This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:OWASP Joomla Vulnerability Scanner Project"
| (29 intermediate revisions by 2 users not shown) | |||
| Line 5: | Line 5: | ||
{| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- | ||
| valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | | valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | ||
| + | [[file:JoomScan_Logo.png|right]] | ||
| + | |||
<div class="plainlinks"> | <div class="plainlinks"> | ||
| Line 19: | Line 21: | ||
</div> | </div> | ||
| + | [[File:joomscan_download.png|link=https://github.com/rezasp/joomscan/releases]] | ||
| − | |||
| − | ==OWASP | + | ==OWASP JoomScan Project == |
| − | OWASP | + | OWASP Joomla! Vulnerability Scanner (JoomScan) is an open source project, developed with the aim of automating the task of vulnerability detection and reliability assurance in Joomla CMS deployments. Implemented in Perl, this tool enables seamless and effortless scanning of Joomla installations, while leaving a minimal footprint with its lightweight and modular architecture. It not only detects known offensive vulnerabilities, but also is able to detect many misconfigurations and admin-level shortcomings that can be exploited by adversaries to compromise the system. Furthermore, OWASP JoomScan provides a user-friendly interface and compiles the final reports in both text and HTML formats for ease of use and minimization of reporting overheads.<br> |
| + | '''OWASP JoomScan is included in Kali Linux distributions.''' | ||
| + | ==== Why joomscan ? ==== | ||
| + | |||
| + | Automated ... | ||
| + | *Version enumerator | ||
| + | *Vulnerability enumerator (based on version) | ||
| + | *Components enumerator (1205 most popular by default) | ||
| + | *Components vulnerability enumerator (based on version)(+950 exploit) | ||
| + | *Firewall detector | ||
| + | *Reporting to Text & HTML output | ||
| + | *Finding common log files | ||
| + | *Finding common backup files | ||
| − | |||
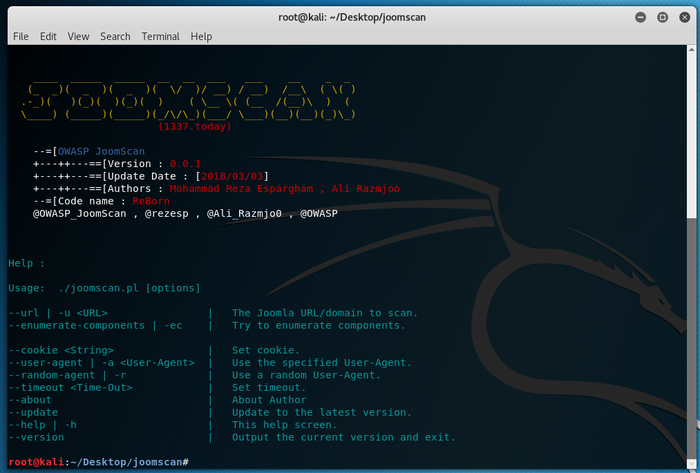
| − | + | [[File:Joomscan screenshot.png|700px|thumb|center]] | |
| Line 35: | Line 48: | ||
<span style="color:#ff0000"> | <span style="color:#ff0000"> | ||
| − | OWASP | + | OWASP JoomScan (short for [Joom]la Vulnerability [Scan]ner) is an opensource project in Perl programming language to detect Joomla CMS vulnerabilities and analyses them. |
| − | |||
| + | {| | ||
| + | |- | ||
| + | {{#ev:youtube|Ik2CJ9LkuoI}} | ||
| + | |} | ||
==LICENSE== | ==LICENSE== | ||
| Line 67: | Line 83: | ||
[mailto:[email protected] Mohammad Reza Espargham] | [mailto:[email protected] Mohammad Reza Espargham] | ||
| + | |||
| + | [mailto:[email protected] Ali Razmjoo] | ||
| + | |||
| + | == Contributors & Main Developers == | ||
| + | |||
| + | * [mailto:[email protected] Alireza Zare] | ||
| + | * [mailto:[email protected] Hesam Bazvand] | ||
| + | * [https://github.com/EnDe EnDe] | ||
| + | * [mailto:[email protected] Farhad Sasani] | ||
| + | * [https://github.com/ajdumanhug Aj Dumanhug] | ||
| + | * [https://github.com/jcesarstef Julio C. Stefanutto] | ||
| + | * [https://github.com/duraki halis duraki] | ||
==Classifications== | ==Classifications== | ||
| Line 86: | Line 114: | ||
== News and Events == | == News and Events == | ||
| − | * | + | * [https://www.blackhat.com/us-18/arsenal.html#mohammad-reza-espargham OWASP JoomScan at Blackhat Arsenal - USA 2018] |
| + | * JoomScan 0.0.5 - "#BHUSA" Released | ||
| + | * [http://lists.owasp.org/pipermail/owasp-leaders/2018-March/019076.html OWASP JoomScan at Blackhat Arsenal - Singapore 2018] | ||
| + | * [https://tools.kali.org/web-applications/joomscan Latest version of OWASP JoomScan added to Kali Linux repository] | ||
| + | * JoomScan 0.0.5 - "KLOT" Released | ||
| + | * JoomScan 0.0.1 - "Reborn" Released | ||
| + | * [https://www.blackhat.com/asia-18/arsenal.html#mohammad-reza-espargham OWASP Joomscan has Been Selected for Blackhat Asia Arsenal 2018] | ||
| + | |||
|} | |} | ||
| Line 99: | Line 134: | ||
* [https://www.owasp.org/index.php/User:rezasp Mohammad Reza Espargham] | * [https://www.owasp.org/index.php/User:rezasp Mohammad Reza Espargham] | ||
| + | * [https://www.owasp.org/index.php/User:alirazmjoo Ali Razmjoo] | ||
= Road Map and Getting Involved = | = Road Map and Getting Involved = | ||
Latest revision as of 18:10, 16 August 2019
|
OWASP JoomScan ProjectOWASP Joomla! Vulnerability Scanner (JoomScan) is an open source project, developed with the aim of automating the task of vulnerability detection and reliability assurance in Joomla CMS deployments. Implemented in Perl, this tool enables seamless and effortless scanning of Joomla installations, while leaving a minimal footprint with its lightweight and modular architecture. It not only detects known offensive vulnerabilities, but also is able to detect many misconfigurations and admin-level shortcomings that can be exploited by adversaries to compromise the system. Furthermore, OWASP JoomScan provides a user-friendly interface and compiles the final reports in both text and HTML formats for ease of use and minimization of reporting overheads. Why joomscan ?Automated ...
Description
OWASP JoomScan (short for [Joom]la Vulnerability [Scan]ner) is an opensource project in Perl programming language to detect Joomla CMS vulnerabilities and analyses them.
LICENSEGNU GENERAL PUBLIC LICENSE , Version 3, 29 June 2007Copyright (C) 2007 Free Software Foundation, Inc. http://fsf.org/ Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Click to see the full license
The OWASP Security Principles are licensed under the http://creativecommons.org/licenses/by-sa/3.0/ Creative Commons Attribution-ShareAlike 3.0 license], so you can copy, distribute and transmit the work, and you can adapt it, and use it commercially, but all provided that you attribute the work and if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. |
Quick Download[Download Page.] Project LeaderContributors & Main DevelopersClassifications
|
News and Events
| |||||||
Contributors
joomscan source code located in github and you could see contributors in this URL.
Please feel free to fork and submit your pull request to develop joomscan Project together.
Leader
This project is going to be the best Joomla scanner, At the end We could have a joomla cms penetration tester which is updated with the last vulnerabilities.
Roadmap
This Project was created to be a joomscanner which already it is and now need to be best with some tasks:
- Optimize software core to be fast and easy to develop
- make it module base and create libraries for developers
- Support all OS
- Be update with latest exploits.
- Create documents for newbie users
- Keep testing and fix bugs!
Feedback
Please submit your feedbacks and issues in HERE.
- What do like?
- What don't you like?
- What features would you like to see prioritized on the roadmap?
- Do you have any problem with tool?
- Do you need any exploit to be add?
Subcategories
This category has only the following subcategory.
O
Pages in category "OWASP Joomla Vulnerability Scanner Project"
The following 5 pages are in this category, out of 5 total.