This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Category:OWASP Flash Security Project
The OWASP Flash Security Project aims is to produce guidelines and tools around Flash Security
SWFIntruder is a tool developed by Stefano Di Paola and maintened by OWASP designed to perform a security analysis of Flash applications.
SWF Intruder Overview
SWFIntruder (pronounced Swiff Intruder) is the first tool specifically developed for analyzing and testing security of Flash applications at runtime. It helps to find flaws in Flash applications using the methodology originally described by Stefano Di Paola in Testing Flash Applications (May 2007) and in Finding Vulnerabilities in Flash Applications (Nov 2007).
SWFIntruder was developed using ActionScript, Html and JavaScript resulting in a tool taking advantage of the best features of those technologies in order to get the best capabilities for analysis and interaction with the testing Flash movies.
SWFIntruder was developed by using only opensource software. Thanks to its genericity, SWFIntruder is OS indipendant.
Goals
SWFIntruder purpose is to analyse a Flash application for version =< 8 and to help check in a semi automated fashion the presence of security issues like Cross Site Scripting and Coss Site Flashing.
Moreover does help raise awareness around the subject of flash applications security and how that can be used to and assist in the security of applications.
QuickStart
Tested on win32 and a few linux flavours. Current version is 0.9. Get it from Google code.
Latest Features
Permanent Preferences, Help Topics, ActionScript Object Explorer, Automated Xss testing fully customizable.
Video Tutorial
Watch (medium quality) or download (high quality) the flash tutorial taking you through some basic features of SWFIntruder.
Download
You can download the latest version of SWFIntruder from Google code.
Requirements
1. Firefox 2.x [Needed] 2. FireBug Addon [Suggested] 3. Flash Player Plugin Ver >= 9 [Needed] 4. Any Web Server [Needed] 5. Any OS [Needed :> ]
Quick and Dirty Tutorial
- Download SWFIntruder latest version from Google Code.
- Uncompress it and save it somewhere in your websever root directory.
- Browse to http://YourHost/swfintruderDir/.
- Use test.swf (a simple flawed swf movie) by filling the "Flash Movie Form" with http://YourHost/swfintruderDir/testSwf/test.swf or download a swf from some host and save it to an accessible path from your web server (http://YourHost/swfDirectory/external.swf).
- Fill the "Flash Movie" form with full URL pointing to the movie (http://YourHost/swfDirectory/test.swf) and click "Load".
- Wait 1 second for the test movie to be loaded.
- Enjoy browsing the objects.
- Test undefined variables by selecting some of them in the "Undefined Variables" and click 'start' on the Xss window.
- Wait for the test to be finished.
- If some XSS was found, it will be listed in the Xss area click on it to get the result on a new browser window.
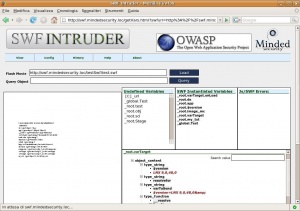
Features and Screenshots
- Basic predefined attack patterns.
- Highly customizable attacks.
- Highly customizable undefined variables.
- Semi automated Xss check.
- User congurable internal parameters.
- Log Window for debugging and tracking.
- History of latest 5 tested SWF files.
- ActionScript Objects runtime explorer in tree view.
- Persistent Configuration and Layout.
Project Contributors
The Flash Security project is run by Stefano Di Paola. He can be contacted at wisec AT owasp.org.
SWFintruder distributions are currently maintained on [Google code].
If you are interested in volunteering for the project, or have a comment, question, or suggestion, please join the Flash Security
Project Sponsors
The SWF Intruder project is sponsored by

This category currently contains no pages or media.