http://www2.econ.iastate.edu/tesfatsi/ProducingOSS.KarlFogel2005.pdf How to start /run a successful Open Source Projects]". | |
| − | |||
| − | + | [[File:RoadmapIncubatorProjectExample2.PNG | 500px | left]] | |
| − | |||
| − | + | Some recommendations on how to start a documentation project | |
| − | + | [[:File:Document_Guide_(1).png| Document Guide Project]] | |
| − | + | ===Importance of a well thought out Road-map=== | |
| + | Many Incubator project leaders struggle with creating a realistic planning, which should be based on their available resources and time. A well thought out plan makes a difference between a procrastinating project and a successful one. The important aspect of this is, that the project leader is able to create a plan based on his situation. The following is an example of a Roadmap, which has focused to produce a Documentation first release in a year and a basic outline how they plan to cover 4 essential aspects which are Research & Development, Marketing, Planning and Goals. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | "Your [project] roadmap should tell a coherent story about the likely growth of your product. Each release should build on the previous one and move you closer towards your vision. Your roadmap should be convincing and realistic: Don’t speculate or oversell your [project]. Be clear who your audience is: An internal roadmap talks to development, marketing, sales, service, and the other groups involved in making your [project] a success; and external one talks to existing and prospective customers." | |
| − | : | + | Extracted from : "[[http://www.romanpichler.com/blog/10-tips-creating-agile-product-roadmap/ 10 Tips for Creating an Agile Product Roadmap]]" |
| − | + | * Start defining a development, documentation and marketing plan for your project. Set short , medium and long term plans. Include promotion of your project, this is very important in order to engage users and consumers of your project. You ''can'' run a single person project, but it's usually best to get the community involved. You should be prepared to support a mailing list, build a team, speak at conferences, and promote your project. | |
| − | |||
| − | + | * You can contribute existing documents or tools to OWASP! Assuming you have the intellectual property rights to a work, you can open it to the world as an OWASP Project. Please coordinate this with OWASP by [https://owasporg.atlassian.net/servicedesk/customer/portal/7/group/18/create/72 Contacting Us]. | |
| − | + | * Available Grants to consider if you need funding - [[Grants|Click Here]] | |
| − | |||
| − | + | * You should promote your project through the OWASP channels as well as by outside means. Get people to blog about it! | |
| − | |||
| − | + | == '''Creating a New Project''' == | |
| − | + | Once you have passed the Project Ideas phase, then you will be ready to start a new project | |
| − | + | '''[https://owasporg.atlassian.net/servicedesk/customer/portal/7/create/70 Please submit a new project application here].'''''' | |
| − | + | '''2016 OWASP Project Process''' | |
| − | + | '''Step 1:''' | |
| + | New Project Leader submits New Project Request Form it is logged in the system and an alert is sent to the Project Coordinator | ||
| − | + | '''Step 2:''' | |
| − | + | New Project Request is received and reviewed by Project Coordinator for complete information .It must contain the following information to qualify as an acceptable submission: | |
| + | You will need to gather the following information together for your application: | ||
| − | + | *Project Name, | |
| − | + | *Project purpose / overview, | |
| − | + | *Project Roadmap, | |
| − | + | *Project links (if any) to external sites, | |
| − | + | *[[Guidelines_for_OWASP_Projects#Project_Licensing|Project License],] | |
| − | + | *Project Leader name, | |
| − | + | *Project Leader email address, | |
| + | *Project Leader wiki account - the username (you'll need this to edit the wiki), | ||
| + | *Project Contributor(s) (if any) - name email and wiki account (if any), | ||
| + | *Project Main Links (if any). | ||
| + | *==>For Documentation: A table of Contents | ||
| + | *==>For Code: A prototype hosted in an open source repository of your choice. | ||
| − | + | '''Step 3:''' | |
| − | + | If all information is completed following the minimum criteria for Projects (Code/Tool/documentation), The Project Coordinator notifies the Project Leader that the request has been accepted, and at the same time notifies the Review team that a new project has been submitted, including all the information requested in the project criteria | |
| − | + | '''Step 4:''' | |
| − | + | Project Coordinator proceeds to create a new Wiki page for the project including all the information sent by the project leader. project coordinator uses one of these project wiki template: | |
| + | *For Docs: https://www.owasp.org/index.php/OWASP_Documentation_Project_Template | ||
| + | *For Code: https://www.owasp.org/index.php/OWASP_Code_Project_Template | ||
| + | *For Tool: https://www.owasp.org/index.php/OWASP_Tool_Project_Template | ||
| + | Also Project coordinator creates a mailing list for the project leader and sets him as admin | ||
| − | + | '''Step 5:''' | |
| − | + | Project Coordinator notifies project leader and Review team about the created wiki page, providing the link to the wiki page. | |
| + | *Review team might provide comments for further improvement of the wiki page if necessary | ||
| + | *Project leader should request a wiki account to be able to update his own wiki page afterwards if he has not one yet | ||
| − | + | '''Step 6:''' | |
| − | + | Project coordinator updates the Wiki project inventory, Dashboard and open hub with the information regarding the new created project | |
| + | '''Step 7:''' | ||
| + | Project is set in the agenda by the Project Coordinator for monitoring over the next 3 months to check how has been developing. | ||
| − | + | '''Step 8:''' | |
| + | Every 3 months, project coordinator monitors the activity on the wiki page for new updates and on the Openhub for commits and level of activity . Findings are then reported on the Dashboard as comments and CC through email to the review team | ||
| − | + | '''Step 9:''' | |
| − | + | if the project has not been updated and has no activities after six months of creation, project coordinator sends an email to the project leader requesting an update and status to see how has been developing, CC: project review team regarding the lack of activity .Findings are then updated on the dashboard. | |
| − | + | '''Step 10:''' | |
| − | + | Over the next 6 months the project is monitored again for activity. If no updates have occurred since its inception after 12 months, project is then set as inactive and project leader and review team is notified about the status. | |
| + | Project coordinators updates : | ||
| + | * Wiki page of the project is labeled as 'inactive' (inactive banner) | ||
| + | *The Project is set under the 'inactive category' | ||
| + | *Dashboard is updated with comments and set as inactive | ||
| − | + | <hr> | |
| − | |||
| − | + | '''Reference Material''' | |
| − | |||
| − | + | [https://www.openhub.net/orgs/OWASP Openhub] | |
| − | |||
| − | + | [https://docs.google.com/spreadsheets/d/1lO8UoQgIFET3MC5v2OVVdtkTe1IbWiJLMnINx6Hm2jE/edit?ts=56a159b7#gid=0 Dashboard] | |
| − | : | ||
| − | + | [[Project_Reviews_Guideline|Project Review Guidelines]] | |
| − | |||
| − | + | [http://owasp.github.io/ProjectReviews/index.html GITHUB OWASP] | |
| − | |||
| − | + | [https://docs.google.com/presentation/d/1tGdmgzDGjoHVtHZbV9dqGR2XQVlT8TR1cet-4r0C8RY/edit?ts=56a16be2#slide=id.gee0716e2f_0_1 Projects Slides] | |
| − | |||
| − | + | * Check out the '''[[Guidelines for OWASP Projects]]'''. | |
| − | + | * [[Grant_Spending_Policy|Grant Spending Policy]] | |
| + | * [[Project_Spending_Policy|Project Spending Policy]] | ||
| + | * [[Project_Sponsorship_Operational_Guidelines|Project Sponsorship Operational Guidelines]] | ||
| − | + | ==OWASP Recommended Licenses== | |
| − | |||
| − | + | {{Recommended_Licenses}} | |
| − | |||
| − | + | ==Funding your Project== | |
| − | + | An OWASP project does not receive any funding for development at project inception; however, a new project does have the opportunity to submit a request to receive funds if they are available for the year. Additionally, project leaders have the option of seeking sponsorship from outside organizations, but project leaders are required to seek funding through their own initiative. | |
| − | + | == Project Release == | |
| − | + | As your project reaches a point that you'd like OWASP to assist in its promotion, the will need the following information to help spread the word about your project: | |
| − | |||
| − | + | # Short 5 sentence paragraph outlining what your project is about, what you hope to accomplish with your project, what value your project brings to software security, and contributor and project leader names and contact information. | |
| − | + | # Link to your wiki page. | |
| + | # Link to your code repository or a link to where readers can download your project. | ||
| + | # Latest Release description answering the following questions: What is it?, What does it do?, Where can I get it?, Who should I contact if something goes wrong?. | ||
| − | + | ==Project Process Forms== | |
| − | + | These forms were created to help project leaders, and those interested in a going through a process in the OWASP projects infrastructure. They facilitate the management of each query based on the specific task an applicant will need help with. The forms are described below, and they are linked with their designated online application form. | |
| − | + | * [https://www.tfaforms.com/264422 Project Transition Application]:The OWASP project transition form gives current project leaders an easy way of handing over project administration information to individuals wishing to take over a project. | |
| − | : | ||
| − | + | * [https://www.tfaforms.com/264413 Project Review Application]:This form is for current project leaders to request a review of their project based on OWASP graduation criteria. The aim is to designate an OWASP volunteer to review these projects within 3 months time. | |
| − | : | ||
| − | + | * [http://www.tfaforms.com/264418 Project Donation Application]:This form is for projects outside of the OWASP project infrastructure. Project Leaders for these open source projects can choose to partner or give their project to OWASP directly through this form. | |
| − | + | * [https://www.tfaforms.com/264428 Project Adoption Request]:This form is used when someone is interested in adopting an archived project. | |
| − | : | ||
| − | + | * [https://www.tfaforms.com/264426 Project Abandonment Request]:The OWASP project abandonment form gives current project leaders an easy way of letting the OWASP Foundation know that they wish to resign their project leader duties. This form should be used when no replacement project leader exists to take over these duties. | |
| − | + | * [https://www.tfaforms.com/264392 Incubator Project Graduation Application]:This application form is for Incubator Projects to apply for Labs Project status. | |
| − | : | ||
| − | + | = Participating in a Project = | |
| − | |||
| − | + | <font size=2pt> | |
| − | + | == Joining a Project... == | |
| − | + | OWASP projects are community driven and most projects are open for anyone motivated to join. | |
| − | |} | + | The first step is to find a project you are interested to be part of. The list of all projects can be found in the {{#switchtablink:Project_Inventory|Project Inventory}}. Further steps then depend on the status of the project you selected. |
| − | + | If the project is active, the best way is to join the mailing list and get in touch with the people actively participating. Other ways would be contacting the project leader team or just starting to participate by testing the software, writing blogs or documentation, report issues via tracker or even propose code modifications. In general, the more you show your interest and motivation, the easier it is to find yourself as a member of the team. | |
| − | + | Some projects are of low activity or even inactive. In this case there is no possibility to join an existing team, but it would rather be a re-boot. If you feel eager to do this, please contact the general OWASP administrators. It is however important that you are sure about the commitment you are about to make. | |
| − | |||
| − | + | Some things are important: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | : | ||
| − | + | - Don’t be shy. If you wish to be part of the OWASP initiative, you will find a task that suits your experience and your level of possible time investment. | |
| − | |||
| − | + | - Baby steps are easier than huge commitments. Just start helping with small tasks and get known by the project team. You will grow into the project in a natural way. | |
| − | |||
| − | + | Please read more about the general project workflow on the {{#switchtablink:Starting_a_New_Project|Starting a New Project}} page. | |
| − | |||
| − | + | == Archives == | |
| − | |||
| − | + | [[Projects_Reboot_2012_Homepage|Archive of the 'Project Reboot 2012' page]] | |
| − | |||
| − | + | = Project Assessments = | |
| − | + | <font size=2pt> | |
| + | ==OWASP Project Lifecycle== | ||
| + | The OWASP Projects Lifecycle represents a balance between keeping a very loose structure around OWASP projects, and ensuring that OWASP consumers are not confused about a project’s maturity and quality. The lifecycle stage allows consumers to easily identify mature projects, and projects that are proofs of concept, experimental, and classified as prototypes in their current state. The greater the maturity of the project, the greater the level of responsibility for the project leader. These responsibilities are not trivial as OWASP provides incentives and benefits (Section 7) for projects who take on these added responsibilities. | ||
| − | |||
| − | |||
| − | + | ====The OWASP Project Lifecycle is broken down into the following stages:==== | |
| − | : | ||
| − | + | '''Incubator Projects''': OWASP Incubator projects represent the experimental playground where projects are still being designed, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity; moreover, the label allows project leaders to leverage the OWASP name while their project is still maturing. OWASP Incubator projects are given a place on the OWASP Projects Portal to leverage the organizations' infrastructure, and establish their presence and project history. | |
| − | |||
| − | + | '''Lab Projects''': OWASP Labs projects represent projects that have produced a deliverable of significant value. Leaders of OWASP Labs projects are expected to stand behind the quality of their projects as these projects have matured to the point where they are accepted by a significant portion of the OWASP community. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are ready for mainstream usage. OWASP Labs Projects are meant to be the collection of established projects that have gained community support and acclaim by undergoing the project review process. | |
| − | |||
| − | + | '''Flagship Projects''': The OWASP Flagship designation is given to projects that have demonstrated superior maturity, established quality, and strategic value to OWASP and application security as a whole. Eligible projects are selected from the OWASP Labs project pool. This selection process generally ensures that there is only one project of each type covering any particular security space. OWASP Flagship projects represent projects that are not only mature, but are also projects that OWASP as an organization provides direct support to maintaining. The core mission of OWASP is to make application security visible and so as an organization, OWASP has a vested interest in the success of its Flagship projects. Since Flagship projects have such high visibility, these projects are expected to uphold the most stringent requirements of all OWASP Projects. | |
| − | |||
| − | + | '''Code Projects''': OWASP code projects are very important for the cyber security solutions. Because these projects are used to find out the application security problems and try to solve those problems. | |
| − | |||
| − | + | == OWASP Project Stage Benefits== | |
| − | + | This section outlines the benefits of starting an OWASP project, and the benefits of being at each different stage in the projects lifecycle. In my short time here at OWASP as the PM, I have had several potential project leaders ask me what the benefits are of starting their project with OWASP. Below is my proposal for each Stage’s benefits. | |
| − | + | '''Incubator''' | |
| − | : | + | * Financial Donation Management Assistance |
| + | * Project Review Support | ||
| + | * WASPY Awards Nominations | ||
| + | * OWASP OSS and OPT Participation | ||
| + | * Opportunity to submit proposal: $500 for Development. | ||
| + | * Community Engagement and Support | ||
| + | * Recognition and visibility of being associated with the OWASP Brand. | ||
| − | + | '''Labs''' | |
| − | : | + | * All benefits given to Incubator Projects |
| + | * Technical Writing Support | ||
| + | * Graphic Design Support | ||
| + | * Project Promotion Support | ||
| + | * OWASP OSS and OPT: Preference | ||
| − | + | '''Flagship''' | |
| − | + | * All benefits given to Incubator & Labs Projects | |
| + | * Grant finding and proposal writing help | ||
| + | * Yearly marketing plan development | ||
| + | * OWASP OSS and OPT participation preference | ||
| − | + | For more detailed information on OWASP Project Stage Benefits, please see the Project Handbook. | |
| − | |||
| − | + | == Project Monitoring Incubator/Documentation == | |
| − | + | Every 6 months, a project monitoring assessment takes place to evaluate if projects had any releases during this period.A warning will be sent to projects without any activity in 90 days and after 180 days, the project will be set automatically as inactive. | |
| + | You can set your project active at any time, as long as: | ||
| + | * There has been commits to the project's open repository or | ||
| + | * There has been a beta release of the documentation produced so far or | ||
| + | * Provide a detailed Roadmap | ||
| − | + | ===Importance of a well thought out Roadmap=== | |
| − | + | Many Incubator project leaders struggle with creating a realistic planning, which should be based on their available resources and time. A well thought out plan makes a difference between a procrastinating project and a successful one. The important aspect of this is, that the project leader is able to create a plan based on his situation. The following is an example of a Roadmap, which has focused to produce a Documentation first release in a year and a basic outline how they plan to cover 4 essential aspects which are Research & Development, Marketing, Planning and Goals. | |
| − | |||
| − | |||
| − | + | [[File:RoadmapIncubatorProjectExample2.PNG | 600px]] | |
| − | |||
| − | + | "Your [project] roadmap should tell a coherent story about the likely growth of your product. Each release should build on the previous one and move you closer towards your vision. Your roadmap should be convincing and realistic: Don’t speculate or oversell your [project]. Be clear who your audience is: An internal roadmap talks to development, marketing, sales, service, and the other groups involved in making your [project] a success; and external one talks to existing and prospective customers." | |
| − | : | + | Extracted from : "[[http://www.romanpichler.com/blog/10-tips-creating-agile-product-roadmap/ 10 Tips for Creating an Agile Product Roadmap]]" |
| − | + | ==Project Monitoring for LABS/Flagship== | |
| − | : | + | These project represent the best OWASP has to offer, therefore monitoring of these projects is closely supervised. |
| + | ===For Code and Tools=== | ||
| + | For projects holding Flagship status, we closely monitor their health every 6 months on the following, among other key indicators: | ||
| + | *Can the project be built correctly? | ||
| + | *Does the project has any activity(commits) in the last 6 months? | ||
| + | *Does the project had any releases in the last 6 months? | ||
| + | *Has the project leaders updated his wiki or website to reflect latest releases? | ||
| + | ===For Documentation=== | ||
| + | For this part, we are working on the development of an adequate assessment criteria | ||
| + | The following is a draft of the new process proposal: [[:File:Qualitative_and_Quantitative_Content_Audit.pdf|Proposal for Reviewing OWASP Document projects]] | ||
| − | + | == OWASP Project Graduation== | |
| − | + | The Project Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs. In order to be considered for OWASP Labs, an Incubator project must have submitted an OWASP reviewed deliverable, and obtained at least two (2) positive responses for each of the core criteria project health questions. | |
| − | + | The review centers around the following core questions. Each core question has three (3) specific questions made up of binary queries. A project must receive at least two (2) positive responses from each reviewer in two of the binary questions, to warrant a postive response for the core question. Each core question must receive a positive response from both project reviewers to pass the Project Health Assessment for Incubator Projects. | |
| − | |||
| − | + | * [https://docs.google.com/spreadsheet/ccc?key=0AllOCxlYdf1AdG5NZGhzTjZpT1RDcnRibjd0aXhfOUE Project Graduation Criteria Checklist] | |
| − | : | ||
| − | + | To request graduation for your project please use the [https://owasporg.atlassian.net/servicedesk/customer/portal/7/create/71 Project Graduation Application] | |
| − | |||
| − | + | ==OWASP Project Health Assessment== | |
| − | + | The Project Health Assessment is an optional process undertaken at the request of a project leader when he/she applies for Project Graduation for projects going from Incubator to LAB and from LAB to Flagship. The purpose of this assessment is to determine whether a project meets the minimum criteria of an OWASP Project outlined in the [https://docs.google.com/spreadsheet/ccc?key=0AllOCxlYdf1AdG5NZGhzTjZpT1RDcnRibjd0aXhfOUE Project Health Assessment Criteria Document]. If a project passes the assessment, it then becomes eligible to graduate into the OWASP Labs Project stage. In order to be considered for OWASP Labs, an Incubator project must have submitted an OWASP reviewed deliverable, and obtained at least two (2) positive responses for each of the core criteria project health questions. | |
| − | + | ==OWASP Project Deliverable/Release Assessment== | |
| − | + | The Project Deliverable/Release Review is an optional process undertaken at the request of a project leader using the Project Deliverable Review Form. The purpose of this process is to review a project’s progress, and to make sure the project is heading in the right direction based on the roadmap they provided at project inception. | |
| − | + | Reviews must be performed by two (2) OWASP Chapter or Project Leaders, and their review must answer affirmatively to at least the first two (2) core Project Deliverable/Release Review questions. A project must pass the OWASP Project Deliverable/Release Assessment in order to graduate into the OWASP Labs Project stage. | |
| − | |||
| − | + | * [https://docs.google.com/spreadsheet/ccc?key=0AllOCxlYdf1AdG5NZGhzTjZpT1RDcnRibjd0aXhfOUE Project Deliverable/Release Assessment Criteria Checklist] | |
| − | |||
| − | |||
| − | |||
| − | + | = Brand Resources = | |
| − | + | <font size=2pt> | |
| − | + | ==The Brand Usage Rules== | |
| − | + | See OWASP's [[Marketing/Resources#tab=BRAND_GUIDELINES|The Brand Usage Rules]] for details. | |
| − | + | ==Project Icons & Templates== | |
| − | + | See OWASP'S [[Marketing/Resources#PROJECT_RESOURCES|Project Icons & Templates]] for details. | |
| − | + | (Following links and images are provided for a quick overview only, the primary page is [[Marketing/Resources#PROJECT_RESOURCES|Project Icons & Templates]]). | |
| − | |||
| − | + | If you require more assistance with these files and/or templates, please contact the OWASP staff for assistance | |
| − | |||
| − | + | '''[[OWASP_Operations_Project_Template|OWASP Operational Wiki Template]]''' | |
| − | |||
| − | + | '''[[OWASP_Documentation_Project_Template|OWASP Example Template: DO NOT EDIT]]''' | |
| − | |||
| − | + | [[Image:OWASP_Project_Header.jpg|Owasp logo|500px]] | |
| − | |||
| − | + | [[Image:Project_Type_Files_TOOL.jpg|Owasp logo|200px]] [[Image:Project_Type_Files_DOC.jpg||Owasp logo 1c|200px]] | |
| − | : | ||
| − | + | [[Image:Project_Type_Files_CODE.jpg|Owasp logo|200px]] [[Image:Owasp-defenders-small.png|Owasp logo|100px]] [[Image:Owasp-builders-small.png|Owasp logo|100px]] [[Image:Owasp-breakers-small.png|Owasp logo|100px]] | |
| − | : | ||
| − | + | [[Image:Owasp-incubator-trans-200.png|Owasp logo rev icon|100px]] [[Image:Owasp-labs-trans-85.png|Owasp logo flat|100px]] [[Image:Owasp-flagship-trans-85.png|Owasp logo icon|100px]] | |
| − | : | ||
| − | + | ===OpenSAMM=== | |
| − | + | '''[[Media:OpenSAMM_icons.zip|OpenSAMM Icons]]''' | |
| − | + | '''Construction:''' | |
| − | |||
| − | + | [[Image:Construction black.png| Construction black| 100px]] [[Image:Construction blue.png| Construction blue| 100px]] [[image:Construction olive.png |construction olive|100px]] | |
| − | : | ||
| − | + | '''Deployment:''' | |
| − | : | ||
| − | + | [[image:Deployment black.png| Deployment black| 100px]] [[image:Deployment blue.png| Deployment blue| 100px]] [[image:Deployment olive.png | Deployment olive| 100px]] | |
| − | : | ||
| − | + | '''Governance:''' | |
| − | |||
| − | + | [[image:Governance black.png| governance black| 100px]] [[image:Governance blue.png | governance blue | 100px]] [[image:Governance olive.png | governance olive| 100px]] | |
| − | : | ||
| − | + | '''Verification:''' | |
| − | |||
| − | + | [[image:Verification black.png | Verification black | 100px]] [[image:Verification blue.png | verification blue | 100px]] [[image: Verification olive.png | Verification olive | 100px]] | |
| − | : | ||
| − | + | ==Book Cover Files== | |
| − | + | See OWASP's [[Marketing/Resources#PROJECT_RESOURCES|Project Icons & Templates]] for details. | |
| − | + | [[Media:Lulu-guide.pdf|Lulu Guide]] | |
| − | |||
| − | + | '''[https://www.dropbox.com/s/h27gsbe5m7idg0y/Finished%20Covers.zip Download the Book Cover Zip File]''' | |
| − | + | {| | |
| + | |- | ||
| + | ! width="500" align="center" | <br> | ||
| + | ! width="300" align="center" | <br> | ||
| + | |- | ||
| + | | align="center" | [[Image:BookImage_01.jpg|500px| link=https://www.dropbox.com/s/h27gsbe5m7idg0y/Finished%20Covers.zip]] | ||
| + | | align="center" | | ||
| − | + | |} | |
| − | |||
| − | + | = Terminology = | |
| − | + | <font size=2pt> | |
| + | == OWASP Project Infrastructure == | ||
| − | |||
| − | |||
| − | + | *'''OWASP Project Lifecycle:''' The OWASP Projects Lifecycle represents a balance between keeping a very loose structure around OWASP projects, and ensuring that OWASP consumers are not confused about a project’s maturity and quality. The lifecycle stage allows consumers to easily identify mature projects, and projects that are proofs of concept, experimental, and classified as prototypes in their current state. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Incubator Project:''' OWASP Incubator projects represent the experimental playground where projects are still being fleshed out, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity. The label also allows project leaders to leverage the OWASP name while their project is still maturing. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Labs Project:''' OWASP Labs projects represent projects that have produced a deliverable of value. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are at least ready for mainstream usage. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | *'''Flagship Project:''' The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Benefits:''' The standard list of resources and incentives made available to project leaders based on their project's current maturity level. | |
| − | : | ||
| − | |||
| − | |||
| − | |||
| − | + | == OWASP Project Reviews == | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Reviews:''' Project reviews are the method OWASP uses to establish a minimal baseline of project characteristics and release quality. Reviews are not mandatory, but they are necessary if a project leader wishes to graduate to the next level of maturity within the OWASP Global Projects infrastructure. Projects can be reviewed when an Incubator project wishes to graduate into the OWASP Labs designation, and project releases can be reviewed if they want the quality of their deliverable to be vouched for by OWASP. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Reviewer Pool:''' The project reviewer pool is made up of veteran reviewers who have proven themselves dedicated to executing quality reviews of projects. | |
| − | :The | ||
| − | |||
| − | + | *'''Project Graduation:''' The Project Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs. | |
| − | |||
| − | |||
| − | + | *'''Project Health Assessment:''' The Project Health Assessment is an optional process undertaken at the request of a project leader when he/she applies for Project Graduation The purpose of this assessment is to determine whether a project meets the minimum criteria of an OWASP Project outlined in the [https://docs.google.com/a/owasp.org/spreadsheet/ccc?key=0AllOCxlYdf1AdG5NZGhzTjZpT1RDcnRibjd0aXhfOUE#gid=1 Project Health Assessment Criteria Document]. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Release:''' A project release refers to the final deliverable a project produces. It is the final product of the project. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Deliverable/Release Review:''' The Project Deliverable/Release Review is an optional process undertaken at the request of a project leader using the Project Deliverable Review Form. The purpose of this process is to review a project’s progress, and to make sure the project is heading in the right direction based on the roadmap they provided at project inception. | |
| − | |||
| − | |||
| − | |||
| − | + | == OWASP Projects Processes == | |
| − | |||
| − | + | *'''Project Processes:''' The set of streamlined processes that exist to help projects move smoothly through the OWASP Project Lifecycle. | |
| − | : | ||
| − | |||
| − | |||
| − | + | *'''Project Inception Process:''' The Project Inception Process is how a brand new idea becomes an OWASP Project. Such projects are labeled as OWASP Incubator projects. The process involves submitting the proposed project name, project leader information, project description, project roadmap, and selecting an appropriate open-source license for the project using the New Project Form on the Projects Portal. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Donation Process:''' The Project Donation Process is used for a project that has an existing functional release, but is not currently associated with OWASP. This process is the primary mechanism by which individuals or organizations can transfer the ownership of their project’s copyright to OWASP. | |
| − | :a project | ||
| − | |||
| − | |||
| − | + | *'''Project Transition Process:''' The Project Transition Process is used to transition leadership of a project to a new project leader. This is a simple automated process to transfer the relevant accounts, mailing lists, and other project resources to the new project leader. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | *'''Project Abandonment Process:''' The Project Abandonment Process was put in place for those occasions in which a project leader is no longer able to manage their project, and has not been able to find a suitable replacement for the leader role. Project Abandonment can also occur when the project leader feels his/her project has become obsolete. Under these circumstances, the acting project leader is encourage do submit the Project Abandonment Form found in the Projects Portal. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Incubator Graduation Process:''' The Incubator Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs. | |
| − | :a project | ||
| − | |||
| − | |||
| − | + | == Projects at Conferences == | |
| − | |||
| − | + | *'''AppSec Conferences:''' OWASP AppSec conferences bring together industry, government, security researchers, and practitioners to discuss the state of the art in application security. This series was launched in the United States in 2004 and Europe in 2005. Global AppSec conferences are held annually in North America, Latin America, Europe, and Asia Pacific. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''Open Source Showcase:''' The Open Source Showcase is an OWASP AppSec Conference event module designed to give Open Source project leaders the opportunity to demo their projects. | |
| − | |||
| − | |||
| − | |||
| − | + | *'''OWASP Project Track:''' The OWASP Project Track is an OWASP AppSec Conference event module designed to give OWASP Project leaders the opportunity to showcase their projects as an official conference presenter. | |
| − | |||
| − | |||
| − | |||
| − | + | == OWASP Projects General == | |
| − | |||
| − | + | *'''OWASP Code of Ethics:''' The OWASP Code of Ethics are the set of guidelines and principles that the OWASP Foundation expects all of its members and conference attendees to abide by. A copy of the Code of Ethics can be found here in the [[About_The_Open_Web_Application_Security_Project#Code_of_Ethics|OWASP About page]]. | |
| − | |||
| − | |||
| − | |||
| − | + | = Sponsorships and Donations = | |
| − | + | <font size=2pt> | |
| − | + | ==Donate to OWASP Global Projects == | |
| − | + | OWASP Projects, a global division of the OWASP Foundation, is run under the same world wide not-for-profit charitable status as all the foundation strategic groups. OWASP provides a platform for contributors to share their work while providing them with the project and community support they need throughout their project development. All OWASP Projects are run by volunteers and they rely on personal donations and sponsorship to continue their development. Donate to OWASP Projects, and we promise to spend your money wisely on open source initiatives. | |
| − | + | '''This is how your money can help:''' | |
| − | |||
| − | + | * $20 could help us spread the word on the importance of open source initiatives in the Application Security industry. | |
| − | + | * $100 could help fund OWASP project demos at major conferences. | |
| + | * $250 could help get our volunteer Project Leaders to speaking engagements. | ||
| − | |||
| − | |||
| − | + | [[Image:Donate_Button.jpg | link=http://www.regonline.com/Register/Checkin.aspx?EventID=1044369]] | |
| − | : | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | = Contact US = | |
| − | + | <font size=2pt> | |
| − | + | If you need any help with anything projects related, or if you simply need some more information, please do not hesitate to [Please contact the OWASP Projects Manager for more information. Contact Us]. | |
| − | + | </font> | |
| − | + | = Current Project Review Guidelines = | |
| − | + | <font size=3pt> | |
| − | + | PROJECT REVIEWS RESTART November 2016 | |
| − | |||
| − | + | Steps for Project Graduation Review: | |
| − | : | + | |
| + | Process Starts when Project Leader Requests a Graduation Review this is done through a [https://owasporg.atlassian.net/servicedesk/customer/portal/7/create/71 Project Graduation Application]. | ||
| − | + | Project Coordinator send link to the the Project Review Form for the Project Leader to provide the assessment. | |
| − | |||
| − | + | Senior Techinical Coordinator reviews the assessment received and works with the Project Leader if there are any questions. Once reviewed the assessment is passed to the Project Coordinator.. | |
| − | + | Project Coordinator Reviews the request and adds to the Volunteer Job Board for outreach to the community - http://owasp.force.com/volunteers/GW_Volunteers__Volunteerhttps://www.tfaforms.com/393806sJobListing | |
| + | Once volunteer signs up and chooses a project review then the Project Coordinator sends the link to the Volunteer with instructions to the google doc for the Project Review (Sample DOC) | ||
| − | + | There will need to be at least two reviewers for each Project Review along with the Senior Technical Coordinator to finalize the results. | |
| − | |||
| − | + | Senior Technical Coordinator could process a review if the there is lack of reviewers. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Senior Technical Coordinator/Volunteers has about 2-4 weeks to complete the Project Review . | |
| − | |||
| − | + | Senior Technical/ Volunteer works with the Project Leader on any information or questions. | |
| − | |||
| − | + | The time to complete can be extended to up to a an additional week. | |
| − | |||
| − | + | Senior Technical Coordinator provides recommendations. | |
| − | |||
| − | |||
| − | + | Project Coordinator sends Project Review to the community for feedback. | |
| − | |||
| − | + | Community Leaders can also process a review if they choose to disagree with the review. | |
| − | + | Project Graduation is announced by Connector and other social media | |
| − | + | Current OWASP Project Review Guidelines Link below: | |
| + | [[Project Reviews Guideline]] | ||
| + | </font> | ||
| + | <headertabs /> | ||
Latest revision as of 09:42, 23 September 2019
| |
|
|---|---|
- Welcome
- Project Inventory
- Former Project Task Force
- Online Resources
- Starting a New Project
- Participating in a Project
- Project Assessments
- Brand Resources
- Terminology
- Sponsorships and Donations
- Contact US
- Current Project Review Guidelines
|
|
Quick Guide to Projects
Quick Guide for Developers
This is a Quick Guide for Developers new to OWASP projects:
Infographic containing Hyperlinks to projects: https://magic.piktochart.com/output/6400107-untitled-infographic
Downloadable Images: File:Owasp Dev Guide.pdf
Flagship Projects
The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole. After a major review process More info here the following projects are considered to be flagship candidate projects. These project have been evaluated more deeply to confirm their flagship status:
Tools
- OWASP Zed Attack Proxy
- OWASP Web Testing Environment Project
- OWASP OWTF
- OWASP Dependency Check
- OWASP Security Shepherd
- OWASP DefectDojo Project
- OWASP Juice Shop Project
- OWASP Security Knowledge Framework
- OWASP Dependency Track Project
Code [Health Check January 2017]
Documentation
- OWASP Application Security Verification Standard Project
- OWASP Software Assurance Maturity Model (SAMM)
- OWASP AppSensor Project
- OWASP Top Ten Project
- OWASP Testing Project
- OWASP Cheat Sheet Series
- OWASP Mobile Security Testing Guide
Labs Projects
OWASP Labs projects represent projects that have produced a deliverable of value. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are at least ready for mainstream usage.
Thumbs up
Thumbs up are given to LAB projects showing a steady progress in their development, had very active and continuous releases and commits, regular update of information on their wiki page and have quite complete documentation. These projects are almost ready to become flagship
Tools
- O-Saft
- OWASP EnDe Project
- OWASP Mobile Security Project
- OWASP O2 Platform
- OWASP Passfault
- OWASP WebGoat Project
- OWASP Xenotix XSS Exploit Framework
- OWASP Code Pulse Project
- OWASP SeraphimDroid Project
- OWASP Glue Tool Project
- OWASP Amass Project
Documentation [Health Check January 2017]
- OWASP Code Review Guide Project
- OWASP Cornucopia
- OWASP Podcast Project
- OWASP Proactive Controls
- OWASP Internet of Things Top Ten Project
- OWASP Top 10 Privacy Risks Project
- OWASP Snakes and Ladders Project
- OWASP Automated Threats to Web Applications
Contests - Health Check February 2016
Code
Incubator Projects
OWASP Incubator projects represent the experimental playground where projects are still being fleshed out, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity. The label also allows project leaders to leverage the OWASP name while their project is still maturing.
Thumbs up
Thumbs up are given to incubator projects showing a steady progress in their development, had continuous releases and commits or have delivered a complete product, including open source repository location, basic user guidelines and documentation
Code
- OWASP Java Encoder Project

- OWASP Java HTML Sanitizer Project

- OWASP Node.js Goat Project

- OWASP Mth3l3m3nt Framework Project

- OWASP CSRFProtector Project
- OWASP WebGoat PHP Project

- OWASP Secure Headers Project
- OWASP Vicnum Projct

- OWASP DeepViolet TLS/SSL_Scanner

- OWASP Off the record 4 Java Project

- OWASP Learning Gateway Project
- OWASP SonarQube Project
- OWASP Zenzengorri Code Project
- OWASP Find Security Bugs
- OWASP Vulnerable Web Application
- OWASP Samurai WTF
- OWASP Secure Coding Dojo
Research
Tools
- OWASP Threat Dragon

- OWASP Mutillidae 2 Project
- OWASP Pyttacker Project

- OWASP ZSC Tool Project

- OWASP Basic Expression Lexicon Variation Algorithms (Belva) Project]

- OWASP VBScan

- OWASP Appsec Pipeline

- OWASP Bug Logging Tool

- OWASP iGoat Tool Project
- OWASP Risk Rating Management
- OWASP DevSlop Project
- OWASP SecurityRAT Project
- OWASP SecureTea Project
- OWASP Attack Surface Detector Project
- OWASP Nettacker
- OWASP Serverless Goat
- OWASP Honeypot
- OWASP DVSA
- OWASP Python Honeypot
- OWASP Maryam Project
- OWASP QRLJacker
- OWASP D4N155
- OWASP Jupiter
Documentation
- OWASP Vulnerable Web Applications Directory Project

- OWASP .NET Project
- OWASP Incident Response Project
 *
* - OWSP_Application_Security_Program_Quick_Start_Guide_Project
- OWASP SecLists Project
- OWASP Knowledge Based Authentication Performance Metrics Project

- OWASP RFP Criteria
- OWASP Web Mapper Project

- OWASP 10 Fuer Entwickler
- WASC_OWASP_Web_Application_Firewall_Evaluation_Criteria_Project

- OWASP_Secure_Software_Development_Lifecycle_Project
- OWASP Ransomeware Guide Project

- OWASP Cyber Defense Matrix
- OWASP Top 5 Machine Learning Risks
- OWASP Security Operations Center SOC Framework Project
- OWASP Vulnerability Management Guide
- OWASP Embedded Application Security
- OWASP Application Security Curriculum
- OWASP Software Security 5D Framework
- OWASP Anti-Ransomware Guide Project
- OWASP Serverless Top 10 Project
- OWASP Cloud-Native Application Security Top 10
- OWASP Application Security Guide For CISOs Project
- OWASP Cloud Security Project
- OWASP Docker Top 10
- OWASP Blockchain Security Framework
- OWASP API Security Project
- OWASP PHP Project
- OWASP Security Pins Project
- OWASP Risk Assessment Framework
- OWASP Container Security Verification Standard
- OWASP Top 10 Card Game
- OWASP DevSecOps Maturity Model
- OWASP Secure Medical Device Deployment Standard
Educational Initiatives
Health Check February 2017
- OWASP Student Chapters Project

- OWASP Education Project

- OWASP Speakers Project

- OWASP Media Project

- OWASP PHP Security Training Project

- OWASP Online Academy

Low Activity Projects
Low Activity (LABS)[Reviewed July 2015] Health Check February 2016
These projects had no releases in at least a year, however have shown to be valuable tools Code [Low Activity] Health Check February 2016
Tools Health Check February 2016
Documentation [Low Activity] Health Check February 2016
- OWASP Legal Project

- Virtual Patching Best Practices

- OWASP Secure Coding Practices - Quick Reference Guide

Donated Projects
OWASP Donated Projects are inactive projects that have been donated to the OWASP Projects Infrastructure.
Tools
OWASP Archived Projects
OWASP Archived Projects are projects that have developed outside OWASP umbrella or have become inactive. If you are interested in pursuing any of the inactive projects (click hyperlink for list), please contact us and let us know of your interest.
Added New Project on February 2016
OWASP Project Task Force
This task force is focused on OWASP Projects with a first focus on cleaning up the OWASP incubator list
Project Online Resources
Please note that some services are 100% free and some have nominal cost.
This page is for OWASP project leaders and details some of the online services that have been found to be useful for OWASP projects.
How to Run a Successful Open Source Project
http://www2.econ.iastate.edu/tesfatsi/ProducingOSS.KarlFogel2005.pdf
GitHub
OWASP is a registered Organisation on GitHub, a free, public directory of Free and Open Source Software and the contributors who create and maintain it.
If you manage an OWASP project you should:
- Register yourself on GitHub
- Request that your repository get created by a GitHub admin and that you are made an admin on the repository
- Check that the settings are correct for your repositor
Other Free Services
These are all free to open source projects.
- http://crowdin.net/ a translation and localization management platform
- https://scan.coverity.com/ C/C++/C# and Java static source code analysis
Other Paid For Services
Open for Suggestions and depending on your project budget and/or *Community Engagement Funding.
- Please note: Th cost may be covered by the Community Engagement Funding up to $500 if it meets the policy requirements.
If it is more than $500 or outside policy guidelines, it would require special approval by our Executive Director.
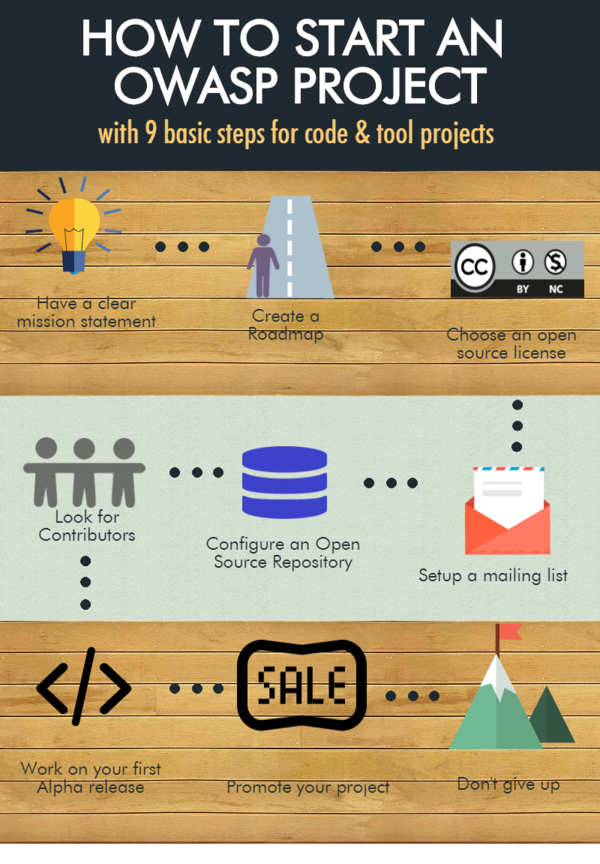
So you want to start a project...
Starting an OWASP project is quite easy, and your desire to contribute and make it happen is essential.
Here are some of the guidelines for running a successful OWASP project:
-Start exploring the actual OWASP projects Inventory. Many projects handle specific areas of security it is a good idea to start looking how other successful projects do this (LABS/Flagship)
-Place your idea or project on the Project Ideas Board. This phase will help you to define the project goals and also explore and exchange with other OWASP leaders and volunteers how to develop the idea into a tangible project
-Explore and research if your idea covers a unique segment in the Security arena. Think of your project as a product, if you really want people using it, think how this project will cover a necessity in the security area you are working on
-Define what kind of project you would like to start. Is it a code, tool or documentation?
-Communicate through the Project leader mailing list about your idea and get feedback and meet potential contributors
-Develop your project based on the type of project. For example if you are willing to start a documentation project, begin by defining a Table of Content and work it through with potential contributors. First of all begin by creating a Road-map for your project. This is essential to submit your project. We highly recommend to read documentation such as "How to start /run a successful Open Source Projects".
Some recommendations on how to start a documentation project Document Guide Project
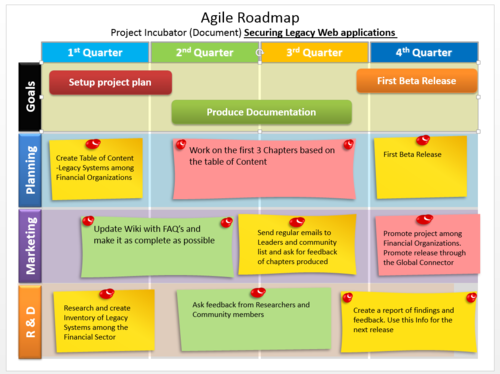
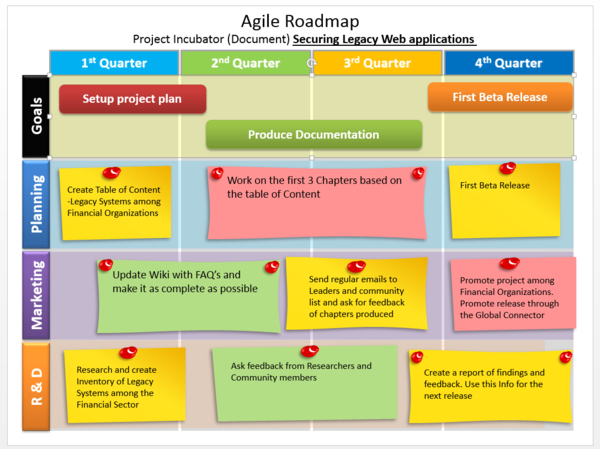
Importance of a well thought out Road-map
Many Incubator project leaders struggle with creating a realistic planning, which should be based on their available resources and time. A well thought out plan makes a difference between a procrastinating project and a successful one. The important aspect of this is, that the project leader is able to create a plan based on his situation. The following is an example of a Roadmap, which has focused to produce a Documentation first release in a year and a basic outline how they plan to cover 4 essential aspects which are Research & Development, Marketing, Planning and Goals.
"Your [project] roadmap should tell a coherent story about the likely growth of your product. Each release should build on the previous one and move you closer towards your vision. Your roadmap should be convincing and realistic: Don’t speculate or oversell your [project]. Be clear who your audience is: An internal roadmap talks to development, marketing, sales, service, and the other groups involved in making your [project] a success; and external one talks to existing and prospective customers." Extracted from : "[10 Tips for Creating an Agile Product Roadmap]"
- Start defining a development, documentation and marketing plan for your project. Set short , medium and long term plans. Include promotion of your project, this is very important in order to engage users and consumers of your project. You can run a single person project, but it's usually best to get the community involved. You should be prepared to support a mailing list, build a team, speak at conferences, and promote your project.
- You can contribute existing documents or tools to OWASP! Assuming you have the intellectual property rights to a work, you can open it to the world as an OWASP Project. Please coordinate this with OWASP by Contacting Us.
- Available Grants to consider if you need funding - Click Here
- You should promote your project through the OWASP channels as well as by outside means. Get people to blog about it!
Creating a New Project
Once you have passed the Project Ideas phase, then you will be ready to start a new project
Please submit a new project application here.'
2016 OWASP Project Process
Step 1: New Project Leader submits New Project Request Form it is logged in the system and an alert is sent to the Project Coordinator
Step 2: New Project Request is received and reviewed by Project Coordinator for complete information .It must contain the following information to qualify as an acceptable submission: You will need to gather the following information together for your application:
- Project Name,
- Project purpose / overview,
- Project Roadmap,
- Project links (if any) to external sites,
- [[Guidelines_for_OWASP_Projects#Project_Licensing|Project License],]
- Project Leader name,
- Project Leader email address,
- Project Leader wiki account - the username (you'll need this to edit the wiki),
- Project Contributor(s) (if any) - name email and wiki account (if any),
- Project Main Links (if any).
- ==>For Documentation: A table of Contents
- ==>For Code: A prototype hosted in an open source repository of your choice.
Step 3: If all information is completed following the minimum criteria for Projects (Code/Tool/documentation), The Project Coordinator notifies the Project Leader that the request has been accepted, and at the same time notifies the Review team that a new project has been submitted, including all the information requested in the project criteria
Step 4: Project Coordinator proceeds to create a new Wiki page for the project including all the information sent by the project leader. project coordinator uses one of these project wiki template:
- For Docs: https://www.owasp.org/index.php/OWASP_Documentation_Project_Template
- For Code: https://www.owasp.org/index.php/OWASP_Code_Project_Template
- For Tool: https://www.owasp.org/index.php/OWASP_Tool_Project_Template
Also Project coordinator creates a mailing list for the project leader and sets him as admin
Step 5: Project Coordinator notifies project leader and Review team about the created wiki page, providing the link to the wiki page.
- Review team might provide comments for further improvement of the wiki page if necessary
- Project leader should request a wiki account to be able to update his own wiki page afterwards if he has not one yet
Step 6: Project coordinator updates the Wiki project inventory, Dashboard and open hub with the information regarding the new created project
Step 7: Project is set in the agenda by the Project Coordinator for monitoring over the next 3 months to check how has been developing.
Step 8: Every 3 months, project coordinator monitors the activity on the wiki page for new updates and on the Openhub for commits and level of activity . Findings are then reported on the Dashboard as comments and CC through email to the review team
Step 9: if the project has not been updated and has no activities after six months of creation, project coordinator sends an email to the project leader requesting an update and status to see how has been developing, CC: project review team regarding the lack of activity .Findings are then updated on the dashboard.
Step 10: Over the next 6 months the project is monitored again for activity. If no updates have occurred since its inception after 12 months, project is then set as inactive and project leader and review team is notified about the status. Project coordinators updates :
- Wiki page of the project is labeled as 'inactive' (inactive banner)
- The Project is set under the 'inactive category'
- Dashboard is updated with comments and set as inactive
Reference Material
- Check out the Guidelines for OWASP Projects.
- Grant Spending Policy
- Project Spending Policy
- Project Sponsorship Operational Guidelines
OWASP Recommended Licenses
Why are you recommending these licenses?
Which other open source licenses are eligible for an OWASP project?
Choosing a license under which an artifact is distributed and enforcing the license are prerogatives of the copyright holders over that artifact. By default, each contributor is copyright holder over the contributed piece. Contributors must all agree on the license and cooperate in enforcing it or must assign their copyright to the entity which becomes responsible for choosing and enforcing the license.
OWASP is a collaborative initiative for the public good and most of its output is expected to be functional, rather than aesthetic. The problem OWASP tackles is so large that OWASP acknowledges a need to collaborate with the commercial world. Therefore, in order to become an OWASP Sponsored Project, you should be comfortable with:
- Allowing arbitrary uses for your work, for example for commercial purposes. (If you disagree, consider using CC-BY-NC.)
- Revealing to the world your project's source code (its form preferred for modification).
- Allowing your work, under certain conditions (see below), to be modified by others and redistributed. (If you disagree, consider using CC-BY-ND.)
| Artifact | Under what conditions can your work be modified and redistributed? | |||
|---|---|---|---|---|
| As long as modifications are licensed in the same spirit | If credit is appropriately given to you | Under any circumstances | ||
| Standalone Tool | Run locally |
|
|
|
| Consumed over the network |
| |||
| Library |
| |||
| Document (includes E-Learning, presentations, books etc.) |
|
| ||
Funding your Project
An OWASP project does not receive any funding for development at project inception; however, a new project does have the opportunity to submit a request to receive funds if they are available for the year. Additionally, project leaders have the option of seeking sponsorship from outside organizations, but project leaders are required to seek funding through their own initiative.
Project Release
As your project reaches a point that you'd like OWASP to assist in its promotion, the will need the following information to help spread the word about your project:
- Short 5 sentence paragraph outlining what your project is about, what you hope to accomplish with your project, what value your project brings to software security, and contributor and project leader names and contact information.
- Link to your wiki page.
- Link to your code repository or a link to where readers can download your project.
- Latest Release description answering the following questions: What is it?, What does it do?, Where can I get it?, Who should I contact if something goes wrong?.
Project Process Forms
These forms were created to help project leaders, and those interested in a going through a process in the OWASP projects infrastructure. They facilitate the management of each query based on the specific task an applicant will need help with. The forms are described below, and they are linked with their designated online application form.
- Project Transition Application:The OWASP project transition form gives current project leaders an easy way of handing over project administration information to individuals wishing to take over a project.
- Project Review Application:This form is for current project leaders to request a review of their project based on OWASP graduation criteria. The aim is to designate an OWASP volunteer to review these projects within 3 months time.
- Project Donation Application:This form is for projects outside of the OWASP project infrastructure. Project Leaders for these open source projects can choose to partner or give their project to OWASP directly through this form.
- Project Adoption Request:This form is used when someone is interested in adopting an archived project.
- Project Abandonment Request:The OWASP project abandonment form gives current project leaders an easy way of letting the OWASP Foundation know that they wish to resign their project leader duties. This form should be used when no replacement project leader exists to take over these duties.
- Incubator Project Graduation Application:This application form is for Incubator Projects to apply for Labs Project status.
Joining a Project...
OWASP projects are community driven and most projects are open for anyone motivated to join.
The first step is to find a project you are interested to be part of. The list of all projects can be found in the Project Inventory. Further steps then depend on the status of the project you selected.
If the project is active, the best way is to join the mailing list and get in touch with the people actively participating. Other ways would be contacting the project leader team or just starting to participate by testing the software, writing blogs or documentation, report issues via tracker or even propose code modifications. In general, the more you show your interest and motivation, the easier it is to find yourself as a member of the team.
Some projects are of low activity or even inactive. In this case there is no possibility to join an existing team, but it would rather be a re-boot. If you feel eager to do this, please contact the general OWASP administrators. It is however important that you are sure about the commitment you are about to make.
Some things are important:
- Don’t be shy. If you wish to be part of the OWASP initiative, you will find a task that suits your experience and your level of possible time investment.
- Baby steps are easier than huge commitments. Just start helping with small tasks and get known by the project team. You will grow into the project in a natural way.
Please read more about the general project workflow on the Starting a New Project page.
Archives
OWASP Project Lifecycle
The OWASP Projects Lifecycle represents a balance between keeping a very loose structure around OWASP projects, and ensuring that OWASP consumers are not confused about a project’s maturity and quality. The lifecycle stage allows consumers to easily identify mature projects, and projects that are proofs of concept, experimental, and classified as prototypes in their current state. The greater the maturity of the project, the greater the level of responsibility for the project leader. These responsibilities are not trivial as OWASP provides incentives and benefits (Section 7) for projects who take on these added responsibilities.
The OWASP Project Lifecycle is broken down into the following stages:
Incubator Projects: OWASP Incubator projects represent the experimental playground where projects are still being designed, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity; moreover, the label allows project leaders to leverage the OWASP name while their project is still maturing. OWASP Incubator projects are given a place on the OWASP Projects Portal to leverage the organizations' infrastructure, and establish their presence and project history.
Lab Projects: OWASP Labs projects represent projects that have produced a deliverable of significant value. Leaders of OWASP Labs projects are expected to stand behind the quality of their projects as these projects have matured to the point where they are accepted by a significant portion of the OWASP community. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are ready for mainstream usage. OWASP Labs Projects are meant to be the collection of established projects that have gained community support and acclaim by undergoing the project review process.
Flagship Projects: The OWASP Flagship designation is given to projects that have demonstrated superior maturity, established quality, and strategic value to OWASP and application security as a whole. Eligible projects are selected from the OWASP Labs project pool. This selection process generally ensures that there is only one project of each type covering any particular security space. OWASP Flagship projects represent projects that are not only mature, but are also projects that OWASP as an organization provides direct support to maintaining. The core mission of OWASP is to make application security visible and so as an organization, OWASP has a vested interest in the success of its Flagship projects. Since Flagship projects have such high visibility, these projects are expected to uphold the most stringent requirements of all OWASP Projects.
Code Projects: OWASP code projects are very important for the cyber security solutions. Because these projects are used to find out the application security problems and try to solve those problems.
OWASP Project Stage Benefits
This section outlines the benefits of starting an OWASP project, and the benefits of being at each different stage in the projects lifecycle. In my short time here at OWASP as the PM, I have had several potential project leaders ask me what the benefits are of starting their project with OWASP. Below is my proposal for each Stage’s benefits.
Incubator
- Financial Donation Management Assistance
- Project Review Support
- WASPY Awards Nominations
- OWASP OSS and OPT Participation
- Opportunity to submit proposal: $500 for Development.
- Community Engagement and Support
- Recognition and visibility of being associated with the OWASP Brand.
Labs
- All benefits given to Incubator Projects
- Technical Writing Support
- Graphic Design Support
- Project Promotion Support
- OWASP OSS and OPT: Preference
Flagship
- All benefits given to Incubator & Labs Projects
- Grant finding and proposal writing help
- Yearly marketing plan development
- OWASP OSS and OPT participation preference
For more detailed information on OWASP Project Stage Benefits, please see the Project Handbook.
Project Monitoring Incubator/Documentation
Every 6 months, a project monitoring assessment takes place to evaluate if projects had any releases during this period.A warning will be sent to projects without any activity in 90 days and after 180 days, the project will be set automatically as inactive. You can set your project active at any time, as long as:
- There has been commits to the project's open repository or
- There has been a beta release of the documentation produced so far or
- Provide a detailed Roadmap
Importance of a well thought out Roadmap
Many Incubator project leaders struggle with creating a realistic planning, which should be based on their available resources and time. A well thought out plan makes a difference between a procrastinating project and a successful one. The important aspect of this is, that the project leader is able to create a plan based on his situation. The following is an example of a Roadmap, which has focused to produce a Documentation first release in a year and a basic outline how they plan to cover 4 essential aspects which are Research & Development, Marketing, Planning and Goals.
"Your [project] roadmap should tell a coherent story about the likely growth of your product. Each release should build on the previous one and move you closer towards your vision. Your roadmap should be convincing and realistic: Don’t speculate or oversell your [project]. Be clear who your audience is: An internal roadmap talks to development, marketing, sales, service, and the other groups involved in making your [project] a success; and external one talks to existing and prospective customers." Extracted from : "[10 Tips for Creating an Agile Product Roadmap]"
Project Monitoring for LABS/Flagship
These project represent the best OWASP has to offer, therefore monitoring of these projects is closely supervised.
For Code and Tools
For projects holding Flagship status, we closely monitor their health every 6 months on the following, among other key indicators:
- Can the project be built correctly?
- Does the project has any activity(commits) in the last 6 months?
- Does the project had any releases in the last 6 months?
- Has the project leaders updated his wiki or website to reflect latest releases?
For Documentation
For this part, we are working on the development of an adequate assessment criteria The following is a draft of the new process proposal: Proposal for Reviewing OWASP Document projects
OWASP Project Graduation
The Project Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs. In order to be considered for OWASP Labs, an Incubator project must have submitted an OWASP reviewed deliverable, and obtained at least two (2) positive responses for each of the core criteria project health questions.
The review centers around the following core questions. Each core question has three (3) specific questions made up of binary queries. A project must receive at least two (2) positive responses from each reviewer in two of the binary questions, to warrant a postive response for the core question. Each core question must receive a positive response from both project reviewers to pass the Project Health Assessment for Incubator Projects.
To request graduation for your project please use the Project Graduation Application
OWASP Project Health Assessment
The Project Health Assessment is an optional process undertaken at the request of a project leader when he/she applies for Project Graduation for projects going from Incubator to LAB and from LAB to Flagship. The purpose of this assessment is to determine whether a project meets the minimum criteria of an OWASP Project outlined in the Project Health Assessment Criteria Document. If a project passes the assessment, it then becomes eligible to graduate into the OWASP Labs Project stage. In order to be considered for OWASP Labs, an Incubator project must have submitted an OWASP reviewed deliverable, and obtained at least two (2) positive responses for each of the core criteria project health questions.
OWASP Project Deliverable/Release Assessment
The Project Deliverable/Release Review is an optional process undertaken at the request of a project leader using the Project Deliverable Review Form. The purpose of this process is to review a project’s progress, and to make sure the project is heading in the right direction based on the roadmap they provided at project inception.
Reviews must be performed by two (2) OWASP Chapter or Project Leaders, and their review must answer affirmatively to at least the first two (2) core Project Deliverable/Release Review questions. A project must pass the OWASP Project Deliverable/Release Assessment in order to graduate into the OWASP Labs Project stage.
The Brand Usage Rules
See OWASP's The Brand Usage Rules for details.
Project Icons & Templates
See OWASP'S Project Icons & Templates for details.
(Following links and images are provided for a quick overview only, the primary page is Project Icons & Templates).
If you require more assistance with these files and/or templates, please contact the OWASP staff for assistance
OWASP Operational Wiki Template
OWASP Example Template: DO NOT EDIT
OpenSAMM
Construction:
Deployment:
Governance:
Verification:
Book Cover Files
See OWASP's Project Icons & Templates for details.
Download the Book Cover Zip File
| |
|
|---|---|

|
OWASP Project Infrastructure
- OWASP Project Lifecycle: The OWASP Projects Lifecycle represents a balance between keeping a very loose structure around OWASP projects, and ensuring that OWASP consumers are not confused about a project’s maturity and quality. The lifecycle stage allows consumers to easily identify mature projects, and projects that are proofs of concept, experimental, and classified as prototypes in their current state.
- Incubator Project: OWASP Incubator projects represent the experimental playground where projects are still being fleshed out, ideas are still being proven, and development is still underway. The “OWASP Incubator” label allows OWASP consumers to readily identify a project’s maturity. The label also allows project leaders to leverage the OWASP name while their project is still maturing.
- Labs Project: OWASP Labs projects represent projects that have produced a deliverable of value. While these projects are typically not production ready, the OWASP community expects that an OWASP Labs project leader is producing releases that are at least ready for mainstream usage.
- Flagship Project: The OWASP Flagship designation is given to projects that have demonstrated strategic value to OWASP and application security as a whole.
- Project Benefits: The standard list of resources and incentives made available to project leaders based on their project's current maturity level.
OWASP Project Reviews
- Project Reviews: Project reviews are the method OWASP uses to establish a minimal baseline of project characteristics and release quality. Reviews are not mandatory, but they are necessary if a project leader wishes to graduate to the next level of maturity within the OWASP Global Projects infrastructure. Projects can be reviewed when an Incubator project wishes to graduate into the OWASP Labs designation, and project releases can be reviewed if they want the quality of their deliverable to be vouched for by OWASP.
- Project Reviewer Pool: The project reviewer pool is made up of veteran reviewers who have proven themselves dedicated to executing quality reviews of projects.
- Project Graduation: The Project Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs.
- Project Health Assessment: The Project Health Assessment is an optional process undertaken at the request of a project leader when he/she applies for Project Graduation The purpose of this assessment is to determine whether a project meets the minimum criteria of an OWASP Project outlined in the Project Health Assessment Criteria Document.
- Project Release: A project release refers to the final deliverable a project produces. It is the final product of the project.
- Project Deliverable/Release Review: The Project Deliverable/Release Review is an optional process undertaken at the request of a project leader using the Project Deliverable Review Form. The purpose of this process is to review a project’s progress, and to make sure the project is heading in the right direction based on the roadmap they provided at project inception.
OWASP Projects Processes
- Project Processes: The set of streamlined processes that exist to help projects move smoothly through the OWASP Project Lifecycle.
- Project Inception Process: The Project Inception Process is how a brand new idea becomes an OWASP Project. Such projects are labeled as OWASP Incubator projects. The process involves submitting the proposed project name, project leader information, project description, project roadmap, and selecting an appropriate open-source license for the project using the New Project Form on the Projects Portal.
- Project Donation Process: The Project Donation Process is used for a project that has an existing functional release, but is not currently associated with OWASP. This process is the primary mechanism by which individuals or organizations can transfer the ownership of their project’s copyright to OWASP.
- Project Transition Process: The Project Transition Process is used to transition leadership of a project to a new project leader. This is a simple automated process to transfer the relevant accounts, mailing lists, and other project resources to the new project leader.
- Project Abandonment Process: The Project Abandonment Process was put in place for those occasions in which a project leader is no longer able to manage their project, and has not been able to find a suitable replacement for the leader role. Project Abandonment can also occur when the project leader feels his/her project has become obsolete. Under these circumstances, the acting project leader is encourage do submit the Project Abandonment Form found in the Projects Portal.
- Incubator Graduation Process: The Incubator Graduation Process is an optional process undertaken at the request of a project leader using the Incubator Graduation Form. The purpose of this process is to move a project from the OWASP Incubator into the OWASP Labs.
Projects at Conferences
- AppSec Conferences: OWASP AppSec conferences bring together industry, government, security researchers, and practitioners to discuss the state of the art in application security. This series was launched in the United States in 2004 and Europe in 2005. Global AppSec conferences are held annually in North America, Latin America, Europe, and Asia Pacific.
- Open Source Showcase: The Open Source Showcase is an OWASP AppSec Conference event module designed to give Open Source project leaders the opportunity to demo their projects.
- OWASP Project Track: The OWASP Project Track is an OWASP AppSec Conference event module designed to give OWASP Project leaders the opportunity to showcase their projects as an official conference presenter.
OWASP Projects General
- OWASP Code of Ethics: The OWASP Code of Ethics are the set of guidelines and principles that the OWASP Foundation expects all of its members and conference attendees to abide by. A copy of the Code of Ethics can be found here in the OWASP About page.
Donate to OWASP Global Projects
OWASP Projects, a global division of the OWASP Foundation, is run under the same world wide not-for-profit charitable status as all the foundation strategic groups. OWASP provides a platform for contributors to share their work while providing them with the project and community support they need throughout their project development. All OWASP Projects are run by volunteers and they rely on personal donations and sponsorship to continue their development. Donate to OWASP Projects, and we promise to spend your money wisely on open source initiatives.
This is how your money can help:
- $20 could help us spread the word on the importance of open source initiatives in the Application Security industry.
- $100 could help fund OWASP project demos at major conferences.
- $250 could help get our volunteer Project Leaders to speaking engagements.
If you need any help with anything projects related, or if you simply need some more information, please do not hesitate to [Please contact the OWASP Projects Manager for more information. Contact Us].
PROJECT REVIEWS RESTART November 2016
Steps for Project Graduation Review:
Process Starts when Project Leader Requests a Graduation Review this is done through a Project Graduation Application.
Project Coordinator send link to the the Project Review Form for the Project Leader to provide the assessment.
Senior Techinical Coordinator reviews the assessment received and works with the Project Leader if there are any questions. Once reviewed the assessment is passed to the Project Coordinator..
Project Coordinator Reviews the request and adds to the Volunteer Job Board for outreach to the community - http://owasp.force.com/volunteers/GW_Volunteers__Volunteerhttps://www.tfaforms.com/393806sJobListing Once volunteer signs up and chooses a project review then the Project Coordinator sends the link to the Volunteer with instructions to the google doc for the Project Review (Sample DOC)
There will need to be at least two reviewers for each Project Review along with the Senior Technical Coordinator to finalize the results.
Senior Technical Coordinator could process a review if the there is lack of reviewers.
Senior Technical Coordinator/Volunteers has about 2-4 weeks to complete the Project Review .
Senior Technical/ Volunteer works with the Project Leader on any information or questions.
The time to complete can be extended to up to a an additional week.
Senior Technical Coordinator provides recommendations.
Project Coordinator sends Project Review to the community for feedback.
Community Leaders can also process a review if they choose to disagree with the review.
Project Graduation is announced by Connector and other social media
Current OWASP Project Review Guidelines Link below: Project Reviews Guideline
Subcategories
This category has the following 132 subcategories, out of 132 total.
A
B
C
D
E
F
G
H
I
J
L
M
N
O
P
R
S
T
V
W
X
Y
Pages in category "OWASP Project"
The following 200 pages are in this category, out of 419 total.
(previous page) (next page)A
B
C
- Classic ASP Security Project
- GPC Project Details/OWASP Cloud ‐ 10 Project
- GPC Project Details/OWASP Code Crawler
- Code review
- OWASP Codes of Conduct
- Collaborate
- OWASP Common Numbering Project
- GPC Project Details/OWASP CBT Project
- Cornucopia - Ecommerce Website Edition - Wiki Deck
- OWASP Corporate Application Security Rating Guide
- OWASP Cross-Site Request Forgery Research Pool
- OWASP CSRFGuard Project/es
- CSRFProtector Project
E
G
H
J
M
O
- O-Saft
- O-Saft/Documentation
- OWASP O2 Platform Project - Project Identification
- Octoms
- Opa
- Projects/Opa
- OWASP OVAL Content Project
- OWASP - Cyber Security in the Boardroom
- OWASP 1-Liner
- OWASP A&D Project
- OWASP Academy Portal Project
- OWASP AJAX Crawling Tool
- OWASP Amass Project
- OWASP Androick Project
- OWASP Anti-Ransomware Guide Project
- OWASP API Security Project
- OWASP APK DISSECTOR
- OWASP Application Fuzzing Framework Project
- OWASP Application Security Curriculum
- OWASP Application Security Guide For CISOs Project
- OWASP Application Security Guide For CISOs Project v2
- OWASP Application Security Program Quick Start Guide Project
- OWASP AppSec Designer Security Functional Requirements & Countermeasures Libraries
- OWASP AppSec Pipeline
- OWASP Appsec Tutorial Series
- OWASP AppSensor Handbook
- OWASP AppSensor Project
- OWASP ASP.NET MVC Boilerplate Project
- OWASP Assimilation Project
- OWASP ASVS Assessment tool
- OWASP Attack Surface Detector Project
- OWASP Auth
- OWASP Automated Threats to Web Applications
- OWASP Autosploit Project
- OWASP Barbarus
- OWASP Basic Expression & Lexicon Variation Algorithms (BELVA) Project
- OWASP Best Practices in Vulnerability Disclosure and Bug Bounty Programs
- OWASP Broken Web Applications Project
- OWASP Browser Security Project
- OWASP Bug Logging Tool
- OWASP Bywaf Project
- OWASP Cheat Sheet Series
- OWASP Chinese Project
- OWASP CISO Survey Project
- OWASP Click Me Project
- OWASP Cloud Security Mentor
- OWASP Cloud Security Project
- OWASP Cloud Testing Guide
- OWASP Cloud-Native Application Security Top 10
- OWASP Code Project Template
- OWASP Code Pulse Project
- OWASP Container Security Verification Standard (CSVS)
- OWASP Cornucopia
- OWASP Counter Project
- OWASP Crossword of the Month
- OWASP Crowdtesting
- OWASP Cyber Defense Matrix
- OWASP D4N155
- OWASP Damn Vulnerable Crypto Wallet
- OWASP Damn Vulnerable Web Sockets (DVWS)
- OWASP DeepViolet TLS/SSL Scanner
- OWASP DefectDojo Project
- OWASP Dependency Check
- OWASP Dependency Track Project
- OWASP Desktop Goat and Top 5 Project
- OWASP DevSecOps Maturity Model
- OWASP DevSlop Project
- OWASP Documentation Project Template
- OWASP Droid Fusion
- OWASP Droid10 Project
- OWASP DVSA
- OWASP Ecuador
- OWASP EJSF Project
- OWASP Embedded Application Security
- OWASP Encoder Comparison Reference Project
- OWASP Example Incubator
- OWASP Excess XSS Project
- OWASP Faux Bank Project
- OWASP File Hash Repository
- OWASP Financial Information Exchange Security Project
- OWASP Find Security Bugs
- OWASP Focus
- OWASP Framework Security Project
- OWASP Game Security Framework Project
- OWASP Global Chapter Meetings Project
- OWASP Glue Tool Project
- OWASP Go Secure Coding Practices Guide
- OWASP Good Component Practices Project
- OWASP Google Assistant
- OWASP Guide Project
- OWASP H2H Tool Project
- OWASP HA Vulnerability Scanner Project
- OWASP Hackademic Challenges Project
- OWASP Hacking Lab
- OWASP Hacking-the Pentest Tutor Game
- OWASP Hive Project
- OWASP Honeypot Project
- OWASP ICS / SCADA Security Project
- OWASP iGoat Tool Project
- OWASP iMAS iOS Mobile Application Security Project
- OWASP Incident Response Project
- OWASP Information Security Metrics Bank
- OWASP Insecure Web Components Project
- OWASP Intelligent Intrusion Detection System
- OWASP Internet of Things Project
- OWASP IOT Analytics 4Industry4
- OWASP iSABEL Proxy Server
- OWASP ISO IEC 27034 Application Security Controls Project
- OWASP ISO Project
- OWASP Java Encoder Project
- OWASP Java File I O Security Project
- OWASP Java J2EE Secure Development Curriculum
- OWASP Java Uncertain Form Submit Prevention
- OWASP JavaScript Sandboxes
- OWASP JAWS Project
- OWASP JOTP Project
- OWASP JSEC CVE Details
- OWASP JSON Sanitizer
- OWASP Jupiter
- OWASP KALP Mobile Project
- OWASP Kates Project
- OWASP Knowledge Based Authentication Performance Metrics Project
- OWASP Knowledge Graph
- OWASP LAPSE Project
- OWASP Learning Platform Project
- OWASP Lock It
- OWASP Logging
- OWASP LWAF