This site is the archived OWASP Foundation Wiki and is no longer accepting Account Requests.
To view the new OWASP Foundation website, please visit https://owasp.org
Difference between revisions of "Category:OWASP CSRFGuard Project"
(→Source Code) |
Bill Sempf (talk | contribs) (→Classifications: Added stage and category) |
||
| (82 intermediate revisions by 9 users not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
| − | + | =Main= | |
| − | [ | + | <div style="width:100%;height:90px;border:0,margin:0;overflow: hidden;">[[File: flagship_big.jpg|link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Flagship_Projects]]</div> |
| − | == | + | {| style="padding: 0;margin:0;margin-top:10px;text-align:left;" |- |
| + | | valign="top" style="border-right: 1px dotted gray;padding-right:25px;" | | ||
| − | CSRFGuard | + | ==OWASP CSRFGuard == |
| − | + | Welcome to the home of the OWASP CSRFGuard Project! OWASP CSRFGuard is a library that implements a variant of the [http://www.corej2eepatterns.com/Design/PresoDesign.htm synchronizer token pattern] to mitigate the risk of [[Cross-Site Request Forgery]] (CSRF) attacks. | |
| − | + | ==Introduction== | |
| − | + | The OWASP CSRFGuard library is integrated through the use of a JavaEE Filter and exposes various automated and manual ways to integrate per-session or pseudo-per-request tokens into HTML. | |
| − | == | + | ==Description== |
| − | + | ==== Overview ==== | |
| − | + | OWASP CSRFGuard implements a variant of the synchronizer token pattern to mitigate the risk of CSRF attacks. In order to implement this pattern, CSRFGuard must offer the capability to place the CSRF prevention token within the HTML produced by the protected web application. CSRFGuard 3 provides developers more fine grain control over the injection of the token. Developers can inject the token in their HTML using either dynamic JavaScript DOM manipulation or a JSP tag library. CSRFGuard no longer intercepts and modifies the HttpServletResponse object as was done in previous releases. The currently available token injection strategies are designed to make the integration of CSRFGuard more feasible and scalable within current enterprise web applications. Developers are encouraged to make use of both the JavaScript DOM Manipulation and the JSP tag library strategies for a complete token injection strategy. The JavaScript DOM Manipulation strategy is ideal as it is automated and requires minimal effort on behalf of the developer. In the event the JavaScript solution is insufficient within a particular application context, developers should leverage the JSP tag library. The purpose of this article is to describe the token injection strategies offered by OWASP CSRFGuard 3. | |
| − | === | + | ==== JavaScript DOM Manipulation ==== |
| − | + | OWASP CSRFGuard 3 supports the ability to dynamically inject CSRF prevention tokens throughout the DOM currently loaded in the user's browser. This strategy is extremely valuable with regards to server-side performance as it simply requires the serving of a dynamic JavaScript file. There is little to no performance hit when the fetched dynamic JavaScript updates the browser's DOM. Making use of the JavaScript token injection solution requires the developer map a Servlet and place a JavaScript HTML tag within all pages sending requests to protected application resources. Developers are strongly encouraged to leverage the JavaScript token injection strategy by default. This strategy requires minimal effort on behalf of the developer as most of the token injection logic is automated. In the event that the JavaScript automated solution may be insufficient for a specific application context, developers should leverage the OWASP CSRFGuard JSP tag library. | |
| − | + | '''Note:''' Use of JavaScript DOM Manipulation is required for Ajax support. | |
| − | |||
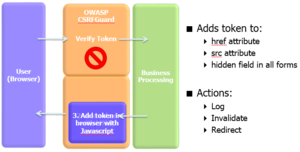
| − | [ | + | [[File:CSRGuard.PNG|300px|thumb|left|CSRFGuard Architecture]] |
| − | + | == What is CSRFGuard? == | |
| − | + | OWASP CSRFGuard provides: | |
| + | * A library that implements a variant of the synchronizer token pattern to mitigate the risk of Cross-Site Request Forgery (CSRF) attacks. | ||
| + | * A JavaEE Filter and exposes various automated and manual ways to integrate per-session or pseudo-per-request tokens into HTML. | ||
| − | |||
| − | + | == Ohloh == | |
| − | + | *https://www.ohloh.net/p/OWASP-CSRFGuard | |
| − | + | | valign="top" style="padding-left:25px;width:200px;" | | |
| − | |||
| − | |||
| − | |||
| − | + | == In Print == | |
| − | + | This project can be purchased as a print on demand book from Lulu.com | |
| − | + | ==Classifications== | |
| − | [ | + | {| width="200" cellpadding="2" |
| + | |- | ||
| + | | align="center" valign="top" width="50%" rowspan="2"| [[File:Owasp-flagship-trans-85.png|link=https://www.owasp.org/index.php/OWASP_Project_Stages#tab=Flagship_Projects]] | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-builders-small.png|link=]] | ||
| + | |- | ||
| + | | align="center" valign="top" width="50%"| [[File:Owasp-defenders-small.png|link=]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:Cc-button-y-sa-small.png|link=http://creativecommons.org/licenses/by-sa/3.0/]] | ||
| + | |- | ||
| + | | colspan="2" align="center" | [[File:Project_Type_Files_CODE.jpg|link=]] | ||
| + | |} | ||
| − | + | |} | |
| − | + | = Licensing = | |
| − | + | OWASP CSRFGuard 3.1 is offered under the BSD license | |
| − | + | | valign="top" style="padding-left:25px;width:200px;border-right: 1px dotted gray;padding-right:25px;" | | |
| − | = | + | = Presentation & Manual = |
| − | + | Link to presentation | |
| − | + | https://www.owasp.org/index.php/CSRFGuard_3_Token_Injection | |
| − | + | = Project Leader = | |
| − | + | The CSRFGuard project is run by [mailto:azzeddine.ramrami(at)owasp.org Azzeddine RAMRAMI]. | |
| − | + | The project co-leader is [mailto:sebastien.gioria(at)owasp.org Sébastien Gioria]. | |
| − | : | + | With the active participation of: |
| − | : | + | [mailto:ahamednafeez(at)gmail.com Ahamed Nafeez] : Security Tester & Bug Finder |
| − | : | + | [mailto:Trent.schmidt(at)gmail.com Trent Schmidt] : Release & Maven Central helper |
| − | == | + | == Related Projects == |
| − | + | :*[http://www.owasp.org/index.php/Category:OWASP_CSRFTester_Project OWASP CSRFTester ] - utility to assist in the testing and generating PoC for CSRF attacks. | |
| + | :*[[Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet | OWASP CSRF Prevention Cheat Sheet]] - provides a more holistic overview of CSRF prevention strategies and associated frameworks. | ||
| + | :*http://www.owasp.org/index.php/PHP_CSRF_Guard - project implementing CSRFGuard style solution for PHP. | ||
| + | :*http://www.thespanner.co.uk/2007/10/19/jsck/ - project implementing CSRFGuard style solution for PHP and JavaScript. | ||
| + | :*http://www.owasp.org/index.php/.Net_CSRF_Guard - project implementing CSRFGuard style solution for ASP.NET. | ||
| + | :*https://www.owasp.org/index.php/CSRFProtector_Project - CSRF Protector Project - Implements new Anti CSRF method in web applications | ||
| − | = | + | = Source Code Download = |
| − | + | Download and build the latest source code from GitHub : | |
| − | [[ | + | * https://github.com/aramrami/OWASP-CSRFGuard |
| − | [[ | + | |
| − | [[Category: | + | Download and build the latest source code from GitHub - https://github.com/aramrami/OWASP-CSRFGuard-3 |
| − | [[Category: | + | |
| + | [[CSRFGuard_Deprecated_Releases | Deprecated Releases]] - article containing several download references to deprecated and officially unsupported releases | ||
| + | |||
| + | == CSRFGuard Binary in Maven Central == | ||
| + | |||
| + | You can download a binary version from Maven Central here: | ||
| + | |||
| + | * https://oss.sonatype.org/#nexus-search;gav~~csrfguard | ||
| + | |||
| + | Thanks to Trent Schmidt and Joel Orlina (JIRA) for there help. | ||
| + | |||
| + | == User Manual(s) == | ||
| + | |||
| + | [[CSRFGuard_3_User_Manual | OWASP CSRFGuard v3 ]] - series of articles describing the installation, configuration, and deployment of OWASP CSRFGuard v3. | ||
| + | = News and Events = | ||
| + | |||
| + | * [08 Fev 2014] A security fix has been published. See details on GitHub | ||
| + | * [10 Feb 2014] Release 3.1 of CSRFGuard project is now available for download | ||
| + | * [28 Jul 2014] A new Github repository called "OWASP CSRFGuard-3" with issues management has been created | ||
| + | =FAQs= | ||
| + | |||
| + | Here a complete CSRF attacks FAQ: | ||
| + | |||
| + | * http://www.cgisecurity.com/csrf-faq.html | ||
| + | |||
| + | = Acknowledgements = | ||
| + | ==Volunteers== | ||
| + | |||
| + | CSRFGuard is developed by a worldwide team of volunteers. The primary contributors to date have been: | ||
| + | |||
| + | * Ahamed Nafeez, Security Engineer. | ||
| + | * Christa Erwin, Security, Programmer/Analyst. | ||
| + | * Trent Schmidt, Release & Maven Central helper | ||
| + | |||
| + | ==Others== | ||
| + | |||
| + | * Eric Sheridan was the original designer of CSRFGuard until 3.0 version. | ||
| + | |||
| + | = Road Map and Getting Involved = | ||
| + | |||
| + | As of CSRFGuard the priorities are: | ||
| + | * Address any security vulnerabilities around javascript prototype hijacking | ||
| + | * Support for Internet Explorer | ||
| + | * Addressing outstanding issues listed in GitHub | ||
| + | * Support for Multi-part requests | ||
| + | * Add support for the 'Origin' header | ||
| + | |||
| + | Involvement in the development and promotion of CSRFGurd is actively encouraged! | ||
| + | You do not have to be a security expert in order to contribute. | ||
| + | Some of the ways you can help: | ||
| + | * Make fix to the actual version | ||
| + | * Propose a security enhcement | ||
| + | * Write a complete Architecture Folder for CSRFGurd | ||
| + | * Add an IA engine to detect unknown attacks. | ||
| + | |||
| + | |||
| + | |||
| + | =Contact US= | ||
| + | You can sign up for the OWASP CSRFGuard email list at [https://lists.owasp.org/mailman/listinfo/owasp-csrfguard https://lists.owasp.org/mailman/listinfo/owasp-csrfguard] | ||
| + | |||
| + | __NOTOC__ <headertabs /> | ||
| + | |||
| + | [[Category:OWASP Project]] | ||
| + | [[Category:SAMM-SA-2]] | ||
Latest revision as of 20:19, 28 March 2016
- Main
- Licensing
- Presentation & Manual
- Project Leader
- Source Code Download
- News and Events
- FAQs
- Acknowledgements
- Road Map and Getting Involved
- Contact US
OWASP CSRFGuardWelcome to the home of the OWASP CSRFGuard Project! OWASP CSRFGuard is a library that implements a variant of the synchronizer token pattern to mitigate the risk of Cross-Site Request Forgery (CSRF) attacks. IntroductionThe OWASP CSRFGuard library is integrated through the use of a JavaEE Filter and exposes various automated and manual ways to integrate per-session or pseudo-per-request tokens into HTML. DescriptionOverviewOWASP CSRFGuard implements a variant of the synchronizer token pattern to mitigate the risk of CSRF attacks. In order to implement this pattern, CSRFGuard must offer the capability to place the CSRF prevention token within the HTML produced by the protected web application. CSRFGuard 3 provides developers more fine grain control over the injection of the token. Developers can inject the token in their HTML using either dynamic JavaScript DOM manipulation or a JSP tag library. CSRFGuard no longer intercepts and modifies the HttpServletResponse object as was done in previous releases. The currently available token injection strategies are designed to make the integration of CSRFGuard more feasible and scalable within current enterprise web applications. Developers are encouraged to make use of both the JavaScript DOM Manipulation and the JSP tag library strategies for a complete token injection strategy. The JavaScript DOM Manipulation strategy is ideal as it is automated and requires minimal effort on behalf of the developer. In the event the JavaScript solution is insufficient within a particular application context, developers should leverage the JSP tag library. The purpose of this article is to describe the token injection strategies offered by OWASP CSRFGuard 3. JavaScript DOM ManipulationOWASP CSRFGuard 3 supports the ability to dynamically inject CSRF prevention tokens throughout the DOM currently loaded in the user's browser. This strategy is extremely valuable with regards to server-side performance as it simply requires the serving of a dynamic JavaScript file. There is little to no performance hit when the fetched dynamic JavaScript updates the browser's DOM. Making use of the JavaScript token injection solution requires the developer map a Servlet and place a JavaScript HTML tag within all pages sending requests to protected application resources. Developers are strongly encouraged to leverage the JavaScript token injection strategy by default. This strategy requires minimal effort on behalf of the developer as most of the token injection logic is automated. In the event that the JavaScript automated solution may be insufficient for a specific application context, developers should leverage the OWASP CSRFGuard JSP tag library. Note: Use of JavaScript DOM Manipulation is required for Ajax support.
What is CSRFGuard?OWASP CSRFGuard provides:
Ohloh |
In PrintThis project can be purchased as a print on demand book from Lulu.com Classifications
| |||||||
OWASP CSRFGuard 3.1 is offered under the BSD license
| valign="top" style="padding-left:25px;width:200px;border-right: 1px dotted gray;padding-right:25px;" |
Link to presentation
The CSRFGuard project is run by Azzeddine RAMRAMI.
The project co-leader is Sébastien Gioria.
With the active participation of:
Ahamed Nafeez : Security Tester & Bug Finder Trent Schmidt : Release & Maven Central helper
Related Projects
- OWASP CSRFTester - utility to assist in the testing and generating PoC for CSRF attacks.
- OWASP CSRF Prevention Cheat Sheet - provides a more holistic overview of CSRF prevention strategies and associated frameworks.
- http://www.owasp.org/index.php/PHP_CSRF_Guard - project implementing CSRFGuard style solution for PHP.
- http://www.thespanner.co.uk/2007/10/19/jsck/ - project implementing CSRFGuard style solution for PHP and JavaScript.
- http://www.owasp.org/index.php/.Net_CSRF_Guard - project implementing CSRFGuard style solution for ASP.NET.
- https://www.owasp.org/index.php/CSRFProtector_Project - CSRF Protector Project - Implements new Anti CSRF method in web applications
Download and build the latest source code from GitHub :
Download and build the latest source code from GitHub - https://github.com/aramrami/OWASP-CSRFGuard-3
Deprecated Releases - article containing several download references to deprecated and officially unsupported releases
CSRFGuard Binary in Maven Central
You can download a binary version from Maven Central here:
Thanks to Trent Schmidt and Joel Orlina (JIRA) for there help.
User Manual(s)
OWASP CSRFGuard v3 - series of articles describing the installation, configuration, and deployment of OWASP CSRFGuard v3.
- [08 Fev 2014] A security fix has been published. See details on GitHub
- [10 Feb 2014] Release 3.1 of CSRFGuard project is now available for download
- [28 Jul 2014] A new Github repository called "OWASP CSRFGuard-3" with issues management has been created
Here a complete CSRF attacks FAQ:
Volunteers
CSRFGuard is developed by a worldwide team of volunteers. The primary contributors to date have been:
- Ahamed Nafeez, Security Engineer.
- Christa Erwin, Security, Programmer/Analyst.
- Trent Schmidt, Release & Maven Central helper
Others
- Eric Sheridan was the original designer of CSRFGuard until 3.0 version.
As of CSRFGuard the priorities are:
- Address any security vulnerabilities around javascript prototype hijacking
- Support for Internet Explorer
- Addressing outstanding issues listed in GitHub
- Support for Multi-part requests
- Add support for the 'Origin' header
Involvement in the development and promotion of CSRFGurd is actively encouraged! You do not have to be a security expert in order to contribute. Some of the ways you can help:
- Make fix to the actual version
- Propose a security enhcement
- Write a complete Architecture Folder for CSRFGurd
- Add an IA engine to detect unknown attacks.
You can sign up for the OWASP CSRFGuard email list at https://lists.owasp.org/mailman/listinfo/owasp-csrfguard
Pages in category "OWASP CSRFGuard Project"
The following 4 pages are in this category, out of 4 total.